Overview
APT Transparent Tribe (APT36) is luring the Indian Army into opening the malicious file themed ‘Revision of Officers posting policy.’ Quick Heal’s APT Team has been constantly tracking this persistent threat group and has encountered a new attack campaign targeting India.
At the same time, we have also observed increased targeting of the education sector by the same threat actor. This is in continuation of targeting IITs since last year.
Furthermore, the sub-division of this group, SideCopy, has been observed recently targeting an Indian Defense Organization where the domain hosting malicious files was probably being tested to act as a phishing page.
Key Findings
- APT36 is targeting Indian Army with malicious PPAM files with ‘Officers posting policy reviseed final’ as the theme.
- These macro-enabled PowerPoint add-on files (PPAM) are utilized to wrap malicious payloads by embedding archive files as OLE objects.
- The infection chain leads to the execution of a .NET-based Crimson RAT payload that can receive and execute 22 commands along with the persistence mechanism.
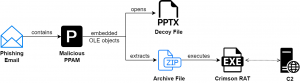
Overview of Attack Chain
- C2 used by APT36 uses the same Common Name, which is usually found in this threat group’s C2 infrastructure.
- From targeting IITs to NITs and Business schools now, we have observed an increased targeting in the first quarter of 2023, peaking in February.
Summary
Transparent Tribe is a Pakistani threat group, active since 2013. It is a persistent threat actor targeting the Indian government and military entities. The group continuously uses payloads such as Crimson RAT and Capra RAT in its campaigns, constantly upgrading them.
Since May 2022 last year, Transparent Tribe has begun targeting the education sector, which surged in 2023. An in-depth analysis of the latest infection chain targeting the Indian Army and details of the education sector targeting can be found in our whitepaper.




