Email has become a necessity of day-to-day communication. We can realize the importance of email with the fact that the down-time of organization email server directly affects the organization’s productivity. Email has become most prominent and integral part of network system, hence one must know how to manage it and keep it secure. Let’s understand the email technology and its basic flow in nutshell.
1.1 How email works
 1.1 Diagram to illustrate basic email flow
1.1 Diagram to illustrate basic email flow
![]()
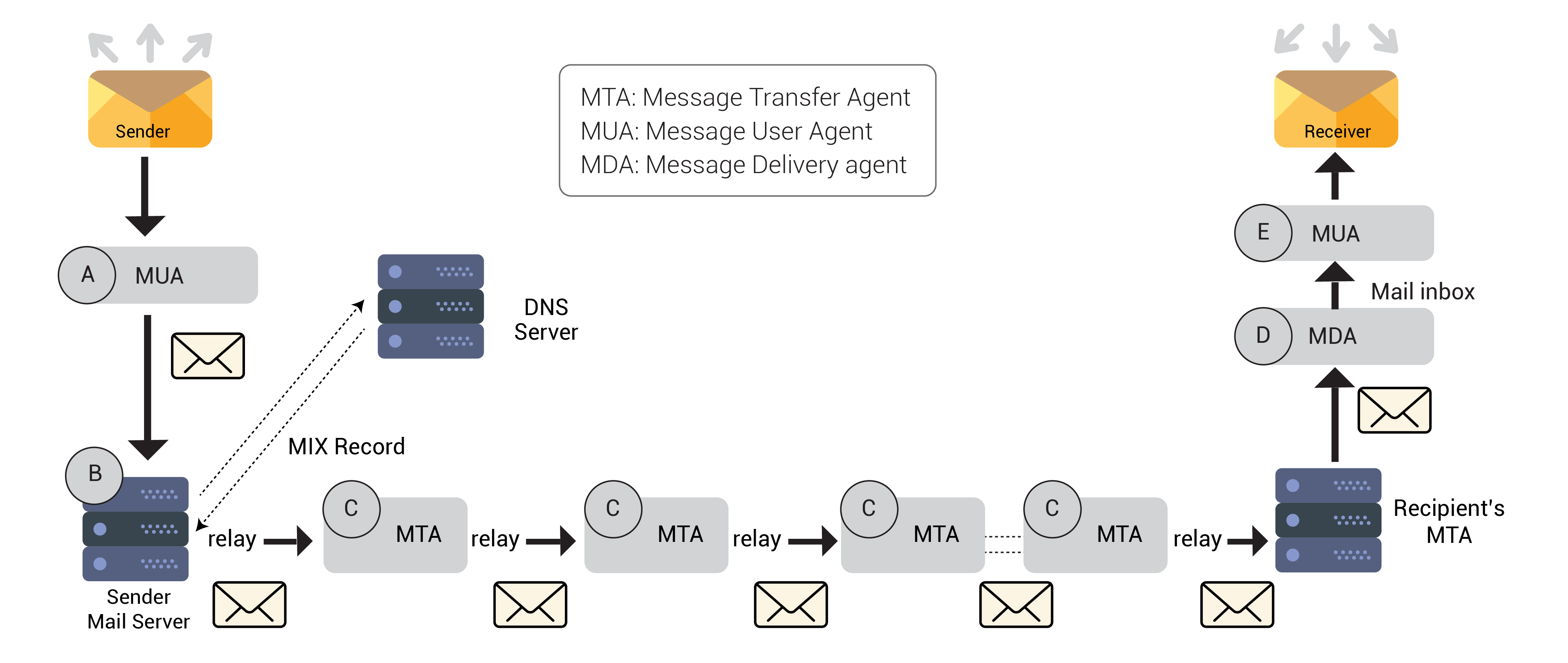
MUA, also referred to as an email client, is a computer application that allows you to compose and send emails or fetch and read emails intended for you. MUA can be a web-based client which means that you can send and receive emails via browser (i.e. Gmail, Yahoo on Firefox, Chrome etc.) or it can be application- based client (i.e. Thunderbird, Outlook etc.). In order to send an email, the sender needs to compose an email, add recipient name, and click on Send button.
