The recent Bad Rabbit ransomware outbreak is currently making headlines. This post outlines the analysis of the ransomware by Quick Heal Security Labs.
According to our telemetry, we have not seen any Bad Rabbit ransomware infection on our customer’s machines so far.
Propagation technique
Bad Rabbit is distributed via a drive-by-download attack from the below URL
hxxp://1dnscontrol[.]com/flash_install.php
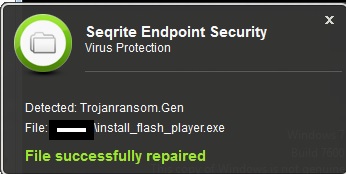
The payload is pretending to be a bogus Adobe Flash Player update named as “install_flash_player.exe”. The ransomware escalates itself to the administrative privilege using UAC prompt. Further, it drops ‘C:\Windows\infpub.dat’ which is actually a DLL file executed through ‘rundll32.exe’ as seen in the execution flow below.
Execution flow
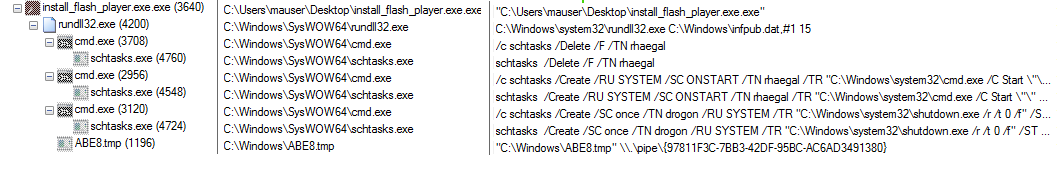
Dropped artifacts
Bad Rabbit ransomware drops multiple artifacts which are named after the dragons in the popular TV series called Game of Thrones.
- C:\Windows\infpub.dat
- C:\Windows\System32\Tasks\drogon
- C:\Windows\System32\Tasks\rhaegal
- C:\Windows\cscc.dat
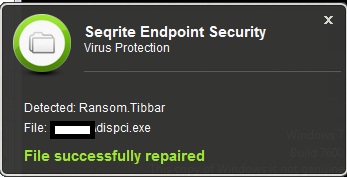
- C:\Windows\dispci.exe
Below is the screenshot of the code from the ransomware to use ‘rundll32.exe’ to execute ‘infpub.dat’.
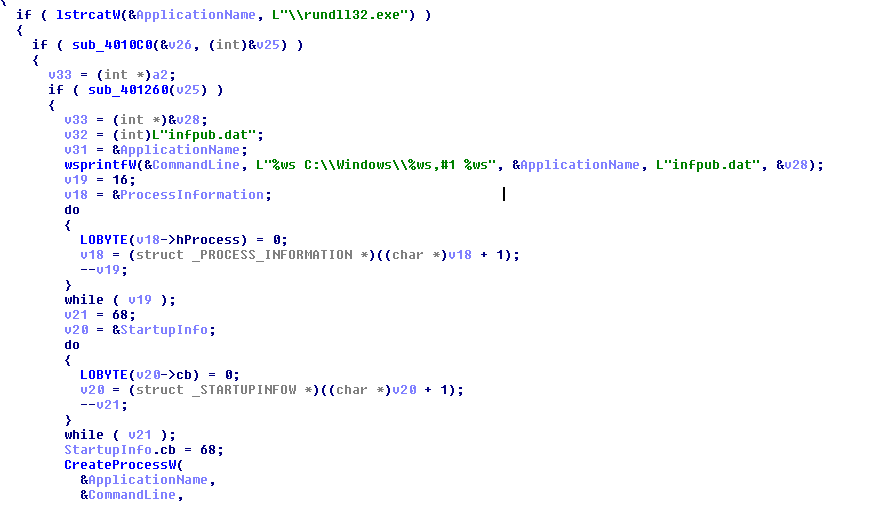
The ‘infpub.dat’ drops a malicious executable ‘dispci.exe’ at ‘C:\Windows’ which is responsible for Disk Encryption.
