GandCrab has been in the wild since last week of January 2018. Over the period it kept learning from its mistakes and GandCrab’s agile development grabbed the attention of many security researchers. From moving its servers to Namecoin powered Top Level Domain (.BIT TLD) servers after the first breach, then learning from silly mistakes of encryption and communication process sequence, it kept moving forward. As observed recently, after version 4.0, newer version 5.0 also has infected a large number of machines and has seen a number of variants till now.
The version 5.0.9 was initially reported in the first week of December 2018, which has shown behavior similar to other GandCrab 5.0 versions. Although, to make sure that GandCrab does not become a memory before the new year starts, this version is showing message box ‘We will become back very soon! ;)’. From various indicators, we may say that authors are Russian and are non-native English speakers resulting in this poor sentence formation. We may predict the correct message as ‘We will come back very soon! ;)’.
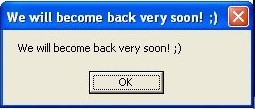
Fig. 1. Message Box
Infection Vector
GandCrab spreads through malicious mail campaigns containing malicious attachments or even through sextortion campaigns. Doc files are attached in mails with some genuine looking file name and user is forced to enable macros/download plugin update. This action results in infection of GandCrab.
Initially, it collects all data related to the user like username, computer name, workgroup, IP address, etc. This information is stored as ‘PCData’ in encrypted form and further used for identification of machine.
Before moving to the main execution part it checks for popular anti-virus services with all running processes.
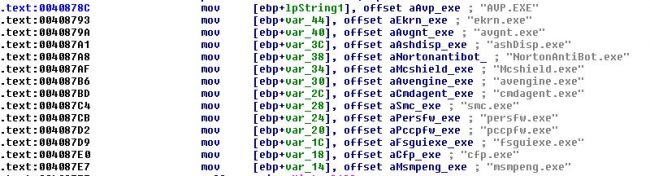
Fig. 2. AV Processes List
To know drives present on the machine, it checks every alphabet with the letter of the drive for drive enumeration. After collecting all the needed information related to the machine in PCData, it encrypts this information with RC4 algorithm having IV string ‘jopochlen’. Further, this data is again converted to the base64 format and is attached in ransom note under PCData section.
For extension, GandCrab has followed fixed length random strings from last two variants. This format is also continued for this version with up to 13 characters random length string.
Key Encryption
The main payload contains an RSA public key which is encrypted using salsa20 algorithm and this encrypted key is again XORed with byte key 5. After decrypting this key, it is then exported using the CryptExportKey function. The Salsa20 algorithm was originally developed by Daniel Bernstein (twitter handle:@hashbreaker). In this sample customized version of salsa20 is used. We can see the casual comment ‘@hashbreaker Daniel J. Bernstein let’s dance salsa <3’ in the file.
![]()
Fig. 3. Salsa identifier.
Two registry keys are created.
SOFTWARE/key__dats/dats (in previous version it was SOFTWARE/key__data/data) SOFTWARE/ext_data/data
The randomly generated extension which is appended to encrypted file is stored in ‘ext’ value of registry key:
SOFTWARE/ext_data/data
A new key pair of RSA-2048 is generated using Microsoft Enhanced Cryptographic Provider CryptoAPI CryptGenKey.
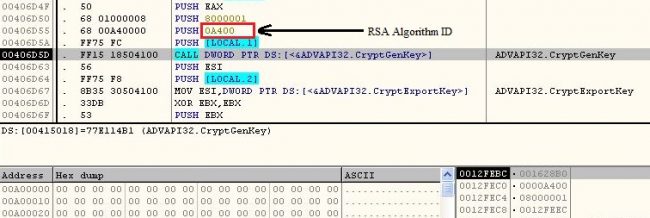
Fig. 4. CryptGenKey RSA-2048
RSA private key from this key-pair is encrypted with SALSA20 algorithm. This public key and encrypted private key pair is stored in ‘SOFTWARE/key__dats/dats’ registry with values public and private. The Salsa20 key used for this is again encrypted with RSA public key which was restored from the file itself.
 Fig. 5. Key Encryption And Storage
Fig. 5. Key Encryption And Storage
An encrypted ransom note is stored in the .data section of payload. This note is then decrypted by XORing bytes with 0x10. This ransom note is dropped with a name format: ‘extension_name-DECRYPT.txt’.
File Encryption
Before starting file encryption it terminates a few important processes which might be using files like documents, excel sheets or databases. This is done to confirm that no file in use is left without encryption.
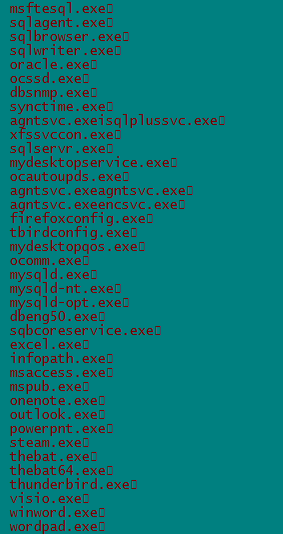
Fig. 6. List of Processes to Terminate
Also, list of all extensions which will be encrypted is present in the file. While carrying out encryption, GandCrab avoids a few important directories like Program Files, Windows, TOR(required to contact malware authors),etc. Also few files like boot.in, ntuser.dat are excluded from encryption.

