Ransomware authors keep experimenting with the development of payload in various dimensions. In the timeline of ransomware implementations, we have seen its evolution from a simple screen locker to multi-component model for file encryption, from novice approach to a sophisticated one. The Ransomware as a Tool has evolved in wild and one of them has been received in the Quick Heal lab. This sample is identified as LockerGoga and it is unique as it acts as a tool giving various options for performing encryption.
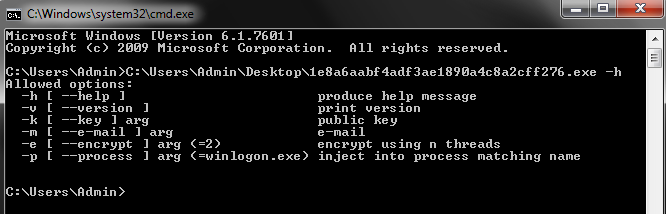
Like any standard command-line tool, LockerGoga Ransomware shows help information for reference. On execution with parameter -h, it shows options like “-v” for the print version of LockerGoga and “-m” [Email ID as an argument] parameter to specify email id of the attacker for payment, in case victim wants to decrypt encrypted files. The same email id is mentioned in ransom note to contact for price of decrypter.
LockerGoga uses Boost library for parsing command line arguments.
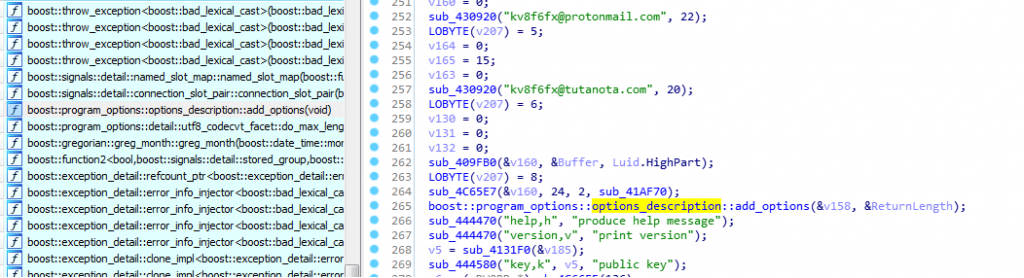
Last option in the command line tool “-p” allows to select the process in which malicious code needs to inject; if process name is not provided, then by default it will inject code into “winlogon.exe“.
The received sample contains four executable components inside it, such as
- encrypt32.dll
- encrypt64.dll
- {random_name}.exe (32 bit)
- {random_name}.exe (64 bit)
Upon execution, the malware drops dll component according to system architecture as mentioned above, at location %AppData%/Local/Temp
Then it will inject the shell code and RSA Public Key of 1024 bit to the process “winlogon.exe” or in the process specified as an argument. The injected shell code is used to load dropped encrypt**.dll with the help of ldrloaddll.
The encrypt**.dll has an export function “encryptStart”. This function contains code used to enumerate all drives and folders to generate a list of files present in it. All files list is stored in file C:\cl.log.
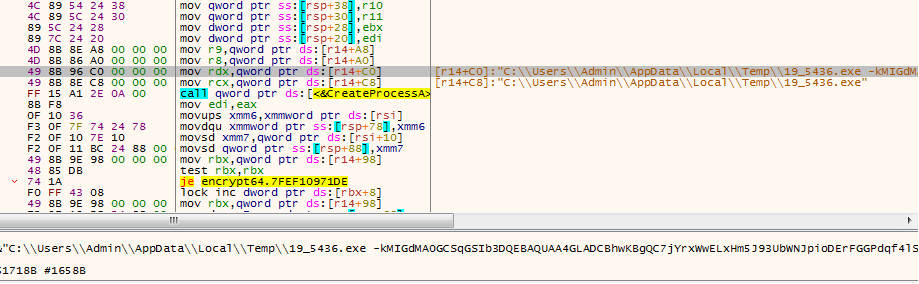
For every single file listed in C:\cl.log, it drops an executable file with {random name}.exe in %AppData%/Local/Temp or C:\Windows\Temp depending upon 64 or 32 bit architecture of the system and invoke that {random_named}.exe in a loop with -k{public key} {file_path(i.e. file to be encryp)} as the command line argument.
Unique thing about LockerGoga Ransomware is that for every single file, it creates a new process, encrypts that file and terminates that process. By this technique, it might evade anti-ransomware product. While encryption happens, it consumes most of the CPU resources almost up to 90%.
