
As implied in the name itself,
Man In The Middle Attack is a type of attack where a illegal person tries to intercept the communication between two parties.
Either to secretly overhear or to steal the critical data being exchanged, with the intention to spy or to destroy the communication & corrupt the data.
Basically, when you try to overhear any conversation between two entities without letting them know, it itself is a kind of MAN-IN-THE-MIDDLE-ATTACK.
SO, WHAT EXACTLY IS A MAN-IN-THE-MIDDLE-ATTACK?
But Before going further into Man-In-the-Middle attack, I want you to look around !
look at your smartphones, devices accessing internet, all the software applications you are using.
What do you think? What is driving all these things?
DATA! Right?
Well, all this data travels around ourselves with no bounds. From one source to another destination, data has no limitation at all. This unobserved traveling of data raises a huge question on the privacy and security of the data.
Have you ever given any thoughts about maintaining this privacy?
What if someone is already seeing all your data in your phone or using your private information to benefit his/her needs?
While data transmission takes place between client & server, attacker places itself between two endpoints of communication and interferes with the data transfer, while trying to acquire the critical information which is being exchanged.
Meanwhile the client and the server thinks that they are interacting with each other but they are actually dealing with the attacker.
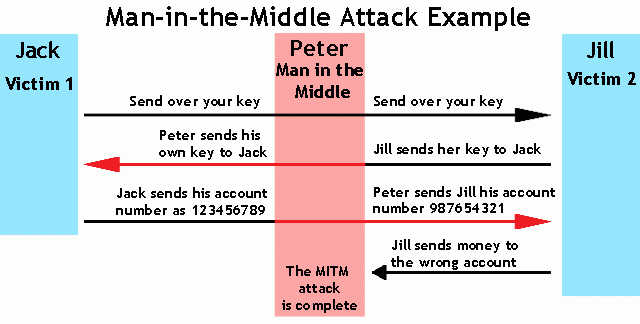
Explanation :
Let’s Suppose A & B are two entities and C is the Man-in-the-middle. Now if A & B want to share information with each other, A will ask for a public key from B, so that A will send Encrypted data accessible with only that public key and only B will be able to open that information using that key. But, as soon as B sends its Public key to A, C present in the middle takes that key and sends its own public key to A.
A now assuming that key is of B, encrypts the required data and sends it to B again. Now C will decrypt that data using its own public key, read that data and alter the information as per requirement and send it to B with its Public key so that B will be able to decrypt the information, assuming that this information is directly coming from A and likewise this process continues. Both A & B doesn’t even get to know that they are actually not talking to each other.
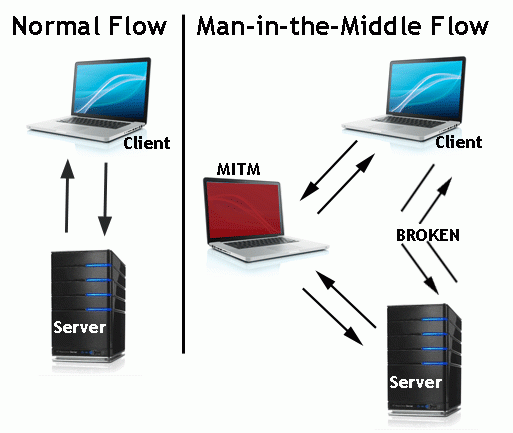
Technically, whenever two party speak with each other, TCP connection gets establish. So what an attacker does is, it will divide that connection into two parts where 1 connection is between attacker and client and another one is between attacker and the server and attacker works as a proxy between them. Another way this attack can happen is through Man-In-The-Browser attack where an attacker put its Bot onto your system which collects all credentials and important information from your daily web browsing and eventually sends it to the attacker.
HOW DOES THIS ATTACK WORK?
Attackers are always in search for any vulnerable network, where they can breach the security and access the data transfer. Attack is performed in two phases: First phase is ‘Interception’ or ‘Encryption’ and the second one is ‘Decryption’.
