Malspam email or malicious spam email is considered as one of the favorite malware delivery channels for attackers to deliver their malware to their targeted victims. Attackers also run spam email campaigns to distribute their malware to a large number of users.
For attackers to succeed, two things are important – first is to get through the installed security product’s spam email filters and the secondly, the attachment should be opened by the user. To accomplish the second task, attackers use different social engineering tactics to make their malicious email look as legitimate as possible in order to trick users into opening such attachments.
About the Blank Slant Malspam Campaign
Since March 2017 we have been observing this campaign where the attacker has used emails leaving the body blank and subject line blank or unclear; hence the name ‘Blank Slate’. We found the sender’s email ID to be spoofed. Users are receiving emails with attachments only. Due to the absence of these fields, other than looking for an attachment, there is no way for the user to understand what the email is about. This tricks the user into opening the malicious attachments out of curiosity and this triggers an infection. A typical malspam used in the Blank Slate Campaign looks like the below figure.
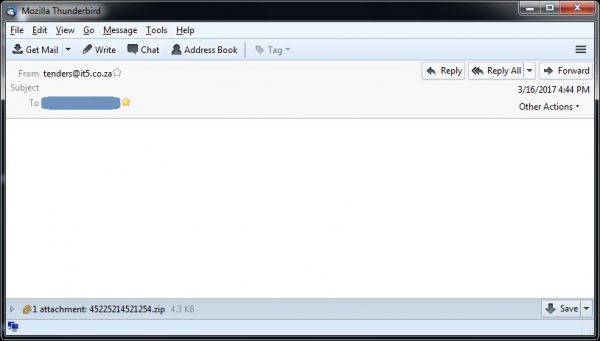
Fig 1: Blank Slate Email
Infection Routine:
Attachments of these email campaigns contain a nested zip file – a zip file inside a zip file. Inside the second zip file, the actual malware downloader is placed. For now, we have observed that either a JavaScript (.js) file or Microsoft Word Document (.doc) file is delivered via this malspam. The Blank Slate Campaign follows the below infection routine.
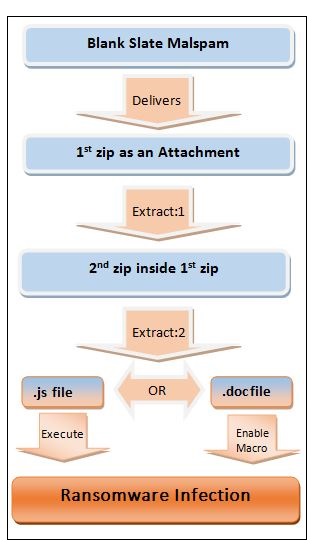 Fig 2: Blank Slate Infection Routine
Fig 2: Blank Slate Infection Routine
The final infection in both the cases (JavaScript or Word) was observed to be a variant of a ransomware. In some instances, doc files also were observed to be trying to exploit CVE-2017-0199 on MS-Office vulnerable systems.
Blank Slate Delivering Ransomware Variants
Cerber Ransomware
The Blank Slate Campaign was first observed in March 2017 and was used further to spread Cerber Ransomware for a long period of time. The spam email used in this particular campaign is the one shown in fig 1. The zip attachment in the spam email contained another zip file with the name “45214_ZIP.zip’. This file contained an actual malware downloader with the name 44582.js. When the user clicks on this .js file, it automatically downloads and executes the Cerber Ransomware. This ransomware was getting downloaded from a domain whose name ends with “.top”. Cerber has been one of the most dominating ransomware families for the last 2 years. After successful encryption, this variant appends the .aeac extension to the encrypted files.
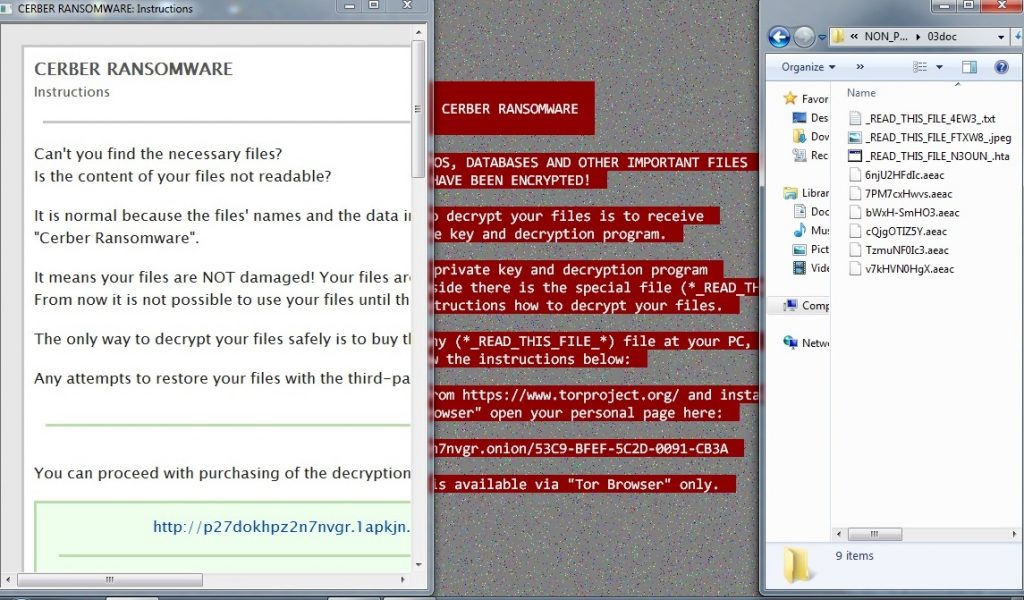
Fig 3: Cerber infected System with Ransom Note and Encrypted Files
Some other instances of spam emails were also observed where doc files were getting delivered. These files were trying to exploit CVE-2017-0199 that downloads and executes malware on the victim’s computer.
