Estimated reading time: 2 minutes
Exploit Kits are dynamic in nature particularly in terms of their delivery mechanism. Their landing page i.e., the content is obfuscated and changed frequently in order to evade various security software. The RIG Exploit Kit, however, has a different...Information Technology, Network Security & Cybersecurity Updates

Estimated reading time: 3 minutes
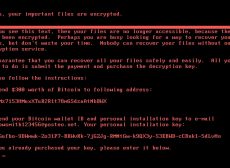
Cyber breaches are a threat to almost all kinds of businesses. Many large organizations establish elaborate policies and deploy sophisticated technology to ensure security of their infrastructure as well as their data. Smaller companies and start-ups, however, are different....