In the wake of numerous security incidents in which attackers exploited unsegmented networks to spread malware and access sensitive data, it’s clear that traditional network architectures often fail to prevent the lateral movement of threats. This blog will illustrate how network segmentation can effectively contain potential breaches, minimize attack surfaces, and enhance compliance with regulatory standards, ultimately bolstering an organization’s security posture.
Network segmentation is a security technique that divides a network into smaller, distinct sub-networks or segments to improve security, performance, and manageability. This approach can significantly enhance an organization’s security posture by containing potential breaches, reducing attack surfaces, and improving compliance with regulatory standards. Here, we will explore various aspects of network segmentation and its impact on security, potential challenges, and best practices.
Introduction to Network Segmentation
Network segmentation involves dividing a more extensive network into smaller, isolated segments, each with its own security policies and controls. This technique enhances security by limiting access to sensitive data and systems, reducing the attack surface, and containing potential breaches.
Example 1: Consider a corporate network where the Human Resources (HR) department’s computers are on one segment, the Finance department’s systems are on another, and the rest of the corporate network is on a separate segment. Each segment is isolated from the others with specific access controls in place. For instance, HR staff can access HR systems but cannot access Finance systems, and vice versa. This segmentation ensures that even if an attacker gains access to one segment, they cannot quickly move laterally to other segments and compromise additional sensitive information.
Example 2: Imagine an IT company that provides various services such as software development, customer support, and internal corporate functions. The company might segment its network as follows:
- Development Segment: This segment includes all the systems and servers the software development team uses. Developers can access version control systems, development tools, and test servers.
- Customer Support Segment: This segment contains systems used by the customer support team, including customer relationship management (CRM) software and support ticketing systems.
- Corporate Segment: This segment includes systems used for general corporate functions such as email servers, file storage, and human resources applications.
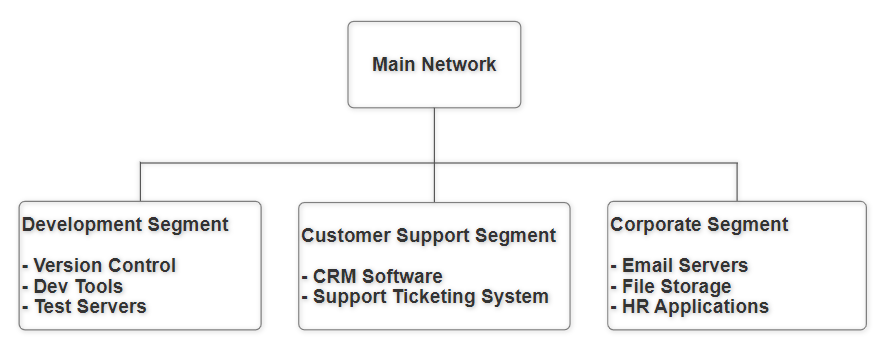
Figure: The basic flow of Network Segmentation based on Example 2
The primary goals of network segmentation are:
- Limit the Spread of Cyber Threats: If a cyber threat, such as malware, infects one segment, it is contained within that segment and prevented from spreading to other parts of the network. For instance, if the customer support segment is compromised, the development and corporate segments remain secure.
- Enhance Network Performance: Network segmentation can improve overall performance by reducing congestion and isolating traffic. Each segment can operate more efficiently because it handles less traffic.
- Improve Compliance with Security Regulations: Many industries have strict security regulations that require specific measures to protect sensitive data. Network segmentation helps meet these regulatory requirements by ensuring that sensitive information is only accessible to authorized personnel within particular segments. For example, financial data in the corporate segment is protected from unauthorized access by staff in other segments.
Benefits of Network Segmentation: Network segmentation offers several significant benefits for organizations, particularly in enhancing security, improving network performance, and ensuring compliance with regulatory standards.
- Containment of Breaches: Network segmentation can prevent attackers from moving laterally across the network by isolating network segments. This means that if an attacker gains access to one segment, they are contained within that segment and cannot easily infiltrate other parts of the network. For example, if malware infects the customer support segment, it will not spread to the development or corporate segments, thereby protecting sensitive information and critical systems.
- Reduced Attack Surface: Network segmentation limits the number of systems exposed to potential attackers. By creating smaller, isolated segments, each with its own security policies, the overall attack surface is reduced. This minimizes the points of entry for attackers, making it harder for them to find and exploit vulnerabilities within the network.
- Enhanced Monitoring and Control: Each network segment can have tailored security policies and controls. This granularity allows for more precise network traffic monitoring and better control over who has access to each segment. For instance, access to the development segment can be restricted to only those employees who need it, and traffic can be closely monitored for any suspicious activity. This enhances the ability to detect and respond to potential security threats more effectively.
