Manual
Refer our user guide for information regarding installation and use of Seqrite ZTNA
Enforce zero-trust network access policies for every employee, contractor, or vendor staff accessing all types of enterprise applications and services.
With advanced correlation between all users, services and applications, organizations can view connection flow between them across organizational IT infrastructure in real-time.
Classify user-entity landscape based on business context. Implement zero-trust model policies based on set classification and security requirements.



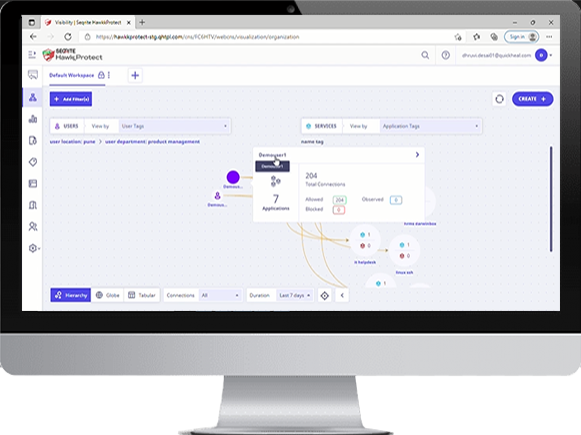
With Seqrite ZTNA, shift the emphasis from safeguarding networks to securing individuals, devices, resources, and connections by leveraging the least privilege approach.
REQUEST A DEMOExperience the best-in-class solutions offered by Seqrite and how they can address the security challenges of your enterprise. Explore our key features and capabilities with a demo.
Request A DemoAdvanced protection that proactively detects and prevents malicious activity which may exploit application vulnerabilities.
Contact Now