Fig. 7. Encrypt File Structure
While encrypting, the entire file is encrypted with Salsa20. The Salsa20 key is generated with CryptGenRandom and it is different for each file. The Salsa20 key used for encryption is again encrypted with locally generated RSA public key.
After all files are encrypted, it tries to connect over 100 domains. Looking at the hostnames, it is clear that these are genuine websites and are compromised somehow. For formation of compromised URLs, it retrieves domain name from the list, then appends it with one of the 7 predefined strings. Again this is appended with second string chosen from other 8 predefined strings (images, image, pictures, graphic, assets, pics, imgs, tmp). Finally, the string is concatenated with randomly generated image name and one extension chosen from the list of 4(jpg, gif, png, bmp).
For example: https://[Genuine domain name]/content/graphic/dekakadake.jpg
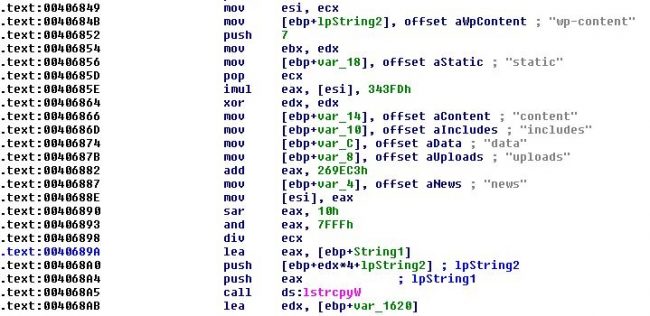
Fig. 8. URL Formation
After retrieving the whole URL, it sends encrypted user information stored in PCData to host.
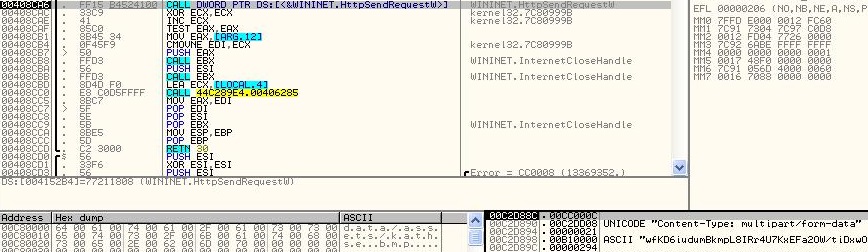
Fig. 9. HttpSendRequest
Ransom Note
Ransom note for GandCrab v5.0.9 looks like
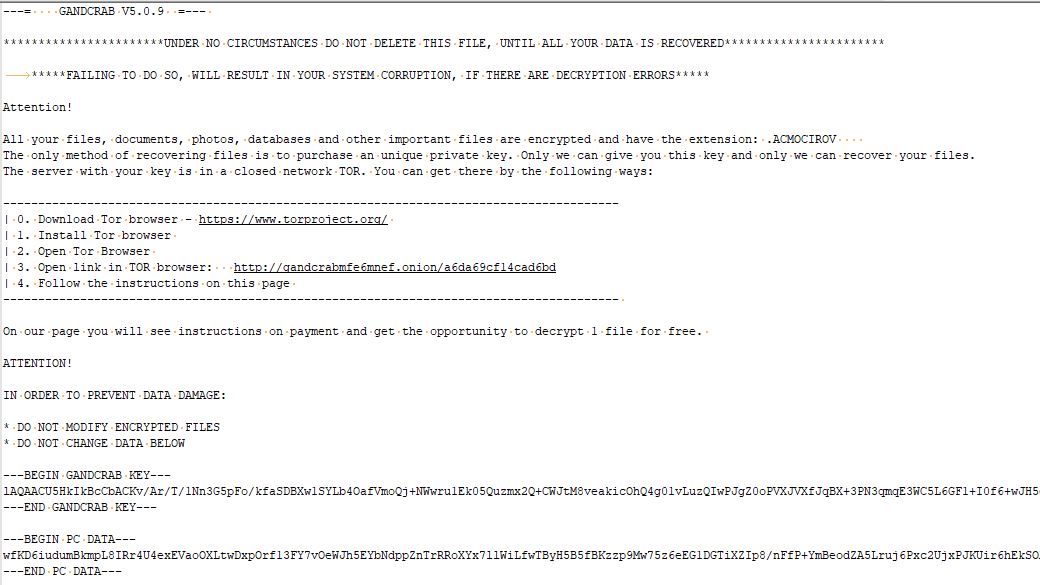
Conclusion
GandCrab has shown modular approach from start and has evolved over time.
Few key features can be:
- Checking for running popular AV services
- Termination of Applications to encrypt all files
- Using salsa for better performance still using RSA 2048
- Using Compromised sites for communication
It’s messagebox shown at the start indicates its next bigger release of a new variant. So we have to be on our toes to combat against it.
IOC
44C289E415E4C12B883003082194D76C
Subject Matter Expert:
Jayesh B. Kulkarni | Quick Heal Security Labs