- Improved Performance: Network segmentation can optimize network performance by reducing congestion and improving bandwidth management. By isolating traffic within segments, each segment handles less overall traffic, leading to faster data transfer rates and more efficient use of network resources. For example, the heavy data traffic from the development segment will not affect the bandwidth available to the customer support or corporate segments, ensuring smoother operation for all departments.
- Regulatory Compliance: Many industries have stringent regulatory requirements for data security that mandate strict data segregation and access controls. Network segmentation helps organizations meet these requirements by ensuring that sensitive data is properly isolated and protected.
In the context of India, network segmentation can help organizations comply with several regulatory frameworks, including:
- PCI DSS (Payment Card Industry Data Security Standard) requires that cardholder data be isolated from other network parts to prevent unauthorized access.
- The IT Act 2000 (Information Technology Act, 2000) requires the protection of sensitive personal data and mandates measures to secure information systems.
- The (soon to be implemented) Digital Personal Data Protection Act aims to protect the personal data of Indian citizens by establishing stringent data protection and privacy requirements, including data localization and access controls.
- The Reserve Bank of India (RBI) has issued guidelines for the banking sector’s cybersecurity framework, emphasizing the importance of network segmentation to safeguard critical financial data and systems.
Implementation Strategies:
Network segmentation involves dividing a more extensive network into smaller, isolated segments, each with security policies and controls. Proper implementation of network segmentation enhances security by containing potential breaches, reducing the attack surface, and improving manageability.
Here are several strategies for implementing network segmentation effectively:
Physical Segmentation: This involves using separate physical hardware for different network segments.
Implementation:
- Dedicated Hardware: Use separate switches, routers, and firewalls for each segment.
- Cabling: Physically separate cabling for different segments.
Logical Segmentation with VLANs (Virtual Local Area Networks): VLANs allow for the creation of multiple virtual networks on the same physical hardware.
Implementation:
- Configure VLANs: Set up VLANs on switches to logically separate network traffic.
- VLAN Tagging: Use VLAN tagging (IEEE 802.1Q) to manage traffic between VLANs.
- Access Control: Implement Access Control Lists (ACLs) on routers and switches to control traffic between VLANs.
Subnetting: Dividing a network into smaller, logical sub-networks (subnets).
Implementation:
- IP Address Planning: Design an IP addressing scheme that defines different subnets for each segment.
- Routing: Configure routers to manage traffic between subnets.
- Access Control: Use ACLs and firewall rules to restrict inter-subnet traffic.
Micro-Segmentation with Software-Defined Networking (SDN): Granular workload or application-level segmentation using SDN technology.
Implementation:
- SDN Controllers: Deploy SDN controllers to manage network traffic programmatically.
- Network Virtualization: Use network virtualization to create isolated segments for different workloads or applications.
- Policy Enforcement: Define and enforce security policies at the micro-segment level.
Use of Next-Generation Firewalls (NGFWs): NGFWs provide advanced features like deep packet inspection and application awareness for segmentation.
Implementation:
- Deploy NGFWs: Place NGFWs at strategic points in the network to enforce segmentation.
- Define Policies: Create and enforce detailed security policies based on applications, users, and content.
- Monitor Traffic: Use NGFW capabilities to monitor and control traffic between segments.
Network Access Control (NAC): NAC solutions enforce security policies for devices attempting to access the network.
Implementation:
- NAC Systems: Deploy NAC solutions to authenticate and authorize devices.
- Policy Definition: Define policies based on device type, user role, and security posture.
- Dynamic Segmentation: Use NAC to assign devices to the appropriate network segments dynamically
Security Policies and Access Control
Network segmentation is challenging due to its complexity, increased management effort, and cost. It requires careful planning, secure inter-segment communication, and proper configurations to avoid vulnerabilities. Scaling the network and ensuring compatibility with existing systems add further difficulties.
Challenges:
- Complexity: Implementing and managing segmented networks can be complex and require significant resources.
- Inter-Segment Communication: Ensuring necessary communication between segments while maintaining security can be challenging.
- Maintenance: Ongoing management and updates to segmentation policies require continuous attention.
- Scalability: Maintaining an effective segmentation strategy can become more complex as organizations grow.
Future / Advance Trends:
- Zero Trust Architecture: Incorporating network segmentation as part of a zero-trust security model to verify every access request as though it originates from an open network.
- Seqrite ZTNA: A SaaS-delivered Zero Trust Network Access solution that provides secure remote access to corporate applications and services to employees, contractors, and vendor staff across borderless workspaces.
For more details, check out the below links:
https://www.seqrite.com/documents/en/datasheets/seqrite-ztna-datasheet.pdf
Co-Authors:
Sumit Patil
Niraj Lazarus Makasare




