How often do you store your important data in files? It’s very common, right? This data may be URLs, topics, personal data like contacts, email-ids, usernames of different portals and sometimes passwords too (though always recommended to not to do so). We very casually copy this data and paste it in respective applications. In the past, we have seen some spyware using this clipboard data. Upon hitting Ctrl+C, this data is stored on clipboard and malware just gathers data from clipboard and send it to the attacker. But, what if this data is altered during its use? It can lead to a huge loss if this data is very sensitive such as your bank details, financial information or cryptocurrency wallet addresses.
Cryptocurrency has been on the radar of malware authors from last few years and they are definitely making a profit out of it as they not losing focus on it. Any cryptocurrency account (wallet) is represented by some unique wallet address. These addresses are difficult to remember as they are a combination of numbers and letters with longer lengths. For all the crypto-transactions, these addresses are used. So, often we store these addresses in some text files in order to use whenever needed. Malware authors are exploiting this habit of copy-pasting to make a profit out of it.
We analyzed a new way of digital funds theft i.e. “Trojan.CBHAgent”. This Trojan monitors the Windows clipboard for cryptocurrency addresses being copied onto the clipboard. Once it detects any bitcoin address, it will be replaced by one of the bitcoin address from list maintained in the file. A user will not easily be able to identify address is different until he confirms it manually again.
Before looking into the working of the Trojan, we need to know what the clipboard is. Clipboard is a shared memory area that you can copy data into and copy data from. All applications have access to this clipboard, data can be easily transferred between applications. Clipboard is used by Windows while cutting, copying, or pasting data. Clipboard is supported with a set of functions that enable applications to transfer or exchange data. Windows provides APIs for managing clipboard.
GetClipboardData is used to fetch the current (copied) data on clipboard and
SetClipboardData is used for saving data on the clipboard (I.e. generally when Ctrl+C is pressed).
Analysis:
Trojan ‘Trojan.CBHAgent’ is using these Windows API’s to manipulate the clipboard data.

It is a dropped DLL on victims system that will be run using rundll32.exe, a DLL host, with below command line.
$> C:\WINDOWS\system32\rundll32.exe “C:\Documents and Settings\Administrator\Desktop\Sample\CBHAgent.dll”,includes_func_runnded
Here ‘includes_func_runnded’ is an exported function which performs the clipboard monitoring. Also, for preventing its analysis, the author checked whether it is being run in virtual machine or not. Trojan is also exported ‘detection_VMx’ function to use it as anti-VM check.
Looking at its file structure, it is found that the Trojan sample is packed with PECompact packer to make analysis more difficult. List of bitcoin addresses which are to be pasted, are present in resource of file as plain text. More than 2.3 million bitcoin addresses are listed out in the file. All these addresses are sorted so that it would help while searching the target bitcoin address.
This resulted the file size to 80 MB.
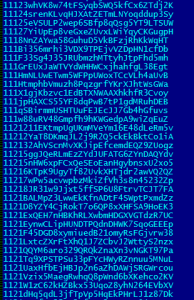
On execution, it starts monitoring clipboard data continuously and checks if there is any like bitcoin address. For validation, it uses regular expression. Once matched, it will be replaced with a address present in the list. The Trojan is not affecting any data other than bitcoin addresses.
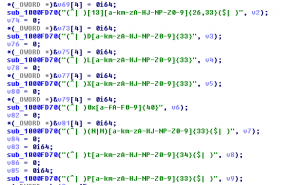
This malware runs in the background so users are not easily able to identify that system is infected by Trojan.CBHAgent. We strongly recommend you to double check bitcoin address while doing any bitcoin transaction. The trojan also ensures its persistence in the system by creating a copy in %TEMP% directory and adding its run entry in registry. It creates a mutex with name as ‘MODULE_DXDIAG_1’.
Quick Heal detects the Trojan as ‘Trojan.CBHAgent.S3076164’.
Indicator of compromise:
48b66dd02a336eb049a784b3fd1beb5312fb8c078b3729d49e92e3e986c98e91
Conclusion:
This malware would attract the other malware authors for exploiting clipboard. In recent future, similar attacks can be observed. So, we should always be careful about the activities which are most common in our day to day life. Malware authors are playing with mentality of the human being and making more sophisticated versions of their payload.
Other preventive measures that should be taken:
– Always use security software with the latest updates.
– Whenever possible, manual verification should be done to prevent the big loss.
– Install third party software as per your need only. Unwanted applications can be a source of malware.
– Operating system patches are applied on time and installed software are up-to-date.
– Avoid clicking on links and downloading attachments in emails from unknown sources.
Subject Matter Experts
Pandurang Terkar | Quick Heal Security Labs