After finishing the encryption of each file, it writes file name in C:\cl.log.
Encryption Process:
It uses two encryption algorithms, AES-128bit for file content encryption and RSA-1024 bit to encrypt AES key used for file content encryption.
Generation of AES Key:
Initially, it used “CryptGenRandom” API to generate the random seed of 32(20h) bytes. Then it used another 32(20h) byte from resource section to make a key stack of 40h byte, which was used for generating AES key.
Along with Boost library, LockerGoga Implements Crypto++ Library for encryption process which makes reversing the sample very difficult.
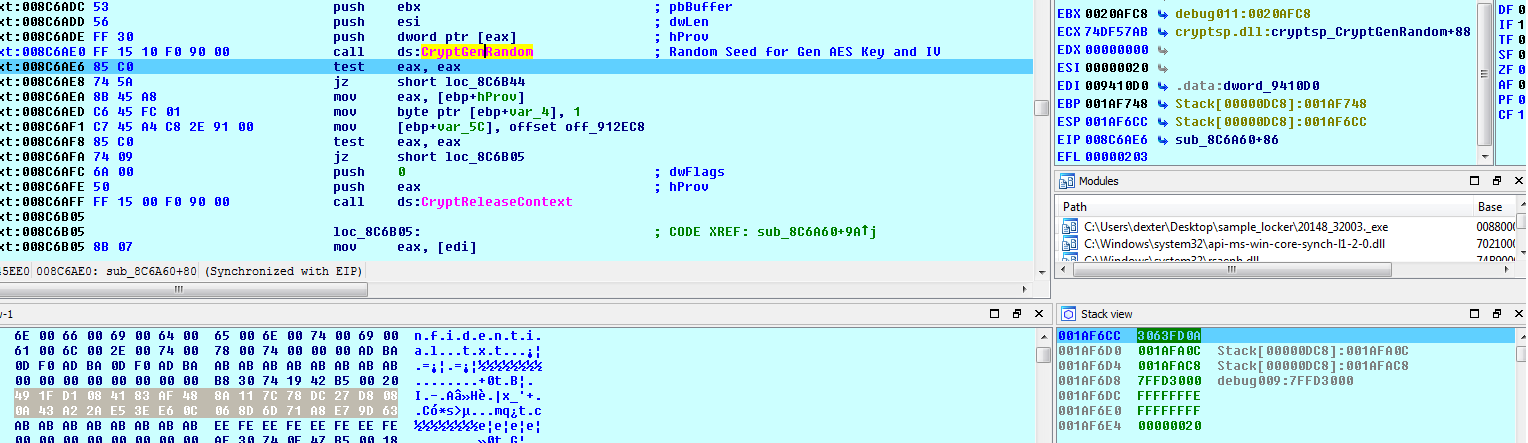
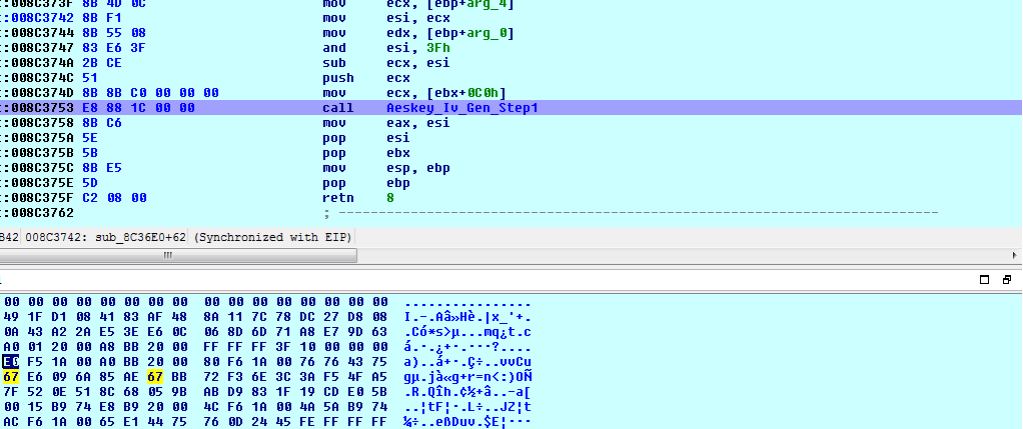
Implementation of Crypto++ library enables AES new instruction set (AES-NI) which were introduced by Intel in 2009.
