Overview:
Over the last year or so, there has been tremendous growth in the number of ransomware attacks that have been spotted in the wild. Cybercriminals have effectively cracked this ‘business model’ and are generating a significant amount of money through this attack mechanism. What was once an attack technique that was aimed solely at susceptible individual users has now developed the ability to afflict advanced enterprise networks as well. Ransomware attacks are capable of causing significant system downtime, loss of critical data, Intellectual Property (IP) theft and more. In several industries, a ransomware attack is now considered on par with a significant data breach.
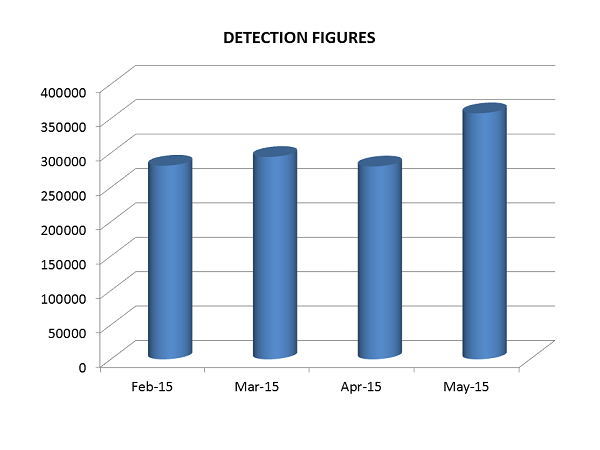 The above mentioned statistics are for the months of February, March, April and May 2015 and they represent a significant rise in the numbers that were reported for the preceding 6 months. This goes to highlight the rising risks of ransomware in the online world and how we need to take steps to prevent such infections.
The above mentioned statistics are for the months of February, March, April and May 2015 and they represent a significant rise in the numbers that were reported for the preceding 6 months. This goes to highlight the rising risks of ransomware in the online world and how we need to take steps to prevent such infections.
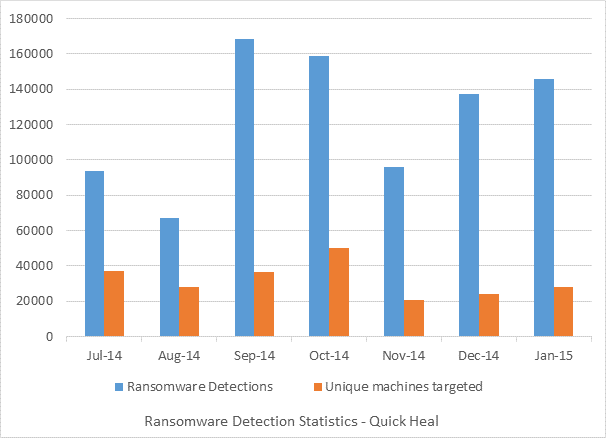
The chart above sheds light on the number of machines that are protected from ransomware through Quick Heal products and the number of ransomware detections that is actually found out. What this translates to is detection of around 100,000 ransomware incidents on approximately 30,000 machines. The ransomware detection rate thus roughly translates to around 3 incidents per machine.
When compared against other malware, ransomware is highly destructive in nature and these large numbers showcase how much user data is under risk and made unusable until a ransom is paid. Here we will discuss ransomware under the following broad sections:
- What is ransomware?
- Infection vectors
- Payment mechanisms
- Mitigation techniques
What is ransomware?
Ransomware is a type of malware that restricts access to or damages infected computer systems for the sole purpose of extorting money from victims. This money can be in the form of direct payments or via Bitcoins. Ransomware also has the capability to encrypt user files on a system and display threatening or incriminating messages on screen in order to demand money via online payment mechanisms. Ransomware can be broadly classified into the following two types:
Encryptor: In this case it encrypts all important files and asks for a ransom to decrypt the files.
Screen Locker: It entirely locks the infected system and prevents the usage of the system until a ransom is paid.
