How Attackers Exploit BitLocker: Turning Legitimate Tools into Ransomware Weapons
Introduction
The ransomware landscape is evolving rapidly, with attackers constantly refining their techniques to outwit security defenses. One alarming trend is the weaponization of trusted tools like Microsoft’s BitLocker. Originally designed to safeguard sensitive data through encryption, BitLocker is now being exploited by cybercriminals to extort victims, turning a security asset into a significant threat.
In this blog, we’ll unpack how BitLocker is misused in ransomware schemes, what makes this tactic so dangerous, and how to defend your systems effectively.
What is BitLocker, and why are Cybercriminals Abusing It?
BitLocker is an encryption feature built into Windows operating systems, intended to protect data by encoding it into an inaccessible format unless a recovery key is provided. This functionality was designed to shield information from unauthorized access, especially in scenarios like device theft.
Unfortunately, attackers have discovered how to misuse this otherwise beneficial tool. By gaining administrative access, they leverage BitLocker to lock users out of their own systems or critical files, demanding a ransom in exchange for the recovery key. This strategy effectively uses trusted technology as a weapon, making detection and prevention especially challenging.
How BitLocker is used in Ransomware:
- Infiltrating the Network: Cybercriminals typically breach networks through common attack vectors like phishing scams, weak credentials, or exploiting unpatched vulnerabilities. Once inside, they elevate their access rights to secure full administrative control.
- Exploiting BitLocker Encryption: Armed with administrative access, the attackers activate BitLocker to encrypt essential files, directories, or even entire drives. This action locks legitimate users out of their data entirely.
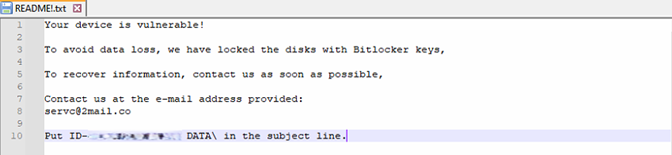
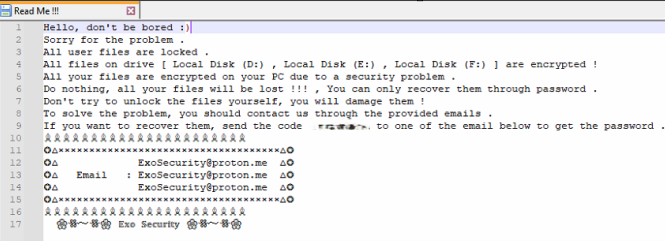
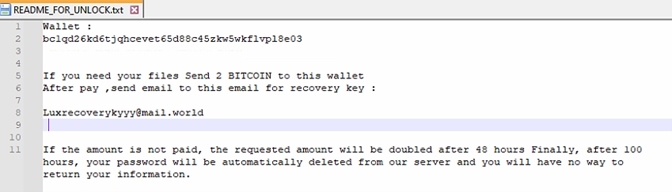
- Extorting Victims: The attackers then demand a ransom, promising the recovery key in return. Given BitLocker’s robust encryption, victims often face a tough choice: pay the ransom or risk permanently losing their data. Below are some examples of ransom notes left by attackers on affected systems and drives.
Ransom Note: A text file is created in affected directories, providing instructions for ransom payment and contact details.
Why This Attack Strategy Works So Well?
- Legitimate Tool Exploitation: By utilizing a built-in feature like BitLocker, attackers avoid using custom malicious software that could be flagged by conventional antivirus tools.
- Virtually Uncrackable Encryption: The strength of BitLocker’s encryption, designed to protect data from unauthorized access, ironically makes it an ideal tool for extortion when wielded maliciously.
- Reduced Detection Risk: Traditional ransomware often relies on custom executables, which are easier to detect. Using native tools minimizes the digital “footprint” of the attack, reducing the likelihood of being caught early.’
How to Safeguard Your Systems: Seqrite
Seqrite’s advanced security solutions are designed to thwart a variety of ransomware techniques, including those leveraging legitimate tools. Here’s how you can proactively protect your systems:
- Restrict Administrative Privileges: Limit admin rights to only those who genuinely need them. By minimizing access, even if attackers breach your system, they’ll face hurdles in deploying ransomware tactics that require admin-level permissions.
- Adopt Multi-Factor Authentication (MFA): Strengthen user accounts with an additional layer of verification to prevent unauthorized access, even if passwords are compromised.
- Stay Updated: Regularly update your operating systems and software, including security solutions like Seqrite Endpoint Protection. Keeping your systems patched and current reduces exposure to known vulnerabilities.
- Maintain Offline Backups: Regularly backup essential data to offline storage devices. This ensures you have a fallback option if encryption-based attacks occur, eliminating the need to pay a ransom.
- Leverage Seqrite: With specialized modules like Ransomware Protection and Multi-Layer Protections Seqrite Endpoint Protection can detect abnormal encryption activity, stopping ransomware in its tracks.
Conclusion
The misuse of BitLocker is a stark reminder of how cybercriminals adapt legitimate tools for malicious purposes, pushing the boundaries of traditional ransomware strategies.
By integrating a strong security solution, practicing good cyber hygiene, and adopting a layered defense strategy, individuals and organizations can minimize their risk of falling victim to such attacks.
Authors
Umar Khan A
Niraj Lazarus Makasare
Dixit Ashokbhai Panchal
Sumit Patil
Matin Tadvi