AESKEYGENASSIST and AESENC instruction are used to implement AES encryption,
AESKEYGENASSIST is used for round key expansion and AESENC is used to perform one round encryption of AES.
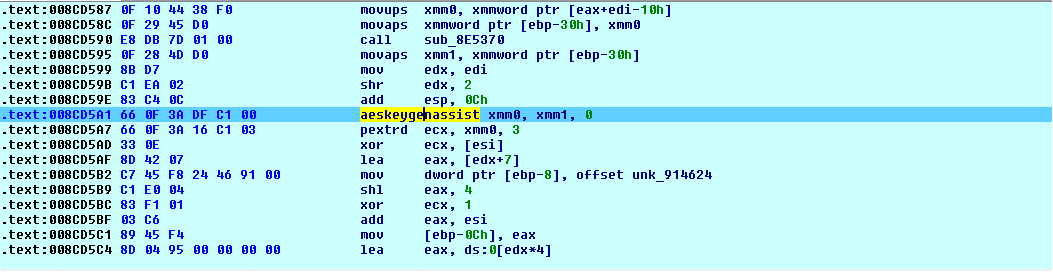
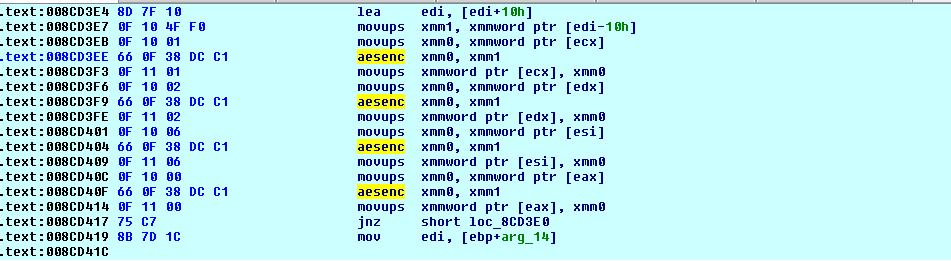
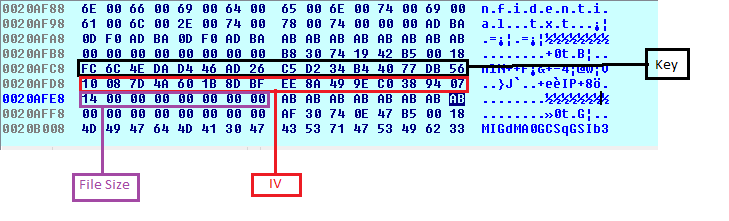
After all above operations, it generates 32-byte data from which 16 bytes are used as Key and other 16 bytes as an Initialization Vector (IV).
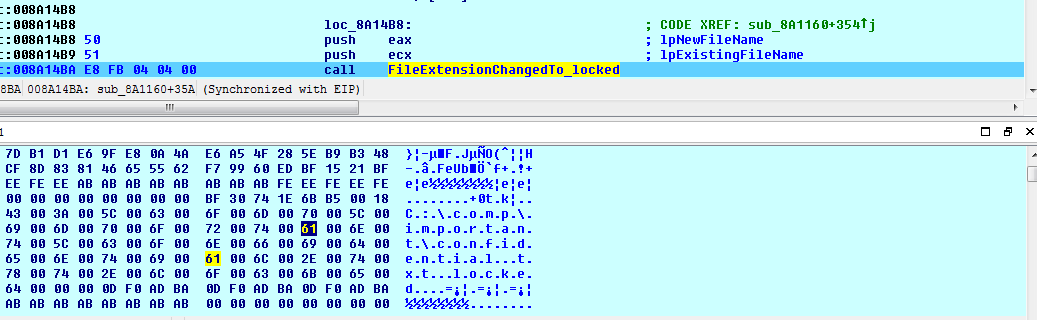
Malware changes file extension to .locked before encrypting it.
![]()
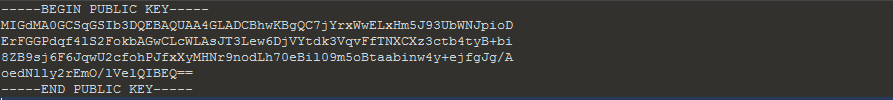
The public key used in the encryption is in PEM format
Convert them into Microsoft Blob format shown below.