Computer users have several important documents, images, photos, source code etc. stored on their systems and as a result of this, ransomware variants ensure that they have the capability to encrypt all possible file types. The extensions that are culpable to attack by ransomware are listed below:
Some of the prevalent ransomware families that have been spotted in the wild are:
- Cryptorbit aka Critroni aka CTB-Locker
- Cryptolocker
- CryptoWall aka Crowti
- ZedoPoo
- TorrentLocker aka Teerac
- PornoBlocker
- PornoAsset
- Foreign
- Genasom
- Urausy
- Reveton
- Blocker
Here are some screenshots of a few ransomware families:
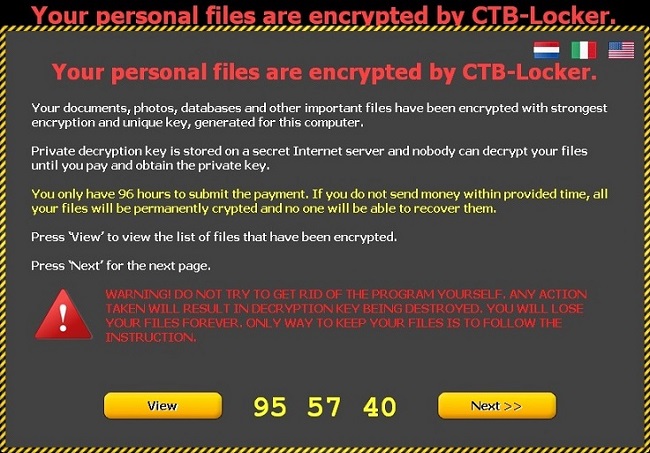
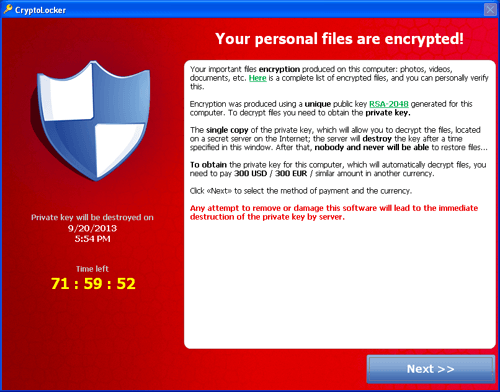
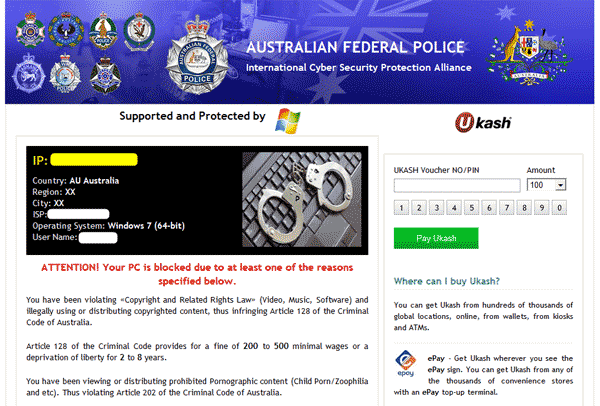
Top ransomware in 2015
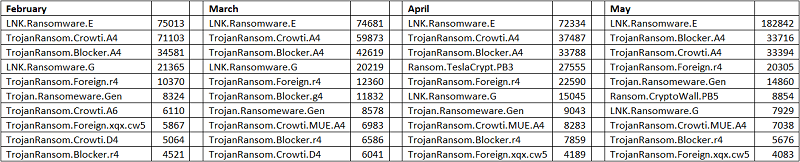
The table above shows the most common ransomware strains that were detected in the last few months of 2015. Most of these common strains reached machines in the form of malicious emails, further highlighting the need for users to be cautious about what emails they open and what attachments they actually download on their machines.
Infection vectors
Spam emails are a major contributor to spreading ransomware across the globe. This infection vector usually comes with attachments with two level .zip files and .scr file. However, recently these attachments have been spotted with .cab extensions as well, and this is highlighted in the below image.
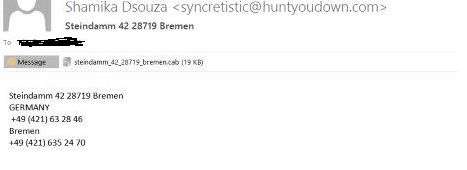
The malicious file inside this attachment is a downloader which installs and executes ransomware on the machine.