Aleta – a variant of BTCWare Ransomware
In the last week of July 2017, the Aleta variant of BTCWare ransomware was getting delivered via the Blank Slate Campaign. Once inside a computer, it encrypts its data and appends “.aleta” to the encrypted files. We also observed that the Aleta variant using RDP (Remote Desktop Protocol) brute-forcing attack to infect the victim. In both the cases, its encryption activity remains the same irrespective of the change in its infection vector.
Globeimposter Ransomware also used Blank Slate
Globeimposter Ransomware has been active in the wild since last month. It appends different extensions like .HappyDayzz, .707, .700, .GOTHAM, and .crypt to the encrypted files. This ransomware is delivered to the users via malicious spam emails.
In the case of the “.crypt” variant, it has been observed that the ransomware is delivered using the Blank Slate Campaign via .js files contained in nested zip files. Once encryption is complete, it drops the below ransom note file with the name “!back_files!.html”, containing instructions on how to pay the ransom to get the decryption keys.
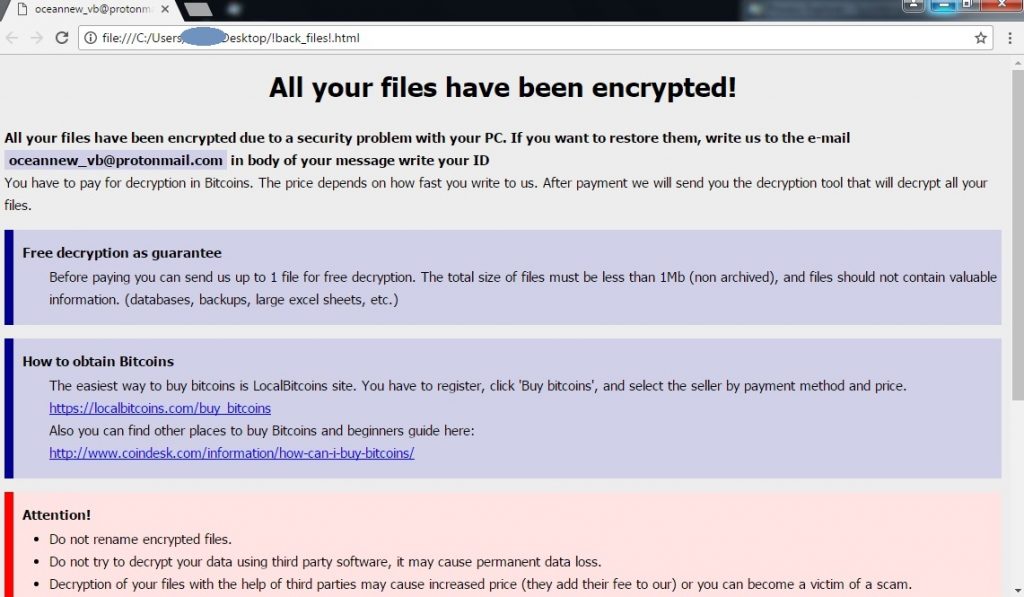
Fig 4: globimposter Ransom Note
Seqrite Endpoint Security Detection
Seqrite Endpoint Security’s Email Protection successfully detects and blocks this campaign at its initial level.
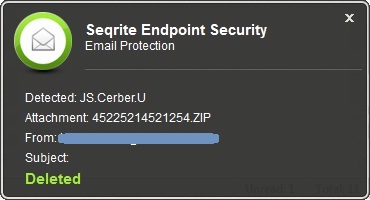
Fig 5: Seqrite Endpoint Security’s email protection detects Blank Slate Campaign
Stay away from ransomware with these security tips
- Do not download attachments that arrive in emails from unwanted or unexpected sources. Even if such emails seem to be from a known source, it is better to call up the sender and verify them first.
- If you get an email that seems unclear or strange, do not let your curiosity get the better of you. Do not respond to the email.
- Back up your files on a regular basis. Remember to disconnect the Internet while you are backing up on an external hard drive. Unplug the drive before you go online again. Several free and paid Cloud backup services available on the market that can take data backup periodically.
- Provide read/write privileges to network shares only when required. Try not to keep open shares as they are likely to fall prey to encryption if there is a ransomware infection.
- Use an antivirus software that gives multilayered protection against infected emails, malicious websites, and stop infections that can spread through USB drives. Keep the software up-to-date.
- Apply recommended security updates for your computer’s Operating System and all other programs such as Adobe, Java, Internet browsers, etc.
Acknowledgment
Subject Matter Expert
- Prashil Moon | Quick Heal Security Labs




