Our previous blog explored an XSS vulnerability within the Bookly plugin (WordPress Online Booking and Scheduling Plugin – Bookly). Today, we will delve into another XSS vulnerability that came to light during our research on the same plugin.
Our team discovered this vulnerability in March 2023. Following its discovery, we promptly initiated responsible disclosure procedures to ensure the vulnerability would be addressed promptly. The assigned CVE identifier for this vulnerability is CVE-2023-1159, and it was successfully patched in May 2023.
In this blog post, we will comprehensively analyze the root cause behind the vulnerability found in the Bookly plugin. Additionally, we will examine the patch that was released to mitigate this issue effectively.
Analyzing CVE–2023-1159 – Authenticated (Admin+) Stored Cross-Site Scripting via Service Title:
Our research identified a vulnerability in the Bookly plugin related to the “Service title” field. This vulnerability exposes the plugin to stored cross-site scripting (XSS) attacks due to insufficient input sanitization measures. It is important to note that administrators can edit or set the title directly through the plugin interface.
Upon further investigation, we discovered that if a malicious title is set within the service, it will be rendered and executed in the client’s browser without their knowledge or consent when they access the said service. This execution can potentially enable remote code execution, which poses a substantial security risk.
To provide a more precise understanding, the following code snippet illustrates how the value of the “Service Title” field is set and read while creating a new service:
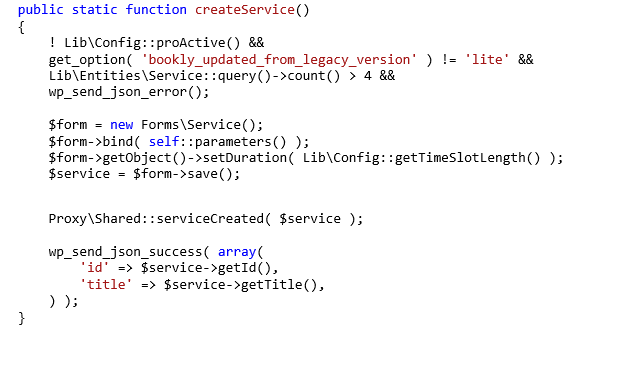
Fig1. createService method, which gets called when a new service is created.
‘createService’ in turn invokes the ‘parameters’ method.
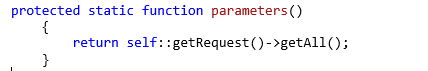
Fig2. shows the parameters method.
Within the ‘parameters’ method, there is a call to the ‘getRequest()’ function. This function is responsible for retrieving the entered values from the interface. Subsequently, these values are passed to the ‘createService’ method, where they are stored. However, it is crucial to highlight that no input sanitization occurs during this process, leaving the system vulnerable to potential security risks.
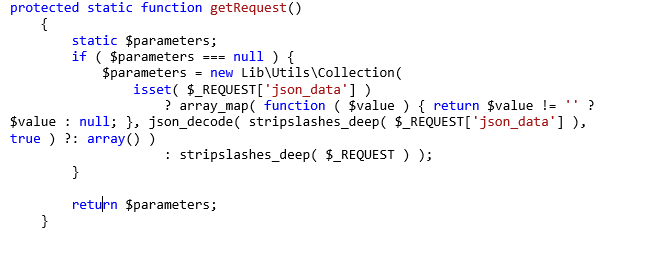
Fig3. shows the getRequest method.
Unveiling the Fix: Investigating the Patch
Upon examining the patch that resolves the vulnerability, we determined that the $parameters variable has undergone proper sanitization, effectively preventing potential security breaches within the program. This notable enhancement includes implementing the ‘unfiltered_html’ function and the ‘stripScripts’ method, which are crucial in sanitizing the $parameters and mitigating potential attacks.
By utilizing the ‘unfiltered_html’ function, the patch ensures that only authorized users with the necessary capability can submit unfiltered HTML content. This prevents the introduction of malicious scripts and significantly reduces the risk of cross-site scripting (XSS) attacks. The ‘stripScripts’ method further enhances the sanitization process by removing or neutralizing any embedded JavaScript code within $parameters.
Overall, this comprehensive approach to sanitization ensures that the $parameters variable is safe for usage throughout the codebase, minimizing the potential for security vulnerabilities and fortifying the overall security of the program.
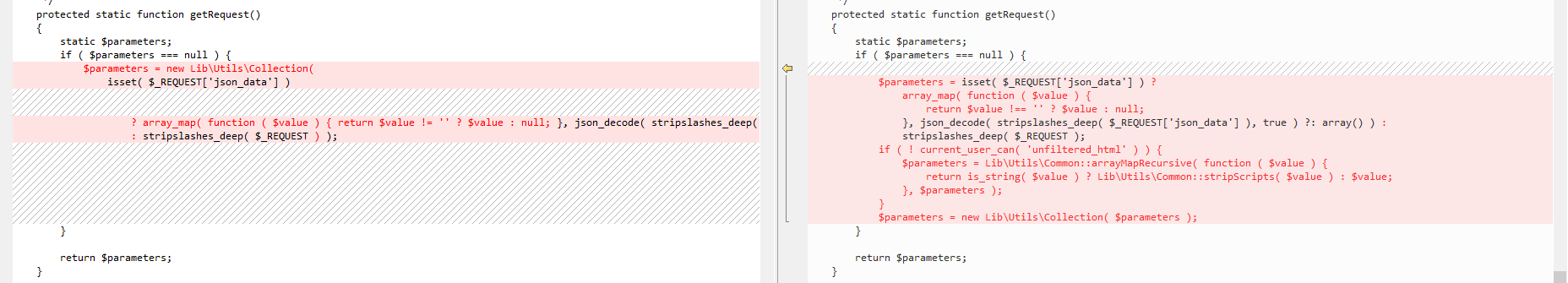
Fig 4. depicting the patch.
Conclusion
In this blog post, we examined a vulnerability discovered in the Bookly plugin, which enabled authenticated attackers to insert harmful scripts, posing a threat to users’ devices. Thankfully, this vulnerability is patched in version 21.8. We advise WordPress site owners to promptly update their installations to the latest plugin version, essential for mitigating potential attacks. Ensuring the timely application of updates and patches is crucial to maintaining a secure online presence. Additionally, when granting the ‘unfiltered_html’ capability to a user role, exercise caution and assign it only to trusted individuals who genuinely require it, considering the potential security implications of this capability.
All SEQRITE and Quick Heal customers are protected against any exploits targeting this vulnerability through the following signatures:
- HTTP/CVE-2023-1159!VK.47550
- HTTP/CVE-2023-1159!VK.47551
- HTTP/CVE-2023-1159!VK.47552
Co-author:
Anjali Rajkumar Raut