‘Encryption’ & ‘Decryption’
For Interception, public places like Railway Station, Airport, etc. are the most favorable one, as there are FREE WiFi n/w (People Just Love Free things). Attackers try to find a poorly secured network and search for any vulnerability. Attacker is between victim client computer and server to intercept the data, placing necessary tools to acquire the critical information exchanged, which victim is thinking to be secure. Data is intercepted now , it needs to be decrypted. Now comes the role of decryption, where data is been decrypted and further acted upon.
Too short right? Well it’s a brief explanation after all to get minimal idea. Now let’s understand it step wise.
There are few more ways to carry out network security attack. Let us discuss some of these attacks in brief:
Examples ~
1. Sniffing:
It is a process of analyzing and capturing the data packets containing sensitive information flowing from one network to another. Data flows from source to destination in the form of small data packets and the attackers manage to access these streams of data and pill out the private information needed to carry out the attack.
2. Packet Injection:
It is a technique where attacker disrupts the established network, by inserting his/her own packet with the regular flow of data between trusted entities, to avoid malicious activities to be over looked or ignored. This type of interference of packets process is used in DDoS and Man-In-The-Middle attacks.
3. Session Hijacking:
Whenever a user logs into a website, it sends a request through a browser to the server of the requested website. The request gets analyzed and a response is sent over the network to the user and a session is establishes for the user to get into the website. Meanwhile, the attacker tries to hijack that session and is in a position to intercept that session and is able to pull out the private information required to initiate the attack successfully.
4. SSL Stripping:
Attacker use this process when it strip off the SSL/TLS encryption used for secured connection, Switches user network connection from HTTPS to HTTP. Victim is vulnerable shifting from secured connection to un-secured connection, it is easy for attacker to push victim to its own environment, where attacker extracts information provided by the victim. KRACK, MITM are few of the attacks carried out by SSL stripping method.
HOW TO GET SAVED FROM THESE ATTACKS?
Following are some of the steps we can follow in order to prevent such cyber-attacks :
-
Use HTTPS connection over HTTP as HTTPS is more secured and a reliable way to connect to any network.
-
Keeping Browser Cookies and cache cleared in order to prevent attacker from stealing information from those resources.
-
Use of HSTS over HTTPS. This web server directive forces any Web-App to connect to HTTPS and block all other content that uses HTTP protocol.
-
Do not click on un-necessary emails and advertisements.
-
Do not use un-secured Public Wi-Fi access or make payments over it.
-
Always keep required security tools updated to protect your system.
-
Always keep your working network secured.
-
Don’t ever download any pirated data.
SEQRITE Unified Threat Machine: IPS
Intrusion Prevention System
IPS is a network security system that protects your organization’s network from external attacks, intrusion attempts, malware and threats. It observe the incoming network traffic and identify the potential threats and responds according to the rules specified. This drops the packet that it determines to be malicious and block all further traffic flowing from that IP address or Port.
Seqrite UTM has a feature called Intrusion Prevention System. It monitor as well as block the vulnerability exploit that attackers use to interrupt and gain control of an application or machine. It consist of pre-configured set of signatures embedded, which are matches with the signatures of the entering data packets. If any incoming signature matches with an existing signature, the IPS either drops the packet or sets up an alarm.
