SnakeKeylogger – A Multistage Info Stealer Malware Campaign
Info-stealer malware has become a growing threat, with attackers constantly refining their techniques to evade detection. Among these threats, SnakeKeylogger has emerged as one of the highly active credential-stealing malware, targeting individuals and businesses.
Known for its multi-stage infection chain and stealthy in-memory execution, SnakeKeylogger is designed to harvest sensitive data while remaining undetected.
Recently, at Seqrite Labs, we observed an interesting malicious campaign delivering SnakeKeylogger as a final payload to compromised systems.
Infection Vector:
Initial infection vector is a malicious spam email containing .img file [Disk Image File] as an attachment. Once the .img file is opened, a virtual drive is created that allows access to the data in the file. The file inside this .img is an executable file (Stage1), masquerading as a PDF document with a file Icon and name carefully chosen to resemble an important PDF document, increasing the likelihood that the recipient will open it.
Attack Chain:
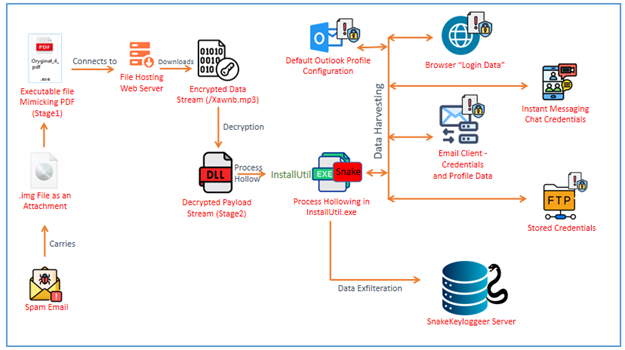
Snake Keylogger follows a systematic approach to harvest credentials and other sensitive data. Some of these approaches include:
- Downloading and decrypting encoded payloads, ensuring stealthy execution.
- Loading obfuscated DLLs directly into memory, avoiding disk-based detection.
- Injecting malicious code into genuine processes, specifically .Net Framework-related processes.
- Checking for the default Outlook profile to extract stored email credentials.
- Harvesting login data from multiple browsers and email clients, stealing saved passwords.
- Extracting stored FTP credentials from FileZilla, which can be used for further exploitation.
Technical Analysis –
Stage1 (Downloader and Loader):
This file is an x64 bit .Net compiled executable with a file size of around 10 KB.
Stage 1 acts as a downloader and loader. Upon execution, it tries to connect to a remote server and fetch some media files.
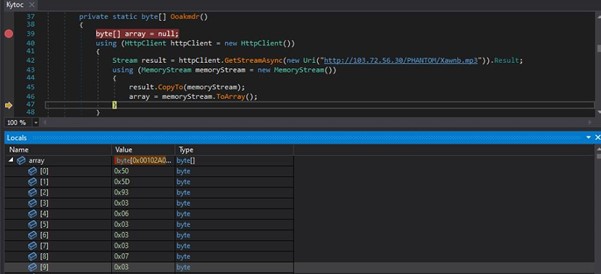
At first glance looking at the URL, it appears to be fetching a simple media file (*.mp3) from the server. However, closer inspection reveals that this is not a media file but rather a disguised encoded payload.
The payload is retrieved as a response stream and not a file on to disk. It is stored as the array of bytes in array variable “array”.
Apache Server is abused for Malware Distribution
Upon investigating the URL further, we found that the Apache 2.4.58 (Windows) server is abused for running a malicious campaign. Attackers are actively maintaining and updating encrypted malicious payloads hosted at hxxp://103.72.56.30/PHANTOM/
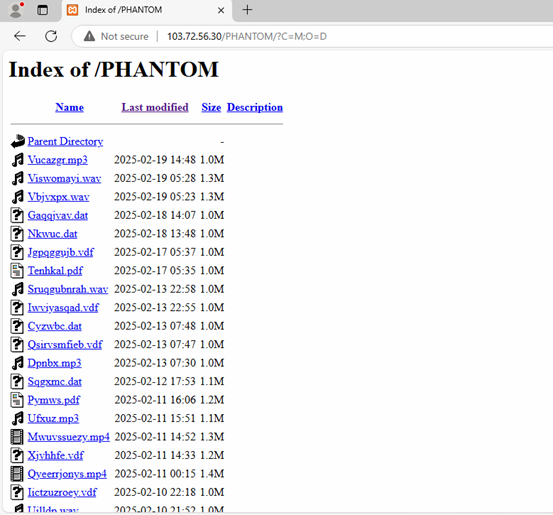
As we can see, attackers regularly upload and rotate files within the /PHANTOM/ directory. This tactic [TA0042] is commonly used in Malware-as-a-Service (MaaS) operations or ongoing phishing and malware distribution campaigns, allowing attackers to update their payloads while maintaining a stable infrastructure[T1608].
