
CVE-2019-0708, popularly known as BlueKeep, is a RDP pre-authentication vulnerability which allows attacker to compromise a vulnerable system without user’s interaction. This exploit is also wormable, meaning that it can spread to other vulnerable systems in a similar way as the WannaCry malware spread across the globe in 2017. Interestingly, healthcare products like radiography, X-ray and other imaging software of various healthcare vendors running on Windows OS are also affected by the BlueKeep exploit.
Since the time this vulnerability was patched by Microsoft, multiple PoCs exploiting it have emerged in public. In September, exploit code for this vulnerability was added in the popular exploitation framework, Metasploit. Chances are that, script kiddies would jump on this Metasploit module to carry out large scale attacks on vulnerable hosts with RDP port open to Internet. Recently, few sources reported that attackers are exploiting this vulnerability for dropping Monero cryptocurrency miner on the unpatched vulnerable machines. We saw an uptick in the detections for these attacks in our telemetry as well. Here is the OS-wise distribution of BlueKeep attacks we blocked in last 6 months.
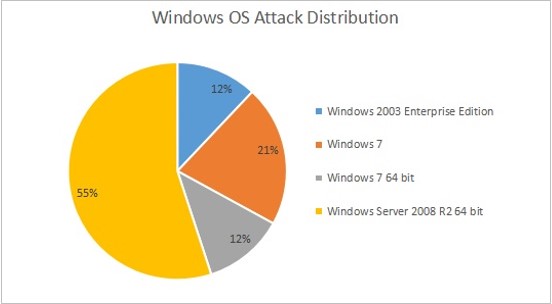
Fig. 1: OS-wise distribution of BlueKeep attacks blocked by Quick Heal in last 6 months
Considering the criticality of this vulnerability, it’s advised to patch it immediately. If applying patches is not an option for some reasons, users are advised to follow these best practices related to RDP:
- Disable RDP access from outside Organization/Company network.
- For machines hosted on cloud, allow RDP access to whitelisted IPs only.
Quick Heal blocks the attacks for this exploit with the following IPS Signatures:
- Remote Desktop Services RCE Vulnerability CVE-2019-0708
- RDP/CVE-2019-0708.UN!SP.34961