Feature Explanation
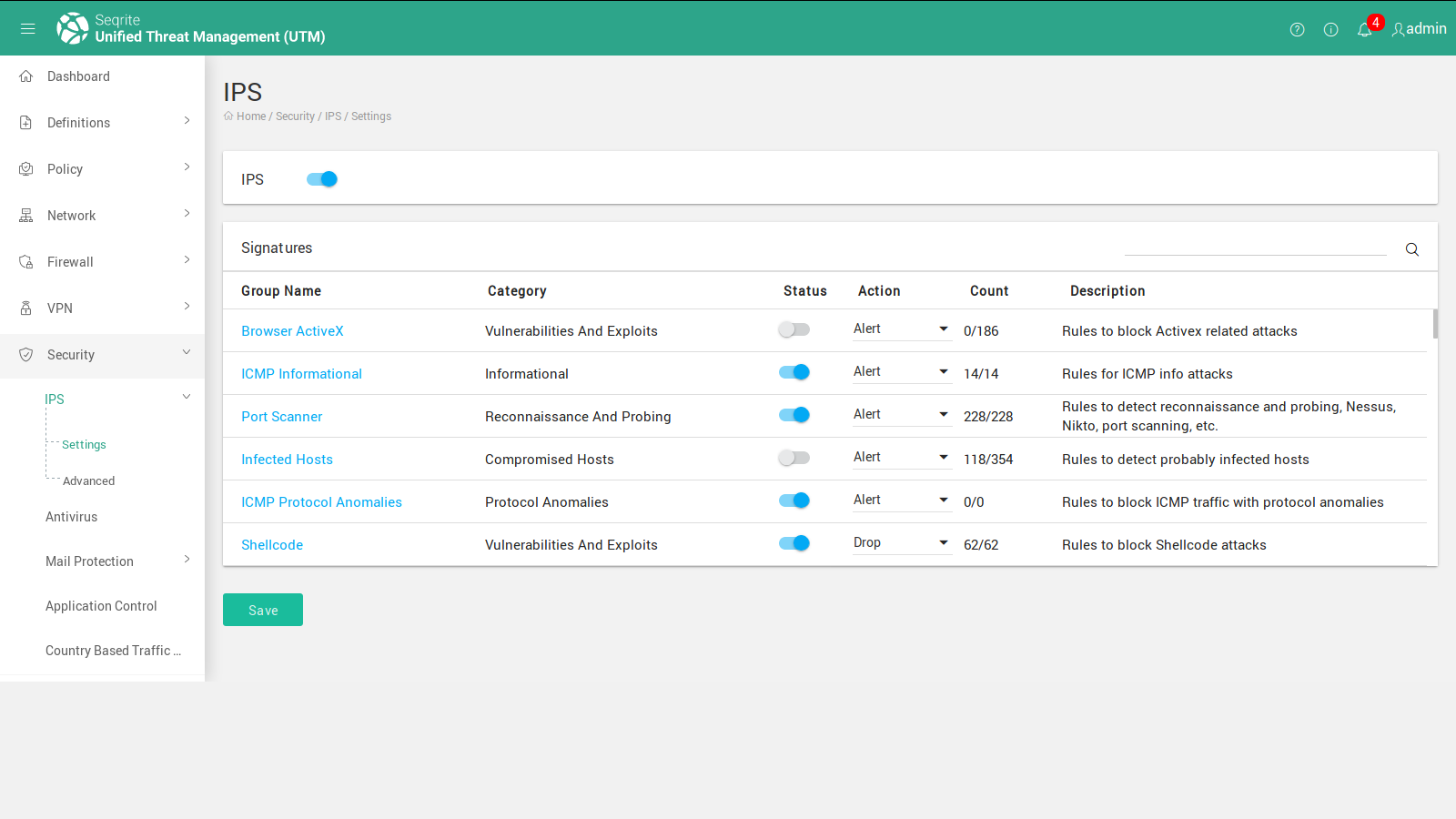
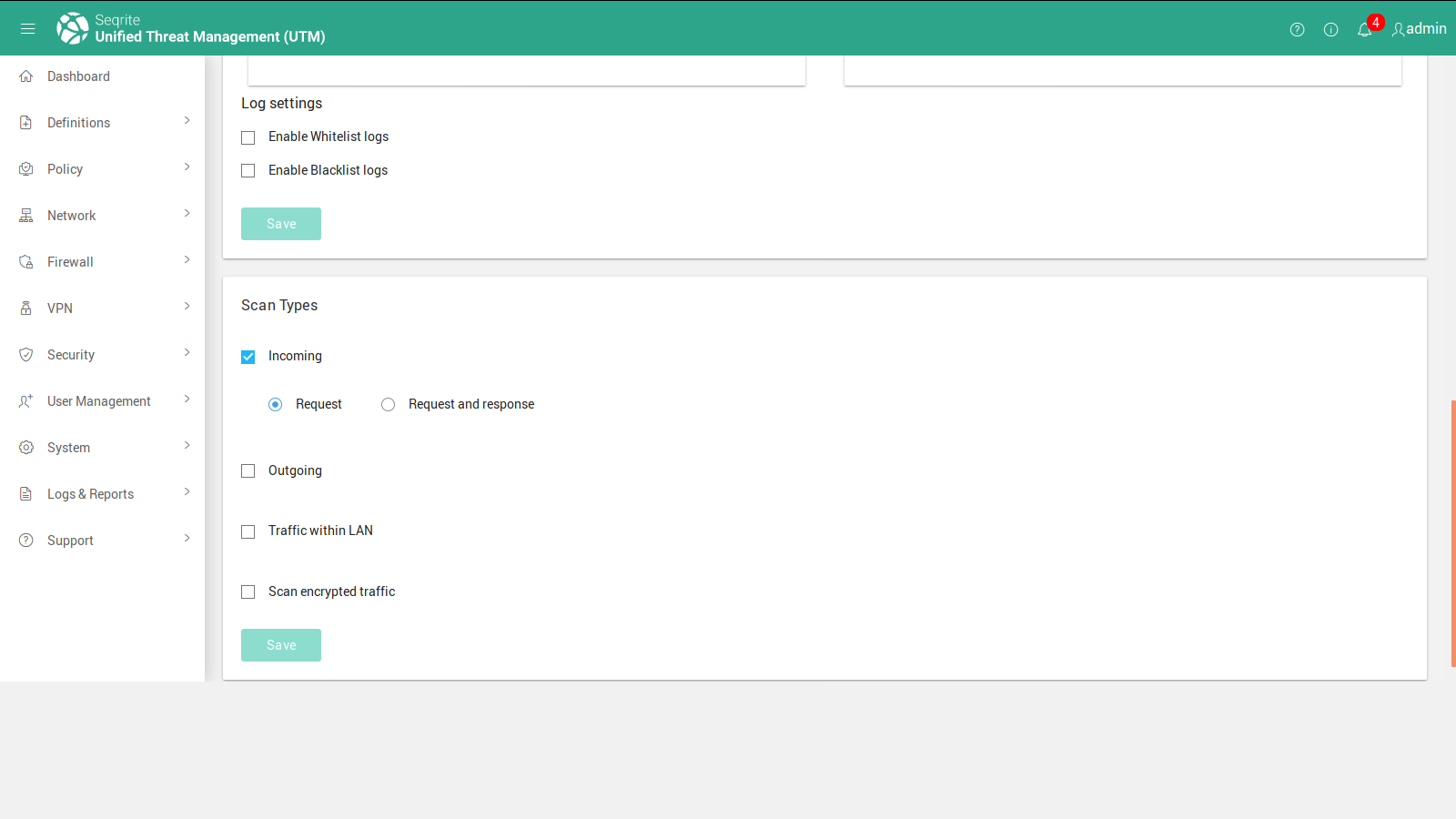
Image below shows the status of IPS and various settings that comes under IPS and the relevant information such as
- Designated action to take.
- Alert or Drop the suspicious packet.
- Count of Occurrences & the Description.