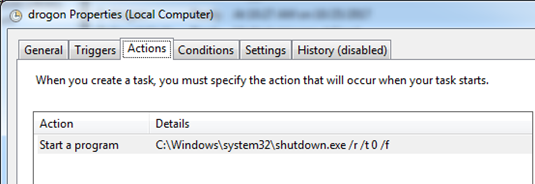
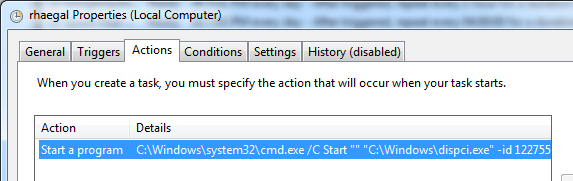
The ‘infpub.dat’ creates two tasks with names ‘drogon’ which is used to force restart the system and ‘rhaegal’ which is used to start a program at startup.
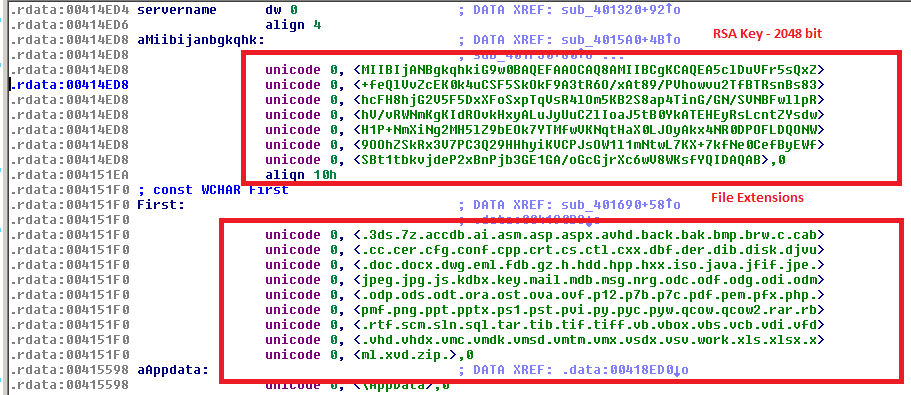
Infpub.dat is also responsible for file encryption using a shared public RSA-2048 key of the attacker for the list of file extensions as seen below.
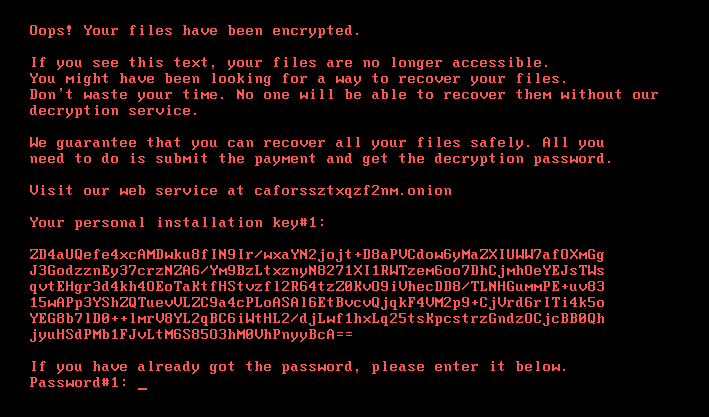
The dropped file ‘dispci.exe’ uses version information from a genuine DiskCryptor utility which is responsible for MBR infection which stops the boot-up process of the affected system until the ransom is paid as shown in the image below.
