A breach at IRINN systems could have affected India’s over 6000 ISPs, Government and Private Organisations.
We at Seqrite’s Cyber Intelligence Labs (https://seqrite.com) working closely with our Partner, seQtree InfoServices (https://seqtree.com/) recently tracked a broadcast advertisement on a Darknet platform where an underground actor had advertised access to the servers and database dump of an unspecified Internet Registry. Following a detailed research the team identified the affected organization as India’s National Internet Registry: IRINN (Indian Registry for Internet Names and Numbers) which comes under NIXI (National Internet Exchange of India). The sample screenshots (shared by actor) confirmed that compromise was real.
As per the standard protocol, we have contacted the appropriate agencies and sensitized them about the possible breach at IRINN.
Here is the detailed sequence of events related to this compromise:
- Upon noticing the broadcast advertisement, seQtree and Seqrite teams started gathering background research on the actor but did not yield any concrete information.
- But the team didn’t get any relevant data even after conducting deep research and it appeared that this actor’s persona was created recently. This is an ongoing trend that the team has noticed with recent data breaches.
- The team then contacted the actor for further details, posing as an interested buyer. Initially the actor was not willing to disclose the name of affected Internet Registry, however, later he agreed to share a small sample of email list from the allegedly compromised database.
- In the sample, the team noticed email address of a prominent Indian technology firm and another email address was from Indian government. Then the team asked for complete/extensive emails list.
- Eventually, the actor agreed to share a text file containing the emails of users/organizations affected, allegedly from the compromised database(s). The text file contained a list of approx. 6000 emails.