![]()
Once sender has composed an email and sent it, an email server is ready to receive and process it. Email server is a computer application that is listening on port 25 (Non-encrypted), 465(SSL/TLS), 587(STARTTLS). The email server receives email from the sender and forwards it for delivery. All outgoing emails are placed in a mail queue and in parallel the SMTP server does a query with the DNS server for its MX record in order to find out where the receiver’s email server is located. Once it finds the IP address of recipient email server, it will send the composed message to that IP. E.g. MX record for xyz.com is like mail1.xyz.com.
In an email queue, SMTP server will lookout for MX record and recipient validation. If server is not able to process that email it will place that email in deferred queue which is not going to deliver immediately and re-tries after some time for a few attempts before sending the failed acknowledgment to client. If it is validated and intended for local delivery, it will handover that email to local delivery agent or if it is intended for remote delivery it contacts other mail servers for relaying.
![]()
If that email is intended for remote delivery, it will relay that email to MTA. MTA is a software application that relays email from one node to another node using SMTP protocol. MTA receives the email from another MTA or a MUA. After receiving that email, it will add the “received” tag at the top of message header file and relay it to another MTA for further delivery. It is also known as relaying agent of email. For each mail, MTA processes it and keeps track of each and every activity and analyzes the list of recipients for the routing actions. It sends responses of non-delivery when a message does not reach its intended destination. A few open source MTAs are Exim, Postfix etc.
![]()
MDA is a software application that takes mail from MTA and is responsible for delivery of that email to the receiver’s mailbox. Upon final delivery, the Return- Path field is added to the envelope to keep record of return path. Some popular open source MDAs are Dovecot, Fetchmail etc.
![]()
MUA is a software application that fetches the email from POP3 server or IMAP server and loads that email from the user’s mail box to email client (i.e. Thunderbird, Outlook).
POP3 server listens on following ports:
- Port 110 – Post Office Protocol for non-encrypted mail.
- Port 995 – Post Office Protocol over SSL/TLS.
IMAP server listens on following ports:
- Port 143 – Internet Message Access Protocol for non-encrypted mail.
- Port 993 – Internet Message Access Protocol over SSL/TLS.
In nutshell, The Mail Transport Agent (MTA), such as Postfix, Exim is responsible for sending email to the correct destination and handing over the mail to MDA.
The Mail Delivery Agent (MDA) such as Dovecot, Fetchmail receives mail from MTA and sends it into user’s mailbox.(Dovecot supports POP3 and IMAP protocols along with MDA functionality.)
The Mail User Agent (MUA) such as Thunderbird, Outlook is the email client that fetches the email from the user’s mailboxes and presents it to the user.
1.2 Security/Protection of Email server:
1.2.1 Scanning from threats
Scanning of emails before they reach the organization’s email server makes organization secure from the malicious activity. Proper scanning for Viruses, Spam, Spy-ware, Trojan horses, Phishing, Worms, Ransomware must be carried out. Email security/protection devices provide the facility to scan email file from the above threats.
1.2.2 Blacklisting of domain/email address
Blacklisting of email domains/ email addresses helps organization prevent receiving email from these malicious addresses or domain names.
1.2.3 Data leak prevention (DLP)
DLP helps organization prevent the leakage of sensitive or confidential information. Security devices check as per administrator’s customized policies at the gateway and accept or reject mail accordingly. Notifying such an activity to administrators would be an added advantage.
1.2.4 Content based blocking
Sometimes inappropriate content may flow through emails. Applying policies for inbound and outbound mail for file types, extension matching, keyword matching, and expression matching in both email body and email attachments reduces the flow of such an information.
1.2.5 Encrypted communication over SSL/TLS
Transport layer security (TLS) for encrypting/decryption can be provided for an email. Sending email in plain text can be intercepted and read by interceptor.
1.2.6 Verification of sender
To maintain the integrity in email communication, the sender should be a verified/legitimate entity. Pretty good privacy (PGP) let you digitally sign an encrypted document. This ensures that email coming to mailbox is not compromised.
Last but not the least, employee training also helps to reduce threats coming to or from the organization. A few points can be included in training.
- Never open the links from unknown senders and report to your manager/admin.
- Do not open attachment if it is from unknown sender and report to manager/admin. If mail is from a known sender but looking suspicious, it is good to confirm before opening the mail.
- Avoid connecting and accessing your email from public non-secure Wi-Fi connections.