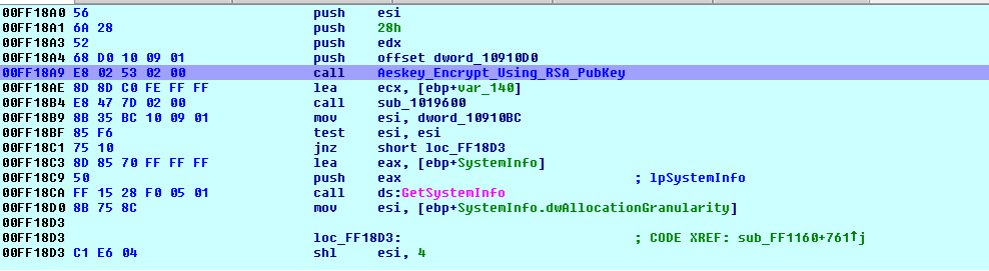
Along with Key (10h), IV (10h) and 8h bytes used as file size (i.e. file to be encrypted) are encrypted by RSA-1024 bit with ‘MGF1 (SHA-1)’ (i.e. mask generation function for the OAEP padding scheme) and appended to the end of the file.
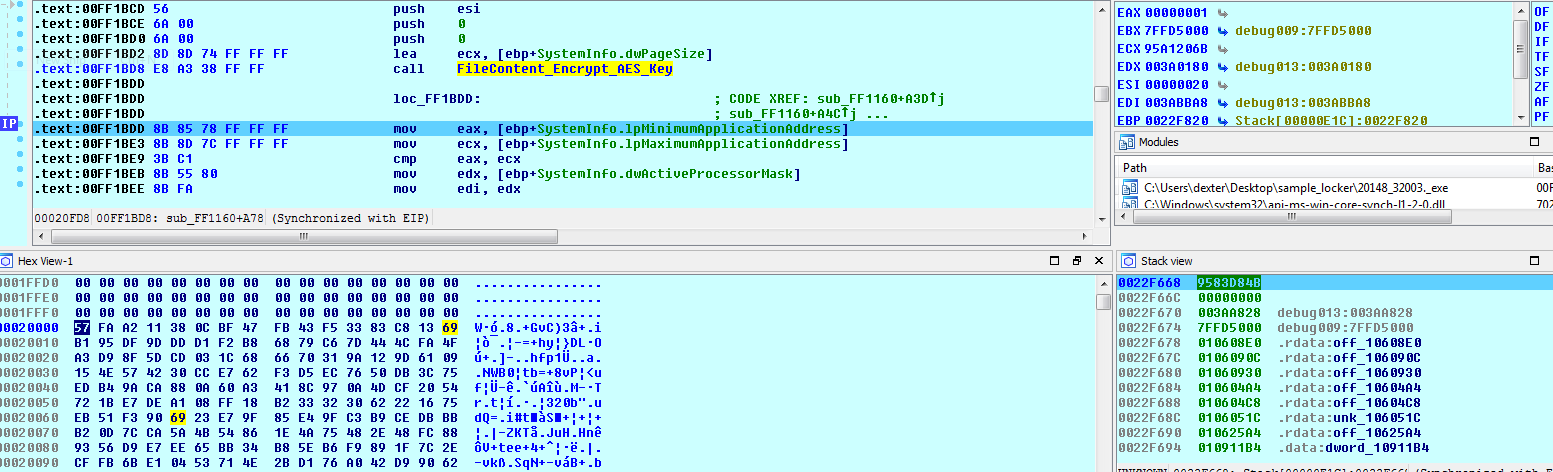
After that it encrypts the file content with AES key and IV in CTR mode with a key length of 128 bits.
Conclusion:
LockerGoga has shown a unique and rare mechanism for encrypting files by creating one master and multiple slave process.
Key features:
Use Boost Library for handling complex mathematical computation.
Instead of using Microsoft Crypto API for encryption, implemented the Crypto++ library (Boost Software License)
IoCs:
1E8A6AABF4ADF3AE1890A4C8A2CFF276 – LockerGoga
91976DBD489FEAE2D8719545C8DE304A- encrypt32.dll
174E3D9C7B0380DD7576187C715C4681-encrypt64.dll
E9E6EBC6A0D5183FC8E66472B3419F1E-{random_name}.exe-64 bit
A52F26575556D3C4ECCD3B51265CB4E6 – {random_name}.exe-32 bit
Subject Matter Expert:
Goutam Tripathy, Rahul Sharma, Manisha Prajapati | Quick Heal Security Labs




