Overview
In the 1990s, as the internet gained popularity, cybercriminals started developing and distributing basic forms of malware, including password stealers. Early stealer malware primarily targeted login credentials and passwords for online services and email accounts. As technology advanced, so did the capabilities of stealer malware. They began to target various forms of sensitive information.
With the rise of the cybercrime ecosystem and underground forums, the number of stealer malware variants increased significantly through MaaS (Malware-as-a-Service). Cybercriminals started selling and distributing different types of stealer malware, catering to specific needs and vulnerabilities. Modern stealer malware, like the “Warp Stealer,” is highly sophisticated and multi-functional. They can extract valuable information from infected systems, including hardware details, network configurations, browsing history, and sensitive data related to finance and online activities. Over time, stealer malware has evolved to evade detection and security measures. Some use advanced obfuscation techniques and rootkit functionality to hide their presence and remain undetected by traditional antivirus software.
Stealer malware is often distributed through various methods, including malicious email attachments, infected software downloads, drive-by downloads from compromised websites, and social engineering techniques.
Infection chain
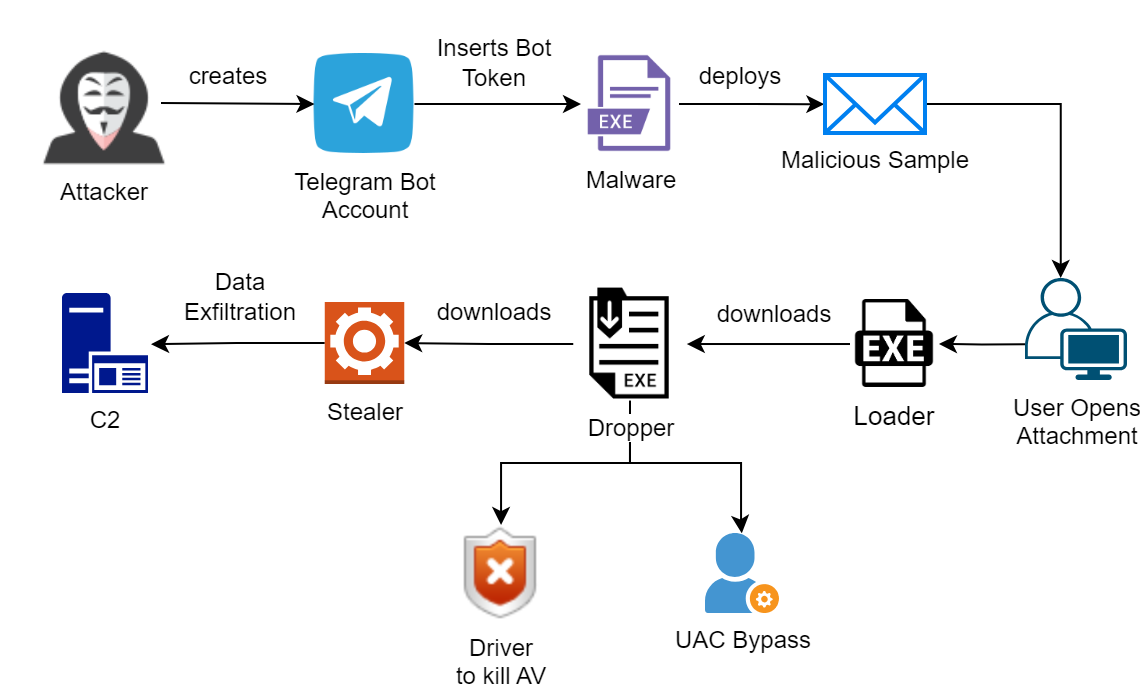
- The attacker creates a Telegram Bot Account and inserts a Bot token into an executable.
- The attacker deploys the executable as an email attachment and sends it to the victim’s mail.
- When the victim opens the mail, the executable gets downloaded and starts its execution.
- It acts as a loader and downloads the dropper component. This, in turn, drops two files, one for bypassing UAC and the other to kill AV/EDR solutions.
- The dropper finally downloads a stealer, which steals all the victim’s system information, credit card details, crypto wallet details, social media account details, web browser cookies, and saved passwords. It also collects web camera shots and saves them as logs, which will later be sent to the attacker’s C2.
- It has anti-analysis techniques like anti-debugging, anti-VM, and anti-sandbox, and it also checks for any analysis tools present in the system to hide its behavior.
- It will collect all the key information and store it in a folder along with clipboard information if it has any crypto wallet. It will also replace the wallet ID with the attacker’s wallet ID.
Conclusion
As the cyber landscape evolves, stealer malware will likely continue to adapt and find new ways to exploit users’ vulnerabilities and compromise their privacy and security. To defend against such threats, individuals and organizations must keep their software updated, use up-to-date antivirus software, regularly update systems and applications, exercise caution while clicking links or downloading files, and practice good password hygiene to safeguard our personal information. An in-depth analysis of Warp Loader, Dropper, and Stealer, along with the UAC bypass & AV-killing techniques, can be found in our whitepaper.
IOC
| MD5 | Description | Detection |
| ac941919c2bffaf6aa6077322a48f09f | Warp Loader | Trojan.WarpLoader |
| fe08102907a8202581766631b1e31915 | Warp Dropper | Trojan.WarpDropper |
| e1f6f92526dabe5365b7c3137c385cd2 | Warp Stealer (Stealerium) | Trojan.YakbeexMSIL.ZZ4 |
| b400973f489df968022756822ca4d76a | UAC Bypass | Exploit.UACBypass |
| 0a0bdd679d44b77d2e6464e9fac6244c | Avast Anti-Rootkit Driver | (legitimate) |
URLs
| hxxps://api.telegram[.]org/bot6273916038:AAHnJC6VymoyKdR2Iq8CzH2-ZnzIcJQ0-w8/sendMessage?&parse_mode=HTML&chat_id=-1001963477498&text= |
| hxxps://api.telegram[.]org/bot6273916038:AAHnJC6VymoyKdR2Iq8CzH2-ZnzIcJQ0-w8/getChat?chat_id=-1001963477498 |
| hxxps://api.telegram[.]org/bot6273916038:AAHnJC6VymoyKdR2Iq8CzH2-ZnzIcJQ0-w8/sendDocument?chat_id=-1001963477498 |
| hxxps://api.telegram[.]org/bot6273916038:AAHnJC6VymoyKdR2Iq8CzH2-ZnzIcJQ0-w8/sendMessage?parse_mode=Markdown&chat_id=-1001963477498&text= |
| hxxps://api.telegram[.]org/bot6273916038:AAHnJC6VymoyKdR2Iq8CzH2-ZnzIcJQ0-w8/getFile?file_id=-1001963477498 |
| hxxps://softstock[.]shop/download/Adobe%20Acrobat%20Update.exe |
Authors
Sathwik Ram Prakki
Rayapati Lakshmi Prasanna Sai