Some other malware families which act as a downloader for ransomware are listed below:
- Upatre
- Cutwail
- Zbot
- Kuluoz
- Gamarue
- Dalexis
Payment mechanisms
Ransomware samples commonly use various payment mechanisms that are mentioned below in order to collect ransom:
- SMSs or phone calls to premium-rate numbers
- Prepaid electronic payment – Ukash, MoneyPack etc.
- Bitcoins – virtual currency which makes it difficult to trace the actual recipient of the money
Ransomware creators have also started hosting dedicated payment gateways running behind TOR networks for anonymity, as seen in the case of TorrentLocker.
Quick Heal strongly advises users to not pay ransom amounts that are demanded. Making such a payment encourages this menace and moreover, it does not provide any guarantee that decryption and data recovery will be provided by the attacker.
Mitigation techniques
We also recommend the following security measures to remain protected against ransomware attacks:
- Ensure you are using the latest version of Quick Heal and it is updated with the latest virus databases.
- Quick Heal provides multiple lines of defense against malware and you need to ensure Virus Protection, DNAScan, Advanced Behavior Detection System and Email Protection are all enabled. We strongly recommend that you configure your Quick Heal security product for maximum protection.
- Since Quick Heal makes use of behavior based detection, we recommend that our users stay aware about any Behavior Based Detection (BDS) prompts that they receive. There have been cases where the BDS has detected a ransomware but a user has allowed execution without actually reading the prompt anyway.
Email Protection: Since ransomware commonly enters systems as spam emails with multiple levels of compressed .zip or .cab archives, or at times links to other downloadable files, you should make sure email protection is ON. Quick Heal Email Protection actively blocks such malicious and suspicious attachments.
Browser Sandbox is a great tool against malware using the Internet as infection vectors. Please enable Browser Sandbox from the Quick Heal dashboard & Internet and Network Settings. Alternatively, you can use the “Quick Heal Secure Browse” feature by launching it from your desktop while you are checking emails or accessing the Internet. The feature creates a secure layer around the OS to avoid tampering that can be carried out by malware.
Advanced Behavior Detection System is a proactive detection-based tool that takes into account the behavior of an application. If the application under suspicion is not installed by you, it is recommended to block activity of this application by selecting the ‘BLOCK’ action.
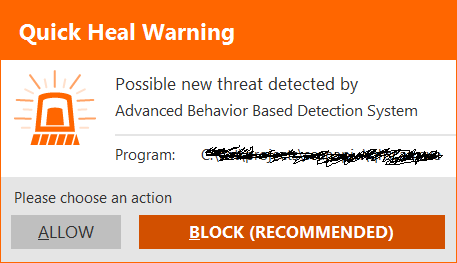
External Drives and Devices: Enable Autorun Protection and scan USB drives or external hard drives before copying any files from them.
Periodically, scan the system using AntiMalware (Quick Heal dashboard >> Tools >> Launch AntiMalware) which detects Adware, pop-ups and potentially unwanted applications (PUAs). It removes the risk of downloading malware through “Malvertising”.
Applying important software updates and patches
Ensure that Windows Update is enabled to automatically download and apply regular security updates. Also ensure that your system has the latest Windows security patches installed. Also apply updates for important software which is regularly targeted, such as:
- The operating system on your machine
- Microsoft Office – Office 2003, 2005 and 2008 with patches are targeted with vulnerable RTF CVE-2012-0158 and CVE-2010-3333
- Java
- Adobe Acrobat Reader
- Web browsers like Internet Explorer, Chrome, Firefox, Opera etc.
- Adobe Reader and Flash Player
Regular backup of important data
It is very important to understand the need for data backup policies for all your important data. It is highly recommended that you periodically backup your important data using the right combination of online and offline backups. Do not keep offline backups connected to your system as this data could be encrypted in case of an infection. Users should also ensure that critical and confidential data needs to be identified so that an effective data backup and recovery process can be planned for.
Follow best security practices
- Do not open and execute attachments received from unknown senders. Cybercriminals use ‘Social Engineering’ techniques to allure users to open attachments or to click on links containing malware.
- Keep strong passwords for login accounts and network shares.
- Avoid downloading software from untrusted P2P or torrent sites. At times, they are Trojanized with malicious software.
- Do not download cracked software as they could propagate the added risk of opening a backdoor entry for malware into your system.