- It was observed some of the most important and high-profile organizations featured in the list. At this point, the team first thought the possibility of the affected organization being India’s National Internet Registry: IRINN (Indian Registry for Internet Names and Numbers) which comes under NIXI.
- To confirm our suspicion, we probed the actor further. The actor agreed to share screenshots which confirmed our suspicion that the compromise/breach is, unfortunately true and IRINN is the affected organization.
- The actor also hinted on the chat that if he doesn’t find any interested buyer, actor will consider posting this on Darknet forum(s)/marketplace(s).
- If he gets an interested buyer, then attack on the system could have disrupted Internet IP allocation and in-turn the complete Internet in India.
This can be a major tool of mass disruption if a state actor gets hands on it.
Below is the list of selective few organizations whose services could have been disrupted and also the sample screenshots to confirm our observation.
| Indian Government | Telecom/ ISPs | Financial Organisations | Technology Firms |
| UIDAI (Aadhaar) | Idea Telecom | Bombay Stock Exchange (BSE) | Flipkart
|
| DRDO | Aircel | Mastercard / Visa | Ernst & Young (E&Y) |
| Reserve Bank of India | BSNL | SBI | TCS |
| ISRO | You Broadband | HDFC | Wipro |
| ISRO Satellite Centre (ISAC) | Spectranet | ICICI Prudential Mutual Fund | VMWare |
| Employees’ Provident Fund Organisation | Hathway | BNY Mellon | eClerx |
| Various Indian state government portals (e.g. Maharashtra Online, MP Online) | Sify | IDBI Bank | Zoho |
| Vikram Sarabhai Space Centre | Tikona | Federal Bank | |
| National Centre for Antarctic and Ocean Research | Royal Bank of Scotland | ||
| Edelweiss Tokio | |||
| Dena Bank | |||
| IDFC Bank | |||
| Canara Bank |
Screenshots
Some of the censored screenshots (we have blurred the personal details) are attached below,
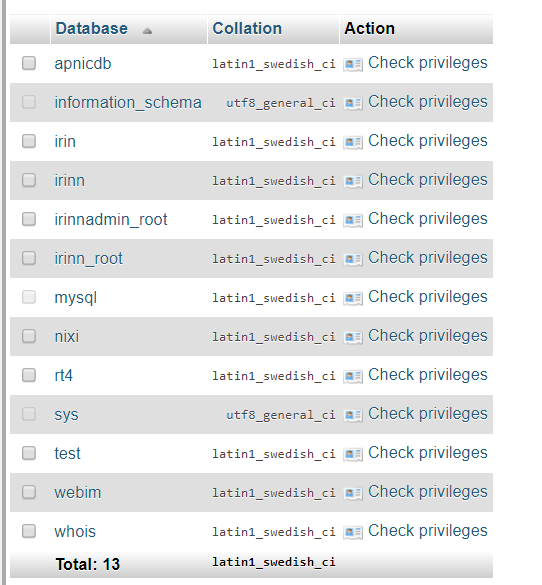 Fig. (1)
Fig. (1)
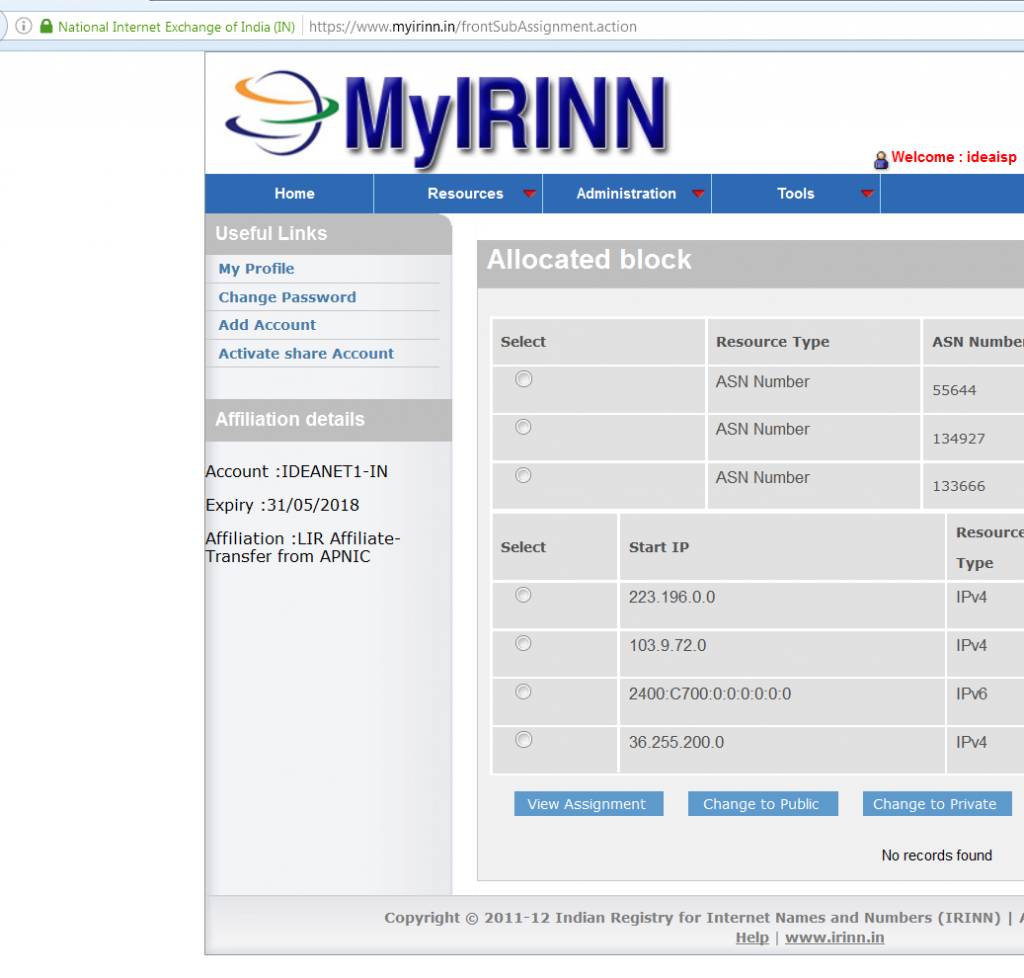
Fig. (2)
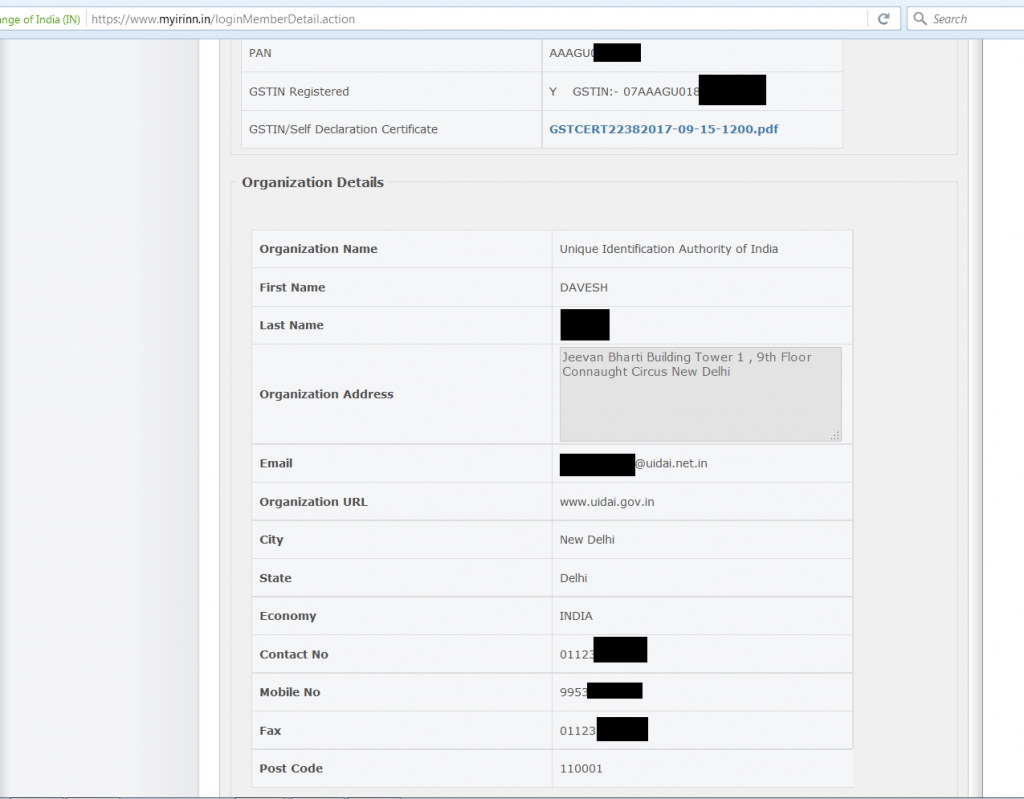
Fig. (3)
Assessment
