Typically, a ransomware will demand money or cryptocurrency after it has locked down your computer or phone or encrypted its data. But, Quick Heal Security Labs has spotted an Android ransomware that demands iTunes gift cards after it locks down the infected device. These gift cards can be sold on auction sites, social media or on the dark web.
Infection vector
Your Android device can get infected with this ransomware if you download a malicious app (that goes by the name ‘Porn Hub’) on third-party app stores or by receiving the app via electronic transfer mediums (Bluetooth, emails, file sharing sites, etc.)
Analysis of Porn Hub app ransomware
AppName: Porn Hub
Package name: com.pornhub_tools
MD5: 9fadc90562ce6e275eb6db8e6ca6ddad
Size: 39KB
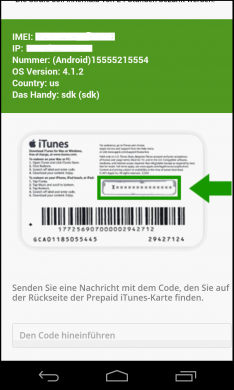
After the ransomware locks down your device, it displays a ransom note where it demands a ransom of an iTunes gifts card worth $200 as a penalty for watching child pornography. An URL is displayed in the ransom note (fig 1). This happens if your device is connected to the Internet.
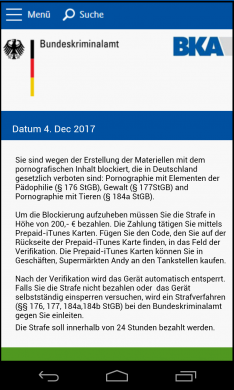
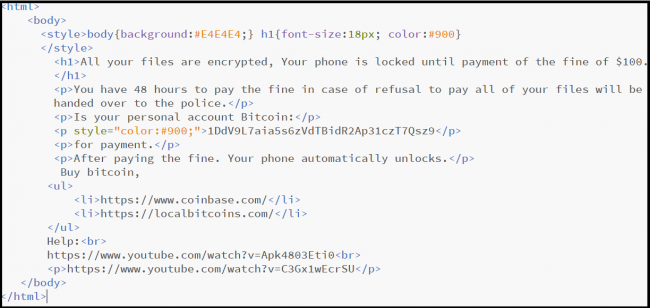
If your device is not connected to the Internet, the ransom note displays a different message. In this one, it says that all your files have been encrypted and that you must pay a ransom of $100 worth Bitcoins in order to unlock the device and decrypt the data (fig 2).
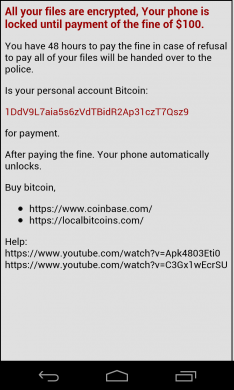
In our analysis, however, we found no instances where the infected device’s data is encrypted by this ransomware. Moreover, the malicious app (‘Porn Hub’) does not have any encryption code. This means you can retrieve your personal information by connecting the device to your PC.
Technical Analysis
When we tried opening the malicious app, it asked us to activate the Device Administrator rights. We selected ‘cancel’ but the app kept repeating the same activity until we selected the ‘activate’ option.
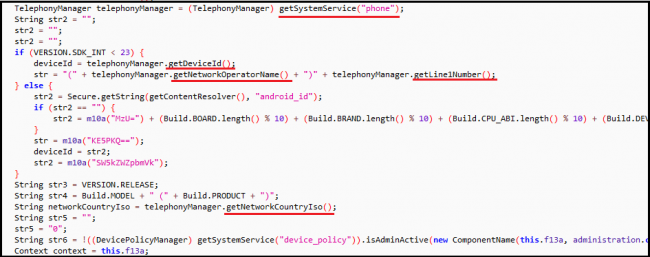
Once activated, the app checked if the device is connected to the Internet. When the device was online, the app collected device data such as device ID and sim operator. This data was sent to a certain URL (HTTP://*******.w*n//private/tuk_tuk.php) which loads the webpage demanding the iTunes gift card (fig 1). And when the device was offline, the app loaded an HTML page demanding Bitcoins (fig 2).
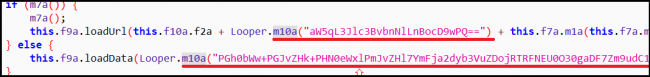
Here, the URL and HTML page content is encrypted using Base64. The Base64 encoded strings are decoded as shown in fig 4.
Analysis of fake Dropbox app ransomware
AppName: Dropbox
Package name: com.example.testlock
MD5: 17bc088027d2f3f71a74beed3a9c715
Size: 415KB
Quick Heal Security Labs found another malicious app hiding a ransomware which demands iTunes gift cards as a ransom. This app uses the icon of Dropbox (a famous a file hosting service). When we opened this app, it asked us to activate the Device Administrator rights (fig 6), just like the app we discussed earlier.
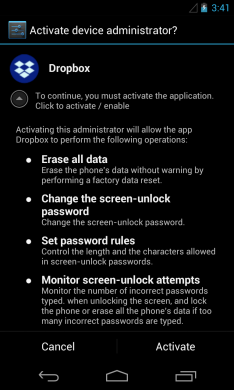
Once activated, the ransomware displays a ransom note claiming that the device has been locked by the Federal Bureau of Investigation (FBI) as a penalty for watching child pornography. To unlock the device, an iTunes gift card worth $25 has to be paid within 72 hours (fig 7).

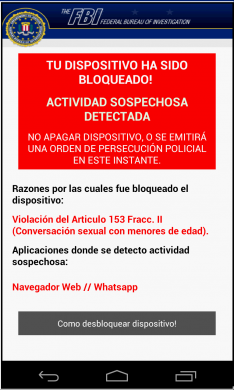
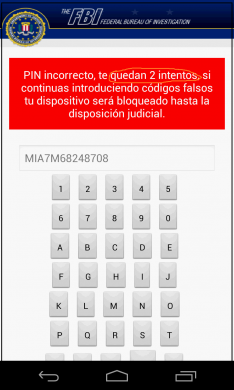
The ransom note asks the user to enter an iTunes gift card code of the demanded value. If the user enters a wrong code, a message is displayed saying that the user is now left only with 2 attempts after which the device will be locked permanently (fig 8).
In our analysis, however, we found that the warning is fake and only shown to threaten the user into paying up the ransom.
Seqrite Detection
Seqrite successfully detects both these ransomware as Android.Locker.Aa54f and Android.Locker.Aa550.
It is strongly recommended not to pay any ransom because there is no guarantee that you will get your files back or have your device unlocked even after paying the ransom.
How to stay safe from Android ransomware
- Before downloading any app (even from Google Play), verify its source. Check the developer’s website and reviews on the app.
- Avoid downloading apps from third-party app stores. Most malware-infected apps are found on these stores. Download apps only from official app stores such as Google Play.
- Always keep ‘Unknown Sources’ disabled. Enabling this option allows installation of apps from unknown sources (third-party). On your device, go to Settings > Security > check for Unknown Sources > Disable it
- Install a reliable mobile security app on your phone that can block fake, suspicious and harmful apps.
Subject Matter Expert
Rupali Parate | Quick Heal Security Labs