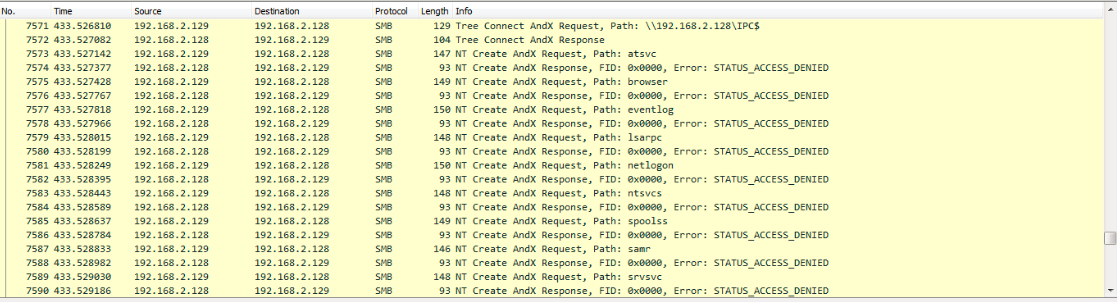
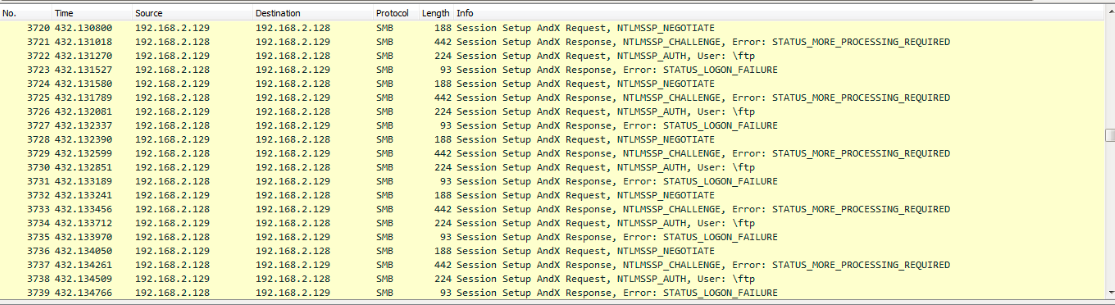
How it spreads in the network
The ‘infpub.dat’ tries to brute-forces login credentials using hard-coded credentials and also uses Mimikatz module to extract NTLM credentials from the system memory. These credentials are used to access other network workstations and server on the same network via SMB and WebDAV.
Similarities between Bad Rabbit ransomware and NotPetya ransomware
- Drops DLL files in Windows folder with ‘.dat’ extension and executes it using ‘rundll32.exe’ with ordinal 1 (#1).
- Use of ‘MimiKatz’ module for extraction of NTLM credentials
- Uses schedule task to restart system using ‘shutdown.exe’
- Displays a similar ransom note after MBR infection
- Uses WMI and SMB for spreading across network
Although both the ransomware share quite a lot of similarities, Bad Rabbit is not a wiper.
Indicators of compromise
| SHA256 | Filename |
| 630325cac09ac3fab908f903e3b00d0dadd5fdaa0875ed8496fcbb97a558d0da | install_flash_player.exe |
| 8ebc97e05c8e1073bda2efb6f4d00ad7e789260afa2c276f0c72740b838a0a93 | dispci.exe |
| 579fd8a0385482fb4c789561a30b09f25671e86422f40ef5cca2036b28f99648 | infpub.dat |
Malicious URLs
- https://1dnscontrol[.]com
- https://1dnscontrol[.]com/flash_install.php
Seqrite Detection
- Trojanransom.Gen
- Ransom.Tibbar
- Ransom.BadRabbit.A5
- Ransom.BadRabbit.B5
- Ransom.BadRabbit.C5
- Ransom.Badrabbit.PB5
How to stay safe
- Never download software from pop-up ads or websites that don’t belong to the software vendor (in this case – Adobe).
- Never click on links or download attachments that arrive in emails from unwanted, unknown or unexpected sources.
- Apply all recommended security updates for Operating System and programs like Adobe, JAVA, Web browsers, etc.
- Take regular backups of your important data in secure online and offline locations.
- Use a layered security software and keep it updated.
Subject Matter Experts
Anita Ladkat, Shantanu Vichare, Prashil Moon, Shriram Munde, Prakash Galande | Quick Heal Security Labs