Coming back to our analysis of Stage-1, after the stream is fetched, it follows a decryption routine to decode the payload.
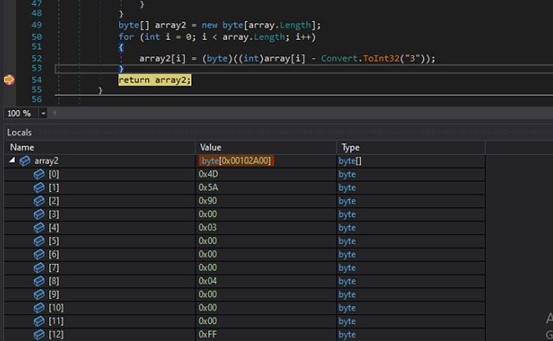
The retrieved payload (array) is decoded by subtracting 3 from each byte, and the results are stored in the array variable “array2”. We can see that the decoded payload has a PE file header. We dumped the decoded stream, i.e., “array2,” and started investigating the decoded payload. We found that the file is a Stage2 DLL file, which is loaded dynamically into the memory.
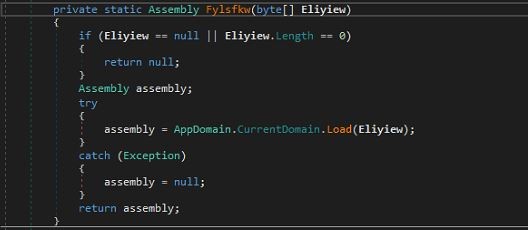
Stage2 (Xspilbxpui.dll)
When analyzing with the DiE (Detect it Easy) tool, we can see that the file is a 32-bit DLL compiled with .NET. It is highly obfuscated, protected, and encrypted to deter reverse engineering, making it difficult to reveal its true functionality and execution flow.
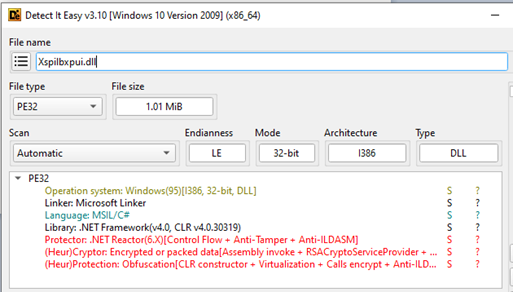
What’s interesting about this sample was the use of delegates along with high obfuscation and intermediate code generation to bypass API monitoring.
In this stage of the infection chain, the malware employs process hollowing to execute its payload stealthily by targeting InstallUtil.exe. “InstallUtil.exe” is a legitimate Windows utility for installing and uninstalling server resources. Process hollowing is a sophisticated technique where a new process is spawned in a suspended state, its legitimate memory region is unmapped, and malicious code is written into the hollowed space before the process is resumed, running the attacker’s payload.
The injected payload is a SnakeKeylogger variant trying to steal system data along with WIFI connection details.
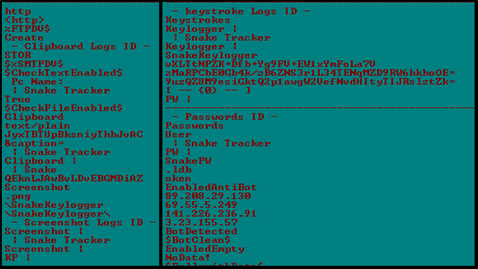
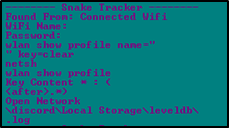
The injected InstallUtil.exe process is exhibiting behavior consistent with credential-harvesting malware, targeting a wide range of applications that store sensitive user data.
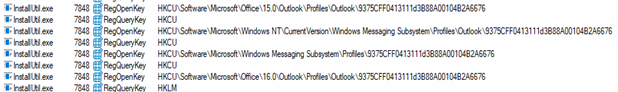
SnakeKeylogger accesses a critical registry location {9375CFF0413111d3B88A00104B2A6676} where Microsoft Outlook 2013 and Outlook 2016+ store user profile configurations. These configurations include email account details, mail server settings, and potentially encrypted credentials. Compromised email accounts can be exploited to bypass multi-factor authentication (MFA), impersonate victims, or launch further attacks within an organization.
