Browser extensions also known as add-ons or plug-ins are programs that extend the functionality of a web browser making it more convenient to use and giving a better browsing experience.
Browser extensions are commonly used to
- Enhance the appearance as per convenience
- Add to the functionality of the browser
- Incorporate with other services and features
To enhance browser extensions, the browser software vendor and third-party developers use different technologies such as browser altering plug-in called BHO (Browser Helper Object), APIs (Application Programming Interfaces), etc. Web Technologies such as JavaScript, HTML and Visual Scripts are also used widely to develop browser extensions which get infused directly into the web pages upon loading.
It goes without saying that these widely used extensions have become the most known malware attack vectors causing page redirection, spyware infection, malvertising, coin mining, pop-ups, poor system performance, etc.
Below are some of malware infection scenarios related to browser extensions:
- Browser Hijacking – contaminating existing and widely used browser extensions
- Installation of malicious extensions with bundled applications
- Accidental installation by a user while visiting malicious websites
Technical analysis of the massive PUA (Potentially Unwanted Application) campaign
Given its popularity, Chrome browser extensions are being increasingly targeted by attackers. A PUA campaign was observed wherein clean code from legitimate chrome extensions was as it is copied in the malicious one along with the malicious content.
After an in-depth analysis of these malicious Chrome extensions, Seqrite Telemetry system identified around 1.2 million hijacked Chrome extensions have been detected and cleaned by Seqrite’s Real-time Protection in the last two months.
Further reading
Generally, Chrome extensions contain component files and an extension core written in HTML and JavaScript contributing towards a common purpose. These component files specify the fundamental information of extensions such as their display name, version, update information, and their actual functionality.
All these component files are present in a single folder of an extension that includes manifest.json and one or more scripts or HTML files for background, content, and popup. These files communicate with each other using a direct function call to each other.
Usually, Chrome extensions look for an update from the update details specified in the extension file after a certain interval of time. Attackers misuse this very phenomenon to fulfill their ill intentions.
In case of the PUA campaign observed by Seqrite Labs, many of the Chrome extensions performing malicious activity were found to be similar to well-known and widely used Chrome extensions. Even the folder hierarchy of extensions, their component files, and fundamental functioning was also similar to the legitimate ones. As there are several Chrome extensions for various functionalities developed by the browser’s vendor as well as third-party developers, it is a daunting task to specify whether the extensions are clean or malicious. However, the task to find out the malicious ones is not impossible.
A close view of the hijacked extensions
Figure 1 shows the comparison between the clean and the modified/hijacked extension script. As seen below, the hijacked extension contains exactly the same script code as that of the clean Chrome extension. However, a block of code with the actual functionality is modified with the malicious code in order to perform the intended malicious activity.
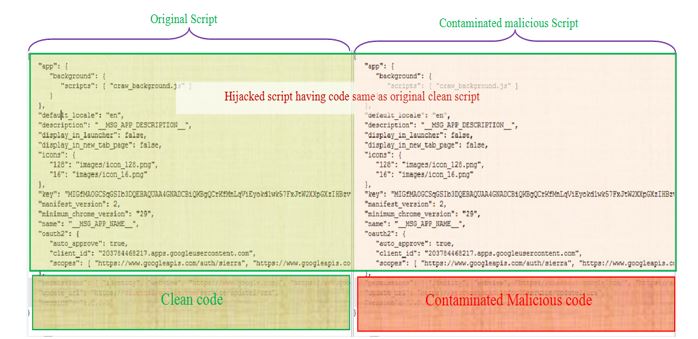
Figure 1: Clean vs hijacked extension file
In some of the cases observed, it has been found that extensions that were already installed were hijacked from the user’s system by modifying the code of their content files. Whereas, in some other cases, the malicious code was directly injected into the extension’s installation sites.
As seen in the above figure 1, a block of script code of the existing script file has been modified with the malicious content responsible for the malicious activity. As the name and folder structure of the extension does not change after infection, it does not give out any signs of any malicious activity. Many of the default as well as popular Chrome extensions have been hijacked using this technique for misleading users.
These extensions have been modified with a code to visit malicious websites resulting in some of the below listed malicious activities:
- Showing malicious ads and pop-ups
- Redirecting pages to phishing websites
- Perform coin mining
- Setting malicious home pages
- Injecting backdoors
How Seqrite Endpoint Security protects users from Chrome Extension hijacking
Seqrite Labs has released a solution for cleaning the malicious Chrome browser extensions. This detection looks for malicious content from contaminated extension files and cleans their concerned extension folder directory.
Figure 2: Seqrite Endpoint Security Virus Protection message
Seqrite’s Real-time Protection detects and cleans malicious Chrome extensions with below listed detection signatures:
- Trojan.4215
- Trojan.4062
- Trojan.4214
- CoinHive.4557
Safety measures to follow:
- Add browser extensions from legitimate sources only.
- Avoid websites that throw unnecessary or lots of advertisements.
- Install software only from genuine and trusted sources only.
- Do not click on links or download attachments received in unknown, unwanted or unexpected emails.
- Check for the authenticity and genuineness of the extensions to be installed.
- Check for the user reviews and ratings before adding any extension to your browser.
- Avoid downloading and installing patched and cracked versions of any software.
- Make it a habit to read end-user license agreements and additional components installed by any software.
- Use a reliable antivirus software that puts layers of defense between your computer and malware threats.
- Keep your browsers, Operating System, and other software such as Adobe, Java, antivirus, etc., up-to-date.
Subject Matter Expert
Dipali Zure | Seqrite Endpoint Security Labs




