2017 was the year of ransomware and cryptocurrency miners but we are still seeing infectors posing a prominent attack vector. However, old infectors still remain a significant threat to users.
In 2017, we observed a few old infector families making new versions of their old code, though no new prominent infector families were seen. This kept file infectors in action and made them a prevalent threat in 2017. With infector families like Sality, Virut, Slugin, Autorun and Ramnit gaining a slot in the top 100 malware families, file infectors contributed to 24% of Quick Heal’s malware detection statistics.
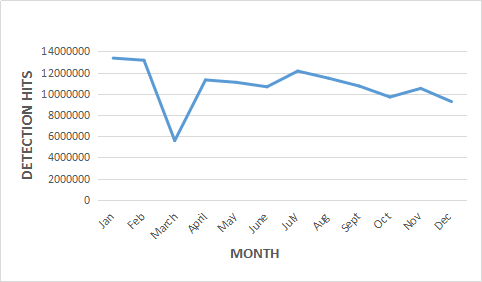
Below are the statistics of infector detection on Windows OS in 2017.
What are file infectors?
A file infector infects files present in the system by attaching itself to the file. It is dependent on the particular file types and platform and it needs to know how the various executables are executed in the Operating System so it is designed in such a way that these files must execute. The virus can spread in many ways, it must execute and replicate itself, it can modify the files or rename the files for spreading its infection.
Figure 2 displays different techniques of file infection. Using one of the given ways or combination of these, the dormant virus inserts a copy of itself into files that were previously uninfected.
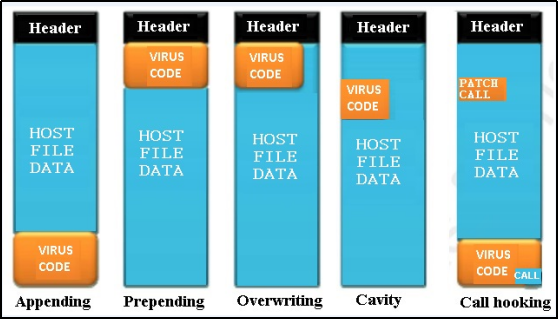
Malware writers can insert a virus code at the end of a host file which is called appending virus or at the starting which is called prepending virus. The malware can also hook call and send control to the virus code for execution and then it will eventually run the original code by fixing the code in memory and give control back to the clean code. This method is called call hooking.
Although the methods of infection are limited, malware authors have been consistently changing the obfuscators to evade static signature-based detections and integrating anti-VM techniques to bypass behavior-based detections.
Here are a few prominent infectors observed by Quick Heal Security Labs in 2017.
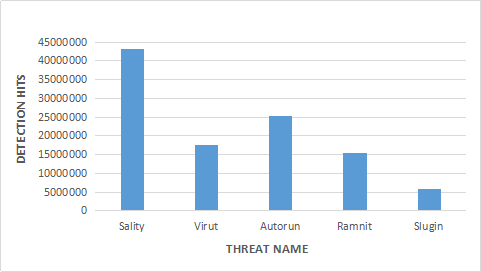
Sality – uses nasty techniques
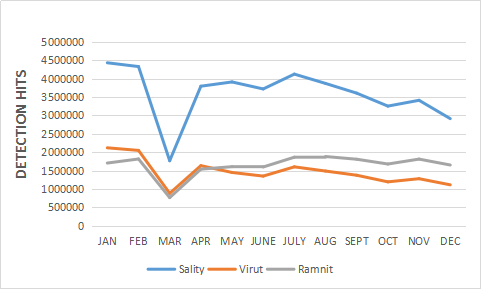
Sality is not a new family but Quick Heal Security Labs still received its variants. It is among the top 10 malware in 2017. It is a high-level polymorphic virus that continuously modifies its code to evade detection. A polymorphic virus is self-encrypting in nature which changes its appearance with different files. It infects ‘.exe’ and ‘.scr’ extension files. It patches few bytes at the entry point and virus code in the last section of original file. From entry point, the control thus passes to the last section where it adds the malware code. We have seen consistent detection for this malware throughout 2017 as shown in figure 4.
Virut – a notorious modifier
Another infector found in the wild is Virut. Virut family consists of polymorphic, memory-resident, and appending file infectors that also have entry point obscuring capabilities. This malware patches the call of a clean file and sends the control to a malware code present in the last section of the file. The malware code is highly obfuscated which uses a new set of instructions which are difficult to emulate. Figure 4 shows the Virut detection statistics in 2017.
Ramnit – versatile in nature
Ramnit has become much sophisticated with time by including a number of malicious activities. Ramnit infects PE and HTML files. Infection for PE files and HTML files are different. For PE file, it adds one more section with an executable permission. The name of the sections should be ‘.text’ or ‘.rmnet’. It sets an entry point of the file in a newly added section. This section contains encrypted data which is to be decrypted and dropped on the disk and then the control is transferred back to the original entry point of the file. For HTML files, it injects VBScript with the purpose of writing the Ramnit installer. Its internal operation, architecture & encryption algorithms remained the same. Malware authors update wrapper and packers to evade detections. Figure 4 shows its occurrence throughout 2017.
Also, a few families like Pioneer and Neshta made upgradations in their binaries.
Pioneer was observed keeping its complete malicious code in a relocation table. Relocation table helps the OS to load a file when an image is not loaded at a certain base address. Pioneer made use of this mechanism as a decryption routine by keeping its base address zero. At run time, the OS will apply the relocation to items specified in the relocation table thus decrypting the code and restoring the original malware. This avoids the use of a decryption procedure inside the virus, transferring the decryption duty to the OS instead and making the malware stealthy.
Neshta is updating its binaries using the latest available packers and protectors. It has also used different file types like DotNet, VB, etc. Using these for changing its mother file of infection, it evades the static detection signatures. Neshta overwrites the first 0xA200 bytes of a clean file and keeps these encrypted at end of the file.
File infectors mostly attack PE files and at times non-pe files too. In 2017, we observed malware families like Zombie, Sulpex, and Anomaly modifying non-pe files. Zombie and Sulpex modify non-pe files by encrypting them with a specific key, whereas Anomaly made changes by overwriting bytes of non-pe file thus corrupting them.
Cleaning of infected files still remains a challenge for AV vendors, because if something goes wrong during the cleaning process, there is always a risk of the computer or application becoming unstable. Also, removing all traces of infectors in an infected file and computer poses one more challenge with respect to the performance of AV.
Although an aged and slowed infection vector, with surprising infection mechanisms and increasing its target list, infectors have been able to persist over the years. As with its history, carving history but not becoming history, after being dormant in 2017, we may see a gust in infectors with another new notorious name in its category.
Seqrite with its advanced detection technology mechanism, has been consistently keeping its detection coverage at par in the virus category of AV Certification.
Subject Matter Experts
Amar Patil, Preksha Saxena | Quick Heal Security Labs