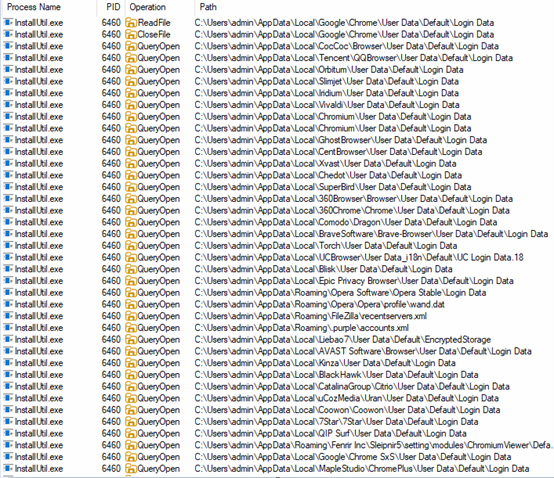
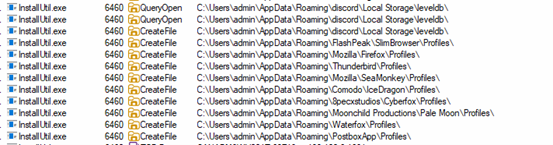
Below are the categories and list of applications targeted by SnakeKeylogger:
| Web Browsers (Chromium & Other Variants) | |||
| Google Chrome | Xpom Browser | Coowon Browser | SuperBird Browser |
| Microsoft Edge | 7Star Browser | CocCoc Browser | BlackHawk Browser |
| Vivaldi | Blisk Browser | Orbitum Browser | CatalinaGroup Citrio |
| Slimjet | Kinza Browser | Sputnik Browser | Epic Privacy Browser |
| Iridium | Torch Browser | Liebao7 Browser | Avast Secure Browser |
| Chromium | Comodo Dragon | QIP Surf Browser | QQ Browser (Tencent) |
| UCBrowser | Brave Browser | Nichrome Browser | MapleStudio ChromePlus |
| 360 Browser | Citrio Browser | Opera / Opera GX | Uran Browser (uCozMedia) |
| Fenrir Inc. Sleipnir5 | |||
These applications save passwords, cookies, and auto-fill data in the “Login Data” file. SnakeKeylogger tries to query and read this sensitive data.
| Mozilla-Based Browsers |
| Mozilla Firefox |
| Waterfox |
| SeaMonkey |
| Comodo IceDragon |
| Cyberfox (8pecxstudios) |
| Pale Moon (Moonchild Productions) |
These stores saved logins, bookmarks, session data, and history in “Profiles\”.
| Email Clients |
| Thunderbird (Profiles\) |
| Postbox (Profiles\) |
These store email credentials and server configurations.
| Instant Messaging / Communication Apps |
| Pidgin (.purple/accounts.xml) |
These store chat credentials in configuration files.
| FTP Clients |
| FileZilla |
Tries to access list of recently accessed FTP servers and stored usernames & passwords present in file “recentservers.xml”
File Hashes (MD5):
851A5FFAC3EE2DA08557108239F90FAB
FD7634082A916C3BD8C94C8493FC83E2
9AD19A4E2D41E214D7BF04F74151DDBD
07B21AAE60698970EBDC2E854B3ACFED
Below are MITRE Attack Tactics, Techniques, and Procedures (TTPs) of SnakeKeylogger:
| Tactics | Techniques/ Sub-technique |
Procedure |
| Initial Access (TA0001) | T1566.001 | Spearphishing Attachment |
| Execution (TA0002) | T1204.002 | Malicious File Execution |
| Defense Evasion (TA0005) | T1140 | Deobfuscate/Decode Files or Information. |
| T1027 | Obfuscated Files or Information. | |
| T1218.004 | System Binary Proxy Execution: InstallUtil. | |
| T1202 | Indirect Command Execution. | |
| Credential Access (TA0006) | T1555 | Credentials from Password Stores. |
| -T1555.003 | Credentials from Web Browsers. | |
| -T1555.004 | Credentials from Email Clients. | |
| -T1555.005 | Credentials from Password Managers. | |
| Discovery (TA0007) | T1083 | File and Directory Discovery. |
| T1012 | Query Registry. | |
| Collection (TA0009) | T1114.002 | Email Collection via Client Application. |
| Command and Control (TA0011) | T1071.001 | Application Layer Protocol: Web Protocols. |
| T1105 | Ingress Tool Transfer. | |
| Resource Development(TA0042) | T1608.001 | Stage Capabilities: Upload Malware |
Conclusion:
The SnakeKeylogger campaign showcases a highly structured attack chain, beginning with spam emails that deliver malicious attachments to unsuspecting users. The attackers maintain a stable infrastructure for hosting malware in encrypted form, allowing them to distribute and update payloads seamlessly. The infection progresses through multiple stages, utilizing techniques like file format deception, process hollowing, and encrypted payload execution to evade detection.
A key objective of the malware is harvesting sensitive data, including Outlook profile credentials, email configurations, and other stored authentication details, which can be exploited for business email compromise (BEC), further intrusions, or sold on underground markets.
Authors:
Prashil Moon
Rumana Siddiqui