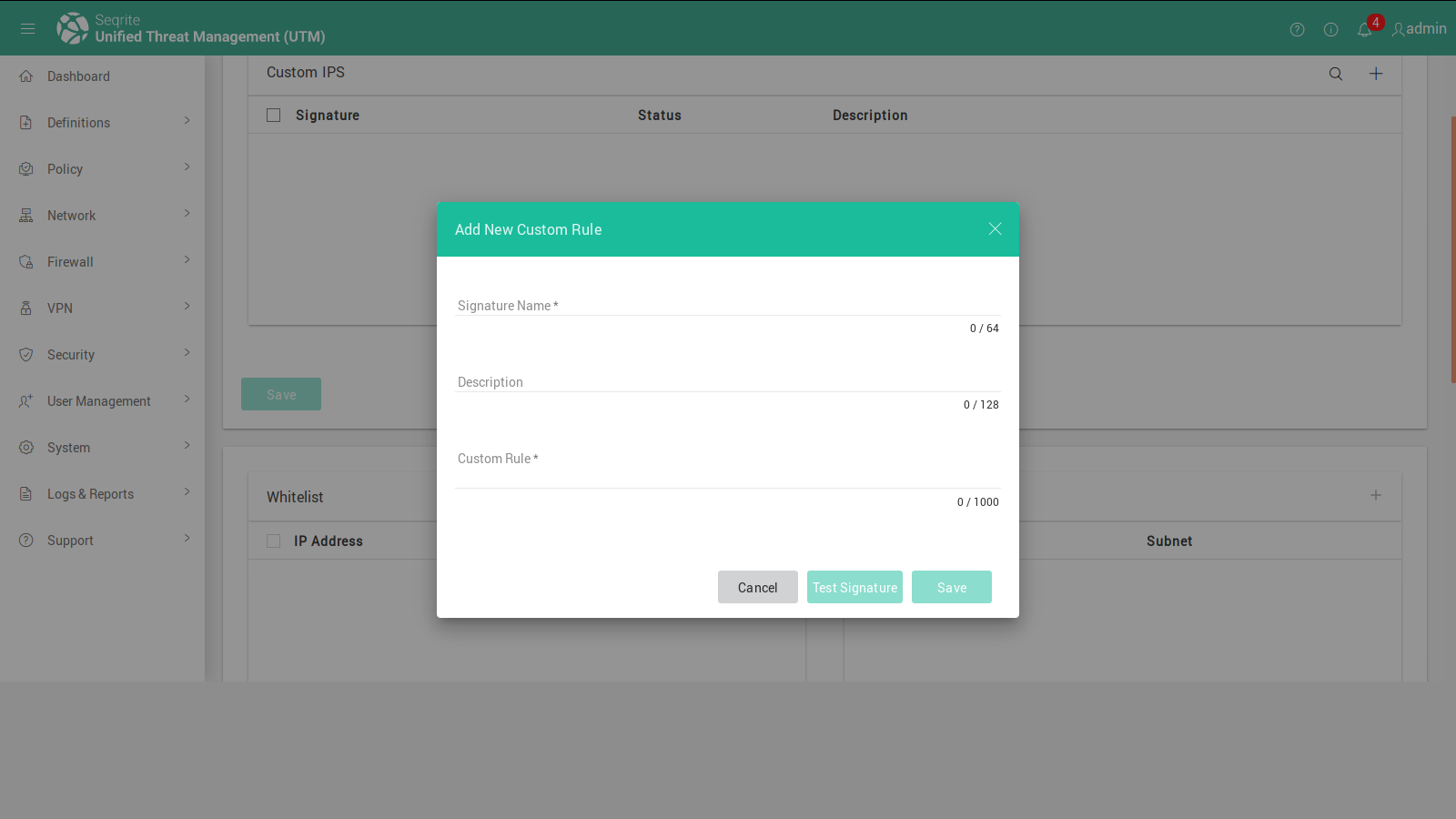
You might need to add new signatures to your existing signature list. In Seqrite UTM IPS you can add your own custom signatures. You can do this using the advances tab on the IPS page.
Your organization may require to monitor all inbound, outbound, as well as intranet traffic. This feature allows you to monitor all or individual traffic types.
REFERENCES
a) thesslstore.com
b) veracode.com
c) securebox.comodo.com
d) Man-In-The-Middle-Attack Prevention Using HTTPS and SSL, IJCSMC, Vol. 5, Issue. 6, June 2016, pg.569 – 579