We assessed the following from our research and the shared screenshots:
- The actor has a database related to IRINN, as well as some database related to APNIC (“apnicdb” in screenshot 1).
- The price set by actor for the database was/is 15BTC (approx. 61500USD in present rate).
- The actor can access other’s portal on IRINN website. This might indicate that along with email addresses, the actor also has access to passwords (as visible in screenshot 2 and 3).
- The actor can possibly control IP/ASN allocation/de-allocation for various organizations (as visible in screenshot 2).
- Actor might have access to internal sensitive documents uploaded by IRINN users (a PDF file is visible in screenshot 3).
Further Update as on 28th September 2017:
Our team noticed a post in Darknet forum, which provides clear indication that actor has started advertising about availability of this information on public Darknet forums as well. Screenshots are below:
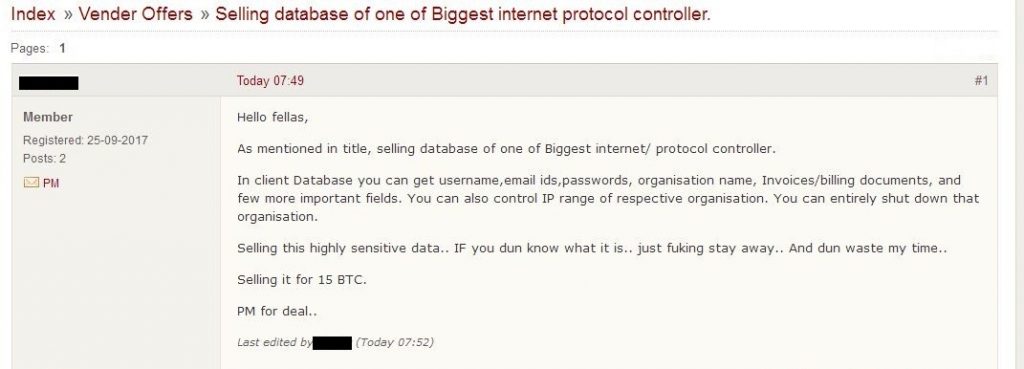
Fig. (4)
Fig. (5)
In the above screenshots, we can see that the actor is asking for 15 BTC in exchange of the IRINN’s database.
Implications
Assessing from the screenshot and emails list shared with our team, we believe this compromise could have serious implications for the affected organizations.
The forum post suggests that the actor has the Username, Passwords, Emails, Organization names, Invoices and Billing documents, etc. among other documents.
If an actor gets access to any organization’s IRINN portal, they might be able to de-allocate/delete IP/ASN, therefore, causing outage and Denial-of-service for the users and organizations.
Actions
We have notified appropriate agencies in the Government and have got an acknowledgement that the issue has been taken care of.
Hopefully this will not lead to any disruption. Proactive monitoring and reporting in any such case can always avert major damages.
All Intellectual Property Right(s) including trademark(s), logo(s) and copyright(s) are properties of their respective owners. Copyright © 2017 Quick Heal Technologies Ltd. All rights reserved.




